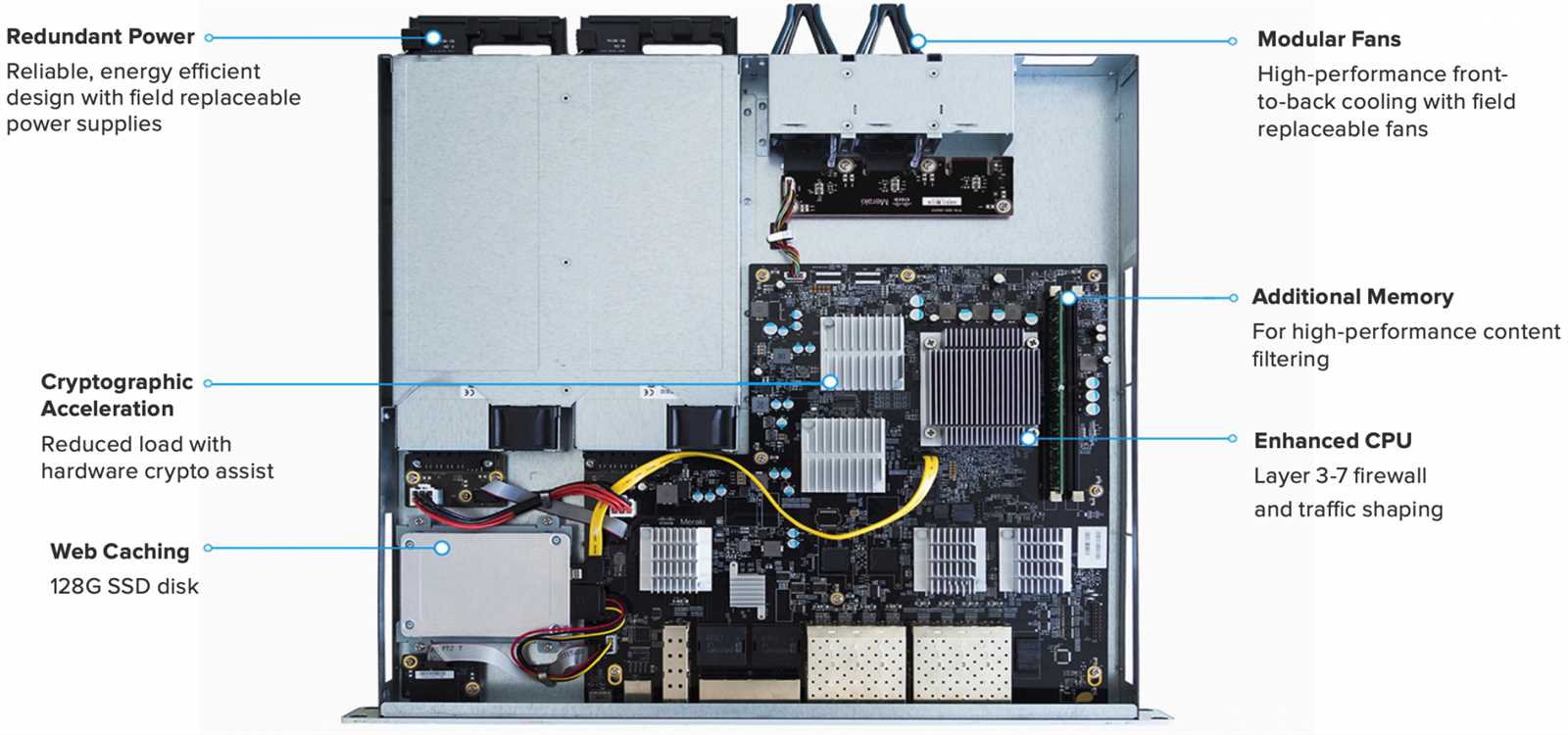
Delving into the intricacies of a leading-edge network device unveils a realm of possibilities, each specification a thread weaving into the fabric of modern connectivity. Within these specifications lies the blueprint of prowess, the embodiment of seamless networking, and the conduit to digital empowerment.
Unraveling the Layers: Beneath the surface of technical jargon lies a narrative of innovation and efficiency. These specifications, akin to the DNA of connectivity, dictate the capabilities and limitations of a device designed to navigate the digital landscape with finesse.
Empowering Connectivity: Understanding the nuances of these specifications is akin to wielding a master key, unlocking doors to enhanced productivity, fortified security, and uninterrupted communication. Each figure and metric is a testament to the promise of streamlined operations and elevated user experiences.
Understanding the Meraki MX67C Datasheet

In this section, we delve into comprehending the intricacies of the documentation provided for the MX67C device by Meraki. The datasheet serves as a fundamental tool for users, offering a comprehensive overview of the device’s capabilities, specifications, and features. Let’s explore the nuances encapsulated within this informational resource.
| Section | Focus |
|---|---|
| Specifications | This segment delineates the technical attributes and performance metrics of the MX67C, encompassing aspects such as throughput, interfaces, and supported protocols. |
| Features | Here, the datasheet elaborates on the functionalities and capabilities inherent to the MX67C, elucidating how these features cater to the diverse needs of users. |
| Deployment Scenarios | This section illustrates various scenarios and environments where the MX67C can be deployed effectively, offering insights into its adaptability and versatility. |
| Comparative Analysis | Comparing the MX67C with other models or similar devices, this part aids users in understanding its positioning within the Meraki product lineup and the broader market. |
| Usage Guidelines | Providing recommendations and best practices for deploying, configuring, and managing the MX67C, this segment empowers users to maximize the utility of their investment. |
By delving into each aspect with a discerning eye, users can glean valuable insights from the datasheet, enabling informed decision-making and efficient utilization of the Meraki MX67C.
Exploring Key Hardware Specifications

Delving into the fundamental hardware intricacies unveils the core architectural features of the device, shedding light on its performance capabilities and operational functionality. This section aims to dissect the essential hardware specifications, providing insight into the underlying framework that powers the device’s operations.
Processor Prowess: At the heart of this device lies a robust processing unit, engineered to handle the complexities of modern networking demands with finesse. The processing prowess dictates the device’s ability to manage data traffic, execute tasks efficiently, and maintain optimal performance levels.
Memory Mastery: Memory modules play a pivotal role in ensuring seamless data processing and storage operations. The memory capacity of the device influences its ability to store critical information temporarily, facilitating swift access and retrieval as per operational requirements.
Connectivity Conundrum: A myriad of connectivity options defines the device’s adaptability to diverse network environments. From Ethernet ports to wireless interfaces, each connectivity component serves a unique purpose in enabling seamless communication and data exchange across the network infrastructure.
Security Safeguards: Embedded security mechanisms fortify the device against potential threats and vulnerabilities, safeguarding sensitive data and ensuring network integrity. Hardware-based security features enhance the device’s resilience to cyber attacks, reinforcing its role as a reliable guardian of network assets.
Power Proficiency: Efficient power management capabilities optimize energy consumption, prolonging the device’s operational lifespan and reducing environmental impact. Power efficiency enhancements bolster the device’s sustainability credentials while ensuring uninterrupted network connectivity.
Exploring these key hardware specifications provides a comprehensive understanding of the device’s technological prowess and operational resilience, laying the foundation for informed decision-making and strategic network deployment.
Examining Security Features and Capabilities

Delving into the realm of safeguarding measures and functionalities, this section navigates through the intricate tapestry of security elements and proficiencies ingrained within the system. It scrutinizes the defensive mechanisms and aptitudes designed to fortify the network infrastructure against potential threats, ensuring a resilient shield against malicious incursions.
Robust Firewall Protection
At the core of its defensive arsenal lies a robust firewall system, engineered to intercept and neutralize unauthorized access attempts while facilitating legitimate communication flows. This multifaceted barrier employs advanced algorithms and rule sets to discern between benign and malevolent traffic, enforcing stringent controls to uphold network integrity.
Dynamic Threat Intelligence
Augmenting its defensive posture, the system integrates dynamic threat intelligence mechanisms that continuously monitor and analyze emerging risks in real-time. Leveraging sophisticated algorithms and threat databases, it remains vigilant against evolving threat landscapes, preemptively mitigating potential breaches and vulnerabilities before they materialize into significant security incidents.
Within this context, the exploration of security features and capabilities underscores the paramount importance of proactive defense strategies in safeguarding digital assets and preserving operational continuity.
Integration and Compatibility Insights

In this section, we delve into the intricate interconnections and seamless interactions within the technological ecosystem surrounding the innovative device at hand. From the intricate web of integrations to the dynamic landscape of compatibility, we uncover the essential insights that pave the way for enhanced functionality and unparalleled user experience.
Seamless Integration

Within the realm of technology, synergy is paramount. The fusion of diverse components harmonizes to create a unified system greater than the sum of its parts. Our exploration into integration unveils the intricate dance between hardware, software, and protocols, where each element contributes its unique prowess to the collective tapestry. From interoperability with existing infrastructures to streamlined workflows across platforms, seamless integration is the cornerstone of efficiency and innovation.
Compatibility Dynamics
Compatibility is the cornerstone upon which reliability and adaptability are built. Within the dynamic landscape of technology, the compatibility of devices, protocols, and interfaces dictates the fluidity of operations and the scope of possibilities. Our analysis delves into the nuanced nuances of compatibility dynamics, exploring the intricate balance between legacy systems and emerging standards. From backward compatibility ensuring continuity to forward-thinking adaptability embracing the future, understanding compatibility dynamics illuminates the path towards sustainable technological evolution.