
Unlocking the Potential: Dive into the comprehensive dossier, unveiling the dynamic capabilities and robust functionalities of the cutting-edge powerhouse. This elucidative exploration delves deep into the myriad features and intricate specifications, presenting a panoramic view of its prowess.
Unraveling the Blueprint: Embark on a journey through the intricate blueprint, meticulously crafted to redefine paradigms in network security. Discover the intricacies encoded within, as each facet unveils a strategic component, meticulously designed to fortify digital infrastructures.
Deciphering Innovation: Navigate through a tapestry of innovation, where technological marvels converge to forge a formidable defense mechanism. Witness the fusion of agility, precision, and scalability, harmonized to orchestrate a symphony of security.
Delving Beyond: Venture beyond the surface, where every data point conceals a narrative of resilience and adaptability. Unravel the layers of insight, as the narrative unfolds to reveal a saga of reliability and efficacy.
Cisco Firepower 2100 Series: Overview and Features
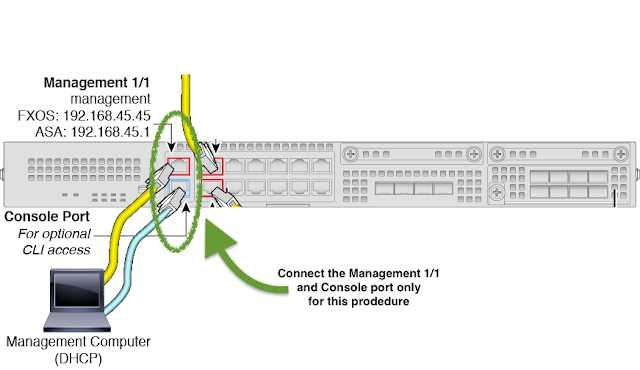
In this section, we delve into an exploration of the comprehensive capabilities and distinguishing characteristics of the acclaimed Firepower 2100 Series by Cisco. Unveiling the essence of its prowess and functionality, we navigate through its array of features, elucidating its role in contemporary network security landscapes.
| Feature | Description |
|---|---|
| Advanced Threat Protection | Employing cutting-edge mechanisms to thwart intricate cyber threats, safeguarding networks against sophisticated breaches. |
| Scalability | Adaptable architecture tailored to accommodate diverse network infrastructures, ensuring seamless expansion without compromising performance. |
| Integrated Security Services | Integrating a myriad of security services into a unified platform, fortifying networks with a holistic defense mechanism against multifaceted cyber risks. |
| High Performance | Delivering exceptional throughput and latency figures, empowering networks with the agility and responsiveness required to tackle evolving threats. |
| Centralized Management | Facilitating centralized control and oversight, simplifying administration tasks and enhancing operational efficiency. |
Through a meticulous examination of these features and beyond, we unravel the multifaceted tapestry of capabilities that define the Firepower 2100 Series, exemplifying its position as a stalwart guardian of modern network integrity.
Discover the Key Specifications

Delve into the fundamental details and essential characteristics that define the technological prowess of this advanced security system. Explore the core attributes and intrinsic features that underpin its performance and functionality, unveiling a comprehensive understanding of its capabilities.
Performance Metrics
Uncover the metrics that gauge the system’s operational efficiency and efficacy in safeguarding digital environments. From throughput to latency, delve into the quantitative measures that illustrate its capacity to handle network traffic and mitigate potential threats.
Technical Features

Explore the intricate technical nuances and innovative functionalities embedded within this cutting-edge solution. From advanced encryption protocols to dynamic threat intelligence integration, unravel the myriad features that fortify its resilience against evolving cyber threats.
| Specification | Description |
| Throughput | Measure of data processing capability, depicting the volume of traffic handled per unit of time. |
| Latency | Indicator of response time, crucial for assessing the system’s agility in threat detection and mitigation. |
| Encryption Standards | Details the encryption algorithms and protocols employed to secure data transmissions. |
| Threat Intelligence Integration | Integration of real-time threat intelligence feeds for proactive threat detection and response. |
Enhanced Security with Cutting-Edge Technology
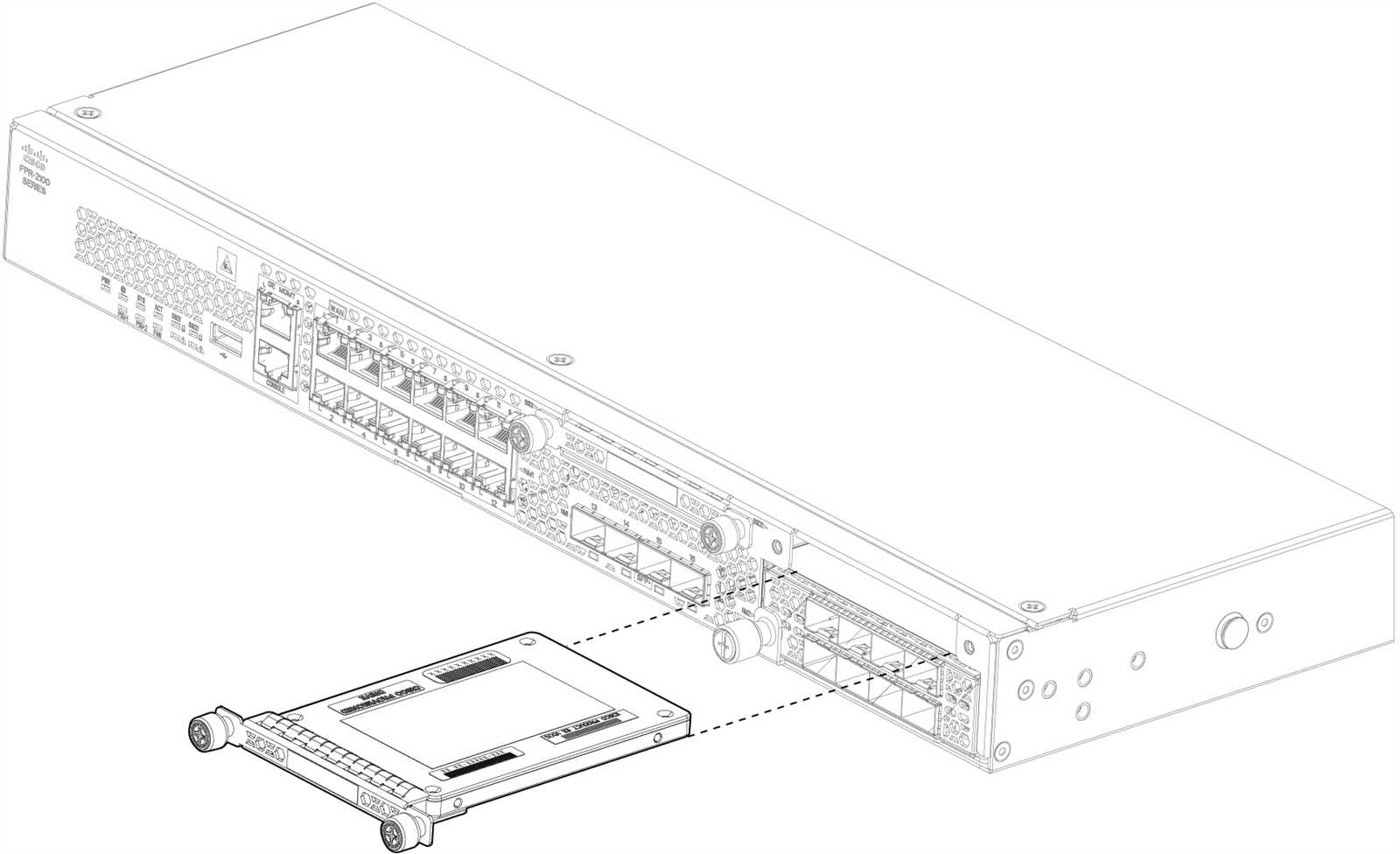
In the realm of digital fortification, there exists a formidable ally, a bastion of protection that transcends conventional barriers. Embrace a paradigm shift in safeguarding your digital assets with the revolutionary technology embodied by the potent solution known by its moniker, the 21st-century sentinel. Explore how this innovative shield elevates the concept of security to unprecedented heights.
Within the digital landscape, threats loom ominously, ever-evolving and relentless. Yet, amidst this turbulent terrain, a beacon of assurance emerges, fortified with advanced mechanisms and proactive defenses. Discover a sanctuary where threats are intercepted before they breach the perimeter, where vigilance is not just a virtue but an inherent attribute.
Experience a holistic approach to security, where intelligence converges with agility, and resilience is not just a notion but a reality. Delve into a realm where threats are not merely detected but neutralized with surgical precision, leaving no room for compromise.
Understanding Advanced Threat Protection
In the realm of digital security, the landscape is constantly evolving, presenting an array of challenges that demand innovative solutions. This section delves into the intricate realm of fortifying networks against sophisticated threats, employing a multifaceted approach to safeguarding digital assets.
The Complexity of Modern Threats
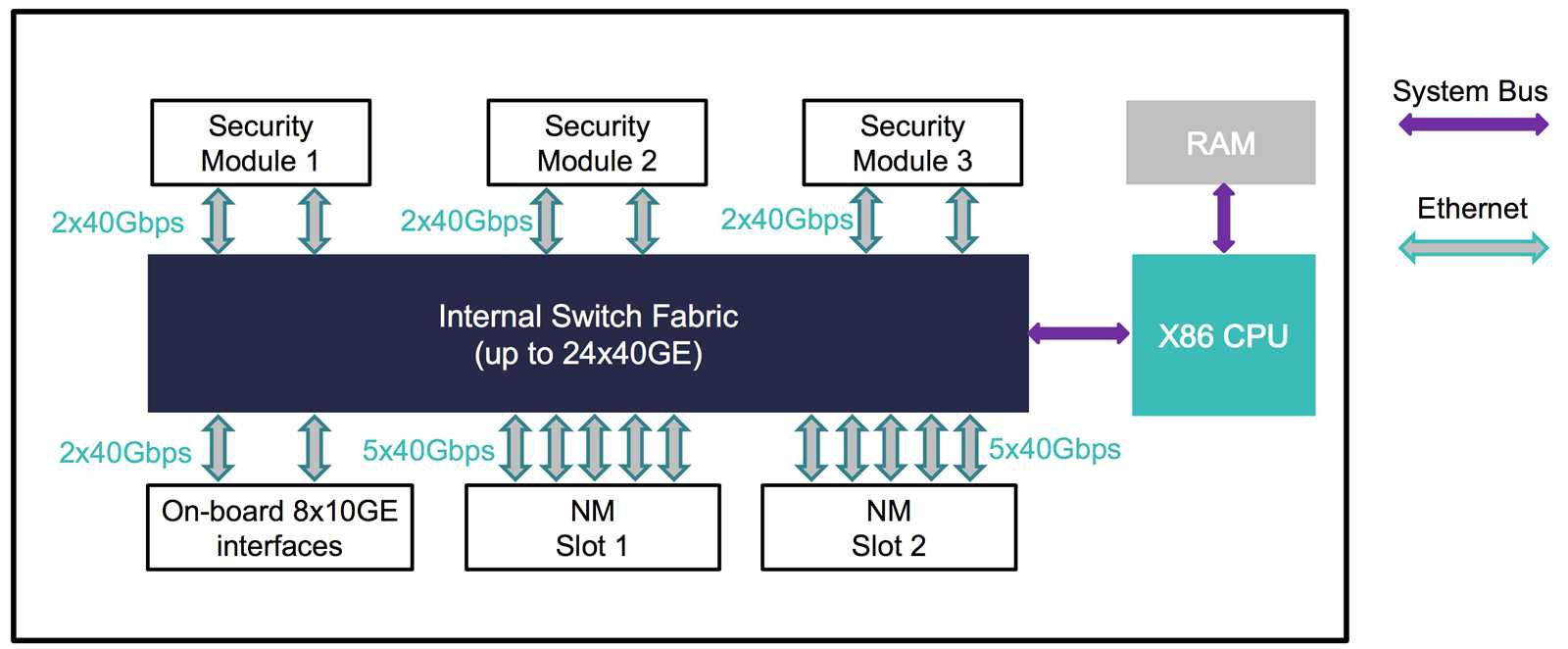
Today’s cyber adversaries employ a diverse arsenal of tactics, ranging from stealthy malware to intricate social engineering schemes. Understanding the nuances of these threats is paramount in devising effective defense strategies.
Advanced Threat Detection: In order to combat the evolving nature of cyber threats, modern security solutions leverage advanced threat detection mechanisms. These sophisticated algorithms analyze patterns, anomalies, and behaviors to identify potential risks before they can wreak havoc.
The Role of Proactive Defense
Proactive defense strategies are essential in mitigating the impact of cyber attacks. By anticipating potential threats and vulnerabilities, organizations can implement preemptive measures to bolster their security posture.
Behavioral Analysis: A key component of advanced threat protection involves behavioral analysis, which scrutinizes the actions of users and entities within the network. By identifying deviations from normal patterns of behavior, suspicious activities can be flagged for further investigation.
Deployment Options for Advanced Security Appliance
Exploring the various configurations and setups for maximizing the potential of the cutting-edge security solution, this section delves into the diverse deployment strategies available for the latest iteration of high-performance network defense technology.
1. Network Topology Considerations

Before diving into deployment specifics, it’s imperative to assess the network landscape and tailor the deployment approach accordingly. Whether it’s a centralized or distributed architecture, understanding the topology nuances helps optimize the utilization of the security appliance.
2. Deployment Scenarios

The versatility of the advanced security appliance allows for flexible deployment scenarios, ranging from traditional perimeter defense to micro-segmentation within the network infrastructure. Examining these scenarios sheds light on how organizations can adapt the solution to suit their unique security requirements.
| Deployment Scenario | Description |
|---|---|
| Perimeter Defense | Securing the network’s edge to safeguard against external threats, ensuring comprehensive protection for incoming and outgoing traffic. |
| Internal Segmentation | Implementing granular security policies to segment internal network segments, fortifying against lateral movement of threats and insider risks. |
| Virtual Private Network (VPN) | Enabling secure remote access for authorized users through encrypted tunnels, extending the perimeter defense to remote locations. |
Each deployment scenario offers distinct advantages and considerations, empowering organizations to tailor their security posture according to their specific operational needs and risk profiles.