Unveiling the latest innovations in digital security, this article delves into the intricacies of cutting-edge protective measures designed to safeguard sensitive information and networks. Delving beyond conventional means of fortification, it navigates through the realm of dynamic security solutions, offering a panoramic view of robust defenses against modern cyber threats.
Embarking on a journey through the realm of digital guardianship, readers will uncover a tapestry of sophisticated techniques and methodologies engineered to fortify digital ecosystems. From intricate encryption protocols to agile threat detection mechanisms, each facet intertwines to sculpt a formidable bulwark against the ever-evolving landscape of cyber intrusions.
Immersing in the lexicon of security paradigms, this exposition elucidates the essence of resilience and adaptability ingrained within contemporary security frameworks. Through a meticulous examination of proactive measures and reactive countermeasures, it illuminates the path toward fortified networks and fortified peace of mind.
Understanding the Features of 5800 Checkpoint Datasheet

Exploring the Attributes
In this section, we delve into the intricate details encapsulated within the 5800 Checkpoint Datasheet. Unraveling its myriad facets, we embark on a journey to comprehend the essence of its functionalities and capabilities. Through a meticulous examination, we aim to illuminate the diverse array of features inherent within.
Analyzing the Characteristics
Here, we embark on a comprehensive analysis of the distinctive traits that define the 5800 Checkpoint Datasheet. By scrutinizing its nuances and intricacies, we aim to gain a profound understanding of its inherent attributes. Through this analytical lens, we seek to unravel the underlying principles that govern its performance and efficacy.
Deciphering the Elements
This segment is dedicated to deciphering the elemental components that constitute the essence of the 5800 Checkpoint Datasheet. By dissecting its constituent parts and functionalities, we endeavor to unveil the intricate interplay of features that contribute to its overall functionality. Through a systematic exploration, we aim to elucidate the significance of each element within the datasheet’s framework.
Unveiling the Capacities
Here, we embark on a journey to unveil the vast capacities encapsulated within the 5800 Checkpoint Datasheet. Through an in-depth exploration of its capabilities and potentialities, we seek to unravel the extent of its prowess and versatility. By shedding light on its diverse capacities, we endeavor to showcase the breadth of possibilities enabled by this comprehensive datasheet.
Key Specifications and Performance Metrics
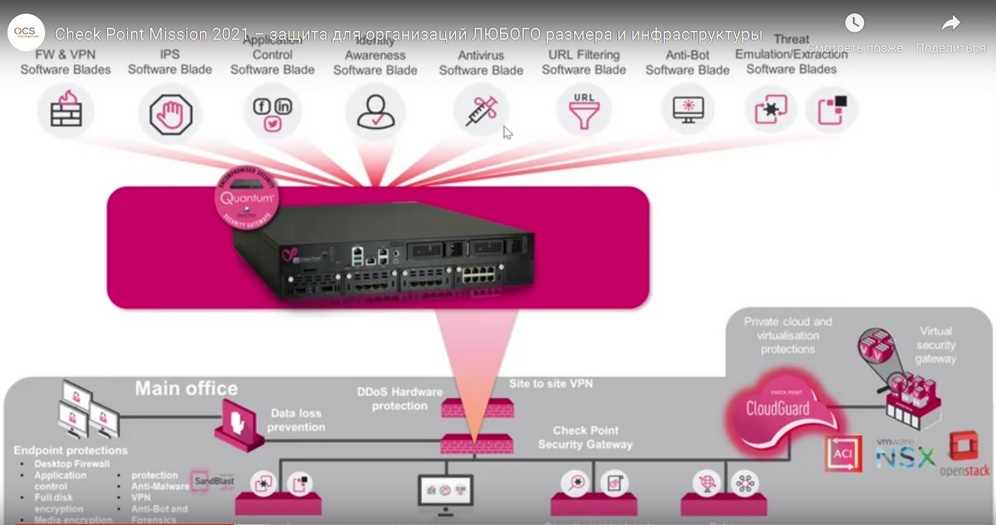
In this section, we delve into the essential characteristics and operational measures defining the prowess of the mentioned system. We explore its foundational aspects, highlighting its capabilities and operational efficacy without delving into specific numerical values.
- Functional Attributes: This encompasses the core functionalities and operational capabilities inherent to the system, elucidating its range of operations and potential applications.
- Performance Metrics: Here, we analyze the quantifiable indicators that gauge the system’s efficiency, responsiveness, and overall performance in various scenarios.
- Reliability and Stability: We assess the system’s consistency and robustness, focusing on its ability to sustain optimal performance levels over extended durations without compromising operational integrity.
- Security Protocols: Delving into the security measures integrated into the system, we explore its resilience against potential threats and vulnerabilities, ensuring comprehensive protection of critical data and assets.
- Scalability and Flexibility: This segment addresses the system’s adaptability to evolving demands and scalability to accommodate expanding requirements, emphasizing its capacity to grow alongside dynamic operational landscapes.
Through a comprehensive examination of these facets, we aim to provide a holistic overview of the system’s capabilities, shedding light on its significance and potential impact within relevant domains.
Practical Applications and Integration Possibilities

In this section, we explore the practical utilization and potential integration avenues of the technology encapsulated within the 5800 checkpoint datasheet. Delving beyond mere specifications, we uncover the tangible scenarios where this technology can be effectively applied, as well as the diverse ways it can seamlessly amalgamate with existing systems and processes.
Real-world Implementation Scenarios
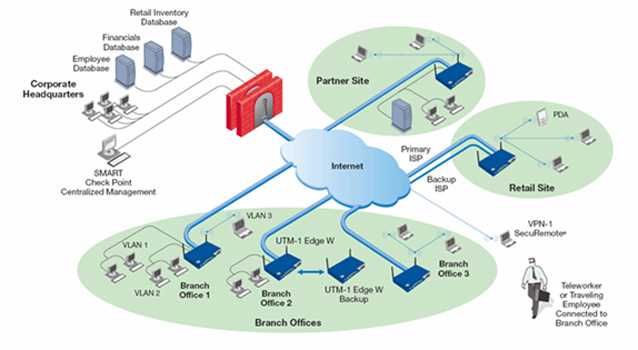
From network security to data management, the functionalities delineated within the 5800 checkpoint datasheet find resonance in a myriad of real-world scenarios. Organizations across various sectors can harness its capabilities to fortify their digital infrastructure, ensuring robust protection against cyber threats while maintaining operational efficiency.
Integration Synergies
The integration potential of the technologies outlined in the 5800 checkpoint datasheet extends far beyond standalone applications. Through strategic integration with existing frameworks and platforms, businesses can unlock synergies that streamline operations, enhance security protocols, and foster innovation. By seamlessly weaving these technologies into their ecosystem, organizations can realize a harmonious convergence of efficiency and resilience.
Security Considerations and Best Practices

In this section, we delve into the vital aspects surrounding the safeguarding of sensitive information and the optimization of protective measures. Understanding the intricacies of securing your systems goes beyond mere technical configurations; it necessitates a comprehensive approach that encompasses both procedural protocols and technological fortifications.
The Importance of Vigilance
Constant Vigilance: Ensuring the integrity and confidentiality of data demands perpetual awareness and proactive measures. Threat landscapes evolve incessantly, demanding a dynamic response to emerging risks.
Implementing Robust Protocols

Establishing Resilient Protocols: Instituting a multi-layered defense strategy fortified by encryption, access controls, and regular audits forms the cornerstone of effective security. Moreover, fostering a culture of security consciousness among personnel is equally imperative to fortify the human element against potential vulnerabilities.
By adhering to these foundational principles and integrating them seamlessly into your operational framework, you can navigate the complexities of security with confidence and diligence.