Discover a comprehensive resource providing insights into the dynamic realm of advanced network security infrastructure. Delve into an in-depth exploration of next-generation technology designed to fortify your digital perimeter against evolving cyber threats.
Explore a compendium of features, functionalities, and performance metrics aimed at elevating your organization’s defensive capabilities. Uncover the potential of state-of-the-art security solutions tailored to safeguard your network ecosystem with unparalleled precision and efficacy.
Embark on a journey through the landscape of cutting-edge network security innovations, meticulously crafted to address the intricacies of modern digital infrastructure. Harness the power of insightful analysis and strategic deployment to shield your organization from the rampant challenges of the cyber age.
Understanding Fortinet Product Information
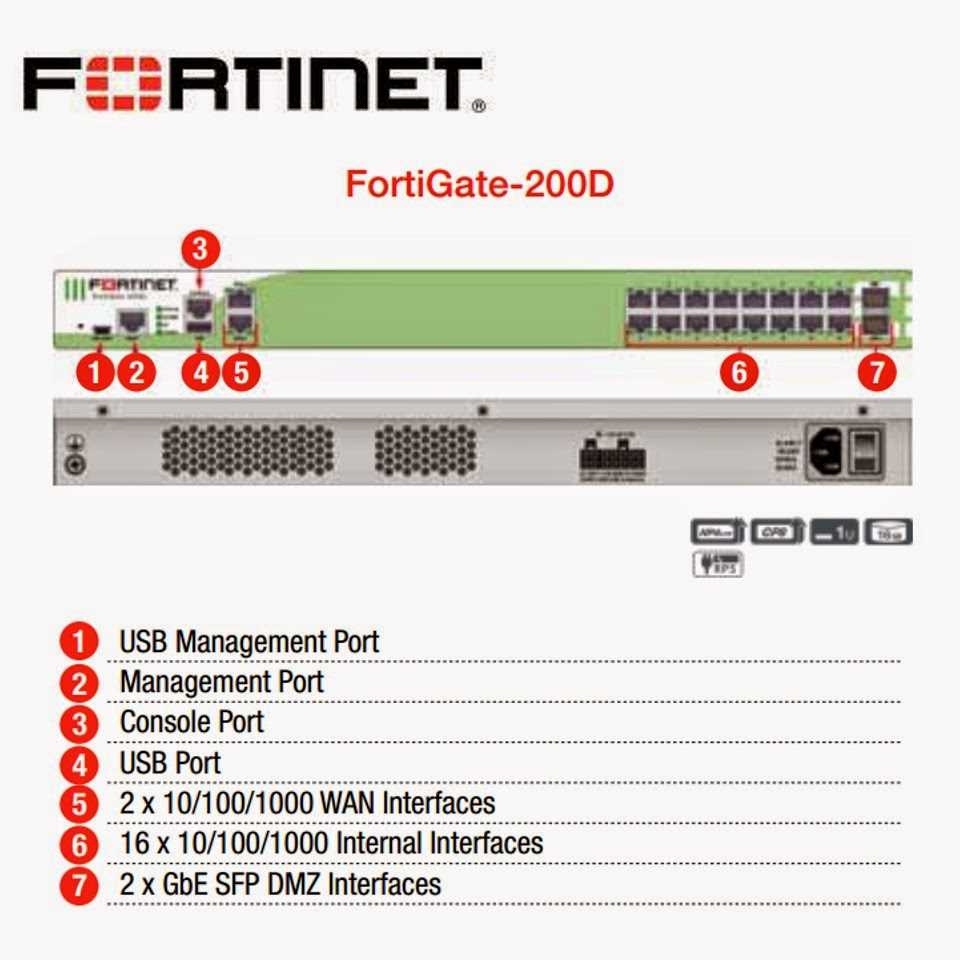
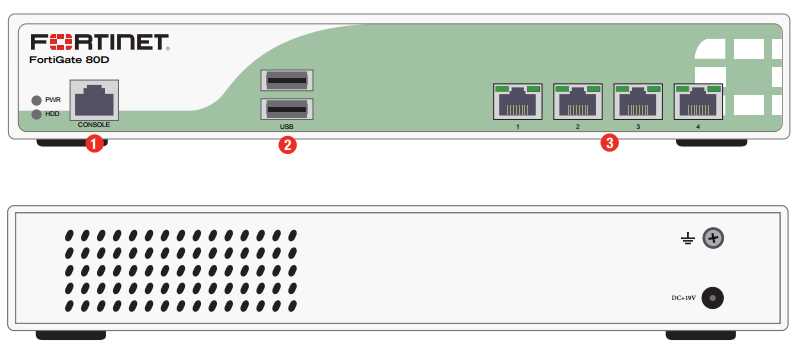
When delving into the intricacies of deciphering a comprehensive overview of a cybersecurity appliance, it’s essential to grasp the nuances embedded within the documentation. Within the realm of network security solutions, Fortinet offers a wealth of product information encapsulated within what is commonly referred to as a datasheet. This vital resource serves as a roadmap, elucidating the capabilities, specifications, and features of Fortinet’s innovative offerings.
| Key Features | Performance Metrics | Deployment Options |
| Integral Functionality | Throughput Rates | Scalability |
| Security Protocols | Connection Capacities | Flexibility |
| Advanced Capabilities | Resource Utilization | Integration Capabilities |
By navigating through the intricate details presented within, one can discern the optimal solution tailored to specific organizational needs. Understanding the nuances of the datasheet empowers decision-makers to make informed choices, aligning technological investments with strategic objectives.
Furthermore, comprehending the terminology and performance benchmarks outlined within the document is paramount for gauging the suitability of Fortinet’s offerings within diverse network infrastructures. Whether evaluating throughput rates, scalability options, or deployment modalities, a nuanced understanding of the datasheet facilitates the alignment of cybersecurity strategies with business imperatives.
In essence, the journey of understanding Fortinet’s product information is a voyage into the realm of cybersecurity efficacy, where clarity and insight serve as guiding beacons amidst the complexity of modern network environments.
Exploring Key Features and Capabilities

In this section, we delve into the essential functionalities and strengths of the product, offering an in-depth exploration of its core capabilities. By dissecting its key features, we aim to provide a comprehensive understanding of its potential and how it can address various networking challenges.
Security Suite
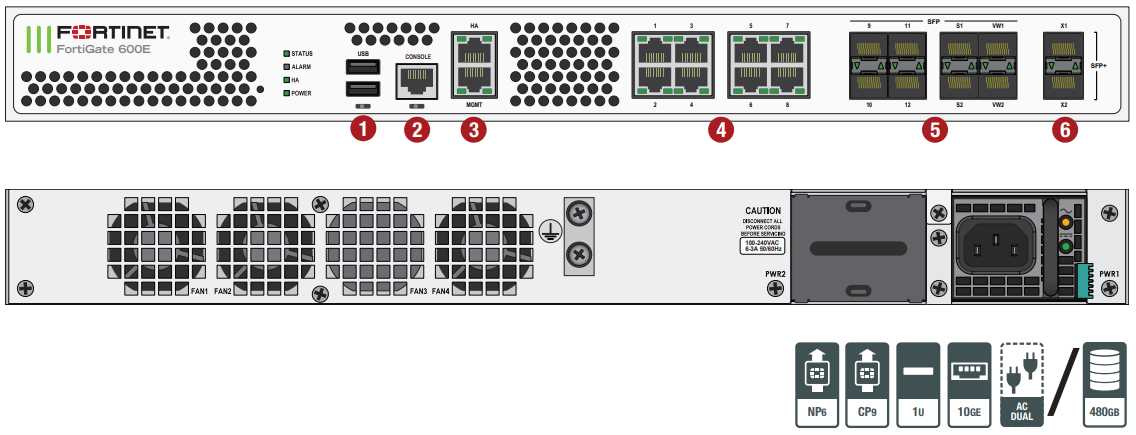
The security suite encompasses a robust array of tools and mechanisms engineered to safeguard digital assets and mitigate emerging threats. Within this suite, users can leverage advanced threat detection, intrusion prevention, and encryption protocols to fortify their network perimeter and ensure data integrity.
Performance Optimization
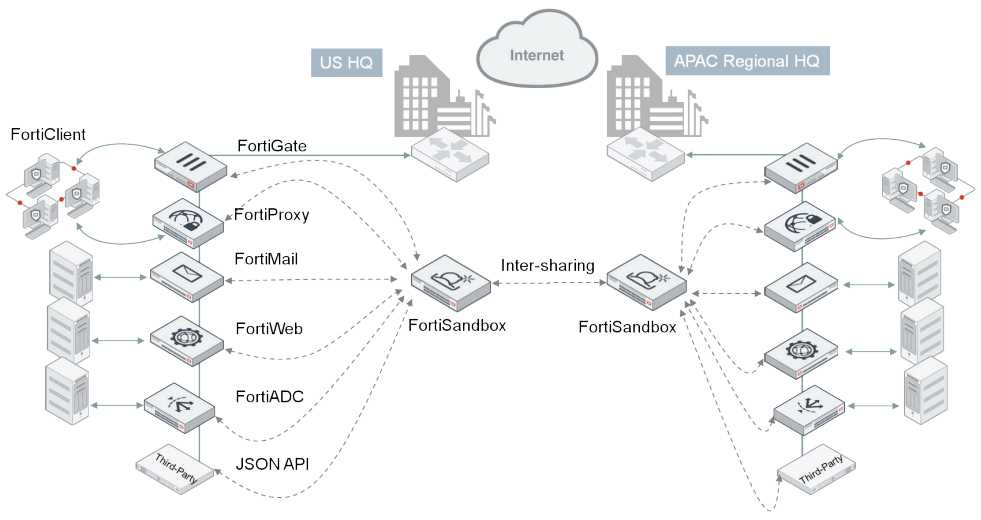
Optimizing performance lies at the heart of this solution, enhancing network efficiency and responsiveness. Through innovative techniques such as traffic shaping, load balancing, and Quality of Service (QoS) configurations, users can streamline data flow and prioritize critical applications, thereby maximizing productivity and user experience.
| Feature | Description |
|---|---|
| Advanced Threat Protection | Employs sophisticated algorithms and behavioral analysis to detect and neutralize evolving cyber threats in real-time. |
| VPN Integration | Seamlessly integrates with Virtual Private Networks (VPNs) to establish secure connections over public networks, ensuring confidentiality and privacy. |
| Web Filtering | Implements granular web filtering policies to regulate internet access, block malicious content, and enforce compliance with organizational guidelines. |
| High Availability | Delivers uninterrupted service availability through redundant hardware configurations and failover mechanisms, minimizing downtime and ensuring business continuity. |
Comparing Firewall Models to Suit Various Requirements

Understanding the diverse spectrum of cybersecurity needs demands a nuanced analysis of available solutions. In this section, we delve into the intricacies of selecting the optimal firewall model to align with specific organizational requirements. Each firewall variant offers distinct features and capabilities, tailored to address unique challenges encountered across various industries and network architectures.
Functionality and performance metrics serve as critical benchmarks for evaluating firewall suitability. By meticulously examining factors such as throughput, concurrent sessions, and security protocols, organizations can discern the ideal fit for their operational demands. Additionally, considerations regarding scalability and future-proofing must not be overlooked, ensuring seamless adaptation to evolving cybersecurity landscapes.
Customization options empower enterprises to tailor firewall deployments according to their distinct security postures. From robust threat detection mechanisms to advanced content filtering capabilities, each model presents a myriad of configuration possibilities. Adaptability emerges as a cornerstone, allowing organizations to fortify their defenses against emerging cyber threats without compromising operational efficiency.
Cost-effectiveness and ROI represent pivotal facets in the decision-making process, underscoring the importance of aligning firewall investments with anticipated benefits. By conducting comprehensive cost-benefit analyses, organizations can ascertain the most economically viable solution without sacrificing performance or security. Striking a delicate balance between affordability and efficacy is imperative for maximizing returns on cybersecurity investments.
Deployment Strategies and Optimization Techniques
In this section, we delve into effective methods and strategies for deploying and optimizing your network security solution. By implementing these best practices, you can enhance the efficiency and efficacy of your system, ensuring robust protection against emerging threats.
- Network Segmentation: Divide your network into distinct segments to isolate sensitive data and critical assets from potential threats. This practice enhances security by containing breaches and limiting the lateral movement of attackers.
- Role-Based Access Control: Implement role-based access control mechanisms to restrict user access based on their roles and responsibilities within the organization. By enforcing the principle of least privilege, you can minimize the risk of unauthorized access and potential security breaches.
- Regular Software Updates: Stay vigilant with software updates and patches to address vulnerabilities and weaknesses in your security infrastructure. Timely updates ensure that your system remains resilient against evolving threats and exploits.
- Threat Intelligence Integration: Integrate threat intelligence feeds and services into your security infrastructure to enhance threat detection and response capabilities. By leveraging real-time threat intelligence, you can proactively identify and mitigate emerging threats before they escalate.
- Continuous Monitoring and Analysis: Establish robust monitoring and analysis procedures to detect anomalous behavior and potential security incidents in real-time. By continuously monitoring network traffic and system logs, you can promptly identify and respond to security threats.
- Secure Configuration Management: Implement secure configuration management practices to ensure that your security devices are properly configured and hardened against potential attacks. Regularly review and update device configurations to align with industry best practices and security standards.
By following these deployment tips and best practices, you can fortify your network security posture and mitigate the risk of cyber threats and breaches. Remember, proactive planning and optimization are key to maintaining a resilient and secure network environment.