
Embark on a journey through the extensive realm of integrated network solutions, where communication conduits merge to form a seamless web of connectivity. Explore the intricacies of a holistic aggregation of data resources, where information pathways converge to amplify operational efficiency.
Delve into the synergistic fusion of technologies that propel modern networking paradigms towards unprecedented cohesion. Discover the synergistic interplay of diverse elements, each contributing its distinctive essence to the overarching tapestry of connectivity.
Unravel the intricacies of this intricately woven framework, where varied strands of innovation intertwine to fortify the foundations of digital infrastructure. Witness the harmonious integration of disparate components, orchestrated to elevate network capabilities to unparalleled heights.
Exploring the Comprehensive Information Package on Fortinet Network Solutions

In this section, we delve into an expansive dossier that elucidates the intricacies of an advanced network infrastructure solution. Delving beyond mere terminology, we embark on a journey to uncover the multifaceted features and capabilities encapsulated within this comprehensive documentation.
Unveiling Functional Capabilities

We commence our exploration by unraveling the operational prowess ingrained within this meticulously crafted compendium. Discovering the array of functionalities intertwined within, we navigate through the diverse spectrum of operations, each contributing to the seamless orchestration of network dynamics.
Unlocking Performance Insights
Beyond the surface, we endeavor to unravel the underlying mechanisms that drive performance excellence. By delving into performance metrics and insights, we unravel the layers of optimization strategies embedded within, illuminating pathways to enhance network efficacy and resilience.
Understanding the Comprehensive Security Features of Fortinet’s Integrated Threat Protection

In this section, we delve into the multifaceted security mechanisms that constitute Fortinet’s holistic approach to safeguarding your digital assets. The amalgamation of diverse protective layers forms a robust shield against an array of cyber threats, ensuring the integrity, confidentiality, and availability of your network resources.
Layered Defense Strategy

Fortinet employs a stratified defensive strategy, akin to a fortified castle with multiple barriers thwarting various assailants. Each layer operates synergistically, reinforcing the overall security posture while addressing distinct threat vectors. From perimeter defense mechanisms to advanced threat detection and response capabilities, every tier contributes to the resilience of the ecosystem.
Comprehensive Threat Intelligence

A cornerstone of Fortinet’s unified threat protection paradigm is its reliance on comprehensive threat intelligence. By leveraging real-time data feeds, machine learning algorithms, and global threat telemetry, Fortinet equips its security apparatus with the foresight necessary to proactively identify and neutralize emerging threats. This proactive stance enables swift adaptation to evolving threat landscapes, empowering organizations to stay one step ahead of adversaries.
| Component | Description |
|---|---|
| Firewall | Acts as the first line of defense, controlling inbound and outbound traffic based on predefined security policies. |
| Intrusion Prevention System (IPS) | Detects and mitigates network threats by inspecting packets and identifying malicious patterns or behaviors. |
| Antivirus | Scans files and network traffic for known malware signatures, preventing malicious payloads from infiltrating the network. |
| Web Filtering | Blocks access to malicious or inappropriate websites, reducing the risk of malware infection and data exfiltration. |
| Application Control | Manages and restricts the usage of specific applications to minimize the attack surface and enforce security policies. |
Examining Performance Metrics and Scalability
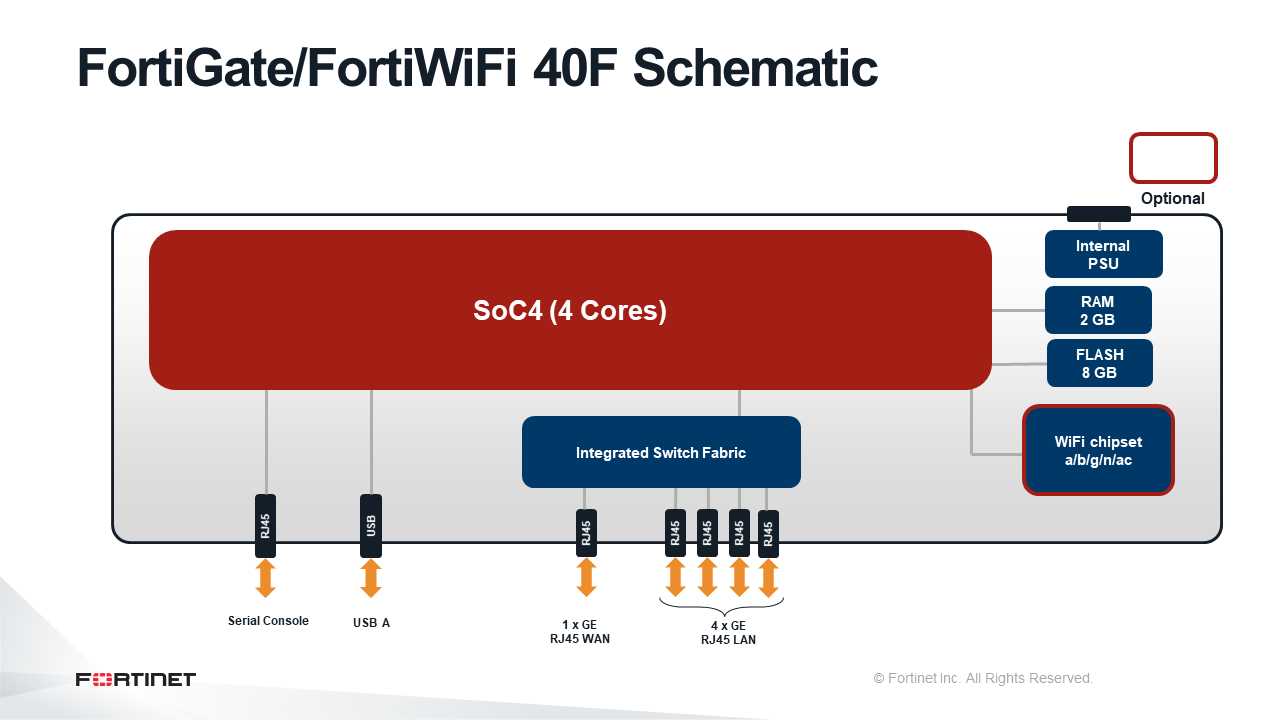
In this section, we delve into the intricacies of assessing the efficacy and adaptability of integrated solutions, exploring the dynamics of performance measurements and the capacity to expand without compromising efficiency.
Understanding Performance Metrics

Performance metrics serve as the barometer of system efficiency, gauging the ability to handle tasks with finesse and precision. These metrics encapsulate the essence of operational fluidity and response agility, reflecting the prowess of a system under varying workloads.
Evaluating Scalability

Scalability embodies the essence of growth potential, encapsulating the system’s ability to gracefully accommodate expanding demands without succumbing to bottlenecks or diminishing returns. By scrutinizing scalability, we uncover the architecture’s capacity to seamlessly adapt to evolving landscapes, ensuring sustained performance and relevance over time.
Integration and Deployment Considerations

When contemplating the assimilation and rollout of this comprehensive solution package, several critical factors warrant careful examination. The successful integration hinges on a meticulous evaluation of existing infrastructure compatibility, seamless assimilation with incumbent systems, and adept orchestration of deployment strategies.
Understanding the intricacies of interoperability among diverse components stands paramount. The cohesive incorporation necessitates a nuanced comprehension of interrelations among various elements within the operational ecosystem. Furthermore, meticulous attention must be accorded to the potential implications of deployment methodologies on existing workflows and operational efficiencies.
Strategizing deployment entails a holistic approach, entailing meticulous planning, adept resource allocation, and judicious scheduling. The delineation of clear deployment milestones and the establishment of robust contingency measures serve as linchpins in mitigating potential disruptions and ensuring the smooth transition to the new operational paradigm.
Moreover, considerations regarding scalability and future-proofing demand deliberate contemplation. Anticipating evolving organizational needs and technological advancements is imperative to ascertain the enduring relevance and efficacy of the integrated solution framework.