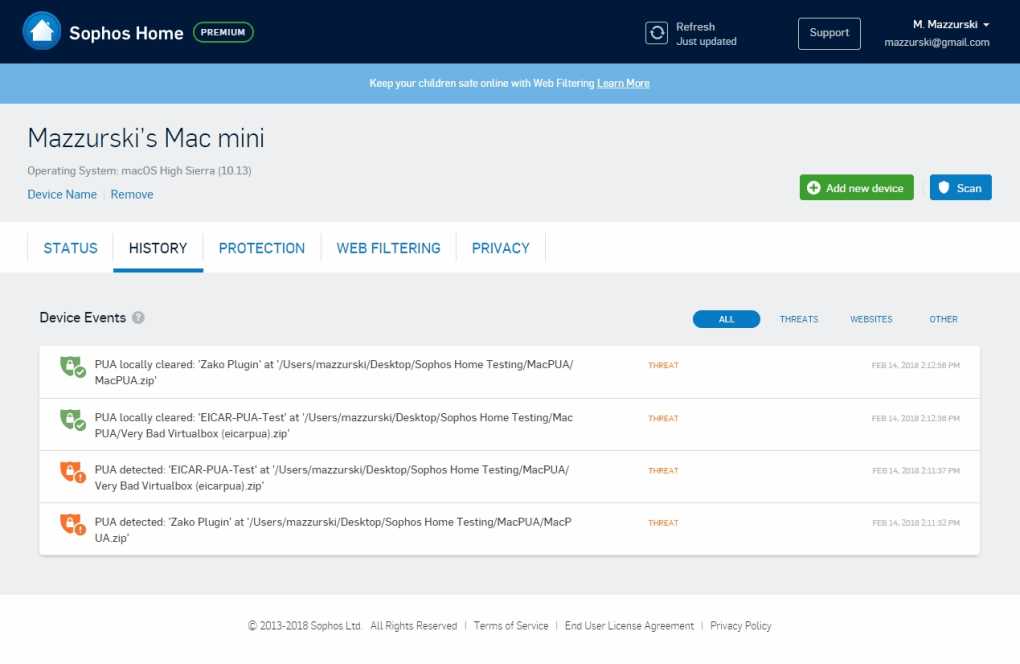
In the realm of modern cybersecurity paradigms, a revolutionary approach emerges, reshaping the landscape of network security. This innovative strategy transcends conventional models, ushering in an era of heightened protection and seamless accessibility.
Embracing a philosophy rooted in skepticism and verification, this transformative concept challenges traditional notions of perimeter defense. Instead of relying solely on fortifying external barriers, it advocates for a dynamic, identity-centric framework.
Within this dynamic ecosystem, the emphasis shifts from securing physical boundaries to safeguarding individual identities and their access privileges. By scrutinizing every access attempt and validating the user’s identity and device integrity, organizations can fortify their defenses against evolving threats.
Through the lens of Zero Trust Network Access (ZTNA), organizations gain granular control over their network resources while empowering users with secure, frictionless access. This paradigm shift heralds a new era of cybersecurity resilience, where trust is earned with every interaction, and security is not a hindrance but an enabler of productivity and innovation.
Understanding Sophos Zero Trust Network Access (ZTNA)
Delving into the realm of modern network security unveils a paradigm shift towards a more discerning approach. Sophos Zero Trust Network Access (ZTNA) represents a pivotal milestone in this evolution, embodying a philosophy of skepticism towards assumed trust within network architectures. By dismantling traditional notions of implicit trust, ZTNA reshapes the landscape of network security, emphasizing verification and validation at every juncture.
- Reimagining Access Control: Instead of relying solely on perimeter defenses, ZTNA adopts a granular approach, scrutinizing each access request irrespective of its origin. This meticulous evaluation ensures that only authorized entities gain entry, bolstering overall security posture.
- Dynamic Policy Enforcement: Unlike static access policies, ZTNA incorporates dynamic rule sets that adapt in real-time to contextual changes. Whether it’s user behavior, device posture, or network conditions, ZTNA remains agile, enforcing tailored policies tailored to the prevailing circumstances.
- Elevating User Experience: Despite its rigorous security mechanisms, ZTNA endeavors to enhance user experience through seamless authentication and transparent access controls. By prioritizing usability without compromising security, ZTNA fosters a conducive environment for productivity and innovation.
- Embracing Zero Trust Principles: At its core, ZTNA embodies the foundational tenets of the Zero Trust model, advocating for continuous verification, least privilege access, and strict segmentation. This holistic approach fortifies networks against evolving threats, mitigating the risk of lateral movement and unauthorized access.
- Unified Visibility and Management: ZTNA converges disparate security functionalities into a unified platform, streamlining administration and bolstering visibility. With centralized management interfaces and comprehensive reporting capabilities, organizations gain unparalleled insights into network activities, facilitating proactive threat mitigation and compliance adherence.
As organizations navigate an increasingly perilous cybersecurity landscape, Sophos Zero Trust Network Access emerges as a beacon of resilience, redefining network security through its unwavering commitment to skepticism and scrutiny. By embracing the principles of Zero Trust, organizations can fortify their defenses, safeguarding critical assets against an array of sophisticated threats.
Understanding the Core Concepts of Zero Trust Network Access (ZTNA)
In this section, we delve into the fundamental principles underpinning the paradigm of Zero Trust Network Access (ZTNA), shedding light on its core concepts and overarching philosophy. Exploring the essence of ZTNA involves a comprehensive examination of its foundational principles, which revolve around redefining traditional network security approaches. Through a lens of continuous verification and strict access controls, ZTNA advocates for a paradigm shift towards a more dynamic, risk-based security model. By fostering a mindset of perpetual skepticism and eliminating implicit trust assumptions, ZTNA aims to fortify organizational defenses against modern cyber threats.
Key Features and Benefits of Advanced Zero Trust Network Access Solution
In this section, we delve into the core components and advantages of our cutting-edge Zero Trust Network Access (ZTNA) solution. Explore the foundational pillars and unique attributes that define the efficacy and value of our innovative platform.
- Granular Access Control: Empower your organization with precise control over user access permissions, ensuring only authorized individuals can interact with critical resources.
- Dynamic Policy Enforcement: Seamlessly adapt access policies based on contextual factors such as user identity, device health, and location, bolstering security without compromising user experience.
- Scalable Architecture: Built to accommodate the evolving needs of modern enterprises, our solution offers scalable deployment options, allowing seamless integration with existing infrastructure.
- Enhanced Visibility: Gain comprehensive visibility into network traffic and user activities, enabling proactive threat detection and swift incident response.
- Reduced Attack Surface: Minimize exposure to potential threats by implementing a Zero Trust framework that verifies every access request, mitigating the risk of lateral movement and data breaches.
- Streamlined Compliance: Facilitate compliance with regulatory standards and industry mandates through robust access controls, audit trails, and reporting capabilities.
- User-Centric Experience: Prioritize user convenience with frictionless access to authorized resources, regardless of device or location, fostering productivity while maintaining security.
- Integration Capabilities: Seamlessly integrate our ZTNA solution with existing security infrastructure and cloud environments, ensuring a cohesive and interoperable security posture.
Implementing Cutting-Edge Zero Trust Network Access: Key Strategies and Insights
In this segment, we delve into the deployment intricacies and strategic maneuvers involved in the integration of advanced Zero Trust Network Access (ZTNA) solutions, offering a comprehensive exploration of optimal approaches and pivotal considerations.
- Establishing Robust Access Policies: Craft meticulous access protocols that align with organizational objectives and security imperatives, ensuring a fortified defense perimeter.
- Layered Authentication Mechanisms: Implement multifaceted authentication layers, incorporating dynamic factors to fortify user verification processes and deter unauthorized access attempts.
- Network Segmentation Strategies: Employ strategic network segmentation tactics to compartmentalize data and resources, mitigating potential breach vectors and enhancing overall network resilience.
- Granular Authorization Protocols: Define granular authorization frameworks to govern resource accessibility based on contextual parameters, bolstering control granularity and minimizing security loopholes.
- Continuous Monitoring and Adaptive Controls: Embrace proactive monitoring mechanisms and adaptive control measures to dynamically respond to evolving threat landscapes and aberrant user behaviors.
By adhering to these meticulously curated strategies and insights, organizations can embark on a transformative journey towards fortified network security and streamlined access governance, fostering a climate of trust and resilience in the digital realm.