
Introduction:
In the realm of technological innovation lies a treasure trove of intricately designed hardware blueprints, each bearing the promise of heightened performance and efficiency. Within this domain, lies a particular document, revered for its comprehensive insights into the capabilities and functionalities of pioneering hardware solutions. This document serves as a guiding light for enthusiasts and professionals alike, offering a detailed glimpse into the prowess encapsulated within the latest advancements in computing infrastructure.
Delving into the intricacies of this compendium unveils a labyrinth of technical intricacies, meticulously crafted to harness the full potential of modern computing paradigms. Through a lens of detailed specifications and performance metrics, one can discern the underlying architecture and design principles that underpin the evolution of hardware innovation.
As we embark on this journey of discovery, we traverse through a landscape teeming with synonyms of power, efficiency, and technological prowess. Through careful examination, we uncover the essence of what propels our digital world forward, transcending mere definitions to embrace the very soul of computational excellence.
The Power Unleashed: Revitalizing Performance

Within the realm of cutting-edge computing solutions lies a formidable force that redefines performance standards and ignites a new era of productivity acceleration. Explore the prowess of a technological marvel that transcends boundaries and elevates the essence of efficiency to unparalleled heights.
Fueling Innovation
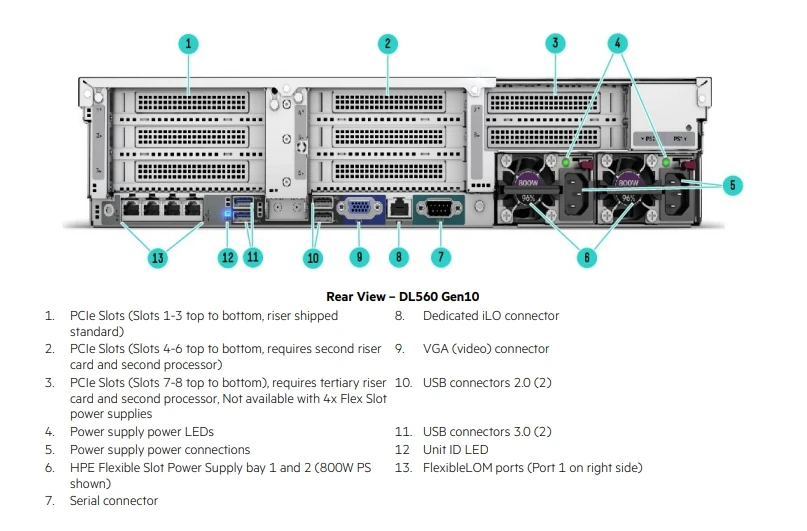
Embark on a journey where computational vigor meets ingenious design, fostering an environment conducive to innovation and advancement. Witness the seamless integration of power and precision, harmonizing to sculpt a masterpiece of engineering ingenuity.
A Symphony of Agility

Experience the symphony of agility as computational capabilities converge with dynamic adaptability, orchestrating a harmonious blend of speed and flexibility. Unleash the full potential of your endeavors with a platform that dances to the rhythm of your ambitions, propelling you towards unparalleled achievements.
Discover the Hardware Innovations

In this section, we delve into the cutting-edge advancements driving the evolution of modern computing hardware. Explore a realm of technological ingenuity where breakthroughs in design, performance, and efficiency redefine the boundaries of possibility. Witness the culmination of relentless research and development efforts, resulting in a symphony of innovation that elevates the user experience to unprecedented heights.
Revolutionary Architectural Enhancements: Embark on a journey through a landscape shaped by pioneering architectural enhancements that revolutionize the very foundation of computing infrastructure. Experience the seamless integration of components optimized for unparalleled synergy, fostering a harmonious ecosystem where every element contributes synergistically to overall performance.
Unprecedented Performance Metrics: Delve into a realm where performance transcends mere benchmarks, where every operation unfolds with unmatched precision and efficiency. Witness the manifestation of breakthrough technologies engineered to shatter barriers, propelling computational capabilities to stratospheric heights while maintaining optimal resource utilization.
Enhanced Security Paradigms: Explore a fortified fortress of digital defense, where robust security measures stand as bastions against an ever-evolving landscape of threats. Embrace a proactive approach to safeguarding data integrity and confidentiality, empowered by a multifaceted arsenal of encryption, authentication, and intrusion detection mechanisms.
Streamlined Management Capabilities: Navigate through a realm of streamlined management capabilities, where the complexities of system administration dissolve into intuitive interfaces and automated workflows. Experience the liberation afforded by centralized control and orchestration, empowering administrators to optimize resource allocation and streamline operational workflows effortlessly.
Exploring Scalability and Flexibility

In this section, we delve into the expansive capabilities and adaptable nature of the system, emphasizing its capacity to grow and adjust to varying demands. Our focus lies on understanding how the architecture accommodates increasing workloads and offers versatility in deployment scenarios.
Scalability Dynamics

Within the realm of expanding operations, the system exhibits a dynamic scalability profile, capable of accommodating diverse workloads without compromising performance or stability. Through efficient resource allocation and utilization, it ensures seamless transitions between different levels of demand, empowering businesses to scale up or down effortlessly.
Flexibility in Deployment
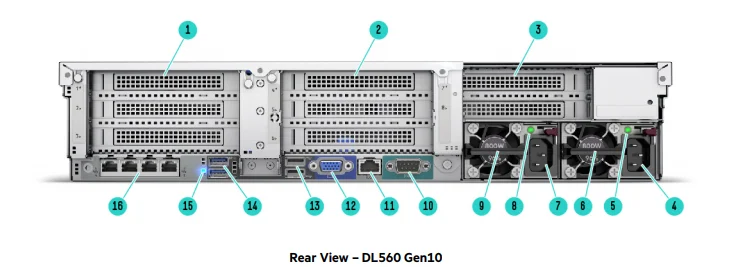
The system’s inherent flexibility extends beyond scalability, enabling versatile deployment options tailored to specific organizational needs. Whether in traditional data center environments, cloud infrastructures, or hybrid setups, its architecture remains adaptable, facilitating smooth integration and operation across diverse platforms.
| Feature | Description |
|---|---|
| Dynamic Resource Allocation | Efficient distribution of resources to meet fluctuating demands. |
| Modular Architecture | Flexible design allowing for easy customization and expansion. |
| Compatibility with Various Environments | Seamless integration with diverse data center setups and cloud platforms. |
Enhanced Security Features of the Latest Generation

In the ever-evolving landscape of digital infrastructure, ensuring robust security measures has become paramount. The latest iteration of server technology introduces a suite of enhanced security features, designed to fortify the integrity and confidentiality of sensitive data.
Advanced Encryption Capabilities

One of the cornerstones of modern data security is encryption, the process of encoding information to render it indecipherable to unauthorized parties. The DL560 Gen10 incorporates advanced encryption mechanisms, bolstering data protection from end to end. Through the utilization of cutting-edge cryptographic algorithms, sensitive data is shielded both in transit and at rest, mitigating the risks posed by potential breaches.
Intelligent Threat Detection

Recognizing the dynamic nature of cyber threats, the DL560 Gen10 integrates intelligent threat detection capabilities. Leveraging sophisticated algorithms and machine learning algorithms, this system continuously monitors for anomalous activities and potential intrusions. By proactively identifying and mitigating security threats in real-time, organizations can maintain the integrity of their infrastructure and safeguard critical assets.
In essence, the DL560 Gen10 represents a paradigm shift in the realm of server security. By embracing advanced encryption techniques and intelligent threat detection mechanisms, it empowers organizations to navigate the complexities of the digital landscape with confidence and resilience.
Fortifying Data Protection Mechanisms
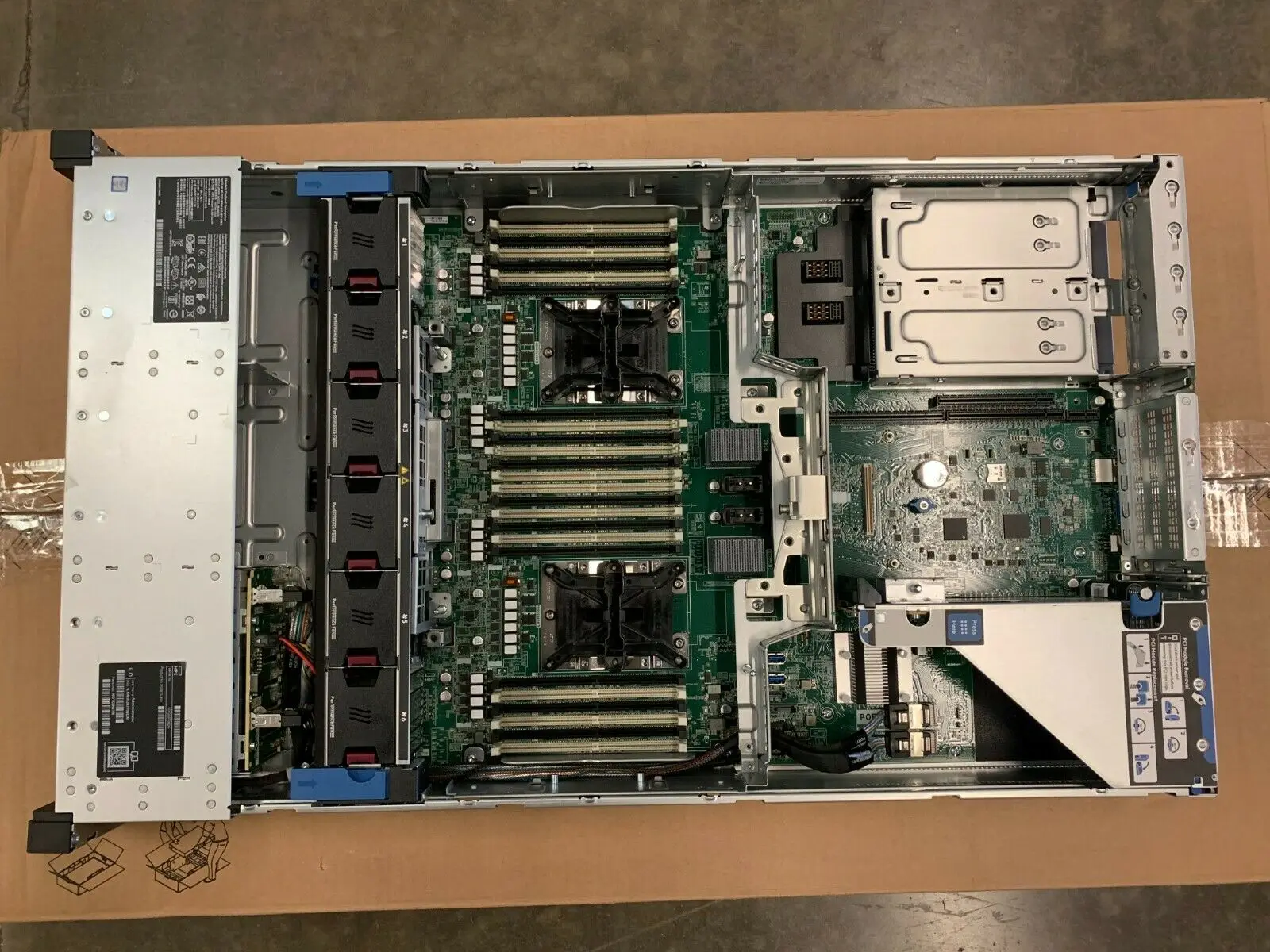
In the realm of digital security, safeguarding sensitive information is paramount. This section delves into strategies and technologies aimed at enhancing the resilience of data protection mechanisms. By implementing robust protocols and leveraging advanced encryption techniques, organizations can bolster their defenses against unauthorized access and data breaches.
Encryption Protocols

One cornerstone of fortifying data protection lies in the deployment of encryption protocols. These protocols serve as a barrier, rendering data indecipherable to unauthorized parties. By employing sophisticated encryption algorithms and key management strategies, organizations can ensure that even if data is intercepted, it remains unreadable and secure.
Access Control Measures

Another vital aspect of fortifying data protection involves implementing stringent access control measures. By regulating who can access sensitive data and under what circumstances, organizations can minimize the risk of unauthorized breaches. Access control mechanisms encompass various techniques, including role-based access control (RBAC), multi-factor authentication (MFA), and biometric verification, ensuring that only authorized personnel can interact with sensitive information.
| Technology | Description |
|---|---|
| Tokenization | Replacing sensitive data with non-sensitive placeholders, reducing the risk of exposure. |
| Data Masking | Concealing specific data elements within a dataset, allowing for safe data sharing without compromising confidentiality. |
| Secure Socket Layer (SSL) | Establishing encrypted links between servers and clients, ensuring secure data transmission over networks. |