
Embark on a journey towards fortified fortification with a suite of cutting-edge measures designed to bolster your digital stronghold. Explore the realm of heightened safeguarding as we delve into the intricacies of an evolved shield, offering an array of robust solutions to fortify your digital perimeter.
Discover a realm where threats are met with resilience and vulnerabilities transformed into strengths. Engage with a panorama of security enhancements meticulously crafted to not only defend but also empower your network infrastructure. Through this exploration, navigate the labyrinth of possibilities, where proactive defense meets agile adaptation.
Unveil the veil of uncertainty, as we dissect the anatomy of resilience, layer by layer. Traverse through a landscape where risk is mitigated, and resilience reigns supreme. Through insightful analysis and comprehensive breakdowns, equip yourself with the knowledge to navigate the ever-evolving landscape of digital security with confidence.
Exploring Enhanced Protection Features in Meraki
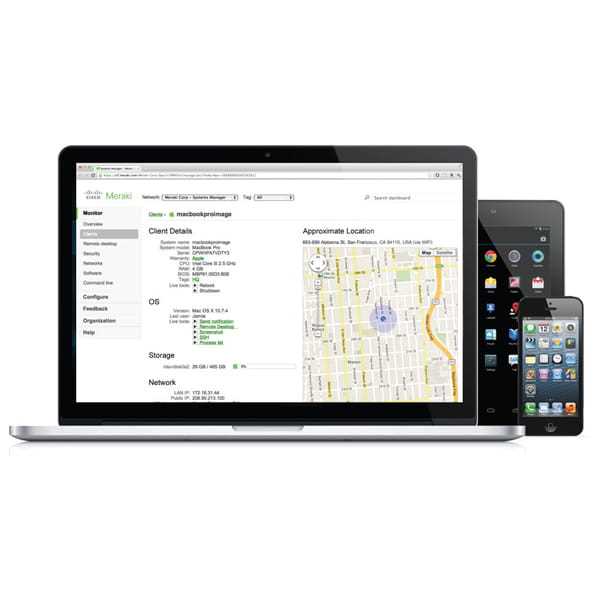
Delve into the advanced capabilities that fortify your network infrastructure with an array of sophisticated defense mechanisms. Unveil a spectrum of robust safeguards meticulously engineered to shield your digital assets from emerging threats and vulnerabilities.
- Dynamic Threat Intelligence: Gain insights into a dynamic repository of threat intelligence, empowering your network with real-time awareness of evolving hazards and malicious activities.
- Behavioral Analysis: Harness the power of behavioral analysis algorithms to discern anomalous patterns and preemptively neutralize potential security breaches before they infiltrate your network.
- Integrated Firewall Solutions: Explore seamlessly integrated firewall solutions that erect formidable barriers against unauthorized access attempts, preserving the sanctity of your digital perimeter.
- Intrusion Prevention Systems: Dive into proactive defense mechanisms designed to intercept and thwart intrusion attempts, ensuring the integrity and confidentiality of your sensitive data.
- Secure VPN Connectivity: Facilitate secure remote access and seamless connectivity through encrypted VPN tunnels, safeguarding data transmissions across disparate networks.
Embark on a journey through the intricate architecture of Meraki’s advanced security features, where innovation converges with resilience to establish a bastion of protection against contemporary cyber threats.
The Comprehensive Security Suite

Within the realm of digital protection lies a robust arsenal designed to fortify your online presence against a myriad of threats. This suite, meticulously curated to safeguard your digital assets, embodies a holistic approach to shielding your network from malicious intrusions and ensuring the integrity of your data. Delving into its components unveils a tapestry of defenses meticulously woven to intercept, analyze, and neutralize potential hazards lurking in the digital landscape.
Unified Threat Management (UTM)

At the forefront of this comprehensive defense system stands Unified Threat Management, a sentinel vigilantly standing guard against a spectrum of perils. With a seamless integration of various security functions, UTM orchestrates a symphony of measures, encompassing firewall protection, intrusion detection, and content filtering. Its unified approach not only simplifies management but also amplifies the efficacy of your defense strategy.
Vigilant Surveillance Mechanisms

Bolstering the fortifications are vigilant surveillance mechanisms, ceaselessly scanning the digital horizons for signs of impending danger. Equipped with advanced anomaly detection algorithms and heuristic analysis, these mechanisms proactively identify and thwart emerging threats before they can wreak havoc. By fostering a proactive stance, they instill confidence in your network’s resilience, ensuring uninterrupted operations even in the face of evolving adversarial tactics.
- Dynamic Threat Intelligence
- Behavioral Analytics
- Real-time Monitoring
This suite epitomizes a commitment to proactive defense, empowering you to navigate the digital realm with confidence and peace of mind.
Enhanced Threat Intelligence Integration

Within the realm of bolstering security prowess, a paramount focus emerges on fortifying defenses against evolving threats. This segment delves into the seamless amalgamation of cutting-edge threat intelligence into the system architecture, fostering a proactive shield against malicious incursions.
Strategic Fusion
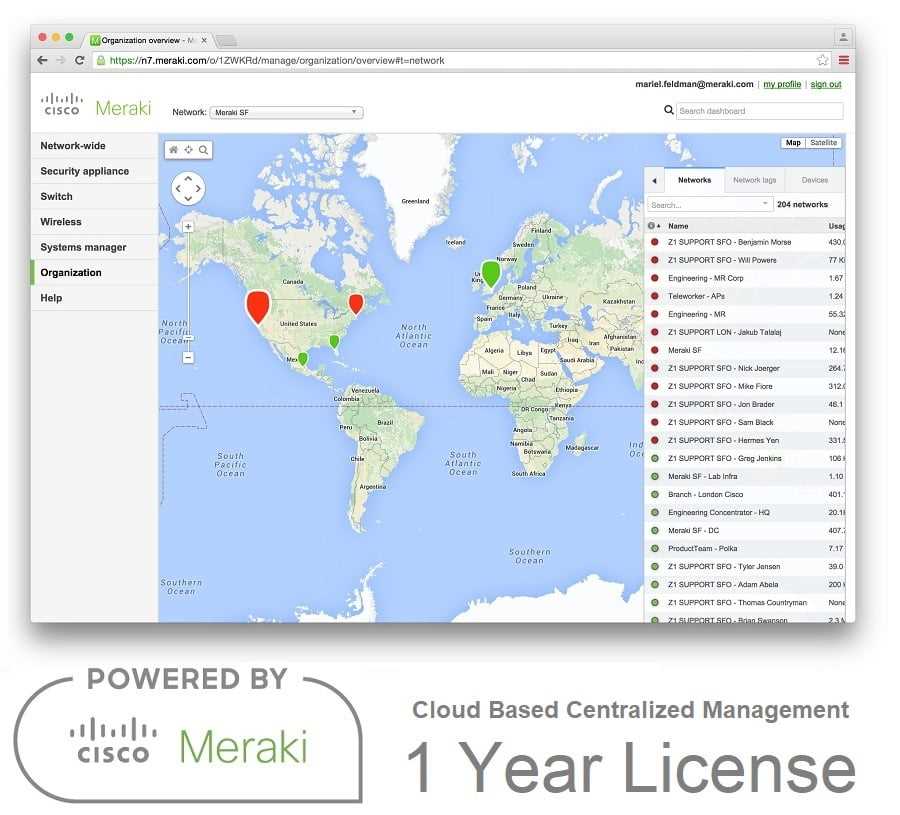
Harmonizing intricate threat data streams with the operational fabric, this integration transcends mere vigilance, orchestrating a symphony of preemptive actions. By assimilating diverse threat intelligence feeds, the system elevates its discernment, sculpting a panoramic view of potential vulnerabilities.
Dynamic Response Mechanisms

Not confined to passive scrutiny, the system propels forward with agile response mechanisms, sculpted by real-time analysis and predictive algorithms. Seamlessly blending reactive measures with proactive anticipation, it erects a robust bulwark against nascent threats, perpetually adapting to the evolving threat landscape.
Streamlined Security Management Capabilities

In this section, we delve into the array of features designed to simplify and enhance the oversight and administration of security measures within your network infrastructure. We explore the tools and functionalities engineered to streamline the supervision and control of protective protocols, ensuring efficiency and efficacy across your digital environment.
|
Centralized Command Center: Gain access to a unified dashboard serving as the nerve center for all security-related operations. From this centralized interface, administrators can seamlessly orchestrate and monitor various security parameters, optimizing resource allocation and response times. |
|
Intuitive Policy Management: Employ an intuitive policy management system, facilitating the creation, modification, and enforcement of security policies across the network ecosystem. This user-friendly interface empowers administrators to swiftly adapt to evolving threats and compliance requirements. |
|
Automated Threat Detection: Harness the power of automated threat detection mechanisms, which employ advanced algorithms to proactively identify and mitigate potential security risks. By automating this critical aspect of security management, organizations can bolster their defenses and preemptively thwart malicious activities. |
|
Real-time Monitoring and Alerts: Stay informed and vigilant through real-time monitoring and alerts, enabling prompt responses to security incidents as they unfold. Administrators receive instant notifications of suspicious activities, allowing for immediate investigation and remediation to safeguard network integrity. |