
In the realm of cybersecurity documentation, the vermillion dossier emerges as a pivotal instrument, offering a comprehensive elucidation of protective mechanisms and digital fortifications. This compendium serves as a beacon, illuminating the labyrinthine corridors of virtual security with its nuanced insights and strategic delineations.
Within its pages, one navigates through a tapestry of discernment, where the intricacies of safeguarding digital perimeters are unveiled. Each section, suffused with meticulous detail and empirical analysis, begets a profound understanding of the contemporary cyber landscape, permeated by ever-evolving threats and clandestine incursions.
The narrative woven within these cryptographic chronicles transcends mere technical explication, embracing a holistic approach to fortification. It beckons both neophytes and seasoned guardians alike, fostering a symbiotic relationship between knowledge and vigilance, thereby fostering a collective defense against the specter of digital malfeasance.
Synopsis of the Document on Scarlet Solution
In this section, we delve into the comprehensive portrayal of the innovative solution encapsulated within the presented documentation. It unfolds a narrative that navigates through the intricacies of a cutting-edge technology devised to fortify networks and ensure seamless connectivity. Herein lies an exploration of functionalities, features, and the overarching vision guiding the development of this transformative solution.
Key Features
- Advanced Network Fortification Mechanisms
- Seamless Connectivity Enhancements
- Robust Security Protocols
Core Objectives
- Augmenting Network Resilience
- Facilitating Secure Data Transmission
- Streamlining Connectivity Across Diverse Environments
This segment provides a glimpse into the essence of the forthcoming discourse, laying the groundwork for a comprehensive understanding of the intricacies and implications encapsulated within.
Understanding Sophos Red Devices
In this section, we delve into comprehending the essence of the innovative solutions provided by Sophos in their suite of connectivity enhancement tools. These devices, identified by their distinctive hue, serve as pivotal components in fortifying network infrastructures, ensuring seamless integration and heightened security measures.
- Introduction to Sophos Red Devices
- Functionality Overview
- Deployment Strategies
- Key Features and Benefits
- Integration Capabilities
Embarking on a journey to grasp the intricacies of Sophos Red Devices involves exploring their fundamental purposes, operational frameworks, and strategic implementations. By dissecting their functionalities and discerning their significance within network architecture, one can unravel the efficacy and versatility these devices offer in diverse organizational contexts.
Key Features and Benefits
In this section, we delve into the core functionalities and advantages offered by our product, emphasizing its prowess in enhancing security and efficiency for users. Discover the array of capabilities designed to fortify your digital environment while streamlining operations, empowering your business to thrive in the dynamic landscape of cybersecurity.
Robust Security Measures
- Advanced threat detection and mitigation mechanisms
- Comprehensive firewall protection
- Real-time monitoring and response to security incidents
- Encrypted communication channels for heightened privacy
- Vigilant malware and ransomware defense
Enhanced Operational Efficiency
- Intuitive user interface for seamless navigation
- Automated updates and patch management
- Centralized management console for simplified administration
- Scalable solutions adaptable to diverse business environments
- Optimized performance to minimize downtime and maximize productivity
Experience the amalgamation of cutting-edge technology and user-centric design, culminating in a solution poised to elevate your security posture and operational effectiveness.
Deployment Scenarios for Network Security Solution

In this section, we explore various strategies for implementing and utilizing the network security solution, delving into diverse setups and configurations to cater to different organizational needs and infrastructural complexities.
1. Remote Office Connectivity
One prevalent scenario involves establishing secure connections for remote offices, ensuring seamless integration with the main network infrastructure while maintaining robust security measures. This deployment caters to organizations with distributed teams or branch offices seeking to uphold consistent protection standards across their network.
2. Mobile Workforce Support

Another critical aspect is accommodating the needs of a mobile workforce, where employees require secure access to network resources from various locations and devices. This deployment scenario focuses on providing flexible yet stringent security measures to safeguard data and communications amidst dynamic working environments.
- Secure VPN Connectivity
- Endpoint Protection
- Centralized Management
By implementing these deployment scenarios effectively, organizations can fortify their network infrastructure against a multitude of threats, ensuring both accessibility and security remain paramount.
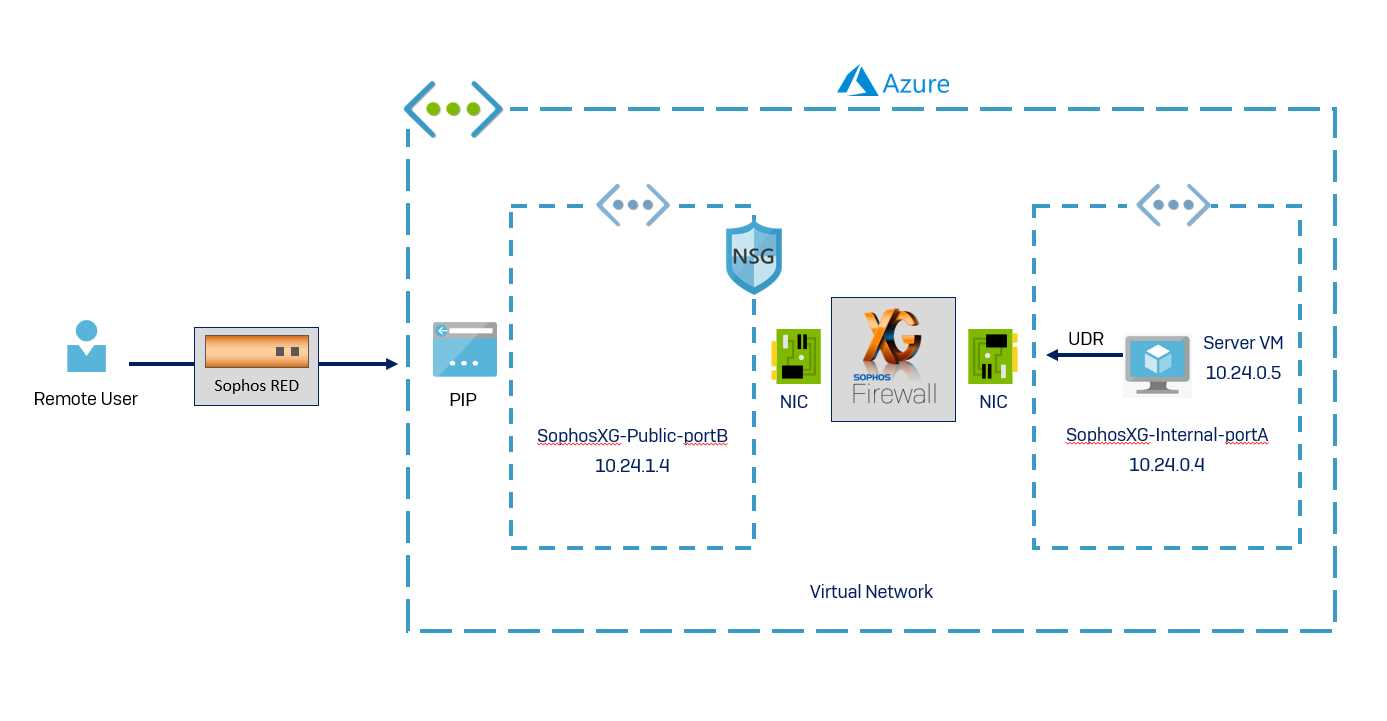
Remote Office Security Solutions
In the realm of safeguarding distributed work environments, ensuring the integrity of data and fortifying network perimeters are paramount considerations. This section delves into comprehensive strategies and tools designed to fortify the security posture of remote offices, mitigating potential vulnerabilities and bolstering defenses against evolving cyber threats.
Enhanced Endpoint Protection
Endpoint security solutions play a pivotal role in fortifying the security landscape of remote offices. By implementing robust endpoint protection mechanisms, organizations can thwart malicious infiltration attempts and prevent unauthorized access to sensitive data. These solutions encompass a suite of technologies, including antivirus software, firewalls, and intrusion detection systems, collectively forming a formidable defense line against cyber threats.
Secure Connectivity Infrastructure

Establishing a secure connectivity infrastructure is imperative for ensuring seamless and protected communication between remote offices and central networks. Utilizing virtual private networks (VPNs) and encrypted communication protocols facilitates secure data transmission over public networks, safeguarding confidential information from interception or tampering. Additionally, deploying multi-factor authentication mechanisms adds an extra layer of defense, fortifying access controls and thwarting unauthorized entry.