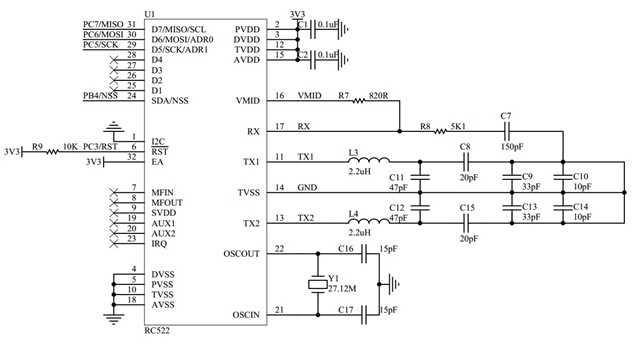
Unlocking the potential of modern electronic systems often hinges on understanding the intricacies of fundamental components. In the realm of embedded systems and RFID technology, there exists a pivotal element that serves as the cornerstone of many innovations. Delving into the intricacies of this component unveils a world of possibilities, where data transmission, authentication, and connectivity converge.
Within the realm of electronic engineering, there lies a component that embodies versatility and innovation. Its capabilities extend beyond mere identification; it forms the backbone of secure communication protocols and authentication mechanisms. Through meticulous exploration and analysis, the essence of this component emerges, revealing a tapestry of functionality and application.
Embarking on a journey to unravel the mysteries of this foundational element leads us down a path of discovery. As we navigate through technical specifications and operational principles, we encounter a fusion of engineering brilliance and practical utility. Each facet of this component contributes to a broader understanding of its role in shaping modern technology.
Join us as we embark on an expedition into the realm of electronic components, where innovation meets functionality and curiosity sparks exploration. Together, we will unravel the essence of this fundamental building block, exploring its applications, challenges, and potential in the ever-evolving landscape of electronic engineering.
Rc522 Datasheet: Understanding the Essentials

In the realm of RFID technology, delving into the intricacies of component specifications can unveil a world of possibilities. This section aims to dissect the fundamental aspects of the RC522 module, shedding light on its core functionalities and operational principles.
Core Components Overview
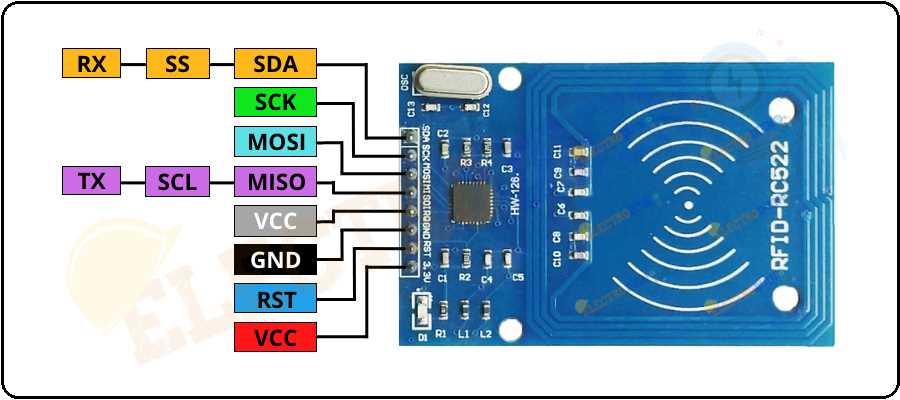
Before diving into the specifics, it’s crucial to grasp the foundational elements that constitute the RC522 module. Understanding the core components sets the stage for comprehending its functionalities and potential applications.
- Transceiver Unit: This pivotal component facilitates communication between the RFID reader and tags, enabling data exchange through radio frequency signals.
- Control Interface: Serving as the brain of the module, the control interface manages data flow, configuration settings, and interaction with external systems.
- Antenna: The antenna plays a pivotal role in transmitting and receiving RF signals, establishing the vital link between the RC522 module and RFID tags.
Operational Principles
Unlocking the mysteries behind the RC522 module involves grasping its operational principles. By deciphering how it interacts with RFID tags and processes data, users can harness its potential for various applications.
- Tag Detection: The RC522 module employs sophisticated algorithms to detect nearby RFID tags, initiating communication upon identification.
- Data Exchange: Through a series of predefined protocols, the RC522 module exchanges data with compatible RFID tags, facilitating information retrieval and storage.
- Security Features: With built-in encryption and authentication mechanisms, the RC522 module ensures data integrity and protects against unauthorized access, bolstering security in RFID applications.
By unraveling the essentials of the RC522 module, enthusiasts and professionals alike can embark on a journey of innovation, leveraging its capabilities to craft innovative solutions in the realm of RFID technology.
Exploring the Key Features and Specifications
In this section, we delve into the essential characteristics and technical details that define the functionality and performance of the device under scrutiny. Through a comprehensive examination, we aim to uncover the intrinsic qualities and operational capabilities that distinguish this technology in the realm of embedded systems and sensor applications. From fundamental attributes to intricate specifications, we traverse the landscape of features that contribute to the overall functionality and versatility of this cutting-edge component.
Performance Metrics: Delving into the operational benchmarks and metrics that gauge the efficacy and efficiency of this device, we unveil the performance parameters that underpin its functionality. From throughput rates to response times, these metrics provide invaluable insights into the device’s ability to meet the demands of diverse applications.
Functional Capabilities: Exploring the myriad functions and capabilities encoded within the architecture of this component, we uncover the breadth and depth of its operational repertoire. From data acquisition to signal processing, each function plays a pivotal role in shaping the device’s utility across a spectrum of use cases.
Interface Specifications: Investigating the interface specifications that govern the interaction between the device and external systems, we elucidate the protocols and standards that facilitate seamless integration and interoperability. Whether through serial communication or wireless connectivity, these specifications delineate the pathways through which data flows and commands are exchanged.
Power Management: Delving into the power management mechanisms embedded within the device, we examine the strategies employed to optimize energy consumption and prolong operational lifespan. From standby modes to dynamic power scaling, these mechanisms play a crucial role in balancing performance with energy efficiency.
Security Features: Unveiling the security measures implemented within the device to safeguard sensitive data and mitigate potential threats, we explore the encryption protocols and authentication mechanisms that fortify its resilience against malicious activities. Through robust security features, the device ensures the integrity and confidentiality of transmitted information.
Environmental Considerations: Addressing the environmental factors that influence the device’s performance and reliability, we assess its suitability for operation across diverse conditions and environments. From temperature tolerance to moisture resistance, these considerations inform the deployment and longevity of the device in real-world scenarios.
Unlocking the Potential: Applications of RFID Module

In this section, we explore the diverse range of applications that can be realized through the utilization of the RFID module. From enhancing security measures to streamlining access control systems, the versatility of this technology extends far beyond its conventional use.
|
Access Control Systems: One of the primary applications of the RFID module lies in access control systems. By integrating this technology, organizations can bolster security protocols, allowing for seamless and efficient authentication processes. |
Asset Tracking: Another noteworthy application is in asset tracking. Whether it’s monitoring inventory in a warehouse or tracking valuable equipment in a facility, the RFID module provides real-time visibility and ensures efficient management of resources. |
|
Identification and Authentication: Furthermore, the RFID module can be instrumental in identification and authentication systems. From employee identification badges to passport verification, this technology offers a reliable means of verifying identity. |
Supply Chain Management: In the realm of supply chain management, the RFID module plays a crucial role in optimizing logistics operations. By tagging products and shipments with RFID labels, businesses can track items throughout the supply chain, enhancing visibility and minimizing errors. |
|
Payment Systems: Moreover, the RFID module can revolutionize payment systems, enabling contactless transactions for enhanced convenience and security. From public transportation fare collection to cashless payments at events, this technology simplifies the payment process for consumers. |
Smart Manufacturing: In the domain of smart manufacturing, the RFID module facilitates automation and efficiency. By incorporating RFID tags into production processes, manufacturers can monitor and track work-in-progress, optimize inventory management, and ensure product quality. |
These are just a few examples of the myriad applications that underscore the transformative potential of the RFID module. As technology continues to evolve, so too will the innovative ways in which this versatile tool can be employed to address diverse challenges and enhance various aspects of our lives.
Real-world Implementations and Case Studies
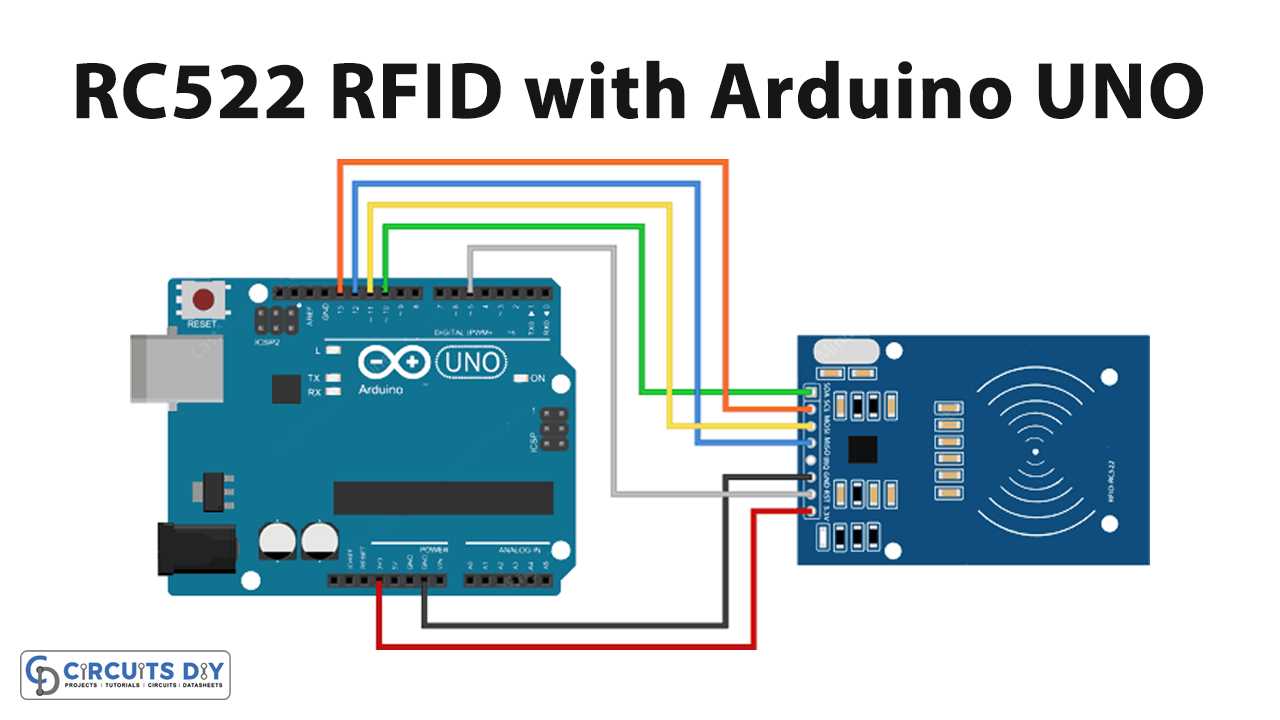
In this section, we explore practical applications and real-life scenarios where the technology described in the aforementioned documentation finds meaningful utilization. Through case studies and empirical evidence, we delve into instances where this innovative technology has been integrated seamlessly into various contexts, showcasing its versatility and efficacy.
- Examining the integration of the technology into access control systems within corporate environments, highlighting its role in enhancing security protocols while streamlining user authentication processes.
- Exploring its utilization in public transportation systems to facilitate efficient ticketing and fare collection, leading to improved passenger experience and operational efficiency.
- Analyzing its application in inventory management systems across retail and logistics sectors, elucidating its contribution to inventory tracking accuracy and supply chain optimization.
- Investigating its role in healthcare settings, particularly in patient identification and medical records management, emphasizing its impact on enhancing patient care and data security.
- Delving into its deployment in IoT (Internet of Things) solutions, illustrating how it enables seamless connectivity and communication between devices, paving the way for the realization of smart environments and automation.
Through these diverse case studies, we aim to provide insights into the real-world implementations of this technology, shedding light on its practical significance and potential for driving innovation across various domains.
Optimizing Performance: Tips and Tricks
In the pursuit of enhancing operational efficiency and maximizing system capabilities, it’s imperative to delve into techniques that elevate overall performance. This section delves into various strategies and methodologies aimed at refining the functionality and responsiveness of electronic components, without explicitly referring to specific technical documents or product specifications.
1. Streamlining Communication Protocols:
Efficient data exchange lies at the heart of seamless operations. Explore methods to optimize communication protocols, ensuring swift and reliable transmission of information between components.
2. Fine-Tuning Operational Parameters:
Delve into the intricacies of system configurations and parameters, seeking opportunities to fine-tune settings for optimal performance. Adjusting parameters such as timing intervals and signal thresholds can significantly enhance overall efficiency.
3. Implementing Intelligent Power Management:
Power consumption plays a pivotal role in the performance equation. Employ intelligent power management techniques to minimize energy wastage while maintaining operational integrity. This may involve strategies such as dynamic power scaling and sleep modes.
4. Optimizing Data Processing Algorithms:
Efficient data processing forms the backbone of responsive systems. Explore algorithms and data structures conducive to swift computation and minimal resource utilization. Optimization in this realm can lead to significant performance gains.
5. Enhancing Error Handling Mechanisms:
Robust error handling mechanisms are paramount for maintaining system resilience. Develop strategies to efficiently identify, isolate, and address errors, ensuring uninterrupted operation even in challenging environments.
6. Leveraging Hardware Acceleration:
Harness the full potential of hardware capabilities through strategic utilization of acceleration techniques. Offloading computational tasks to specialized hardware accelerators can expedite processing and alleviate strain on the primary processing unit.
7. Prioritizing Resource Allocation:
Resource allocation plays a crucial role in multitasking environments. Prioritize resource allocation based on task criticality and system requirements, optimizing performance by allocating resources judiciously.
8. Conducting System-Level Profiling:
Gain insights into system behavior through comprehensive profiling. Identify bottlenecks and inefficiencies by analyzing performance metrics at various levels of abstraction, facilitating targeted optimizations for maximal impact.
By implementing these diverse strategies and embracing a holistic approach to performance optimization, developers can unlock the full potential of electronic components, fostering systems that excel in responsiveness, efficiency, and reliability.