Empowering your digital fortress, this comprehensive guide delves into the intricacies of fortifying your online infrastructure against a myriad of cyber threats. Within these pages, discover a wealth of insights aimed at bolstering the resilience of your web assets, safeguarding sensitive data, and preserving the integrity of your digital presence.
Explore innovative strategies designed to shield your web applications from the relentless onslaught of malicious actors seeking to exploit vulnerabilities for nefarious purposes. From advanced threat detection mechanisms to robust defensive protocols, embark on a journey towards a fortified digital ecosystem where security is paramount.
Unravel the complexities of modern cybersecurity challenges and equip yourself with the knowledge needed to navigate the ever-evolving threat landscape. Through meticulous analysis and actionable recommendations, navigate the nuances of safeguarding your online assets with confidence and efficacy.
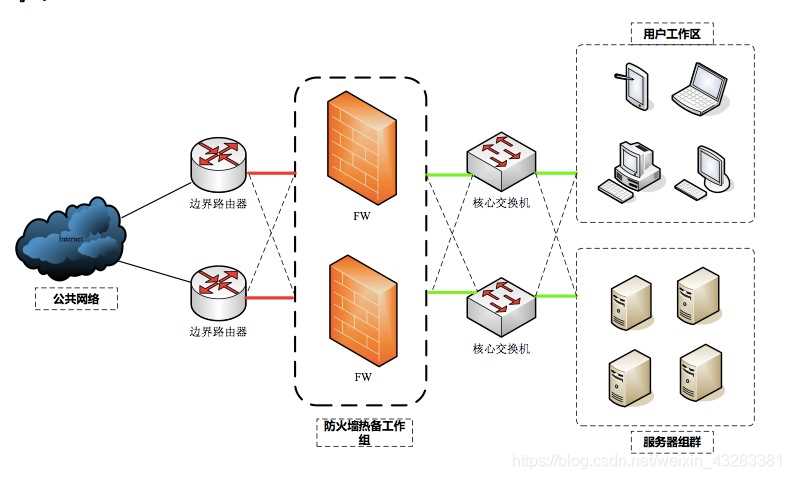
Understanding Radware’s Web Application Firewall (WAF) Offering

In this section, we delve into the core principles and functionalities of Radware’s robust security solution tailored for safeguarding web applications. Through a comprehensive examination, we aim to illuminate the intricacies and benefits of this innovative protective shield.
The Essence of Web Application Security

Before delving into the specifics of Radware’s solution, it’s imperative to grasp the fundamental essence of web application security. In today’s digital landscape, where online threats loom large, safeguarding web applications against malicious attacks is paramount. Organizations must fortify their digital infrastructure to ensure the integrity, confidentiality, and availability of their online assets.
Unraveling the Layers of Protection

Radware’s WAF solution operates as a multifaceted defense mechanism, employing a sophisticated array of techniques to shield web applications from a plethora of cyber threats. By meticulously analyzing web traffic patterns, detecting anomalies, and deploying proactive measures, Radware’s solution fortifies digital assets against a diverse range of attacks, including but not limited to SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) assaults.
Stay tuned as we navigate through the nuanced layers of Radware’s WAF solution, shedding light on its advanced features, proactive security measures, and unparalleled efficacy in safeguarding web applications against evolving cyber threats.
The Evolution of Web Application Security
In the realm of safeguarding web applications, a dynamic narrative unfolds, tracing the trajectory of fortification measures from their nascent stages to contemporary sophistication. This journey delves into the metamorphosis of defensive strategies, highlighting pivotal milestones in the perpetual arms race against digital threats.
Early Defenses: Foundations of Protection
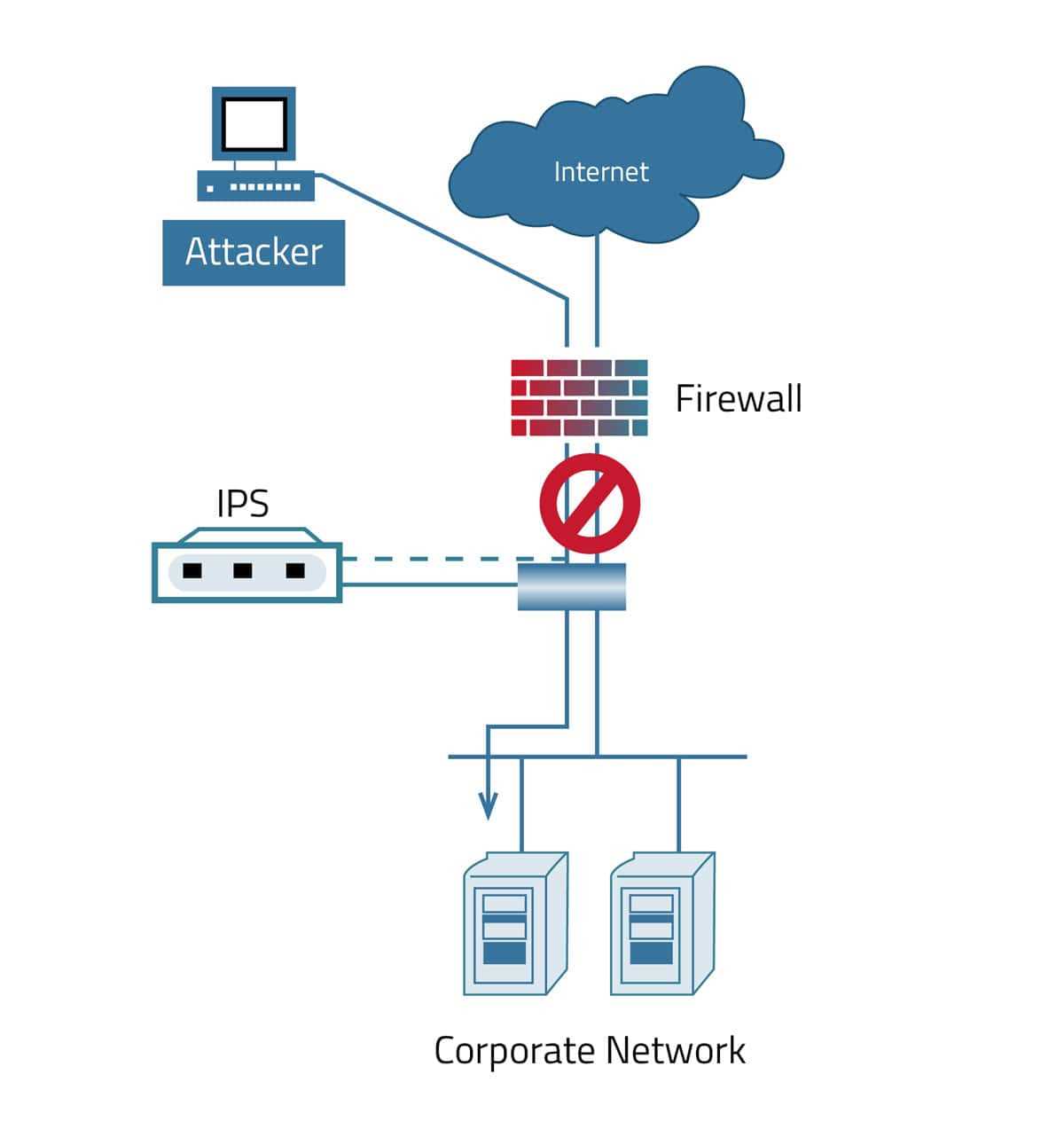
Initially, web application security revolved around rudimentary barricades, akin to primitive ramparts shielding vulnerable citadels. Basic measures such as input validation and access controls formed the cornerstone, erecting a semblance of defense against incursions.
Advancements and Adaptations: Responding to Emerging Threats

As cyber assailants honed their arsenals, necessitating more robust fortifications, the landscape of web application security witnessed a rapid evolution. Innovations in encryption, intrusion detection, and behavioral analysis emerged as bulwarks against the evolving spectrum of attacks.
| Epoch | Milestone | Significance |
|---|---|---|
| 1990s | Introduction of Firewalls | Initiated the paradigm shift towards network-centric security. |
| 2000s | Rise of Web Application Firewalls (WAFs) | Elevated protection to the application layer, offering granular defense. |
| 2010s | Advent of Machine Learning | Enabled proactive threat mitigation through predictive algorithms. |
This HTML section outlines the evolution of web application security, tracing its journey from rudimentary defenses to modern-day adaptive strategies. It includes two subsections highlighting early defenses and advancements, along with a tabulated summary of significant milestones.
Key Features and Benefits of Cutting-Edge Web Application Firewall

Within the realm of advanced cyber-defense solutions, there exists a shield designed to fortify your digital assets against an array of online threats. This sophisticated Web Application Firewall (WAF) boasts an arsenal of features tailored to safeguarding your web infrastructure and ensuring uninterrupted operations.
| Feature | Benefit |
| Comprehensive Threat Detection | Identify and neutralize malicious activities targeting your web applications with precision. |
| Intelligent Attack Mitigation | Employ proactive measures to thwart cyber attacks before they infiltrate your network, preserving data integrity and user trust. |
| Customizable Security Policies | Adapt the firewall’s defenses to align with your organization’s specific security requirements, ensuring tailored protection. |
| Real-time Traffic Monitoring | Stay vigilant against evolving threats by continuously monitoring incoming and outgoing web traffic for anomalies. |
| Scalable Performance | Effortlessly accommodate increasing traffic volumes without compromising on security or performance, ensuring seamless scalability. |
| Compliance Assistance | Facilitate adherence to industry regulations and standards by implementing features designed to support compliance efforts. |
From proactive threat detection to adaptive security policies, this innovative WAF empowers organizations to navigate the digital landscape with confidence, safeguarding their assets and reputation against emerging cyber threats.
Implementing Advanced Web Application Firewall: Optimal Strategies and Key Considerations

When integrating an advanced web application firewall solution into your infrastructure, several pivotal factors demand careful attention to ensure seamless deployment and optimal performance. This section delineates essential strategies and considerations for implementing an advanced web application firewall effectively.
First and foremost, the deployment strategy plays a critical role in determining the efficacy of the solution. Whether opting for inline or out-of-band deployment, understanding your network architecture and traffic patterns is paramount. This comprehension facilitates the strategic placement of the firewall to intercept and inspect web traffic comprehensively.
Moreover, configuring appropriate security policies constitutes another fundamental aspect of implementation. Crafting granular policies tailored to your organization’s specific requirements ensures precise threat detection and mitigation while minimizing false positives. Striking the right balance between stringent security measures and operational efficiency is imperative.
Furthermore, ongoing monitoring and fine-tuning are indispensable components of a robust implementation strategy. Continuous analysis of traffic patterns, threat landscapes, and system performance enables proactive adjustments to security policies and configurations, bolstering the firewall’s effectiveness in combating emerging threats.
Additionally, seamless integration with existing security infrastructure is vital for optimizing overall security posture. Ensuring compatibility with other security tools and platforms fosters a cohesive security ecosystem, streamlining threat detection and response mechanisms.
Lastly, user awareness and training constitute an often-overlooked yet crucial aspect of successful implementation. Educating personnel about the firewall’s capabilities, proper usage, and potential security risks empowers them to act as vigilant guardians of the organization’s digital assets, augmenting the overall efficacy of the security infrastructure.