
Exploring the heart of cutting-edge networking technology, this section delves into the intricacies of a pivotal document that serves as a roadmap to innovation. Dive into a realm where functionality meets form, where specifications dance with potential, and where insight transforms into action. Within these pages lies a blueprint that illuminates the capabilities of a pioneering apparatus, offering a glimpse into its prowess and promise.
Embark on a journey of discovery as we navigate through a trove of information designed to elucidate the essence of groundbreaking infrastructure. Uncover the essence of connectivity as we traverse through descriptions that encapsulate the essence of performance, resilience, and adaptability. Immerse yourself in a narrative woven with technical expertise and visionary design, where each paragraph unveils a facet of a marvel that shapes the digital landscape.
Prepare to be captivated as we peel back the layers of jargon to reveal the core components that underpin the seamless functioning of advanced networking systems. Through the lens of this document, witness the fusion of innovation and reliability, where every specification carries the weight of possibility and progress. Join us in deciphering the language of transformation, as we decode the essence of a document that serves as a gateway to the future of networking.
Understanding the QFX10008 Specifications: Core Features Deciphered
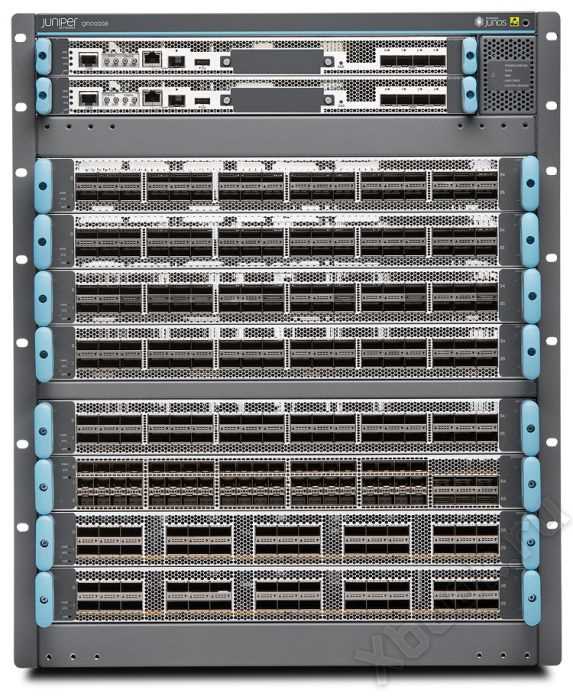
In this segment, we delve into the intricate details of the cornerstone specifications of the high-performance networking marvel, unveiling its essence beyond mere technicalities. Embark on a journey through its foundational elements, dissecting the quintessence that propels modern connectivity forward.
- Performance Prowess: Unveiling the prowess of its performance metrics
- Scalability Secrets: Unraveling the scalability features for seamless expansion
- Reliability Realm: Exploring the domain of reliability mechanisms ensuring uninterrupted operations
- Connectivity Chronicles: Tracing the path of connectivity options for diverse networking needs
Peer into the realm of cutting-edge networking solutions as we decipher the core tenets defining the epitome of technological innovation.
Exploring the Hardware Architecture and Performance Metrics
In this section, we delve into the intricate framework and operational efficiencies of the cutting-edge network infrastructure. Our focus is to dissect the underlying hardware architecture, unraveling its sophisticated design elements, and elucidate the intricate interplay of components that orchestrate seamless data transmission. Additionally, we scrutinize the performance metrics, meticulously evaluating the system’s throughput, latency, and scalability, thereby painting a comprehensive picture of its operational prowess and potential.
Unveiling the Hardware Fabric: Embark on a journey through the heart of the network, where intricate layers of hardware interconnectivity form the backbone of data transmission. Explore the robustness of the fabric, comprising a symphony of processors, memory units, and specialized accelerators, meticulously engineered to handle the demands of modern networking paradigms.
Peering into the Core: Venture deeper into the core architecture, where the convergence of high-speed interfaces and intelligent routing algorithms fosters optimal data flow. Witness the synergy between switching fabrics and forwarding engines, designed to navigate the complex terrain of network traffic with unparalleled efficiency and reliability.
Deciphering Performance Metrics: Navigate the labyrinth of performance metrics, where key indicators such as throughput, latency, and packet processing capabilities provide insights into the system’s operational efficacy. Unravel the intricate balance between raw processing power and algorithmic efficiency, illuminating the path towards enhanced network performance and scalability.
Exploring Scalability and Resilience: Peer into the horizon of scalability, where the system’s ability to accommodate growing workloads and adapt to evolving network dynamics is put to the test. Delve into redundancy mechanisms and fault-tolerance strategies, unveiling the resilience ingrained within the architecture to ensure uninterrupted service delivery in the face of adversities.
Conclusion: As we conclude our expedition into the hardware architecture and performance metrics, a vivid tapestry of technological innovation and operational excellence unfolds before us. Through meticulous analysis and exploration, we gain a deeper appreciation for the intricacies of network infrastructure, paving the way for continued advancements in the realm of connectivity and communication.
Optimizing Network Deployment with QFX10008: Configuration Insights
Enhancing network performance and efficiency entails a meticulous examination of configuration strategies and insights, transcending the mere perusal of technical specifications. This section delves into actionable methodologies to streamline network deployment, leveraging the robust capabilities of the QFX10008 platform without fixating solely on its datasheet.
Efficient Configuration Paradigms: Unveiling the intricacies of network configuration involves navigating through a myriad of parameters, protocols, and optimization techniques. By embracing a holistic approach to configuration management, network architects can orchestrate seamless integration and operation of the QFX10008, thereby optimizing resource utilization and bolstering overall performance.
Strategic Resource Allocation: Effective network deployment transcends the conventional allocation of resources; it demands a nuanced understanding of traffic patterns, latency requirements, and scalability imperatives. By delineating resource allocation strategies tailored to specific network demands, administrators can harness the full potential of the QFX10008, ensuring a harmonious interplay between hardware capabilities and operational exigencies.
Dynamic Protocol Optimization: The efficacy of network protocols lies not merely in their adherence to standards, but in their adaptability to evolving network dynamics. Through judicious protocol selection and parameter tuning, administrators can foster a dynamic network environment that accommodates fluctuating workloads and emergent traffic patterns, thereby enhancing the agility and responsiveness of the QFX10008 deployment.
Continuous Performance Monitoring: Sustaining optimal network performance necessitates vigilant monitoring and analysis, transcending episodic assessments of hardware capabilities. By instituting robust monitoring frameworks equipped with real-time analytics and anomaly detection mechanisms, administrators can proactively identify performance bottlenecks and aberrant behavior, thereby preempting potential disruptions and fortifying the resilience of the QFX10008 deployment.
Conclusion: In navigating the labyrinthine landscape of network deployment, configuration insights emerge as indispensable compasses, guiding administrators towards the zenith of operational efficiency and performance optimization. By embracing a synthesis of strategic configuration paradigms, resource optimization strategies, protocol optimization techniques, and continuous performance monitoring frameworks, administrators can unlock the transformative potential of the QFX10008 platform, transcending the confines of conventional datasheet interpretations.
Best Practices for Configuration, Fusion, and Upkeep
When embarking on the journey of implementing and maintaining intricate network systems akin to the Qfx10008, it is imperative to adhere to a set of well-considered practices that streamline the process and enhance overall efficiency.
First and foremost, meticulous attention to initial configuration lays the foundation for a robust and reliable network infrastructure. Prior to integration, meticulous planning is key. It involves comprehensively assessing the requirements and objectives of the network, identifying potential bottlenecks, and strategizing solutions to mitigate them. This phase sets the stage for seamless integration and operation.
- Thoroughly document configurations, ensuring clarity and accessibility for future reference.
- Utilize standardized configurations where applicable to streamline deployment and troubleshooting processes.
- Regularly review and update configurations to align with evolving business needs and industry standards.
Integration, the next pivotal phase, demands careful orchestration to harmonize diverse components into a cohesive system. Employing interoperable technologies and protocols facilitates smooth data flow and minimizes compatibility issues. Rigorous testing during integration verifies functionality and identifies potential points of failure, enabling preemptive remediation.
- Conduct thorough compatibility tests between hardware and software components to preempt interoperability issues.
- Implement redundancy measures to safeguard against single points of failure, ensuring continuous operation.
- Establish comprehensive monitoring protocols to detect anomalies and deviations from expected behavior.
Maintenance, the ongoing endeavor to preserve optimal performance, demands vigilance and proactivity. Regular audits and performance evaluations uncover inefficiencies and vulnerabilities, enabling timely interventions to forestall disruptions. Additionally, staying abreast of firmware updates and security patches fortifies defenses against emerging threats.
- Schedule routine inspections and performance evaluations to preemptively identify and address potential issues.
- Implement robust backup and recovery strategies to mitigate data loss in the event of unforeseen circumstances.
- Stay informed about firmware updates and security advisories, promptly applying patches to fortify defenses.
By adhering to these best practices throughout the setup, integration, and maintenance phases, organizations can optimize the performance, resilience, and longevity of their network infrastructure, ensuring seamless operations and bolstering competitive advantage.
Security Considerations for QFX10008: Safeguarding Your Network Infrastructure
In the realm of network fortification, meticulous attention to security stands as an imperative pillar. As we traverse the digital landscape, safeguarding the integrity, confidentiality, and availability of network infrastructure remains paramount. Within the domain of the QFX10008, the quest for security resonates profoundly. This segment delves into the nuanced considerations essential for shielding your network infrastructure against a myriad of potential threats.
Fortifying Perimeter Defenses: At the forefront of network security lie robust perimeter defenses, serving as the vanguard against unauthorized intrusions. Establishing resilient barriers entails strategic deployment of firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS). Embracing a proactive stance in fortifying perimeters cultivates a formidable deterrent against external threats.
Elevating Access Control Measures: The veracity of network security hinges upon meticulous control over access privileges. Implementing granular access controls, bolstered by multifactor authentication mechanisms, fortifies the bastions of network entry points. By delineating access rights with precision, organizations engender a fortified defense posture, impeding the ingress of malicious entities.
Embracing Vigilance through Monitoring: The adage “vigilance is the guardian of security” resonates profoundly within network operations. Elevating situational awareness entails the judicious deployment of monitoring solutions, facilitating real-time visibility into network traffic patterns. By embracing continuous monitoring, organizations glean insights vital for preempting potential security breaches, thereby bolstering the resilience of their network infrastructure.
Cultivating a Culture of Security: Beyond technological fortifications, the human element emerges as a linchpin in the security paradigm. Fostering a culture of security entails instilling awareness, accountability, and diligence amongst personnel. Through comprehensive training initiatives and stringent adherence to security protocols, organizations fortify their defenses by transforming individuals into vigilant sentinels against cyber threats.
Conclusion: In navigating the labyrinth of network security considerations pertinent to the QFX10008, the imperative of safeguarding network infrastructure reverberates resoundingly. By fortifying perimeter defenses, elevating access controls, embracing vigilant monitoring, and nurturing a culture of security, organizations erect formidable bulwarks against an array of potential threats. Within this holistic approach lies the key to preserving the integrity, confidentiality, and availability of network infrastructure in an ever-evolving threat landscape.