In the realm of digital protection and fortification against online threats, the demand for comprehensive documentation offering insights into cutting-edge security solutions remains paramount. Delving into the intricacies of contemporary cyber defense strategies, this informational document serves as a guiding beacon amidst the labyrinth of cyber risks and vulnerabilities. Within these pages, discover a compendium of elucidative discourse, illuminating the path towards fortified digital resilience and safeguarded data integrity.
Empowering organizations with the knowledge essential for navigating the dynamic landscape of cyber threats, this dossier encapsulates the quintessence of proactive cybersecurity measures. Through a meticulous examination of advanced security protocols and risk mitigation strategies, readers embark on a journey towards fortified digital bastions, fortified against the relentless tide of malicious incursions.
Embark on a voyage through the panorama of contemporary cyber defense architectures, elucidating the intricacies of preemptive measures and responsive countermeasures. Unveil the panoply of digital armaments at your disposal, each facet meticulously crafted to thwart the machinations of cyber adversaries and uphold the sanctity of your digital domain.
Exploring the Capabilities of Documentation by Proofpoint
In this section, we delve into the intricacies and functionalities of the comprehensive documentation provided by Proofpoint, offering a nuanced exploration of its myriad features and utilities. Through this examination, we aim to illuminate the breadth and depth of its offerings, showcasing its versatility and value in various contexts.
Unlocking Insights: The documentation curated by Proofpoint serves as a gateway to invaluable insights, offering a wealth of information that empowers users to navigate complex landscapes with clarity and confidence. Through meticulous organization and clarity of presentation, it facilitates the extraction of actionable intelligence, enabling informed decision-making and strategic planning.
Enhancing Accessibility: One of the hallmark features of Proofpoint’s documentation lies in its accessibility, catering to diverse audiences with varying levels of expertise and familiarity. Whether you are a novice seeking foundational knowledge or a seasoned professional delving into advanced topics, the documentation accommodates your needs, fostering an inclusive learning environment.
Fostering Efficiency: Efficiency is paramount in today’s fast-paced digital landscape, and Proofpoint’s documentation excels in streamlining processes and workflows. By providing clear instructions, troubleshooting guides, and best practices, it minimizes friction and maximizes productivity, empowering users to accomplish tasks with precision and efficiency.
Cultivating Confidence: Confidence is the cornerstone of effective utilization, and Proofpoint’s documentation instills a sense of assurance through its comprehensive coverage and meticulous attention to detail. By elucidating concepts and demystifying complexities, it equips users with the knowledge and skills needed to navigate challenges with poise and proficiency.
In conclusion, the documentation offered by Proofpoint transcends mere information dissemination, evolving into a dynamic tool that empowers users, enhances productivity, and fosters innovation. Through continuous refinement and innovation, it remains an indispensable resource in the arsenal of modern enterprises, driving success and resilience in an ever-evolving landscape.
The Core Features and Capabilities
In this section, we delve into the fundamental aspects that underpin the essence of this solution. Without resorting to the specific nomenclature, we explore the robust functionalities and innate strengths that define its prowess.
Advanced Threat Protection
Within the realm of safeguarding against malicious entities, this solution stands as a bastion of defense. It employs a sophisticated array of mechanisms to detect, mitigate, and neutralize potential threats, ensuring the integrity of digital ecosystems.
Email Security Enhancements
Amidst the vast expanse of digital communication, the solution fortifies the boundaries of electronic correspondence. It furnishes a suite of tools and protocols to fortify email channels against infiltration and exploitation, bolstering organizational resilience.
- Dynamic threat intelligence integration
- Real-time threat detection
- Comprehensive incident response capabilities
Through a synthesis of innovation and efficacy, this solution heralds a new era of proactive defense and fortified communication infrastructures.
Integration Options and Compatibility
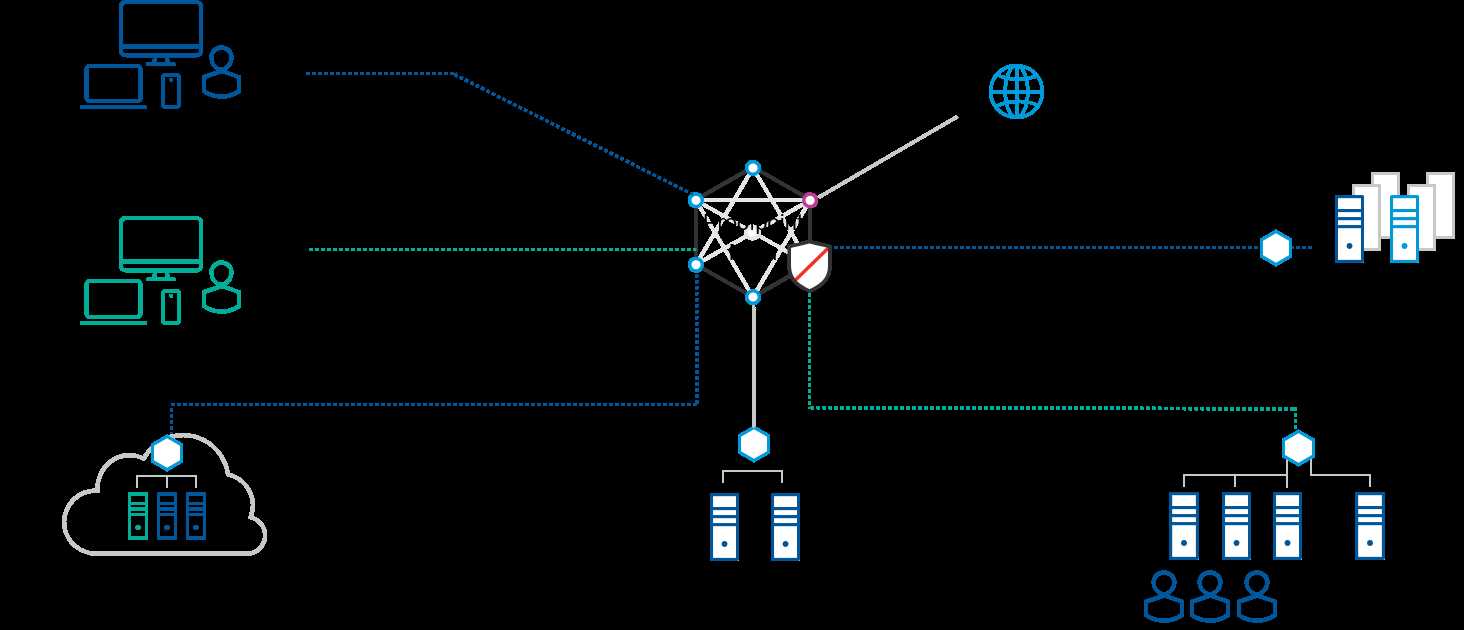
Exploring the synergy between our solution and various platforms is pivotal to optimizing your cybersecurity infrastructure. This section delves into the myriad of integration avenues and compatibility considerations, ensuring seamless incorporation into your existing ecosystem.
- Platform Integration: Discover how our technology seamlessly merges with leading platforms across diverse environments, bolstering your security posture without disruption.
- Interoperability Insights: Gain insights into how our solution interacts with a spectrum of software and hardware components, ensuring smooth interoperability and unhindered functionality.
- API Capabilities: Uncover the potential of our API-driven approach, empowering you to customize and extend functionality, integrating effortlessly with your preferred systems.
- Protocol Support: Delve into the extensive protocol support, facilitating integration with protocols essential for your infrastructure, enhancing flexibility and adaptability.
- Compatibility Matrix: Navigate through our comprehensive compatibility matrix, elucidating supported versions, dependencies, and prerequisites for seamless deployment.
By elucidating integration options and compatibility facets, we pave the way for a cohesive cybersecurity framework, harmonizing diverse elements to fortify your digital landscape.
Security Advantages and Deployment Insights
In the realm of cybersecurity, leveraging advanced solutions yields a plethora of protective benefits, fortifying organizational infrastructures against an array of threats. This section delves into the manifold security advantages and offers insights into their seamless integration.
|
Enhanced Threat Detection: By deploying robust security measures, organizations bolster their capacity to swiftly identify and neutralize potential threats, safeguarding sensitive assets from malicious actors. |
|
Proactive Risk Mitigation: Adopting proactive strategies allows enterprises to anticipate vulnerabilities and preemptively address them, reducing the likelihood and impact of security breaches. |
|
Streamlined Compliance: Integration of comprehensive security solutions facilitates adherence to regulatory standards and industry best practices, ensuring organizational compliance and fostering trust among stakeholders. |
|
Efficient Resource Utilization: Efficient allocation of resources, coupled with automated processes, optimizes security operations, enhancing productivity and minimizing operational overhead. |
|
Holistic Threat Intelligence: Access to real-time threat intelligence empowers organizations with comprehensive insights into emerging risks, enabling informed decision-making and proactive defense strategies. |
These security benefits, when strategically implemented, fortify the organizational posture against evolving cyber threats, fostering resilience and instilling confidence in stakeholders.