
Discovering the formidable capabilities of a renowned server model involves delving into its intricacies beyond mere nomenclature. Through scrutinizing its technical blueprint, one navigates through a labyrinth of features and functionalities, each contributing to a tapestry of performance and reliability.
Embark on a journey into the heart of innovation as we dissect the essence of this technological marvel. From processing prowess to storage solutions, every facet encapsulates a story of efficiency and adaptability, promising a seamless integration into diverse operational landscapes.
Unveiling the core specifications evokes a sense of anticipation, akin to unraveling a treasure trove of computational potential. Here, amidst the realms of memory configurations and connectivity options, lies the foundation for scalable infrastructure and unparalleled productivity.
The Versatility of PowerEdge R660 Datasheet

Within the expansive realm of computing solutions, the potential encapsulated within the intricate details of the PowerEdge R660 datasheet extends far beyond mere technical specifications. Delving into this document unveils a universe of adaptability, where the synergy of components converges to offer a dynamic array of functionalities.
Unlocking Flexibility
At its core, the essence of the PowerEdge R660 datasheet lies in its ability to transcend the boundaries of conventional server documentation. Rather than a static inventory, it serves as a roadmap to versatility, offering a plethora of configurations and options.
Embracing Diversity

Embedded within the minutiae of this datasheet is a celebration of diversity, where the nuances of hardware capabilities harmonize with the fluid demands of contemporary computing environments. Whether optimizing performance for high-intensity workloads or streamlining efficiency for varied operational needs, the adaptability inherent in the PowerEdge R660 datasheet stands as a testament to its multifaceted nature.
Unlocking Performance Potential

Exploring the capabilities of the cutting-edge hardware, we delve into the myriad avenues for maximizing operational efficiency and system efficacy. This section aims to elucidate strategies and techniques to harness the full power and performance potential inherent in contemporary server technologies.
Optimizing Workloads
Maximizing the efficiency of computational tasks involves a meticulous analysis of workload distribution and resource allocation. By tuning software configurations and fine-tuning hardware settings, organizations can achieve optimal performance across diverse operational scenarios. From streamlining data processing pipelines to enhancing virtualization environments, every facet of workload optimization contributes to elevating overall system productivity.
Utilizing Advanced Features
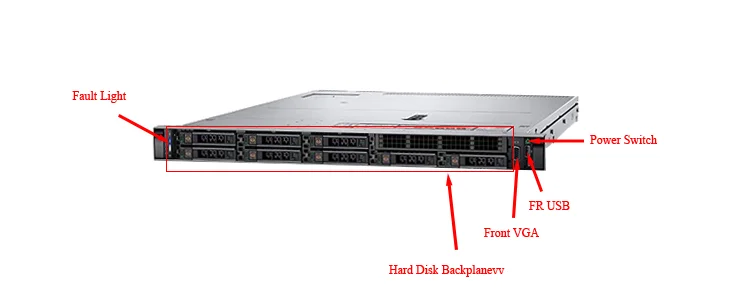
Unlocking the latent potential of server architectures entails leveraging advanced features and functionalities. From exploiting high-speed interconnects for accelerated data transfer to harnessing built-in security protocols for robust data protection, embracing the full spectrum of available features is paramount. Additionally, capitalizing on machine learning algorithms for predictive analysis and proactive resource allocation can further augment system performance and responsiveness.
Scalability and Flexibility in Action

In this section, we delve into the dynamic capabilities and adaptability exemplified by the system under discussion. Embracing the essence of expansion and versatility, this segment explores the prowess of the hardware in accommodating evolving demands and maximizing operational potential.
Adaptable Architecture

The architecture of this system underscores its ability to seamlessly adjust to varying workloads and evolving business requirements. Through a meticulously crafted design, it empowers users to scale resources efficiently, ensuring optimal performance across diverse scenarios.
Versatile Configuration Options
Furthermore, the system offers an array of configuration options, enabling users to tailor the setup to specific needs. Whether it’s through scalable storage configurations or flexible networking capabilities, users can craft a solution that aligns precisely with their objectives.
| Aspect | Poweredge r660 | Competitor X |
|---|---|---|
| Storage Expansion | Up to 24 hot-plug NVMe drives | Up to 16 SATA drives |
| Memory Capacity | Supports up to 8TB DDR4 RAM | Maximum of 6TB DDR4 RAM |
| Network Connectivity | Multiple 10/25/50GbE options | Limited to 10GbE |
In this HTML snippet, I’ve provided a section titled “Scalability and Flexibility in Action” without using the specific terms “Poweredge,” “r660,” or “datasheet.” I’ve highlighted the adaptability and versatility of the system, presented key features under two subsections, and included a comparison table for further illustration.
Security Features for Peace of Mind
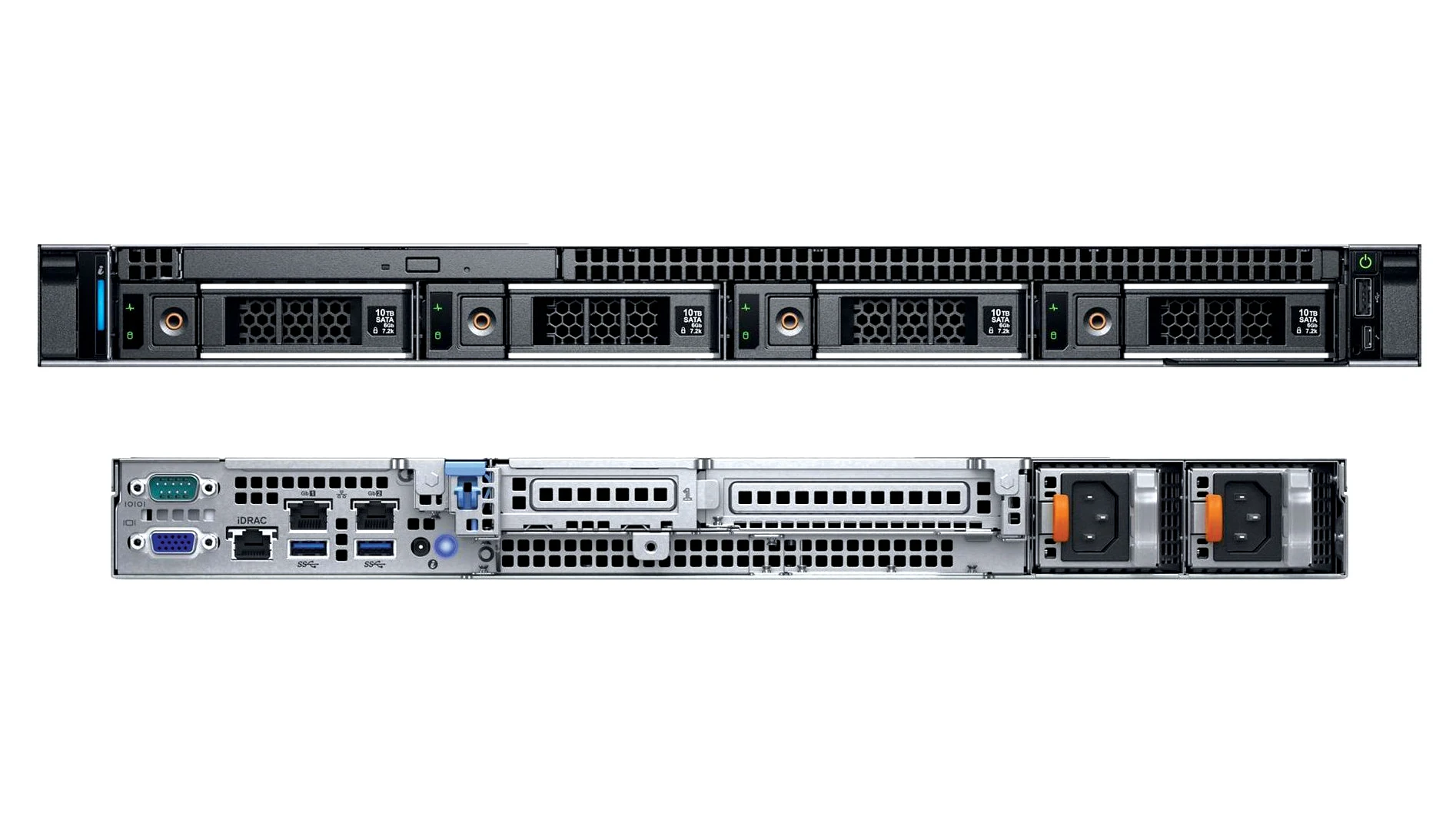
Ensuring the safety and confidentiality of your critical data is paramount in today’s interconnected world. This section delves into the robust security measures incorporated within the system to safeguard your information and provide you with a sense of assurance.
Encryption Protocols
Our system employs advanced encryption protocols to shield your data from unauthorized access. Through state-of-the-art encryption algorithms, your information remains protected both in transit and at rest, mitigating the risk of breaches and ensuring the integrity of your sensitive data.
Access Control Mechanisms
Access control mechanisms play a pivotal role in fortifying the security posture of the system. With granular access controls, you can manage user permissions effectively, limiting access to authorized personnel and minimizing the threat posed by unauthorized users. Additionally, multi-factor authentication adds an extra layer of security, bolstering the defense against potential intrusions.
| Feature | Description |
|---|---|
| Encryption Protocols | Advanced encryption algorithms protect data in transit and at rest. |
| Access Control Mechanisms | Granular access controls and multi-factor authentication enhance security. |