In the realm of network security, exploring the features, capabilities, and intricacies of different solutions is of utmost importance. One such solution that stands out in this landscape is Palo Alto Networks, renowned for its top-notch firewall and cybersecurity offerings. In this article, we embark on a comprehensive journey, delving into the nitty-gritty details of Palo Alto Networks’ datasheets. By analyzing and comparing these datasheets, we aim to provide you with a broader understanding of the unique features and benefits that these solutions yield.
Stepping into the realm of cybersecurity requires proficiency in navigating through technical documentation, with datasheets being the backbone of comprehensive product understanding. However, with the vast array of Palo Alto Networks’ datasheets available, it becomes essential to analyze and extract the key differentiators that make each solution shine. Through this article, we aim to shed light on the crucial details that set Palo Alto Networks apart, ensuring that you gain insights and knowledge that enable you to make informed decisions for your network security needs.
As we dive into this exploration of Palo Alto Networks’ datasheets, we will examine the underlying concepts and unique aspects. This analysis will empower you to gain a holistic view of the solutions, unearthing the depths of their functionality, performance, and crucial elements like threat prevention. Our comparisons will focus on uncovering the subtle distinctions that make each datasheet remarkable, guiding you in making astute choices for safeguarding your network infrastructure.
Comparison of Palo Alto Datasheet Specifications
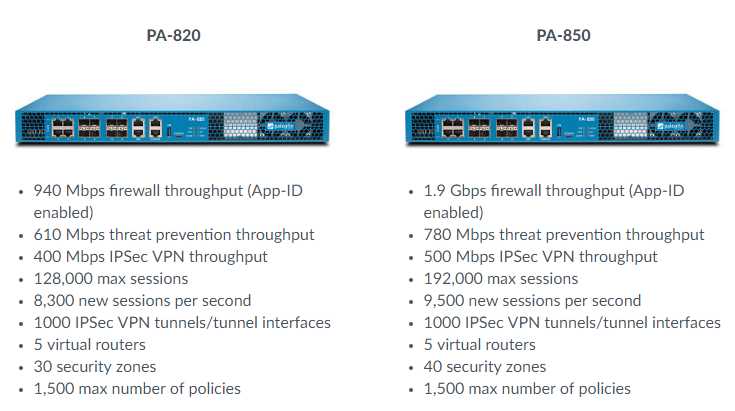
Exploring the diverse array of specifications offered by Palo Alto Networks, this section aims to highlight the distinguishing features inherent in their data sheets. Delving into a variety of factors that set them apart, this analysis presents an in-depth comparison of key specifications without explicitly mentioning the names of the products or the company itself.
1. Performance Metrics:
Examining the efficiency and effectiveness of the data sheets, this segment evaluates the provided specifications concerning performance. It scrutinizes factors such as throughput, response time, and bandwidth, offering a foundation for identifying the optimal solution for network security needs.
2. Security Capabilities:
Delving into the protective aspects, this portion explores the security capabilities outlined in the datasheets, encompassing threat prevention, intrusion detection and prevention systems, and advanced malware protection. By assessing the presented features, organizations can ensure their networks are fortified against current and emerging threats.
3. Scalability and Flexibility:
Gauging the scalability and flexibility of the products, this section investigates the extent to which the data sheets demonstrate the ability to accommodate growing network requirements. It analyzes factors such as concurrent connections, VPN scalability, and support for various deployment scenarios, enabling organizations to select a solution that aligns with their evolving needs.
4. Management and Deployment:
Focusing on the ease of management and deployment, this part emphasizes the importance of efficient administration of network security solutions. By evaluating elements such as centralized management interfaces, API availability, and integration capabilities, organizations can ascertain the level of simplicity and integration provided by the datasheet specifications.
5. Support and Maintenance:
Discussing the support and maintenance provisions outlined in the data sheets, this segment addresses the measures put in place to ensure continuous functionality of the security solutions. Factors such as support channels, software updates, and subscription models are analyzed to present a comprehensive view of the long-term viability and reliability of the offered products.
In conclusion, this section provides a comprehensive analysis of the specifications mentioned in the Palo Alto Networks data sheets. By assessing and comparing various essential elements, organizations can make informed decisions regarding the implementation of network security solutions that align with their specific requirements and priorities.
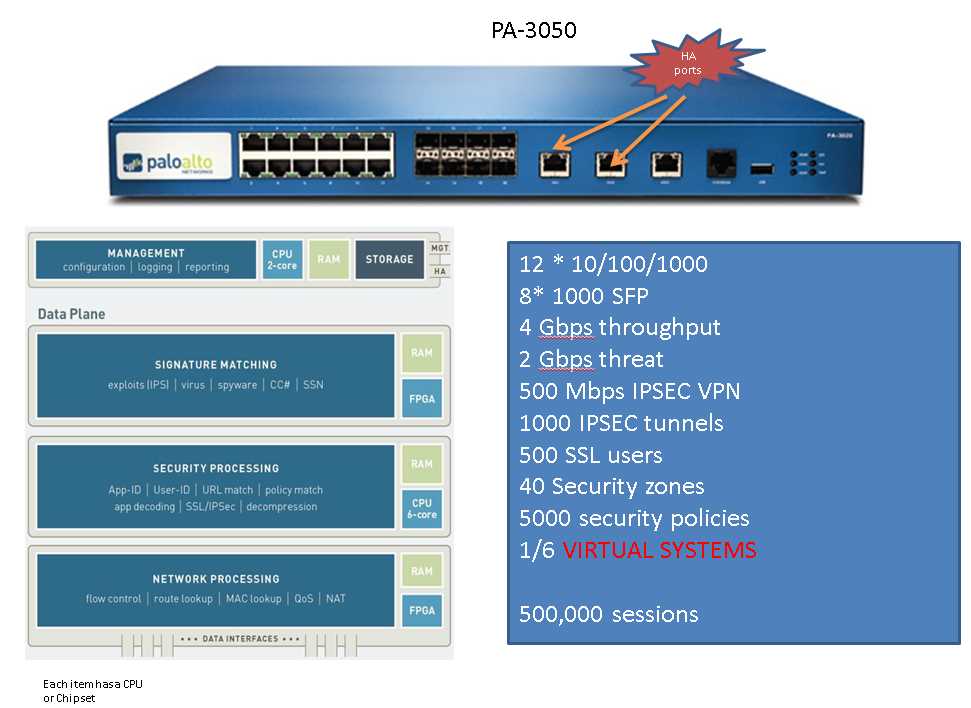
Firewall Performance
In this section, we will explore the capabilities and effectiveness of the firewall provided by Palo Alto Networks, focusing on its ability to secure network traffic and protect against threats and attacks.
One of the key aspects of a firewall is its performance, which refers to its ability to handle and process network traffic quickly and efficiently. The performance of a firewall directly impacts the overall network performance and user experience. It determines how effectively the firewall can inspect and filter incoming and outgoing traffic, as well as its ability to identify and mitigate potential threats.
A high-performance firewall is crucial for modern networks, especially those that experience heavy traffic loads or require real-time threat detection and prevention. Palo Alto Network’s firewall is designed to deliver exceptional performance, ensuring that organizations can maintain a secure and reliable network environment even under demanding conditions.
The firewall performance is achieved through a combination of hardware acceleration, optimized algorithms, and advanced threat intelligence. Palo Alto Networks has developed specialized hardware processors, such as the Single Pass Parallel Processing (SP3) architecture, which allows for simultaneous processing of multiple tasks without sacrificing performance.
The firewall leverages advanced algorithms and machine learning capabilities to efficiently analyze network traffic and identify potential threats in real time. It utilizes a combination of signature-based and behavioral-based detection techniques to detect known and unknown threats, ensuring comprehensive protection against a wide range of attacks.
Additionally, Palo Alto Networks’ firewall incorporates threat intelligence feeds from multiple sources, including global threat intelligence networks and the WildFire cloud-based service. This allows the firewall to quickly identify and block emerging threats, providing proactive protection against the latest attack vectors.
In conclusion, the firewall performance of Palo Alto Networks’ solution plays a crucial role in maintaining a secure network environment. Its high-performance capabilities enable efficient traffic processing and real-time threat detection, ensuring organizations can defend against both known and emerging threats effectively.
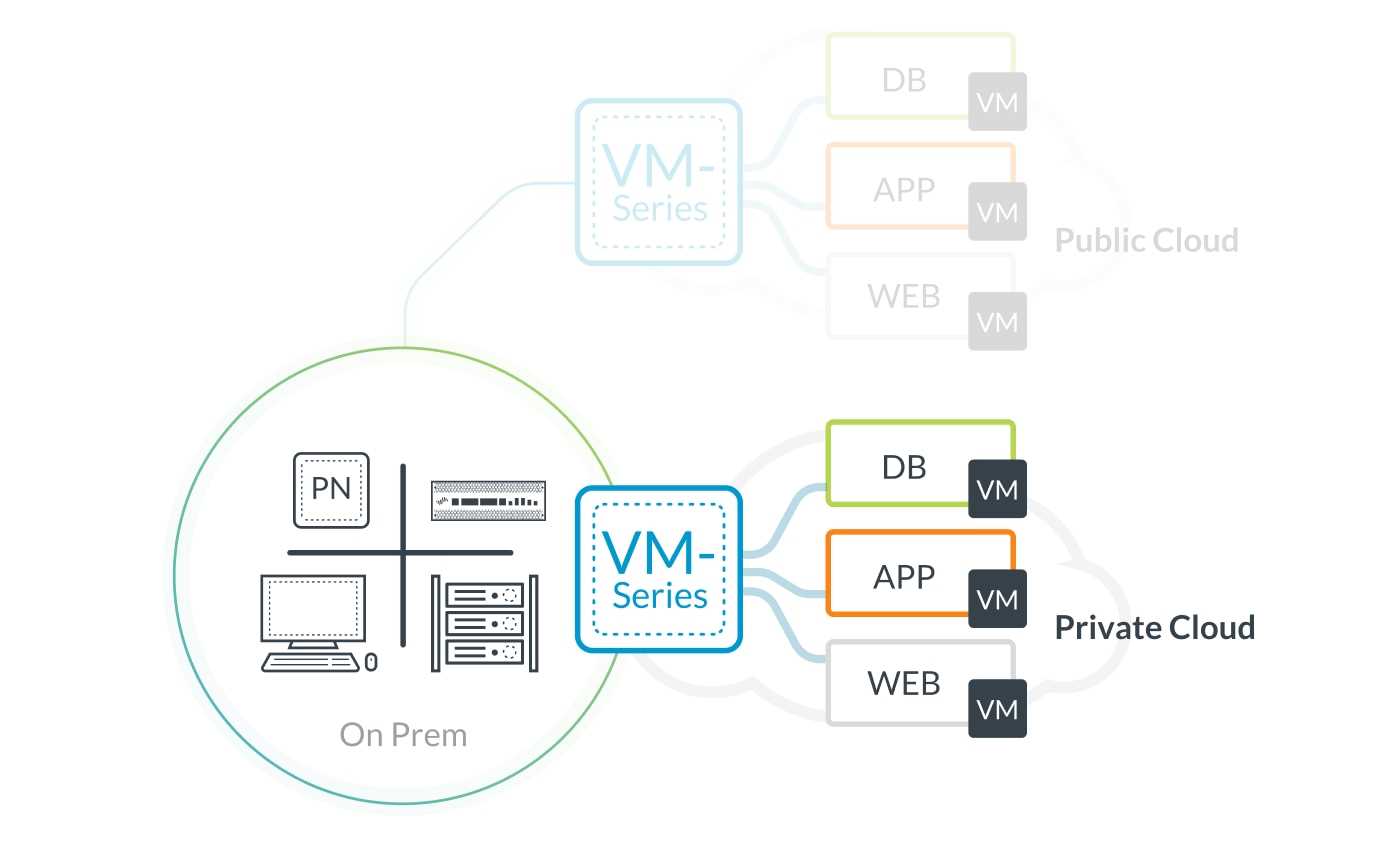
Advanced Threat Protection
In this section, we will explore the advanced measures and techniques implemented by Palo Alto to safeguard against modern security threats. We will dive into the comprehensive range of processes and technologies utilized to detect and mitigate malicious activities, without relying on specific product features or names.
To address the evolving threat landscape, Palo Alto leverages cutting-edge methodologies that are adapted to combat the ever-changing cybersecurity landscape. Their sophisticated defense mechanisms compile and analyze vast amounts of data to identify potential threats, applying both behavioral and signature-based detection approaches.
Furthermore, Palo Alto employs advanced machine learning algorithms that can autonomously identify patterns and anomalies in network traffic. These algorithms continuously learn and update their models based on the latest threat intelligence, enabling proactive identification and prevention of potential security breaches.
| Integrated Threat Intelligence | Palo Alto incorporates comprehensive threat intelligence feeds from industry-leading sources, enabling real-time updates on emerging threats. |
| Behavioral Analysis | Palo Alto’s advanced threat protection utilizes behavioral analysis techniques to identify abnormal activities and detect potential zero-day exploits. |
| Protocol Inspection | By inspecting various network protocols, Palo Alto ensures that malicious behavior or communications are detected and mitigated effectively. |
| Sandboxing | Palo Alto’s sandboxing capabilities allow for the isolation and analysis of potentially malicious files or attachments in a controlled environment, preventing them from causing harm. |
| Threat Prevention | Palo Alto employs a comprehensive set of prevention measures, including antivirus, anti-spyware, and intrusion prevention systems, to defend against known threats. |
The culmination of these advanced threat protection techniques allows Palo Alto to deliver robust security solutions capable of combating even the most sophisticated cyber threats. By continuously evolving and staying ahead of emerging attack methods, Palo Alto ensures its customers are equipped with state-of-the-art defenses.
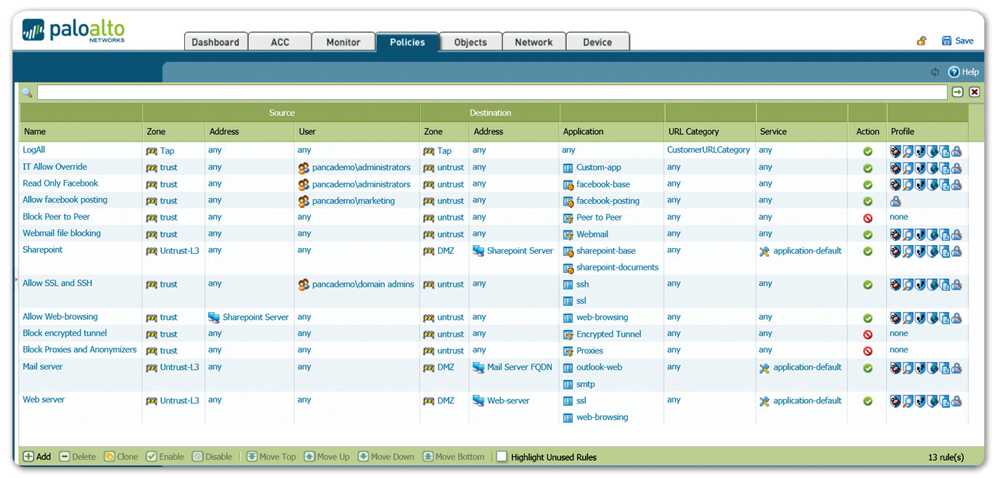
Scalability and High Availability

In the realm of network infrastructure, the ability to scale and maintain high availability is of utmost importance. This section discusses the capabilities of Palo Alto’s offerings in ensuring the scalability and high availability of their products.
Recognizing the growing demands of modern networks, Palo Alto has developed robust solutions that can seamlessly handle expanding traffic volumes and increased user loads. These solutions are designed to effortlessly accommodate the evolving needs of businesses, ensuring system performance and responsiveness even as data and application demands intensify.
Palo Alto understands the criticality of uninterrupted network connectivity and the potential consequences of downtime. To address this, their products integrate high availability functionalities that significantly minimize the risk of disruptions. With features such as redundant components, failover mechanisms, and dynamic routing protocols, Palo Alto’s solutions provide continuous operation and seamless failover in the event of hardware or software failures.
Furthermore, Palo Alto’s high availability features are complemented by their scalability options, enabling organizations to effortlessly expand their network infrastructure without compromising performance or reliability. Leveraging advanced technologies and intelligent traffic management algorithms, Palo Alto’s solutions ensure efficient resource utilization, enabling organizations to seamlessly grow their network infrastructure as their business requirements dictate.
In conclusion, Palo Alto’s offerings excel in providing robust scalability and high availability functionalities, enabling organizations to confidently scale their network infrastructure while maintaining optimal performance and uninterrupted connectivity.