
Welcome to the cutting-edge realm of advanced network hardware that guarantees unrivaled performance, seamless connectivity, and unprecedented efficiency. In this comprehensive article, we unveil the most revolutionary features of the Palo Alto 850, a groundbreaking device that sets a new benchmark in the world of data transfer and network security.
Prepare yourself to delve into the realm of breakthrough innovations as we unveil the capabilities of this next-generation equipment. Equipped with state-of-the-art technology, the Palo Alto 850 paves the way for unparalleled productivity, robust network defense, and lightning-fast data transfer. Discover the key aspects that make it an indispensable tool for businesses craving unmatched performance and enhanced cybersecurity.
Hold your breath as we unleash the power of this marvel: its exceptional processing speed, seamless integration with existing systems, and remarkable adaptability. With every aspect meticulously designed to provide an exceptional user experience, the Palo Alto 850 harnesses the forces of innovation, intelligence, and efficiency to transform the way we perceive network infrastructure.
Palo Alto 850 Datasheet: Key Features and Specifications

In this section, we will explore the main characteristics and technical specifications of the Palo Alto 850 device. It is essential to understand these key features to comprehend the capabilities and potential applications of this advanced security solution.
Performance and Throughput
The Palo Alto 850 offers exceptional performance and throughput, ensuring fast and efficient network security operations. With its powerful processing capabilities and advanced algorithms, it can handle high volumes of traffic without compromising on speed or reliability.
Security Features
This device boasts a wide range of security features that provide comprehensive protection against various cyber threats. It incorporates advanced firewall technologies, intrusion prevention systems (IPS), virtual private network (VPN) capabilities, and application-level visibility and control.
| Feature | Description |
|---|---|
| Firewall | Offers industry-leading firewall capabilities to safeguard the network from unauthorized access and prevent malicious activities. |
| Intrusion Prevention System (IPS) | Detects and prevents intrusion attempts in real-time, protecting against known and unknown threats. |
| Virtual Private Network (VPN) | Enables secure remote connectivity by establishing encrypted tunnels between networks. |
| Application-level Visibility and Control | Allows granular control over network traffic based on applications, ensuring optimal performance and security. |
Scalability and Flexibility
The Palo Alto 850 is a highly scalable solution that can adapt to the evolving needs of growing networks. It offers flexible deployment options, supporting both hardware and virtualized environments, making it suitable for various network infrastructures.
Overall, the Palo Alto 850 combines powerful performance, robust security features, and scalability, making it an ideal choice for organizations seeking a reliable and advanced network security solution.
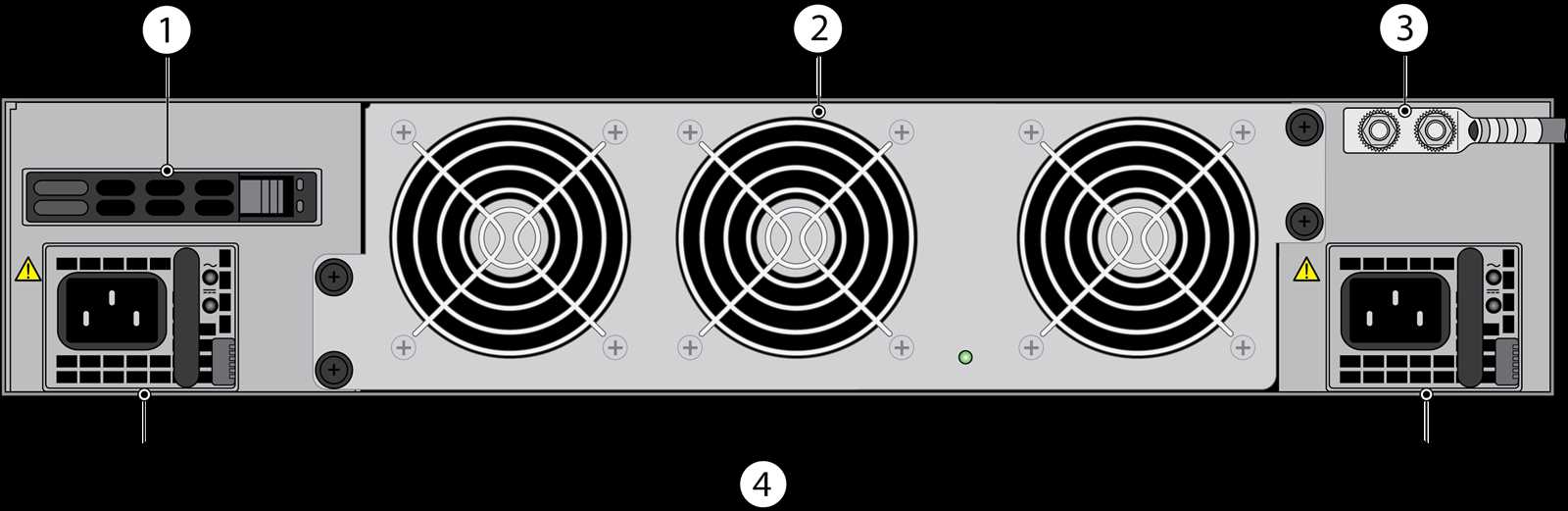
Hardware Specifications
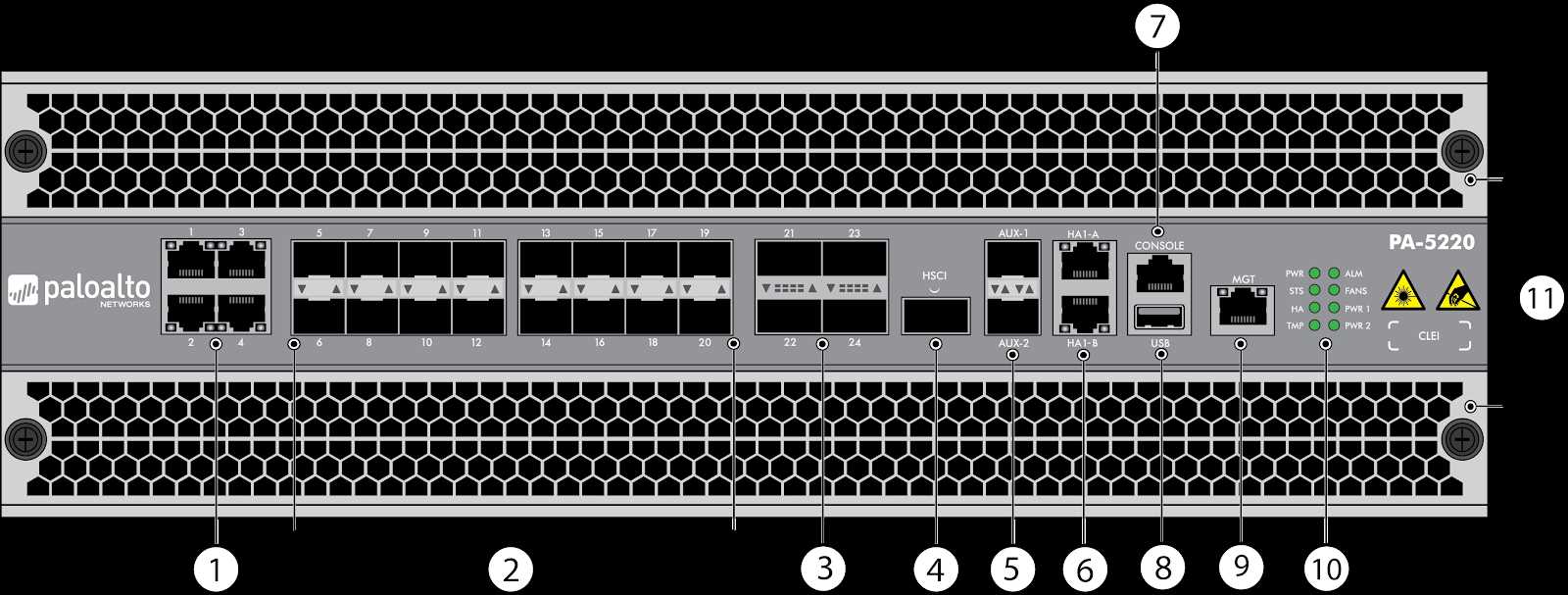
In this section, we will explore the technical details and key features of the hardware components associated with the Palo Alto 850 solution. This will provide a comprehensive understanding of the device’s capabilities and functionalities to aid in network security management. The hardware specifications encompass the physical aspects of the device, such as the processor, memory, storage, and networking interfaces, which collectively contribute to its performance and reliability.
To delve into the hardware specifications of the Palo Alto 850, we will utilize a tabular format to present the information in a structured and organized manner. This will facilitate easy comprehension and comparison of the various components. The table will include specific details such as the processor type, clock speed, number of cores, and cache size. Additionally, the memory and storage configurations, including type, capacity, and interface, will be presented alongside the networking interfaces, such as Ethernet ports and their respective speeds.
| Component | Description |
|---|---|
| Processor | A central processing unit responsible for executing instructions and tasks. |
| Memory | System’s volatile memory for data storage and retrieval. |
| Storage | Non-volatile storage used for long-term data retention. |
| Networking Interfaces | Interfaces that enable connectivity to the network. |
By thoroughly examining the hardware specifications provided, IT professionals and system administrators can gain insights into the Palo Alto 850’s abilities, empowering them to make informed decisions regarding network security implementations and optimizations. Familiarity with the device’s hardware capabilities will allow for more efficient utilization of resources and ensure smooth network operations.
Software Capabilities
In this section, we will explore the diverse range of software capabilities offered by the Palo Alto 850. By leveraging its powerful features, the device empowers users to effectively manage their network security. From comprehensive threat prevention to advanced monitoring and analytics, the software of the Palo Alto 850 enables organizations to enhance their network protection and streamline their security operations.
Comprehensive Threat Prevention
The Palo Alto 850 provides a robust suite of security features to safeguard networks against a wide range of threats. Its advanced threat prevention capabilities include intelligent firewalling, intrusion prevention, and URL filtering. By analyzing network traffic in real-time, the device can identify and block malicious activities, ensuring the integrity of the network and protecting sensitive data.
Advanced Monitoring and Analytics
Beyond threat prevention, the Palo Alto 850 offers advanced monitoring and analytics capabilities. Through intelligent logging and reporting, the device provides detailed insights into network traffic patterns, user behavior, and security events. These analytics empower administrators to identify potential vulnerabilities, detect anomalies, and make informed decisions to optimize network performance and security.
With its comprehensive software capabilities, the Palo Alto 850 delivers a powerful solution for network security management. By combining advanced threat prevention features with robust monitoring and analytics, the device enables organizations to effectively mitigate risks, protect their assets, and maintain a secure network environment.