Intrigued by the technological marvels of modern surveillance? Delve into the intricacies of a cutting-edge innovation poised to redefine the landscape of visual data capture. Step into the realm of ingenuity where precision meets intelligence, offering a glimpse into the future of surveillance solutions.
Embark on a journey where clarity and insight converge, unlocking the potential of visual narratives in unprecedented ways. Uncover the essence of seamless integration and effortless deployment, as each component intertwines to form a cohesive tapestry of functionality.
Peer into the heart of innovation, where every pixel tells a story, and every frame encapsulates a moment in time. Traverse the landscape of features and specifications, where performance isn’t just a metric but a testament to the relentless pursuit of excellence.
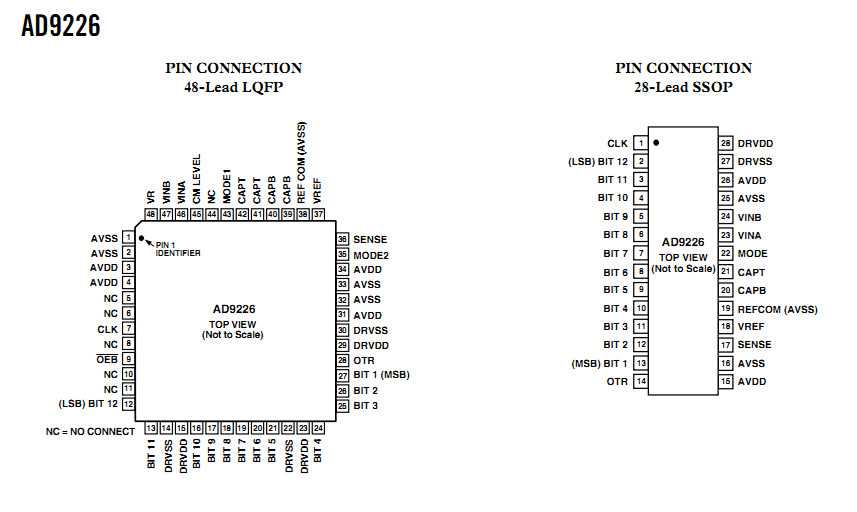
Exploring the Meraki MV21 Datasheet: Key Features and Specifications
In this segment, we embark on a journey delving into the intricate details encapsulated within the documentation of the Meraki MV21. Unveiling its essence entails navigating through a labyrinth of technical intricacies and functionalities. Let’s embark on an exploration, dissecting the quintessence of this device, unraveling its distinguishing attributes and specifications.
Advanced Capabilities: Delving into the core functionalities, we unveil a plethora of sophisticated features designed to elevate surveillance mechanisms. From cutting-edge image processing technologies to seamless integration with existing networks, the MV21 manifests an amalgamation of innovation and efficiency.
Empowering Surveillance: Beyond conventional surveillance paradigms, the MV21 transcends boundaries, empowering users with a comprehensive toolkit tailored for diverse environments. With a keen emphasis on versatility, this device seamlessly adapts to varied scenarios, ensuring robust surveillance across verticals.
Enhanced Connectivity: At the heart of its design lies a commitment to seamless connectivity. Through optimized networking protocols and intuitive interfaces, the MV21 fosters unparalleled interoperability, fostering a cohesive ecosystem conducive to streamlined surveillance operations.
Precision in Detail: Amidst the array of specifications lies a testament to precision engineering. From resolution benchmarks to frame rates, every metric meticulously aligns to redefine the standards of surveillance excellence, ensuring clarity and accuracy in every frame.
Reliability Redefined: Embedded within its architecture is a robust foundation built upon reliability. With a focus on durability and resilience, the MV21 emerges as a stalwart companion, weathering the challenges of dynamic environments while maintaining unwavering performance.
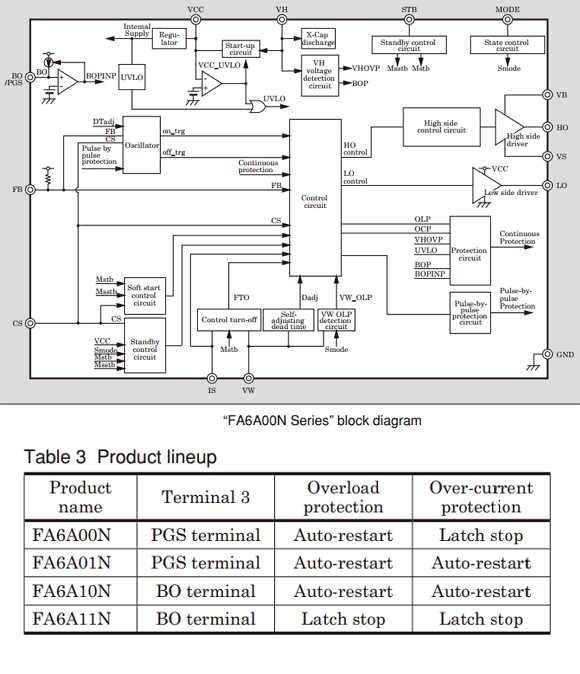
Unveiling the Advanced Camera Capabilities

In this section, we delve into the sophisticated features and functionalities of the cutting-edge camera technology integrated within the system. From its dynamic range to its intricate motion detection algorithms, every aspect has been meticulously crafted to deliver unparalleled performance in diverse scenarios.
Enhanced Visual Acuity
At the core of the camera’s prowess lies its ability to capture imagery with remarkable clarity and precision. Through innovative optics and advanced image processing techniques, it excels in rendering intricate details and maintaining optimal sharpness across varying lighting conditions.
Intelligent Scene Analysis
Beyond conventional image capture, the camera demonstrates a remarkable intelligence in analyzing scenes in real-time. Leveraging sophisticated algorithms, it can discern between different objects, detect anomalies, and adapt dynamically to changing environments, ensuring reliable surveillance and actionable insights.
- High-fidelity image reproduction
- Dynamic range optimization
- Adaptive motion sensing
- Efficient bandwidth utilization
Through these advanced capabilities, the camera empowers users with unparalleled visibility and situational awareness, revolutionizing the way surveillance and monitoring are conducted in modern environments.
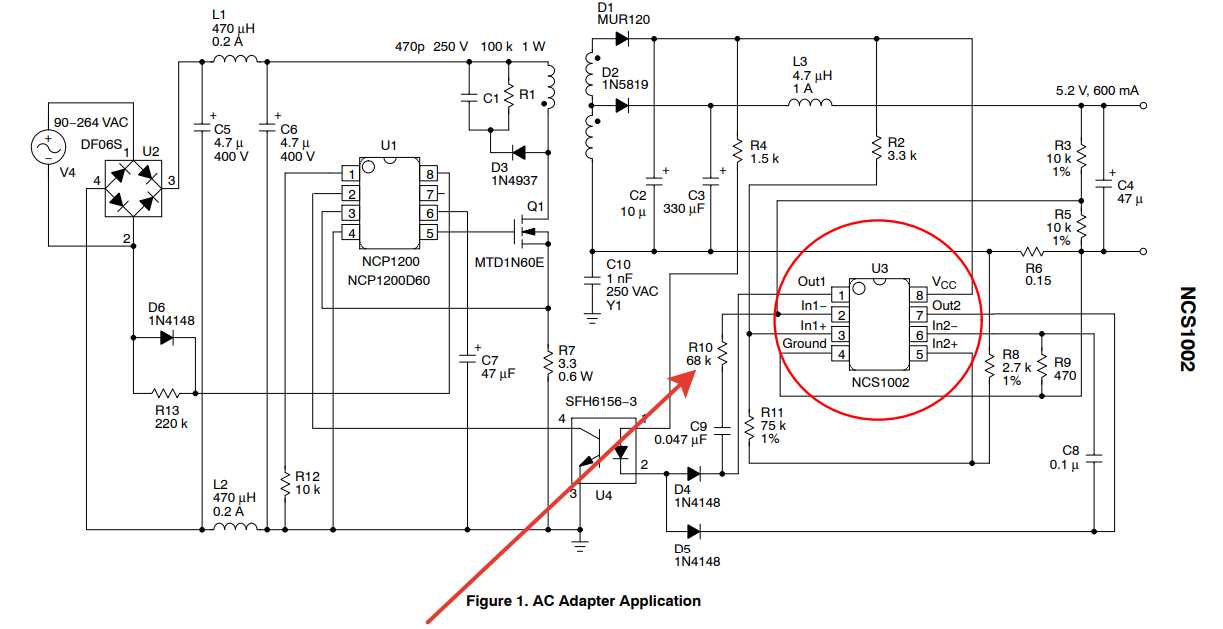
Understanding Connectivity and Integration Options
In this section, we delve into the myriad ways in which the device interfaces with various systems, emphasizing the versatility and adaptability inherent in its connectivity framework. Exploring the integration landscape, we uncover the seamless interactions achievable across diverse platforms and protocols.
Connectivity Features
Delving into the connectivity spectrum, we dissect the device’s ability to establish and maintain connections across a range of networks. From wired to wireless interfaces, each avenue presents unique opportunities for data transmission and exchange.
Integration Possibilities
Examining integration facets, we uncover the potential synergies between the device and complementary technologies. Whether interfacing with existing infrastructure or emerging ecosystems, the device offers avenues for seamless integration and enhanced functionality.
| Connectivity Options | Integration Platforms |
|---|---|
| Wired Ethernet | Cloud-based Services |
| Wi-Fi Connectivity | API Integrations |
| Bluetooth Capabilities | IoT Frameworks |
Examining Security and Privacy Features
Exploring the robust suite of safeguards and confidentiality measures inherent in the product specification unveils an intricate tapestry of protective elements and data integrity protocols. This section delves into the intricate fabric of security and privacy mechanisms engineered within the framework, aiming to shed light on the formidable shield it offers against potential vulnerabilities and breaches.
Comprehensive Encryption Protocols
One cornerstone of its defensive architecture lies in its deployment of advanced encryption methodologies, ensuring end-to-end data transmission remains impervious to interception or tampering. By employing cutting-edge cryptographic algorithms, the system fortifies the confidentiality of sensitive information, rendering it inaccessible to unauthorized entities.
Rigorous Access Control Mechanisms
In tandem with encryption, stringent access controls stand as sentinels at the gates of data ingress and egress points. Through meticulous authentication protocols and granular permission settings, the platform exercises vigilant oversight over user interactions, permitting only authorized personnel to navigate through its digital corridors and interact with sensitive resources.