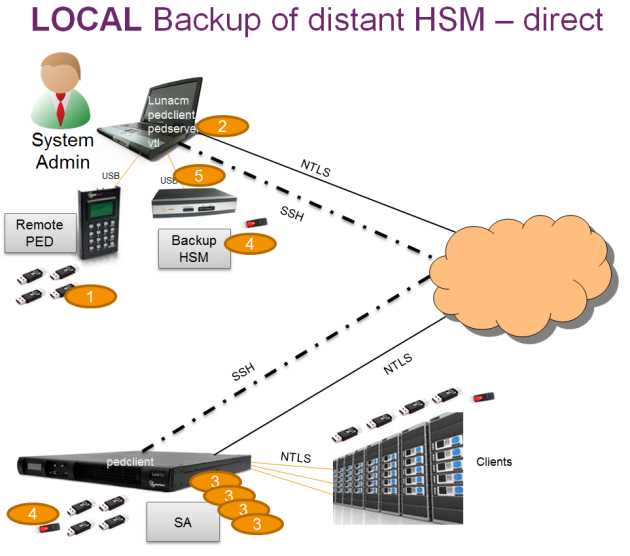
Delve into the intricacies of a revolutionary technology designed to safeguard your digital assets with unparalleled precision and resilience. Embark on a journey through the labyrinthine corridors of cutting-edge security solutions, where every twist and turn reveals a new layer of fortified protection.
Discover the unrivalled strength of a cryptographic fortress meticulously crafted to shield your sensitive data from the relentless onslaught of cyber threats. Uncover the hidden mechanisms that underpin the impregnable bastion standing sentinel against the ever-evolving landscape of digital vulnerabilities.
Peel back the layers of obscurity shrouding the inner workings of this sentinel of security, as we navigate through the enigmatic pathways of its design and implementation. Unlock the secrets that lie at the heart of this technological marvel, empowering you with the knowledge to fortify your digital infrastructure against even the most formidable adversaries.
Luna HSM Datasheet Overview
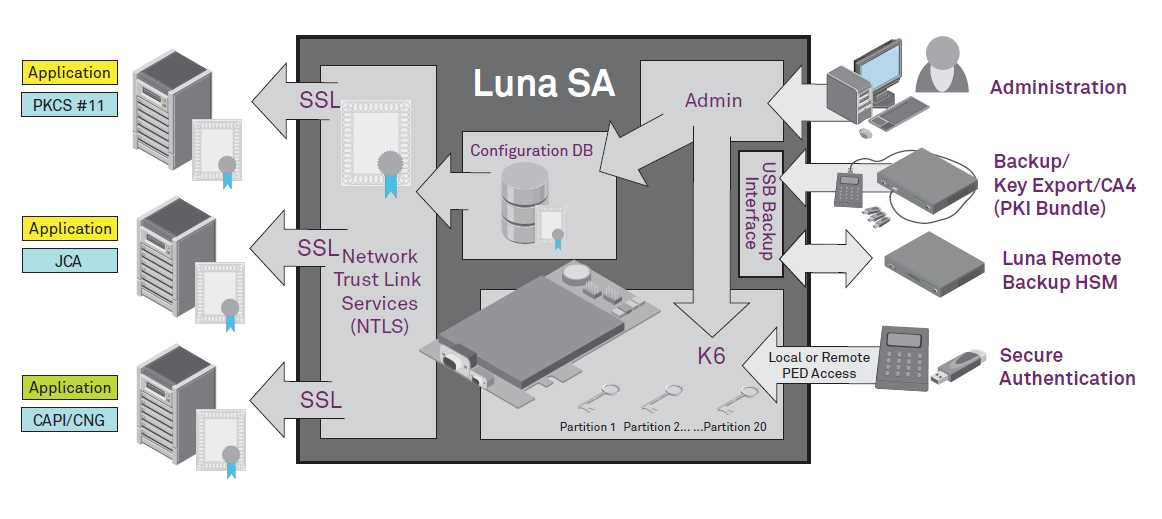
In this section, we provide a comprehensive summary of the document highlighting key features, functionalities, and specifications of the Luna HSM. Delve into an exploration of the device’s capabilities, security measures, and integration options. Gain insight into the robustness and versatility offered by this cutting-edge hardware security module.
- Discover the primary functions and applications of the Luna HSM, encompassing cryptographic operations, key management, and secure data storage.
- Explore the advanced security mechanisms employed within the Luna HSM, ensuring the confidentiality, integrity, and availability of sensitive information.
- Learn about the supported cryptographic algorithms, protocols, and standards, facilitating interoperability and compliance with industry requirements.
- Examine the hardware specifications, including processing power, memory capacity, and connectivity options, essential for deployment in various environments.
- Understand the deployment scenarios and use cases where the Luna HSM excels, ranging from financial institutions to healthcare providers and beyond.
This overview serves as a gateway to comprehending the Luna HSM datasheet in its entirety, offering a glimpse into its significance in safeguarding digital assets and enabling secure transactions.
Features and Specifications of Secure Hardware Security Module (HSM)
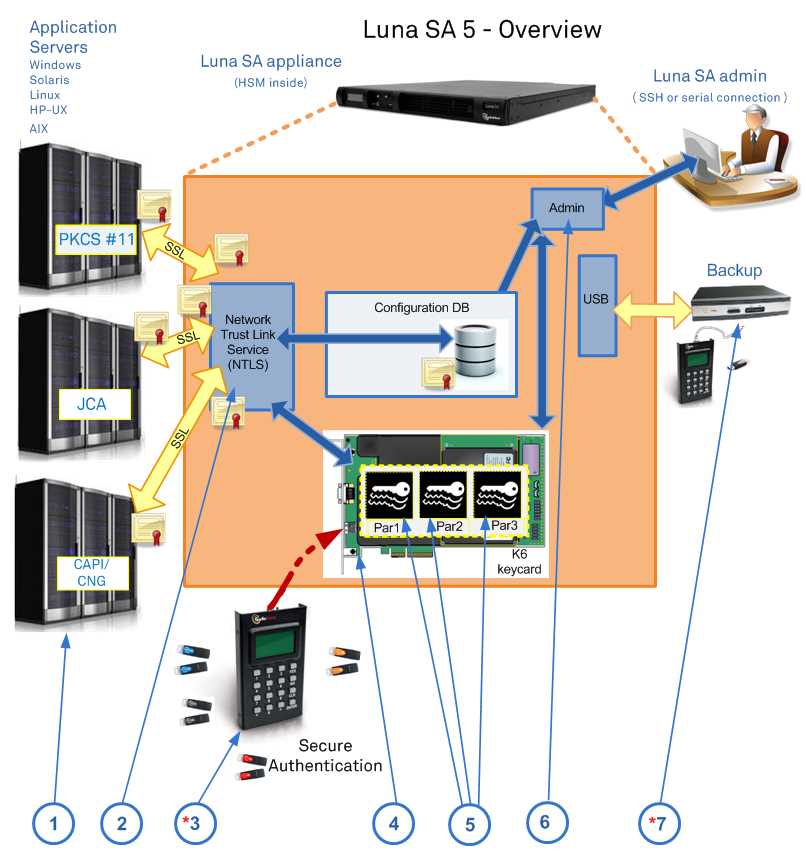
In this section, we delve into the myriad capabilities and technical details encapsulated within the Secure Hardware Security Module (HSM), offering insights into its functionalities and parameters. Discover the intricate workings and performance benchmarks of this formidable security apparatus.
- Robust Encryption Capabilities
- Advanced Key Management
- High-performance Cryptographic Operations
- Secure Storage Mechanisms
- Multi-factor Authentication Support
Delve into the intricacies of its encryption prowess, where data is shielded with an impregnable layer of security. Explore the sophisticated key management system, ensuring the safeguarding of critical cryptographic keys. Witness the seamless execution of cryptographic operations, maintaining optimal performance under demanding conditions.
- Thorough Security Auditing
- Compliance with Industry Standards
- Scalable Architecture
- Resilience against Attacks
Furthermore, delve into its comprehensive security auditing capabilities, providing insights into system integrity and usage patterns. Ensure compliance with industry standards, adhering to regulatory requirements with ease. Witness its scalable architecture, capable of accommodating evolving security needs. Lastly, experience its resilience against a myriad of cyber threats, ensuring the integrity of sensitive data.
Applications and Use Cases of Secure Hardware Security Modules (HSMs)
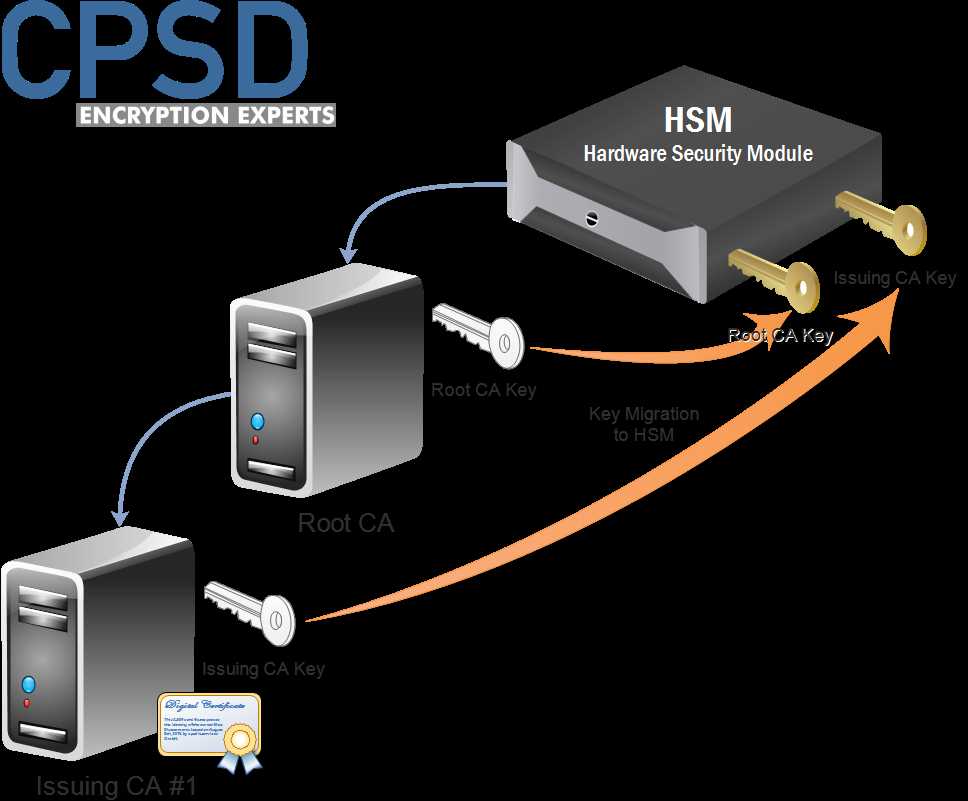
Exploring the diverse array of scenarios where secure hardware security modules (HSMs) play a pivotal role unveils their indispensable nature in modern digital ecosystems. These robust devices serve as guardians of sensitive cryptographic keys and operations, ensuring the integrity, confidentiality, and authenticity of data across various domains.
Financial Sector

- Transaction Security: Safeguarding financial transactions against unauthorized access and fraudulent activities.
- Compliance: Meeting stringent regulatory requirements such as PCI DSS, GDPR, and others by employing tamper-resistant cryptographic modules.
- Key Management: Centralized management of cryptographic keys for secure encryption and decryption processes.
Healthcare Industry
- Protected Health Information (PHI): Securing electronic health records (EHRs) and ensuring patient privacy and confidentiality.
- Medical Device Security: Integrating HSMs into medical devices to prevent unauthorized access and tampering, thereby enhancing patient safety.
- Data Integrity: Verifying the integrity of medical data, including diagnoses, prescriptions, and treatment plans.
Moreover, HSMs find extensive utility in government, cloud computing, IoT, and other sectors where data security is paramount. Their role in enabling secure cryptographic operations, key management, and compliance with industry standards underscores their significance in today’s interconnected digital landscape.