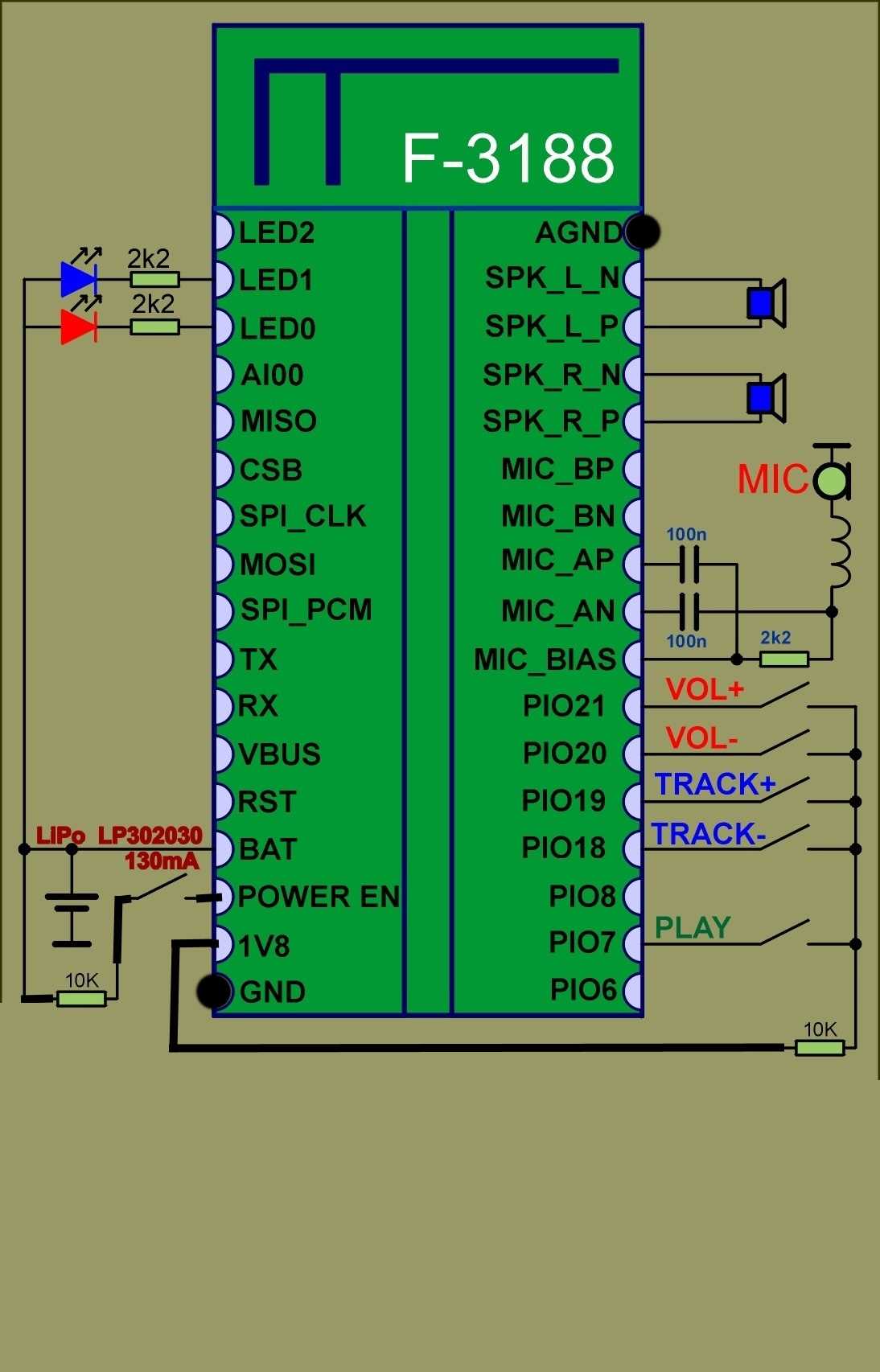
Unlocking the essence of contemporary advancements often lies in the meticulous scrutiny of technical blueprints. Delving into the intricacies of cutting-edge systems, we embark on a journey to decipher the quintessence of innovation, transcending mere documentation.
Embarking upon this odyssey, we navigate through the labyrinth of technical revelations, unveiling the heart and soul of transformative technologies. Within the realm of intricate circuitry and dynamic functionalities, lies a narrative waiting to be deciphered.
Traversing the terrain of technical discourse, we navigate through the lexicon of innovation, venturing beyond the surface to unearth the hidden gems nestled within the framework of evolution. In our quest for enlightenment, we transcend the boundaries of convention, embracing the enigma that propels progress forward.
Understanding the KCX BT003 V1.1 Datasheet: Key Specifications and Features
In this section, we delve into the comprehensive details encapsulated within the documentation of the KCX BT003 V1.1 device, elucidating its intrinsic functionalities and performance metrics. By dissecting its core attributes, we aim to furnish a profound comprehension of the capabilities and intricacies harbored within this technological marvel.
| Aspect | Characteristic |
|---|---|
| Performance Metrics | Explore the operational efficacy and efficiency metrics, unveiling the device’s prowess in handling diverse tasks. |
| Technical Specifications | Unravel the technical nuances, including connectivity options, power requirements, and compatibility with various systems. |
| Functional Attributes | Examine the array of functions endowed within the device, elucidating its versatility and adaptability across different applications. |
| Feature Set | Delve into the distinctive features that distinguish the KCX BT003 V1.1, elucidating its value proposition and competitive edge in the market. |
By navigating through these delineated sections, readers can glean a comprehensive understanding of the KCX BT003 V1.1 device, empowering them to harness its full potential in their respective endeavors.
Unraveling the Technical Specifications
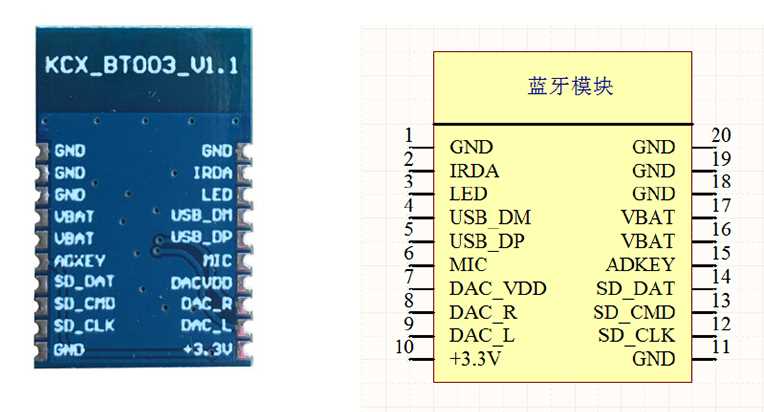
In this section, we delve into the intricate details and nuanced aspects of the technical specifications associated with the aforementioned product variant. By dissecting the underlying specifications, we aim to provide a comprehensive understanding of its capabilities and functionalities.
Understanding the Performance Metrics
First and foremost, it’s imperative to grasp the performance metrics encapsulated within the specifications. These metrics serve as fundamental indicators of the product’s operational efficiency and effectiveness. Through careful analysis, one can decipher the intricacies of its performance across various parameters.
Exploring the Functional Attributes
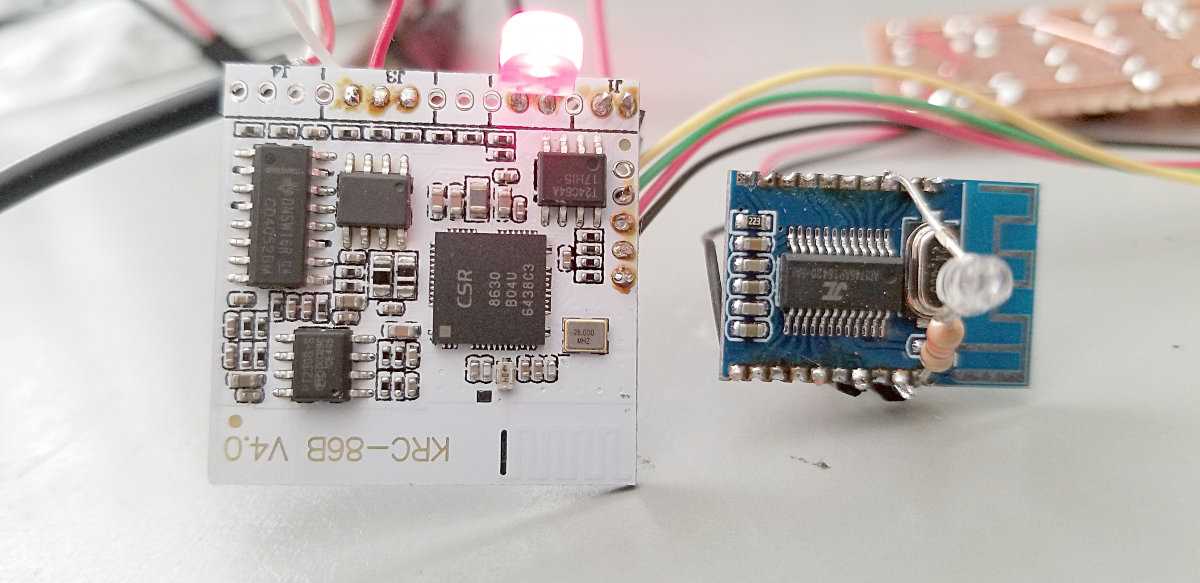
Beyond mere performance metrics, it’s equally crucial to explore the functional attributes delineated within the specifications. These attributes elucidate the diverse functionalities and features embedded within the product. By unraveling these aspects, users can discern the breadth and depth of its utility across different applications and scenarios.
- Comprehensive Examination of Operational Capabilities
- Analyzing the Technical Architecture
- Evaluating Compatibility and Integration
- Assessing Environmental Considerations
Through a systematic exploration of the technical specifications, one can glean valuable insights into the product’s performance, functionality, and compatibility, thereby facilitating informed decision-making and utilization.
Exploring the Functionalities and Applications
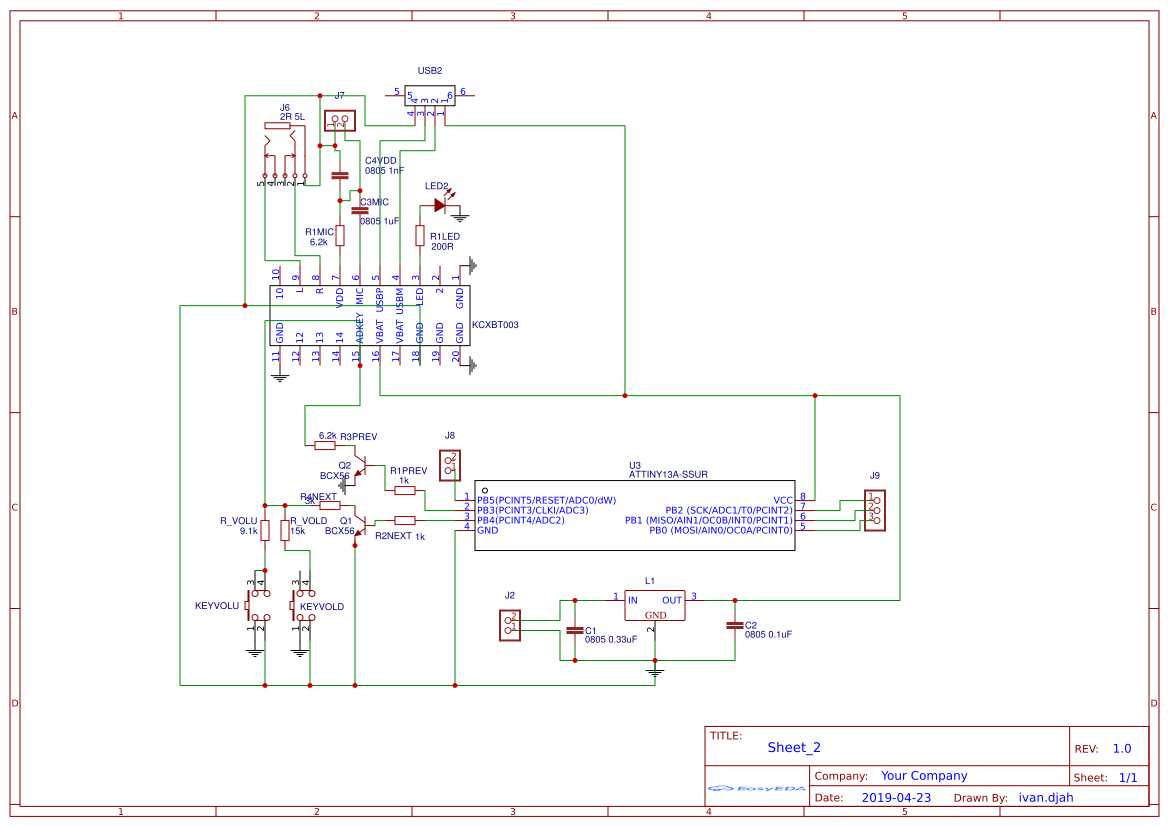
In this segment, we delve into the diverse array of capabilities and practical uses encompassed within the realm of the technology under scrutiny. We embark on a journey to unveil the multifaceted nature of its functionalities and the broad spectrum of applications it facilitates.
The Versatile Features
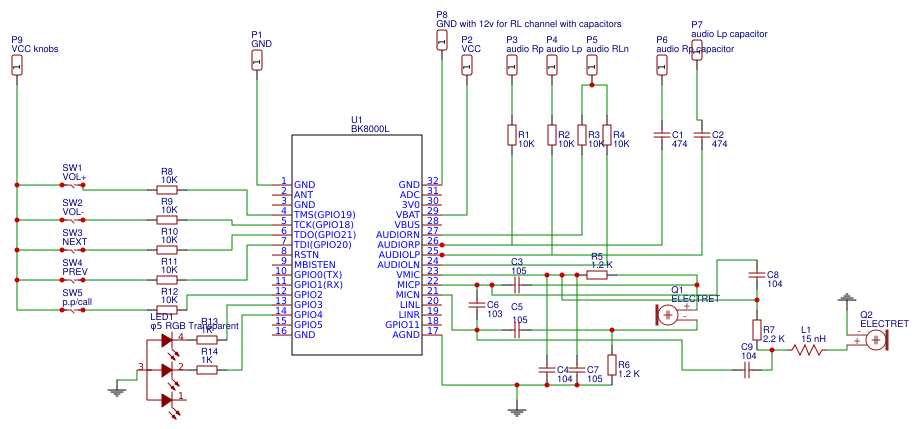
Within the realm of this technology, lies a tapestry of versatile features waiting to be unraveled. These attributes offer a dynamic range of possibilities, from intricate operations to seamless integrations, fostering innovation and adaptability.
Practical Implementations
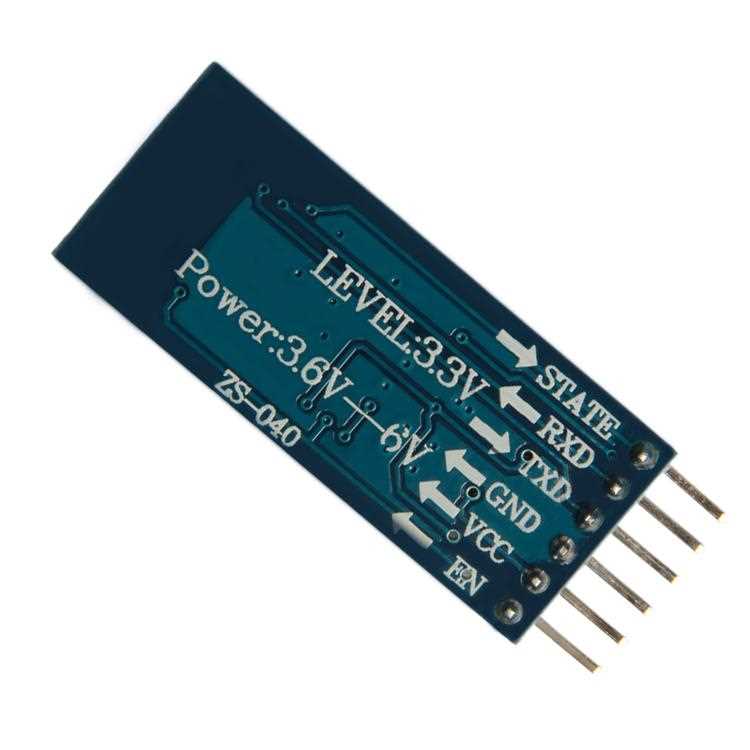
As we navigate through its functionalities, we uncover a tapestry of practical applications that span across industries and disciplines. From enhancing efficiency in industrial processes to revolutionizing consumer electronics, the applications are as diverse as they are impactful.
Optimizing Usage: Strategies and Best Practices
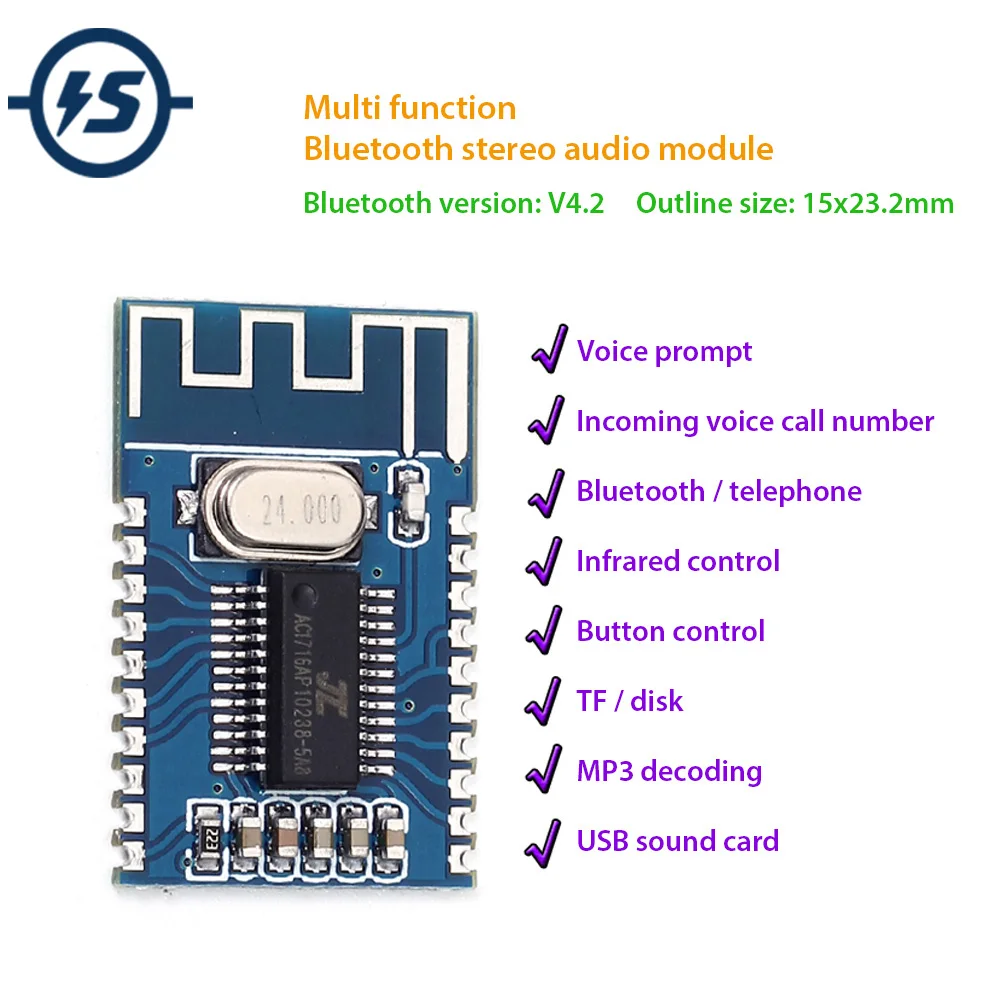
In this section, we delve into enhancing the utilization of the technology discussed earlier, focusing on maximizing its efficiency and effectiveness. By implementing thoughtful approaches and adopting recommended techniques, users can extract the utmost benefit from the device, ensuring seamless performance and prolonged lifespan.
| 1. Enhance Efficiency through Customization | Customize settings and configurations to align the device with specific requirements and operational environments. Tailoring the functionality enhances adaptability and streamlines processes, resulting in optimized performance. |
| 2. Implement Regular Maintenance Protocols | Establish routine maintenance procedures to uphold the device’s functionality and mitigate potential issues. Regular inspections, cleaning, and software updates are paramount to sustain optimal performance and prevent degradation over time. |
| 3. Ensure Adequate Power Management | Manage power consumption effectively to prolong battery life and maintain consistent operation. Utilize power-saving modes and implement energy-efficient practices to optimize usage duration and reduce environmental impact. |
| 4. Foster User Education and Training | Empower users with comprehensive training programs to maximize proficiency and competency in utilizing the device. Well-informed users are better equipped to leverage advanced features and functionalities, driving productivity and innovation. |
| 5. Implement Security Measures | Integrate robust security protocols to safeguard sensitive data and protect against potential threats. Implement encryption, authentication mechanisms, and regular security audits to ensure the integrity and confidentiality of information. |
By incorporating these strategies and adhering to best practices, users can optimize the utilization of the technology, unlocking its full potential and achieving superior performance outcomes.