
Empower your infrastructure with advanced defenses tailored to the demands of modern digital ecosystems. Discover a comprehensive solution designed to fortify your network perimeter and shield vital assets against digital threats.
Unlock innovative technologies crafted to safeguard sensitive information and ensure uninterrupted operations. Seamlessly integrate robust measures that adapt to the dynamic landscape of cybersecurity challenges.
Elevate your defensive posture with a suite of proactive measures engineered to anticipate and neutralize emerging threats. Bolster your organization’s resilience with a strategic approach to safeguarding critical data and preserving operational continuity.
Comprehensive Overview of Advanced Protection Solutions
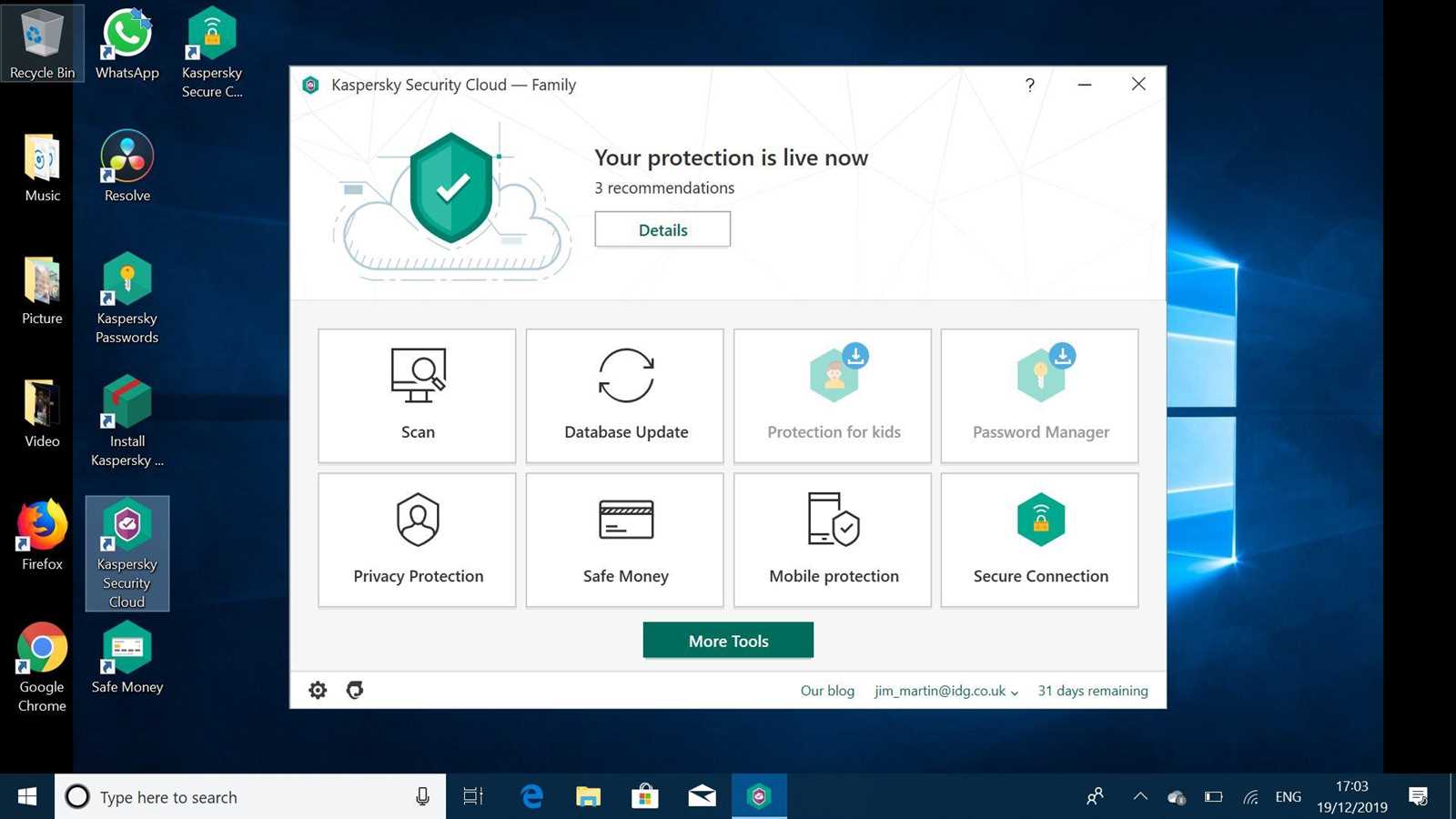
In this segment, we delve into an in-depth exploration of a cutting-edge suite of defensive technologies aimed at fortifying your digital environment. Delve into the realm where innovation meets resilience as we unravel the intricacies of safeguarding your virtual assets against a myriad of digital threats.
Unveiling Enhanced Shielding Mechanisms: Discover how our state-of-the-art methodologies intertwine seamlessly to create an impenetrable barrier, shielding your infrastructure from the relentless barrage of contemporary cyber assailants.
Empowering Your Digital Fort: Learn how our solution, through a fusion of adaptive strategies and proactive measures, bolsters the defenses of your digital stronghold, ensuring unparalleled protection against diverse forms of malevolent intrusions.
Augmented Vigilance: Explore the intricately woven tapestry of surveillance mechanisms meticulously crafted to maintain a vigilant watch over your digital domain, preempting potential threats before they materialize into tangible risks.
Propelling Resilience through Innovation: Embark on a journey through the realm of innovation, where every technological advancement serves as a cornerstone in fortifying your digital infrastructure, fostering an environment of resilience amidst the ever-evolving threat landscape.
Empowering Your Defenses: Witness the convergence of cutting-edge technologies and unparalleled expertise as we equip you with the tools necessary to combat the myriad of challenges posed by today’s digital adversaries, empowering you to navigate the digital realm with confidence and peace of mind.
Understanding the Essentials of Dynamic Cloud Protection
In today’s interconnected digital landscape, safeguarding data across diverse computing environments is paramount. This section delves into the core principles underpinning robust defenses in fluid computing ecosystems.
Adaptable Defense Strategies
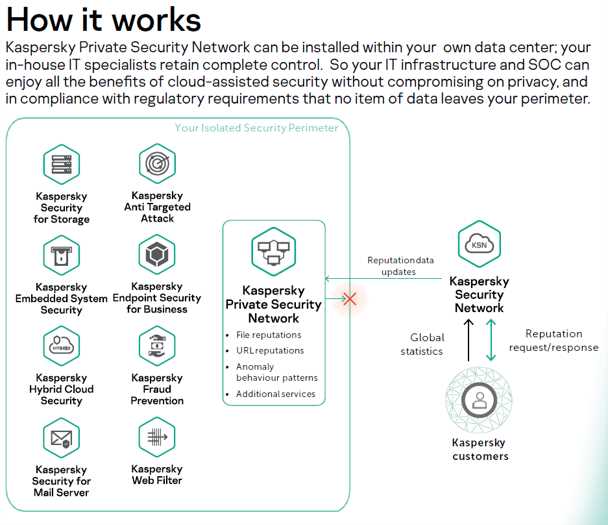
Effective security in modern IT ecosystems necessitates strategies that seamlessly adapt to evolving threats and infrastructures. By leveraging dynamic methodologies, organizations can fortify their digital perimeters against an array of potential hazards.
Interconnected Risk Mitigation

Hybrid cloud environments introduce a tapestry of interconnected risks, ranging from traditional on-premises vulnerabilities to novel cloud-specific threats. Understanding the nuanced interplay between these disparate elements is essential for crafting comprehensive risk mitigation frameworks that transcend traditional security paradigms.
Features of Cutting-Edge Cloud Protection Solution

In this section, we delve into the myriad capabilities that define the dynamic essence of our innovative cloud security solution. Through a comprehensive analysis of its functionalities, users gain insight into the robust defenses and adaptive mechanisms embedded within.
Advanced Threat Detection
Experience unparalleled detection prowess with our solution’s advanced threat identification algorithms, engineered to swiftly pinpoint and neutralize emerging risks. Through a blend of heuristic analysis and behavioral monitoring, potential threats are intercepted and thwarted before they can materialize into full-fledged breaches.
Intelligent Adaptive Controls
Empower your security infrastructure with intelligent adaptive controls, ensuring a proactive stance against evolving threats. Through real-time data analytics and contextual insights, our solution dynamically adjusts its defense mechanisms to align with shifting threat landscapes, fortifying your digital ecosystem with precision and agility.
| Feature | Description |
|---|---|
| Automated Incident Response | Efficiently mitigate potential security incidents through automated response protocols, minimizing downtime and preserving operational continuity. |
| Scalable Performance | Scale your security infrastructure effortlessly to accommodate fluctuating workloads and evolving organizational needs, ensuring consistent protection across dynamic environments. |
| Comprehensive Visibility | Gain comprehensive visibility into your cloud environment, enabling proactive threat hunting and informed decision-making to bolster your security posture. |
Exploring the Advanced Capabilities and Benefits
In this section, we delve into the sophisticated functionalities and advantages that emerge from the fusion of cutting-edge technologies. Here, we unravel the intricate tapestry of features that contribute to heightened efficiency, fortified defenses, and streamlined operations. Through a meticulous examination, we uncover the manifold benefits awaiting those who harness this innovative solution.
| Feature | Description |
| Intelligent Threat Detection | Utilizing advanced algorithms and behavioral analysis to identify and neutralize potential risks proactively. |
| Dynamic Scalability | Adapting seamlessly to fluctuating demands, ensuring optimal performance without compromising on resource allocation. |
| Unified Management Interface | Streamlining administrative tasks through a centralized platform, enhancing oversight and control across diverse environments. |
| Real-time Analytics | Providing actionable insights instantaneously, empowering stakeholders to make informed decisions swiftly. |
| Resilient Architecture | Engineered to withstand evolving threats and challenges, bolstering resilience and fortifying the digital infrastructure. |
Furthermore, by amalgamating these state-of-the-art components, organizations stand to achieve heightened agility, fortified resilience, and unparalleled peace of mind. The synergistic blend of advanced capabilities equips enterprises with a competitive edge in navigating the complexities of the digital landscape, propelling them towards sustained success and innovation.
Implementing Comprehensive Protection in the Cloud Environment

Incorporating a holistic shield within your digital infrastructure is paramount to fortifying your cloud-based operations. This section elucidates the procedural roadmap for integrating an advanced defense mechanism tailored for contemporary cloud landscapes.
| Step | Action |
|---|---|
| 1 | Assessing Infrastructure Vulnerabilities |
| 2 | Formulating Customized Defense Strategies |
| 3 | Deploying Adaptive Security Measures |
| 4 | Continuous Monitoring and Fine-Tuning |
The implementation process revolves around a meticulous evaluation of system susceptibilities, followed by the design and execution of bespoke protective measures. By weaving together adaptive protocols and vigilant oversight, enterprises can fortify their cloud ecosystem against a myriad of cyber threats.