
Delving into the intricacies of cutting-edge technology often leads us down a labyrinth of innovation and precision. Within the realm of advanced electronics, there exists a realm of documents that serve as gateways to understanding, akin to maps guiding explorers through uncharted territories.
Embark with us on a journey where we navigate through the blueprint of a technological marvel, deciphering its capabilities, unraveling its complexities, and uncovering the essence that propels it forward.
Peering into the core of this enigma, we eschew the confines of conventional jargon to reveal the heart of its functionality. Join us as we traverse through a narrative woven with threads of innovation, tracing the evolution of concepts into tangible realities.
Exploring the Features of ISR 2900 Datasheet
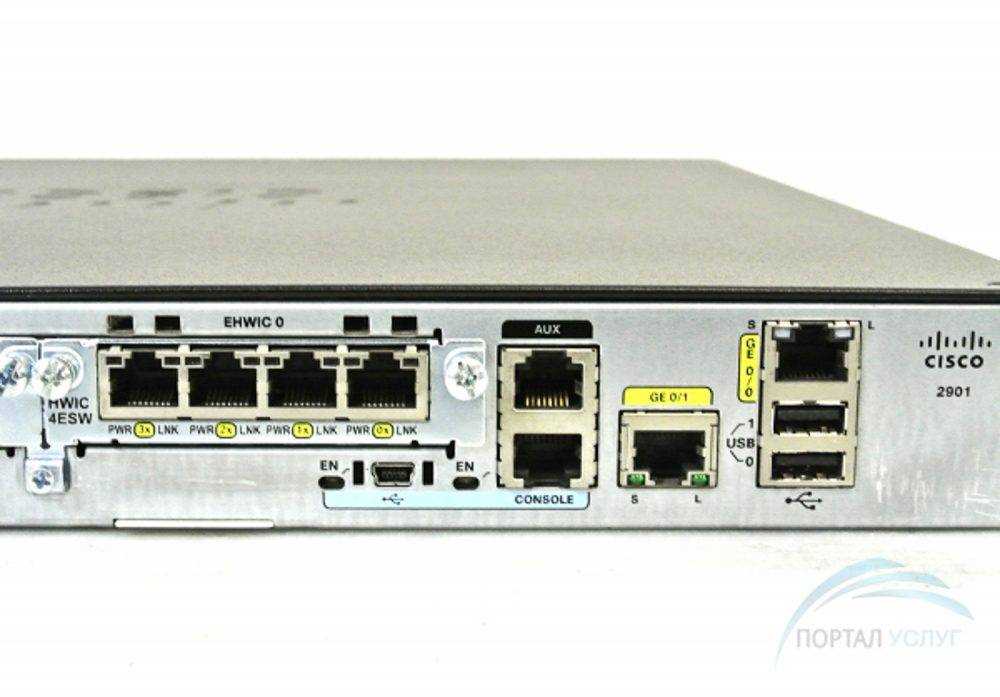
In this section, we delve into the myriad capabilities and functionalities encapsulated within the comprehensive documentation of the ISR 2900 series. Unraveling the intricacies of this versatile system, we navigate through a landscape teeming with innovation and efficiency.
Unveiling Advanced Functionalities
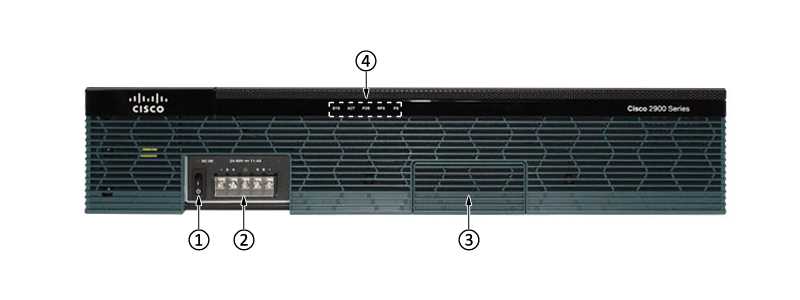
Embark on a journey through the labyrinth of cutting-edge features meticulously outlined within the ISR 2900 datasheet. From robust networking solutions to seamless integration possibilities, discover a treasure trove of technological prowess.
Unlocking Performance Potential

Delve deeper into the performance benchmarks and operational capacities delineated within the ISR 2900 datasheet. Uncover the secrets to harnessing maximum efficiency and optimizing resource utilization, propelling your endeavors to new heights of success.
Understanding the Architecture and Performance

In delving into the intricacies of this technology, it becomes paramount to grasp the underlying framework and operational efficiency without merely skimming through technical specifications. This section aims to illuminate the fundamental structure and operational prowess, shedding light on the mechanisms driving its functionality and the benchmarks shaping its performance.
- Core Design: Exploring the heart of the system entails dissecting its core design, deciphering the interplay of components and their orchestrated synergy. From processing units to data flow management, every facet contributes to the cohesive architecture.
- Functional Modules: Beyond the surface, lies a network of functional modules, each serving a distinct purpose in the grand scheme. Understanding their roles elucidates the system’s versatility and adaptability in handling diverse tasks and workloads.
- Optimization Strategies: Unveiling the secrets of performance entails a closer examination of optimization strategies employed. From hardware enhancements to algorithmic refinements, each tactic fine-tunes the system’s capabilities, maximizing efficiency and throughput.
- Scalability and Flexibility: A hallmark of superior architecture lies in its scalability and flexibility. Exploring how the system accommodates growth and adapts to evolving demands provides insights into its longevity and adaptability in dynamic environments.
- Performance Metrics: Quantifying performance transcends raw numbers; it encompasses a holistic view of efficiency, reliability, and responsiveness. Delving into performance metrics unveils the nuanced evaluation criteria shaping its operational excellence.
By delving into these dimensions, a comprehensive understanding of the architecture and performance emerges, empowering stakeholders to harness its full potential and navigate the technological landscape with confidence and clarity.
Highlighting Key Security Protocols

In this section, we delve into essential security measures integral to the ISR 2900 series, elucidating the fortifications crucial for safeguarding data integrity and confidentiality. Emphasizing the paramount importance of robust security frameworks, we explore foundational principles, cryptographic mechanisms, and authentication methodologies employed to thwart unauthorized access and mitigate potential vulnerabilities.
Encryption Algorithms and Protocols

One cornerstone of secure communication is the implementation of advanced encryption algorithms and protocols. These cryptographic techniques ensure that data transmitted across networks remains confidential and tamper-proof. By leveraging encryption methodologies such as AES (Advanced Encryption Standard) and TLS (Transport Layer Security), the ISR 2900 series fosters a secure environment where sensitive information is shielded from prying eyes.
Access Control Mechanisms

Effective access control mechanisms serve as gatekeepers, regulating the flow of data within network infrastructures. Through the utilization of robust authentication protocols like RADIUS (Remote Authentication Dial-In User Service) and TACACS+ (Terminal Access Controller Access-Control System Plus), the ISR 2900 series bolsters its defenses against unauthorized intrusion attempts. These protocols authenticate users, validate their credentials, and enforce access policies, ensuring that only authorized personnel gain entry to critical resources.
- Implementing encryption algorithms such as AES and TLS
- Utilizing authentication protocols like RADIUS and TACACS+
- Enforcing access control policies to regulate data flow
Integration and Compatibility with Networking Systems

In the realm of network connectivity, seamless integration and compatibility are paramount. This section explores the harmonious coalescence of our technological solutions with various networking systems. It delves into the intricate dance of interoperability and synergy, where our products intertwine with diverse networking environments to deliver robust performance and streamlined operations.
- Interoperability: Our solutions seamlessly interact with a spectrum of networking infrastructures, fostering cohesion and fluid communication across heterogeneous systems.
- Protocol Compatibility: Embracing a plethora of networking protocols, our offerings ensure fluent interaction with industry-standard communication frameworks, promoting universal accessibility and versatility.
- Hardware Integration: Our products are engineered to seamlessly integrate with a diverse array of networking hardware, facilitating effortless deployment and minimizing compatibility concerns.
- Software Compatibility: With comprehensive software compatibility, our solutions synchronize effortlessly with various networking management platforms, empowering administrators with cohesive control and oversight.
- Scalability: Built to scale, our offerings adapt dynamically to evolving networking infrastructures, ensuring sustained performance and adaptability in the face of expanding operational demands.
By prioritizing integration and compatibility, we empower organizations to forge robust networking ecosystems that transcend barriers, enabling seamless communication, enhanced efficiency, and unparalleled connectivity.