
In the realm of safeguarding online platforms, ensuring robust protection against cyber threats remains paramount. As digital landscapes evolve, the fortification of web applications against malicious intrusions stands as a cornerstone in preserving data integrity and user trust. This entails the deployment of advanced defensive measures, adept at identifying and thwarting diverse forms of cyberattacks.
Exploring the Landscape of Web Application Security
Within the expansive domain of safeguarding online assets, the realm of web application security emerges as a critical frontier. It encompasses a multifaceted approach aimed at shielding digital infrastructures from an array of potential threats, ranging from common vulnerabilities to sophisticated cyber assaults. By leveraging a combination of proactive strategies and reactive mechanisms, organizations endeavor to fortify their web presence, ensuring resilience amidst an ever-evolving threat landscape.
Unveiling the Essence of Protection Mechanisms
Central to the paradigm of web application security lies a repertoire of protection mechanisms designed to thwart diverse vectors of attack. These encompass a spectrum of defensive strategies, ranging from robust access controls and encryption protocols to Intrusion Detection Systems (IDS) and heuristic analysis algorithms. Through the orchestration of these elements, organizations endeavor to erect an impenetrable shield around their digital assets, fostering trust and confidence among users.
Understanding the Document Detailing Imperva’s Web Application Firewall
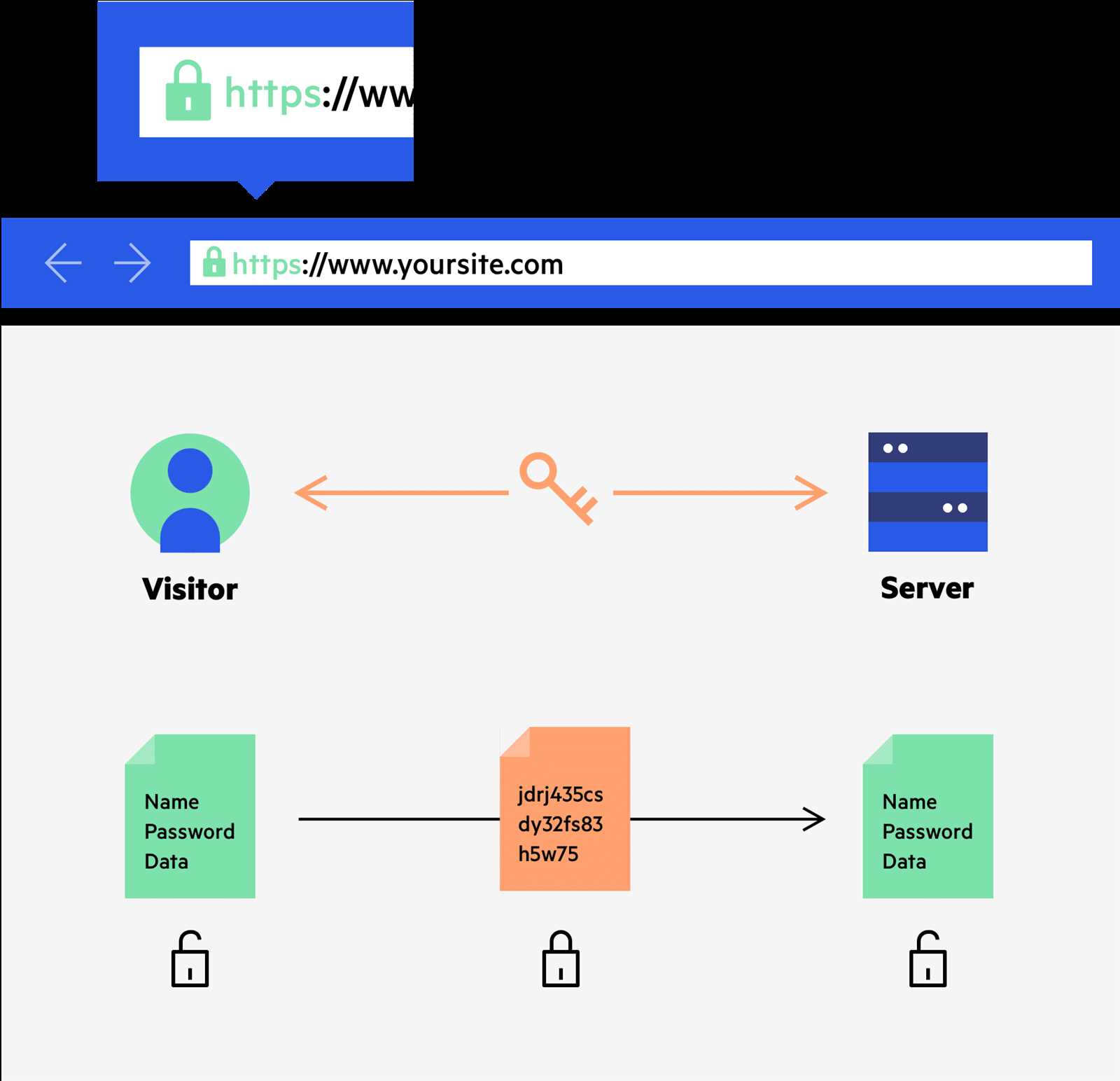
In delving into the intricacies of comprehending the documentation associated with Imperva’s safeguarding solution for web applications, one embarks on a journey of understanding the core functionalities, capabilities, and operational nuances encapsulated within.
The document elucidates a comprehensive portrayal of the manifold features and functionalities embedded within the protective framework, allowing stakeholders to glean insights into its efficacy, deployment methodologies, and operational intricacies.
- Exploring the document unveils a plethora of insights into the shielding mechanisms aimed at fortifying web applications against a spectrum of cyber threats.
- It delineates the operational parameters, furnishing an overview of configuration options, logging mechanisms, and incident response protocols.
- Furthermore, the document elucidates the scalability facets, providing stakeholders with a nuanced understanding of its adaptability to diverse organizational infrastructures and operational exigencies.
Delving deeper, one encounters elucidations on the interpretative facets, deciphering the metrics, thresholds, and performance benchmarks that underpin the operational efficacy of the safeguarding apparatus.
Moreover, the document extends beyond a mere enumeration of features, encapsulating real-world deployment scenarios, use cases, and best practices, thereby empowering stakeholders with pragmatic insights into maximizing the utility of the solution.
In essence, navigating through the intricacies of this documentation enriches stakeholders with a comprehensive understanding of Imperva’s web application firewall solution, fostering informed decision-making and proactive risk mitigation strategies.
Exploring Key Features and Capabilities

In this section, we delve into the fundamental aspects that distinguish the solution under scrutiny. Highlighting its core functionalities and advanced attributes, we aim to provide a comprehensive understanding of its operational prowess and potential benefits.
Advanced Functionality
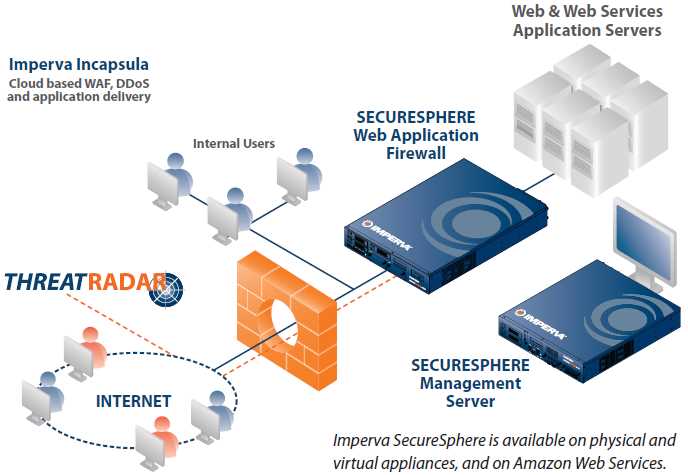
At the heart of this offering lies a suite of advanced functionalities that cater to the intricate demands of modern cybersecurity landscapes. From its nuanced threat detection mechanisms to its robust mitigation strategies, every facet of its operation is meticulously crafted to confront emerging challenges head-on.
Versatile Capabilities
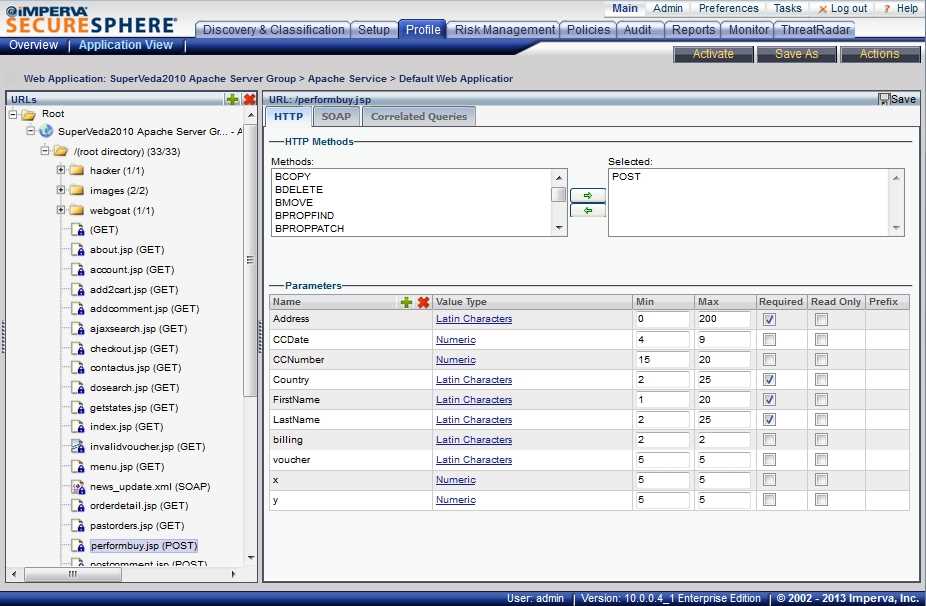
Beyond its fundamental functionalities, the solution boasts a spectrum of versatile capabilities that adapt to diverse operational environments. Whether safeguarding against sophisticated cyberattacks or facilitating seamless integration with existing infrastructures, its versatility ensures adaptive resilience in the face of evolving threats.
Optimizing Security with Advanced Web Application Firewall Solutions
In the realm of cybersecurity, ensuring robust protection for your web applications is paramount. Enhancing the security posture involves deploying sophisticated defense mechanisms capable of safeguarding against a myriad of threats. In this regard, leveraging cutting-edge Web Application Firewall (WAF) solutions proves indispensable.
The Essence of Proactive Defense
Effective security strategies entail proactive measures that anticipate and mitigate potential risks before they manifest into full-fledged threats. Within the realm of web application security, a proactive approach involves implementing advanced WAF solutions that dynamically adapt to emerging attack vectors and vulnerabilities.
- **Dynamic Threat Detection:** By employing intelligent algorithms and real-time analysis, modern WAF systems excel at identifying and thwarting malicious activities without impeding legitimate traffic.
- **Behavioral Analysis:** Through continuous monitoring and behavioral analysis, WAF solutions can detect anomalies indicative of suspicious behavior, allowing for timely intervention and mitigation.
- **Virtual Patching:** WAFs provide a virtual patching mechanism, allowing organizations to address vulnerabilities in real-time, reducing the window of exploitation and enhancing overall security resilience.
Streamlining Security Operations
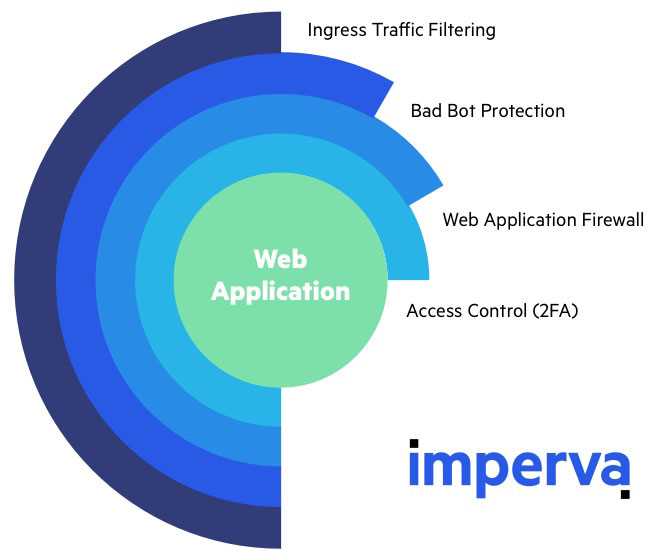
Optimizing security operations entails streamlining processes and enhancing efficiency without compromising on the efficacy of defensive measures. WAF solutions play a pivotal role in this endeavor, offering comprehensive functionalities that empower security teams to effectively manage and mitigate risks.
- **Centralized Management:** Advanced WAF platforms offer centralized management consoles that provide holistic visibility into web traffic, allowing for centralized policy management and streamlined configuration.
- **Automated Threat Response:** Leveraging automation, WAF solutions can automate threat response mechanisms, enabling rapid incident response and mitigation without human intervention.
- **Integration Capabilities:** Seamless integration with existing security infrastructure and third-party solutions ensures interoperability and facilitates a cohesive security ecosystem, enhancing overall defense capabilities.
Embracing advanced Web Application Firewall solutions is instrumental in fortifying your security posture, enabling proactive defense mechanisms, and streamlining security operations to effectively combat evolving cyber threats.
Best Practices and Implementation Strategies
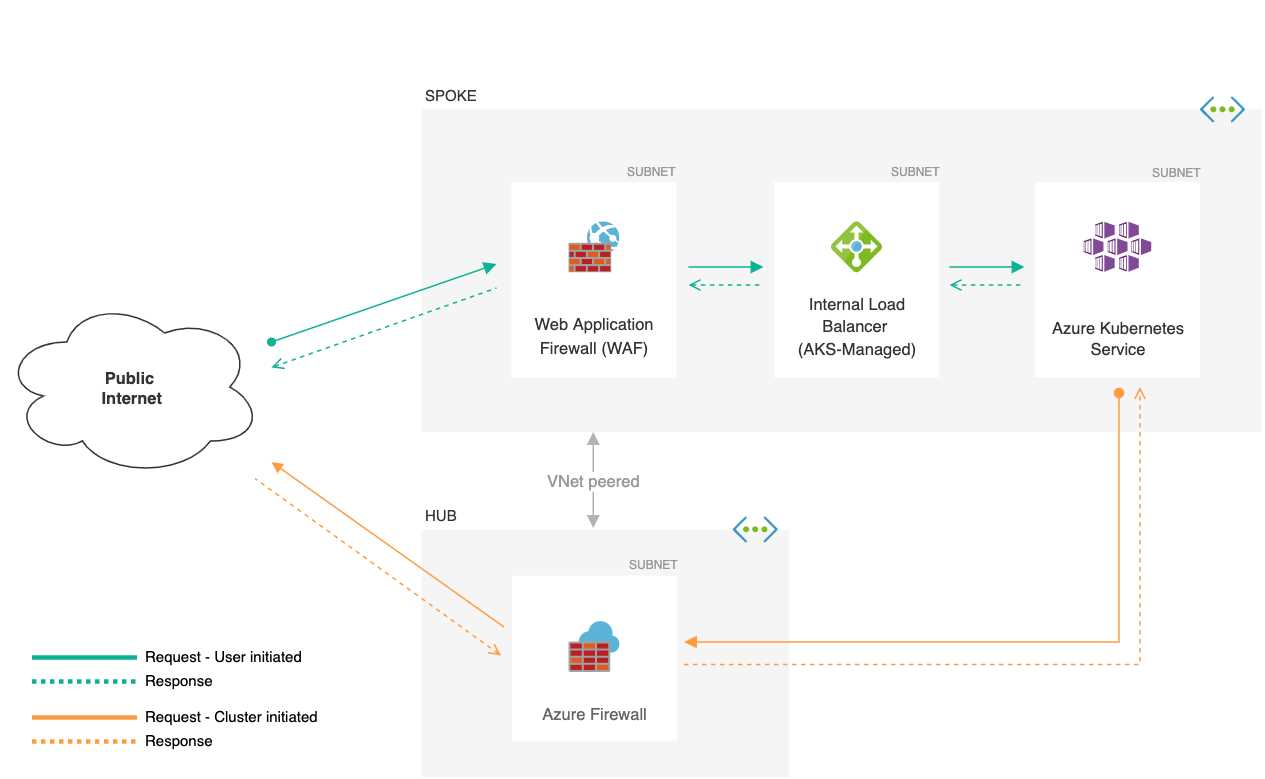
Exploring optimal methods and approaches for deploying and managing web application firewalls (WAFs) involves a nuanced understanding of security protocols and digital fortification. In this section, we delve into effective strategies and guidelines aimed at fortifying digital perimeters and safeguarding against emerging threats.
1. Proactive Defense Mechanisms: Prioritizing preemptive measures is paramount in the realm of cyber defense. Establishing robust security protocols that anticipate potential vulnerabilities and swiftly respond to evolving attack vectors is foundational.
2. Contextual Awareness: Contextualizing threats within the broader landscape of cybersecurity aids in devising tailored defense strategies. Understanding the intricacies of web traffic patterns and discerning legitimate requests from malicious intent empowers effective threat mitigation.
3. Continuous Monitoring and Adaptation: Embracing a dynamic security posture involves continual vigilance and adaptation. Implementing mechanisms for real-time monitoring and response enables swift detection and mitigation of emerging threats, fostering resilience in the face of evolving cyber risks.
4. Collaborative Engagement: Engaging in collaborative partnerships within the cybersecurity community facilitates knowledge sharing and fosters collective resilience. Leveraging insights from industry peers and security experts enriches defense strategies and enhances overall cyber preparedness.
5. Holistic Risk Management: Adopting a holistic approach to risk management involves integrating security measures seamlessly into organizational frameworks. Balancing the imperatives of functionality and security cultivates a culture of resilience, ensuring that protective measures align with overarching business objectives.
6. Embracing Automation: Harnessing the power of automation streamlines security operations and bolsters response capabilities. Automating routine tasks and implementing intelligent defense mechanisms augments efficiency and enables rapid response to emerging threats.
7. Compliance and Regulatory Adherence: Adhering to regulatory standards and compliance frameworks is essential in maintaining operational integrity and instilling trust among stakeholders. Aligning security practices with industry regulations mitigates legal and reputational risks, bolstering organizational credibility.
By adhering to these best practices and implementation strategies, organizations can fortify their digital defenses and navigate the complex landscape of cybersecurity with confidence and resilience.
Comparing Imperva WAF to Alternatives

In this section, we delve into an insightful comparison between the security features, performance capabilities, and overall effectiveness of Imperva’s Web Application Firewall (WAF) and other similar solutions available in the market. We explore the diverse array of functionalities and protective measures offered by these alternatives, aiming to provide a comprehensive understanding of their respective strengths and limitations.
Security Features

When evaluating different WAF solutions, one paramount consideration is the breadth and depth of security features they offer. This encompasses not only the ability to detect and mitigate various types of web threats but also the robustness of their defense mechanisms against emerging attack vectors. We delve into the specifics of how each alternative addresses common vulnerabilities such as SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks, emphasizing the importance of comprehensive threat coverage.
Performance and Scalability
Besides security efficacy, the performance and scalability of a WAF solution play a pivotal role, particularly in high-traffic environments where minimal latency and maximum throughput are imperative. We scrutinize the performance metrics of Imperva WAF alongside its counterparts, examining factors like request processing speed, resource utilization efficiency, and scalability across distributed architectures. Additionally, we assess the ease of integration with existing infrastructures and the flexibility to accommodate evolving workload demands.
| Criteria | Imperva WAF | Alternative A | Alternative B |
|---|---|---|---|
| Security Features | Comprehensive coverage of common vulnerabilities | Robust protection against emerging threats | Versatile defense mechanisms |
| Performance | Optimized request processing | High throughput with minimal latency | Efficient resource utilization |
| Scalability | Ability to scale across distributed environments | Flexible integration with existing infrastructures | Adaptability to changing workload demands |