
Embark on a journey into the realm of integrated security solutions, where the fusion of cutting-edge technologies harmonizes with the demands of modern security landscapes. Delve into a realm where seamless integration converges with unparalleled efficiency, offering a glimpse into the future of safeguarding assets and ensuring peace of mind.
Explore the intricacies of a revolutionary blueprint designed to transcend conventional boundaries, where innovation intersects with necessity. Within these pages, discover the embodiment of precision, where every component synergizes effortlessly, forming a symphony of security unparalleled in its scope and effectiveness.
Unravel the layers of sophistication that underpin this formidable arsenal, where intuitive design meets uncompromising performance. Join us as we navigate through a tapestry of features and functionalities meticulously crafted to cater to the diverse needs of today’s security ecosystem.
Unlocking Security Potential: Exploring Comprehensive Product Information
In this segment, we delve into an in-depth analysis of the multifaceted features and capabilities encapsulated within the document under scrutiny. We navigate through a plethora of details meticulously curated to empower security stakeholders with a comprehensive understanding of the offered solution.
|
Understanding Functionality Embark on a journey through the functional intricacies, unraveling the mechanisms designed to fortify security frameworks. Discover how each component synergistically integrates to bolster the overall resilience against potential threats. |
Exploring Integration Options Probe into the diverse integration pathways delineated within the document, facilitating seamless compatibility with existing infrastructures. Uncover the spectrum of possibilities awaiting exploration, fostering adaptive security architectures. |
|
Unveiling Deployment Strategies Delve into the strategic deployment methodologies outlined, tailored to cater to a myriad of operational environments. Navigate through deployment blueprints crafted to optimize resource utilization while maximizing security efficacy. |
Examining Performance Metrics Scrutinize the performance metrics meticulously documented, providing insights into the solution’s operational efficiency and efficacy. Evaluate benchmarks set forth to gauge performance thresholds and enhance operational workflows. |
Understanding Synergis: Key Features and Benefits

In this section, we delve into the essence of Synergis, exploring its myriad functionalities and advantages. Discover the core components that make Synergis a powerful solution for enhancing security and access control systems.
Comprehensive Security Integration

Synergis offers seamless integration with various security systems, consolidating access control, video surveillance, and alarm monitoring into a unified platform. This integration fosters synergy among disparate security elements, streamlining operations and bolstering overall security posture.
Advanced Access Control Capabilities

Unlock a wealth of advanced access control features with Synergis, empowering organizations to enforce granular access policies, manage credentials efficiently, and monitor access events in real-time. From biometric authentication to role-based access control, Synergis equips users with robust tools to safeguard assets and sensitive areas effectively.
Integration Excellence: Compatibility and Interoperability
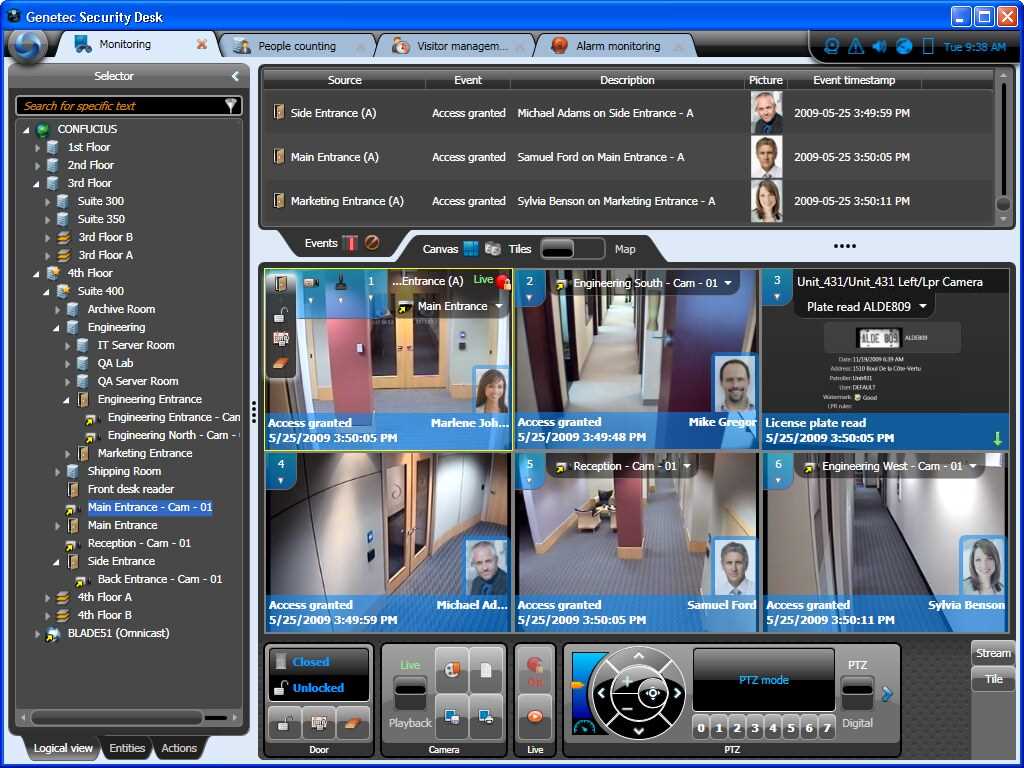
In this section, we delve into the seamless fusion of systems, exploring the harmonious interaction and seamless connectivity that characterize the integration prowess of the Synergis platform. Our focus lies in elucidating the intricate dance of compatibility and interoperability, where diverse components synergize effortlessly to elevate operational efficacy and streamline workflows.
Embracing Compatibility: The foundation of integration excellence lies in the ability of disparate technologies to converge without friction. Synergis exemplifies this ethos, fostering a landscape where systems, protocols, and hardware seamlessly align, transcending boundaries to create a unified ecosystem. Through meticulous engineering and meticulous testing, Synergis ensures that compatibility isn’t just an aspiration but a tangible reality, empowering users with a versatile toolkit that adapts to diverse environments and requirements.
Fostering Interoperability: Beyond mere compatibility, Synergis champions interoperability–a dynamic synergy that transcends static connections. Interoperability embodies the fluid exchange of data, commands, and insights, fostering a collaborative environment where disparate entities communicate harmoniously. Whether integrating with legacy systems or cutting-edge innovations, Synergis serves as a unifying force, bridging gaps and unlocking new dimensions of operational efficiency.
The Nexus of Integration: At the nexus of compatibility and interoperability lies the true essence of integration excellence. Here, Synergis orchestrates a symphony of connections, orchestrating a seamless exchange of information that transcends individual components. It’s not merely about connecting systems; it’s about empowering organizations with a cohesive ecosystem where every interaction adds value and enhances productivity.
In the realm of integration, Synergis stands as a beacon of excellence, embodying the principles of compatibility and interoperability to redefine the landscape of security and beyond.
Enhancing Security Operations: Optimal Strategies for Implementing Synergistic Solutions

In this section, we delve into the art of fortifying security operations through the adept deployment of advanced technological solutions. By seamlessly integrating cutting-edge security measures, organizations can fortify their defense mechanisms against evolving threats and ensure robust protection of assets and personnel.
Strategic Planning and Implementation

Successful implementation of synergistic security solutions hinges upon meticulous planning and strategic execution. Prior to deployment, it is imperative to conduct a comprehensive risk assessment to identify vulnerabilities and assess potential threats. This initial phase lays the groundwork for the formulation of tailored security protocols that align with organizational objectives.
Integrated System Architecture
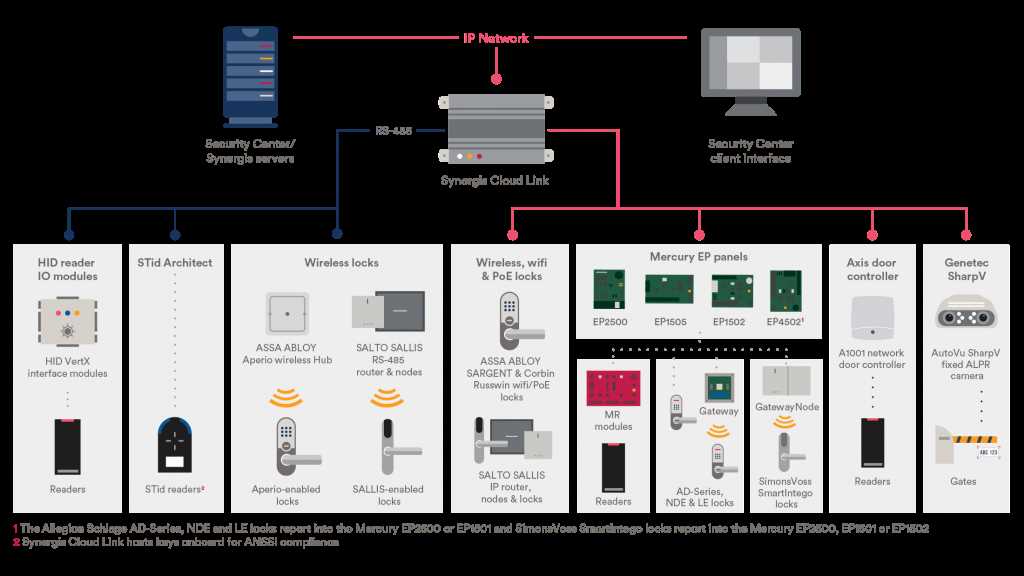
An integrated system architecture serves as the cornerstone of an effective security infrastructure. By amalgamating disparate security components into a cohesive framework, organizations can achieve heightened situational awareness and streamline incident response. Leveraging interoperable technologies fosters seamless communication and data exchange, facilitating real-time monitoring and proactive threat mitigation.
| Best Practices | Benefits |
|---|---|
| Regular System Audits | Identify Weaknesses and Ensure Compliance |
| Continuous Training and Education | Empower Personnel with Proficiency in Security Protocols |
| Collaborative Partnerships | Enhance Information Sharing and Expand Resources |
| Adaptive Response Strategies | Swiftly Adapt to Emerging Threats and Dynamic Environments |