Embark on a journey into the heart of cutting-edge cybersecurity technology, where threats are dissected and vulnerabilities exposed through the art of dynamic analysis. Dive deep into the realm of digital defense as we explore a revolutionary solution designed to fortify your systems against the ever-evolving landscape of cyber threats.
Discover the essence of proactive protection as we delve into the intricacies of real-time threat detection and behavior analysis. Explore how this innovative approach empowers organizations to stay one step ahead of malicious actors, safeguarding sensitive data and preserving operational integrity.
Uncover the dynamic synergy between machine intelligence and human expertise, where every anomaly is scrutinized and every suspicious behavior decoded. Join us as we illuminate the path towards a safer digital future, where resilience and adaptability reign supreme in the face of adversity.
Exploring the Capabilities of Advanced Threat Analysis

Delving into the intricate mechanisms of cutting-edge threat analysis solutions unveils a plethora of functionalities designed to fortify digital ecosystems against malicious intrusions and cyber-attacks. In this section, we embark on a journey to uncover the diverse array of features and capabilities embedded within the innovative framework of advanced threat analysis technologies.
The Power of Dynamic Malware Analysis
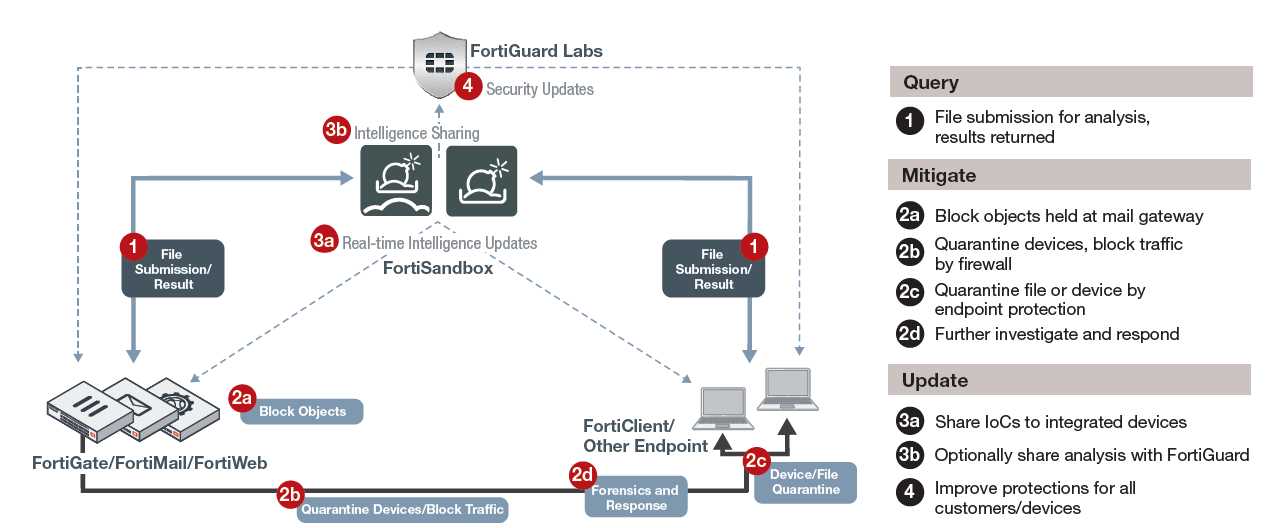
One of the cornerstone functionalities lies in the realm of dynamic malware analysis, where intricate algorithms meticulously dissect the behavior of potentially harmful code in a controlled environment. Through emulation and sandboxing techniques, these solutions simulate real-world scenarios to scrutinize the actions and intentions of malicious entities, thereby enabling proactive threat mitigation.
Comprehensive Threat Intelligence Integration
Furthermore, the integration of comprehensive threat intelligence elevates the efficacy of the analysis process by harnessing a vast repository of data encompassing known malware signatures, behavioral patterns, and emerging threats. By amalgamating historical insights with real-time observations, these solutions empower organizations to anticipate and counteract evolving cyber threats with precision and agility.
| Capability | Description |
|---|---|
| Behavioral Analysis | Examines the actions and interactions of suspicious files within a controlled environment to identify potentially malicious behavior. |
| File Reputation Scanning | Utilizes extensive databases of known malware signatures and file reputations to swiftly identify and quarantine threats. |
| Network Traffic Monitoring | Monitors network communications to detect anomalous activities indicative of cyber-attacks or data breaches. |
Through the synergy of these capabilities and more, advanced threat analysis solutions empower organizations to fortify their cyber defenses and safeguard their digital assets against the ever-evolving landscape of cyber threats.
Unraveling the Security Features
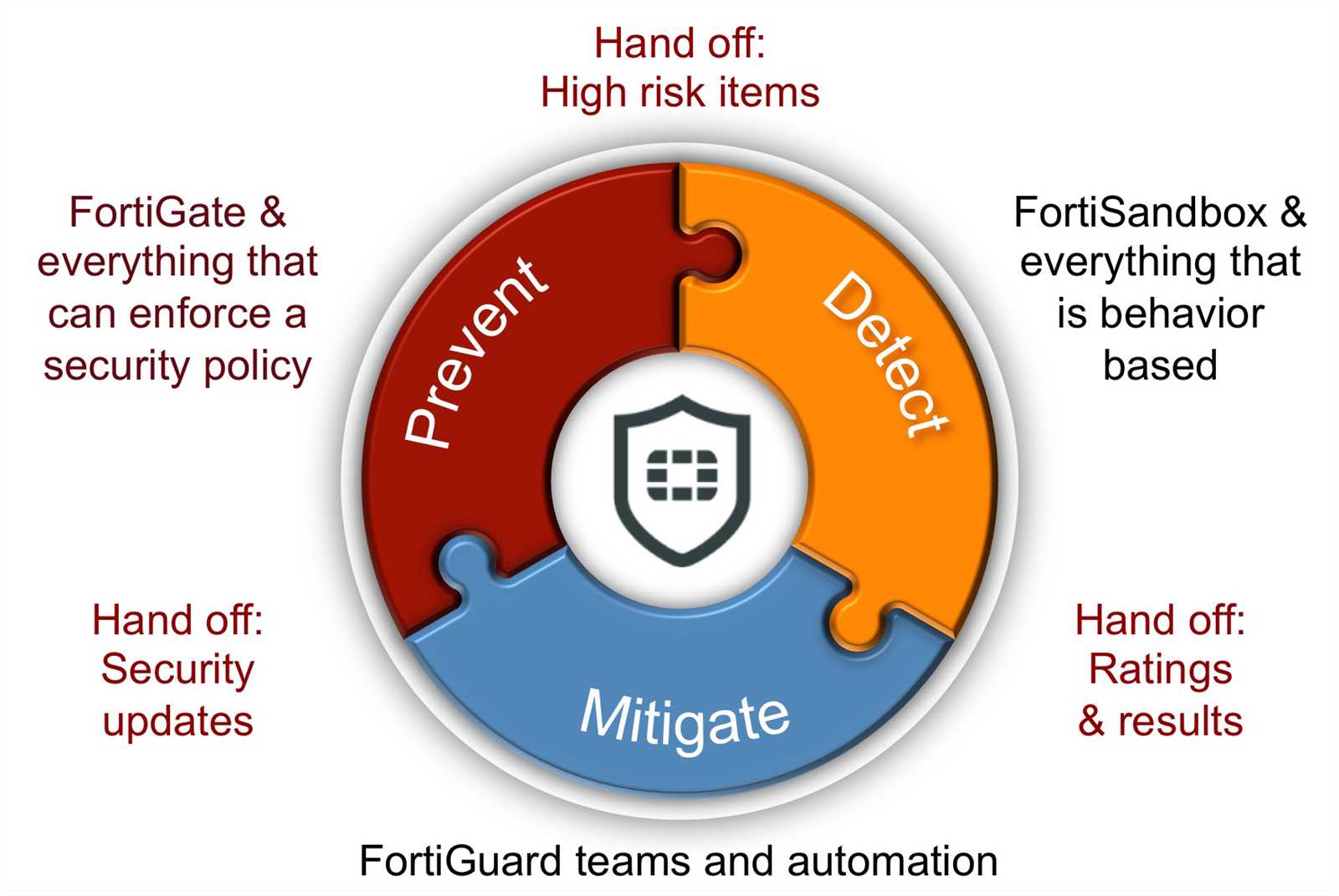
In this section, we delve into the intricate layers of protective mechanisms woven into the fabric of our solution. Our focus is to illuminate the robust shield meticulously crafted to safeguard against a myriad of threats lurking in the digital realm.
Advanced Threat Detection: At the forefront of our defense strategy lies a sophisticated system primed to identify and neutralize even the most elusive and insidious forms of malware and malicious activities. Powered by cutting-edge algorithms and heuristic analysis, this component stands sentinel, perpetually vigilant against emerging threats.
Dynamic Sandbox Environment: Within our ecosystem, an adaptive sandbox environment serves as a virtual crucible, meticulously examining suspicious entities in a controlled setting. This dynamic arena mimics real-world conditions, allowing for comprehensive analysis of behavioral patterns and interactions, thus fortifying our defenses against zero-day exploits and polymorphic threats.
Contextual Awareness: Beyond conventional signature-based detection, our solution possesses a keen understanding of contextual nuances, enabling it to discern between benign anomalies and genuine threats. By contextualizing behaviors within the broader framework of network activity and user interactions, our security apparatus achieves heightened accuracy in threat identification and mitigation.
Threat Intelligence Integration: Augmenting our defensive capabilities is a seamless integration with robust threat intelligence feeds sourced from a diverse array of channels. This symbiotic relationship empowers our solution with up-to-the-minute insights into emerging threats and global cybersecurity trends, enabling preemptive action and proactive defense posture.
Granular Policy Management: Central to our security architecture is the notion of granular policy management, affording administrators fine-grained control over access privileges and security protocols. This modular approach facilitates tailored configurations to suit diverse organizational needs, ensuring optimal balance between security and operational efficiency.
Continuous Monitoring and Remediation: Complementing our proactive defense mechanisms is a regimen of continuous monitoring and remediation, wherein anomalous activities are swiftly identified and addressed. Through real-time telemetry and automated response workflows, our solution minimizes dwell time and mitigates the impact of security incidents, thereby safeguarding organizational assets and preserving business continuity.
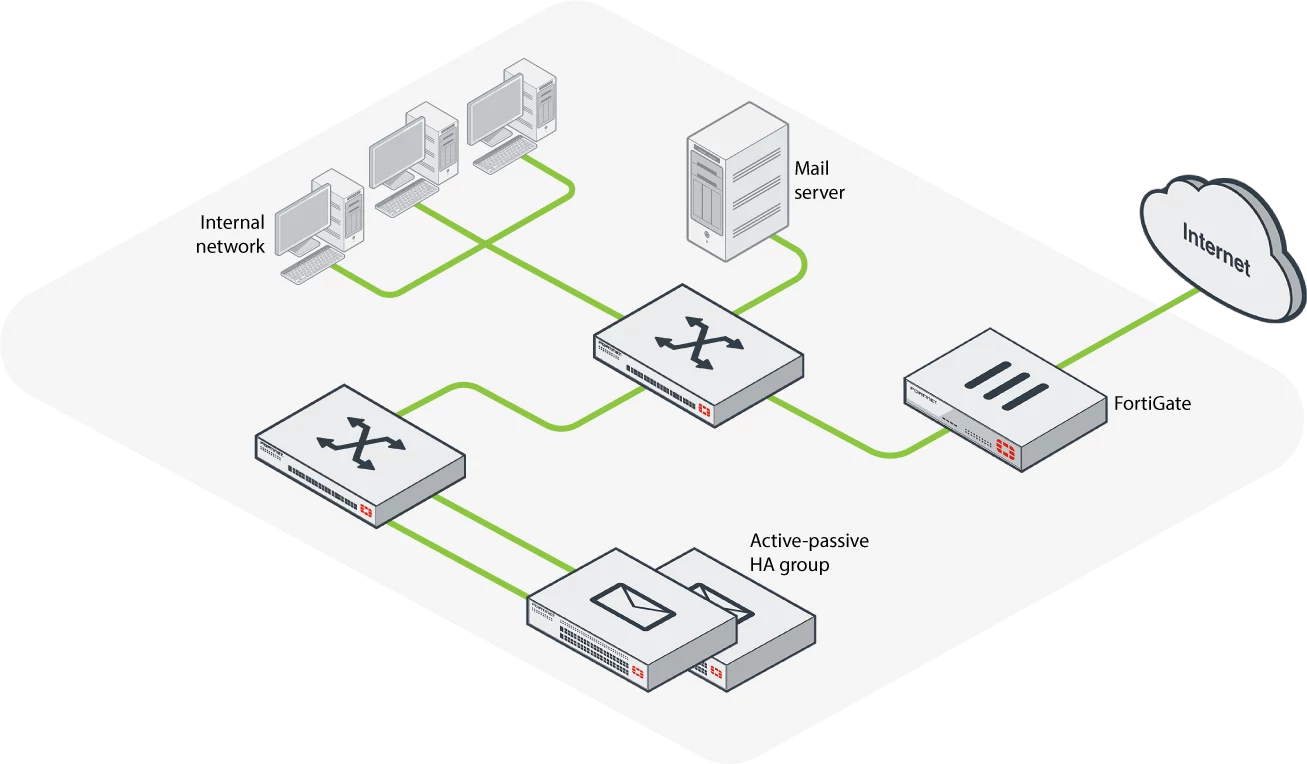
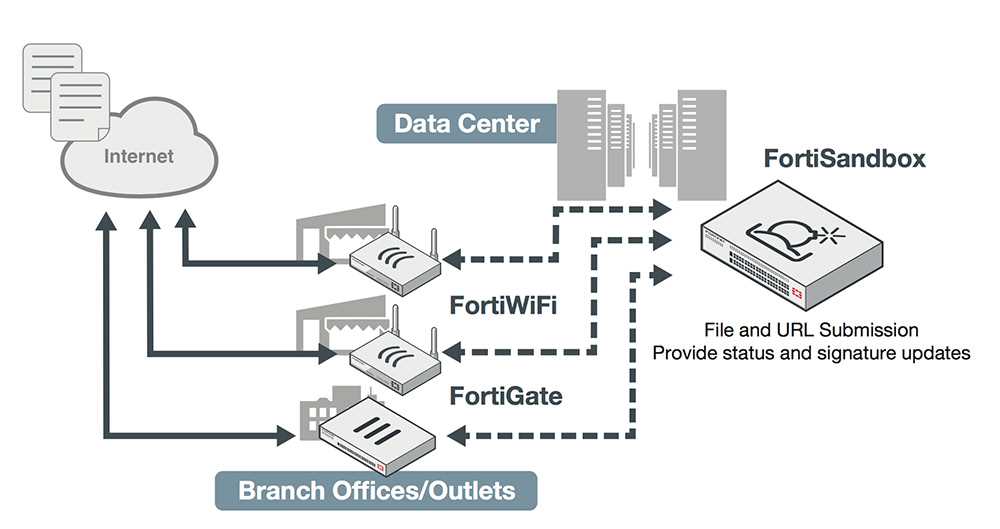
Understanding Deployment Options
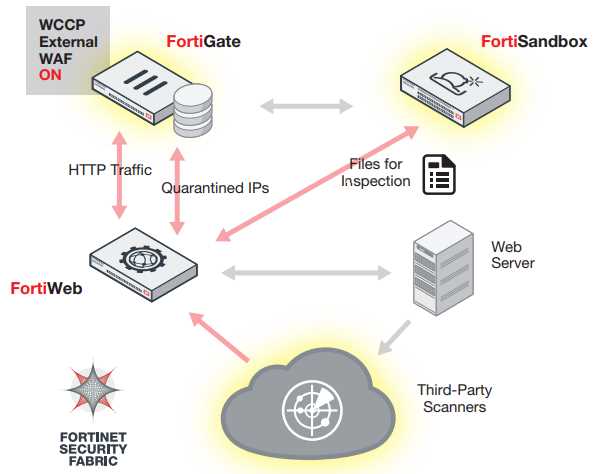
Exploring the diverse array of implementation pathways is crucial in comprehending the operational scope of this technological framework. Delving into the nuances of deployment strategies offers a panoramic view of the adaptability and scalability inherent in the system’s architecture.
Within this domain, the spectrum of deployment options unveils a mosaic of possibilities, each tailored to specific organizational exigencies and infrastructural landscapes. Embracing this multidimensional approach empowers stakeholders to orchestrate bespoke configurations aligned with their unique operational paradigms.
By dissecting the manifold deployment modalities, organizations can navigate the labyrinthine complexities of integration, elucidating the optimal pathway towards seamless assimilation within existing frameworks. This elucidation paves the way for streamlined processes and heightened efficacy in leveraging the technological arsenal at hand.
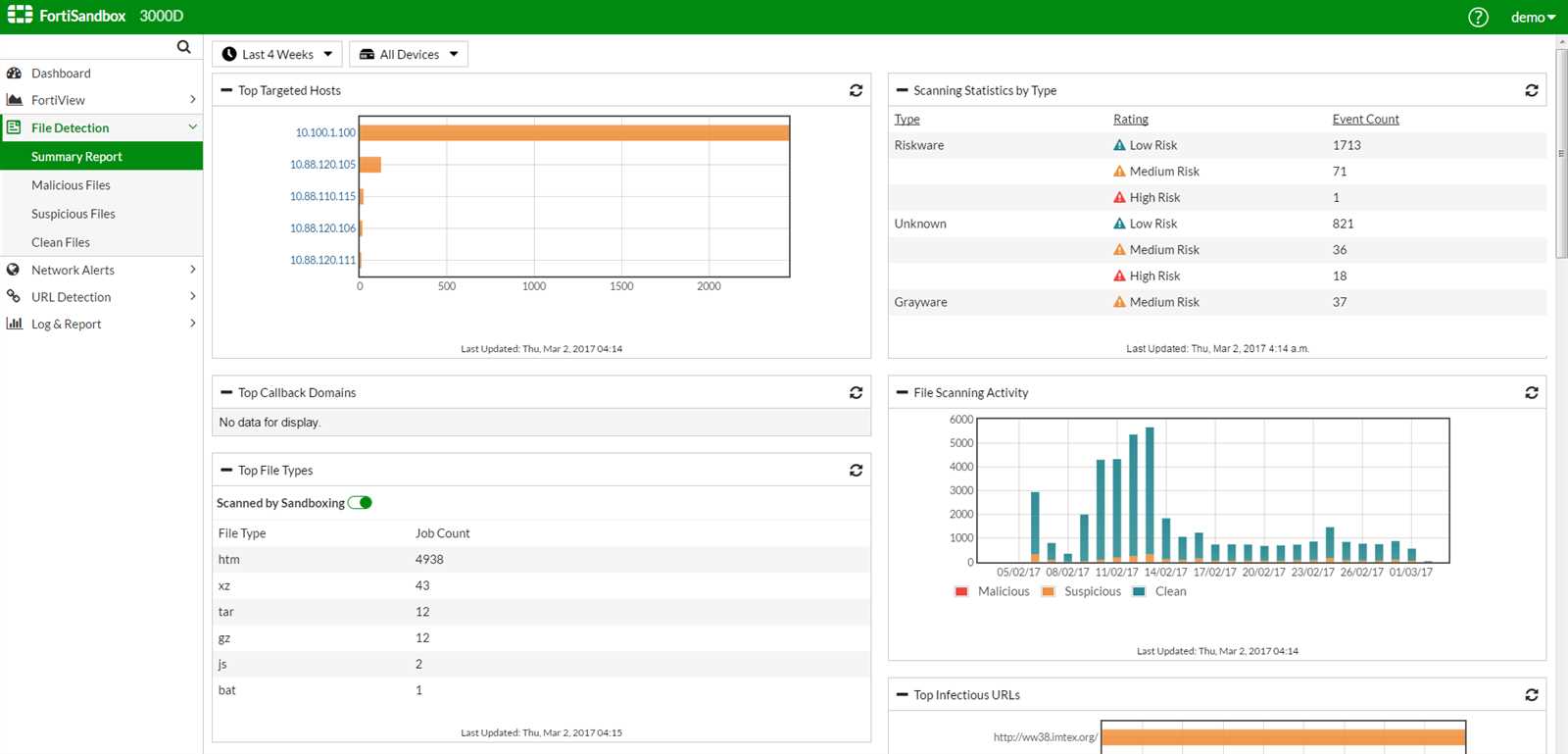
Examining Performance Metrics
In this section, we delve into the evaluation of operational efficiency, gauging the effectiveness and proficiency of the system under scrutiny. Our focus lies in dissecting various performance indicators to comprehensively understand the functionality and competence of the technology at hand.
Performance metrics serve as the compass guiding our assessment journey, providing insights into the system’s responsiveness, resource utilization, and overall efficacy. Through meticulous analysis and comparison, we unearth nuances that unveil the intricacies of its operational dynamics.
| Performance Metric | Description |
|---|---|
| Throughput | Measure of the rate at which tasks are completed or processed within the system, indicating its capacity for handling workload efficiently. |
| Latency | Elapsed time between the initiation of a process and its completion, reflecting the system’s responsiveness and speed of execution. |
| Resource Utilization | Assessment of the allocation and consumption of system resources such as CPU, memory, and storage, highlighting efficiency and potential bottlenecks. |
| Scalability | Evaluation of the system’s ability to adapt and expand its capacity in response to increasing workload or demand, ensuring sustained performance under varying conditions. |
| Reliability | Measurement of the system’s stability and consistency in delivering expected results over time, indicative of its dependability and trustworthiness. |
By scrutinizing these performance metrics, we gain a holistic perspective on the system’s operational prowess, enabling informed decision-making and optimization strategies. Each metric contributes valuable insights towards enhancing the efficiency and effectiveness of the technology ecosystem.