Discover the essence of safeguarding your information with an in-depth exploration into the realm of fortified digital security. Delve into the intricacies of shielding your valuable data against the ever-evolving landscape of cyber threats.
Explore the myriad strategies and techniques employed to fortify your digital assets, ensuring resilience against potential breaches. Gain insights into the holistic approach to protecting sensitive information in an interconnected world.
Unveil the layers of defense mechanisms designed to thwart malicious intrusions and preserve the integrity of your data infrastructure. Navigate through the labyrinth of cybersecurity protocols, empowering your organization with robust security measures.
Embark on a journey towards enhanced cybersecurity posture, equipped with the knowledge and tools essential for safeguarding your digital footprint. Elevate your defenses and fortify your resilience against emerging cyber threats.
The Comprehensive Guide to Fortiphish Datasheet
In this section, we delve into the intricacies and nuances of the comprehensive document that provides a detailed overview of the product offerings and features of Fortiphish. It serves as a crucial resource for understanding the capabilities and functionalities of the solution in depth.
Understanding the Documentation

Before delving into the specifics, it’s essential to grasp the essence of this comprehensive document. It serves as a roadmap, offering insights into the various aspects of the solution, ranging from its technological underpinnings to its practical applications.
Navigating Through Information
Within this guide, readers will uncover a plethora of information, ranging from technical specifications to real-world use cases. Learning how to navigate through this wealth of knowledge efficiently is key to harnessing the full potential of Fortiphish.
Understanding Fortiphish: Features and Capabilities
In this section, we delve into the comprehensive array of functionalities and strengths offered by the innovative Fortiphish solution. Exploring its diverse features and robust capabilities, we uncover the essence of its prowess in safeguarding against modern cyber threats.
- Advanced Threat Detection: Unveiling potential risks through cutting-edge algorithms and heuristic analysis, Fortiphish remains vigilant against emerging threats, ensuring proactive defense measures.
- Dynamic Phishing Simulation: Emulating real-world phishing scenarios, Fortiphish provides invaluable insights into organizational vulnerabilities, empowering informed decision-making and proactive mitigation strategies.
- Intelligent Reporting Mechanism: Transforming complex data into actionable intelligence, Fortiphish equips stakeholders with concise reports and analytics, facilitating informed risk management and resource allocation.
- Adaptive Training Modules: Tailoring educational content to individual learning styles, Fortiphish fosters a culture of cyber awareness and resilience, empowering users to recognize and mitigate potential threats effectively.
- Integrated Remediation Tools: Streamlining incident response processes, Fortiphish offers a suite of remediation tools and protocols, enabling swift and effective resolution of security breaches to minimize impact and downtime.
Through a synergistic combination of proactive defense mechanisms, insightful analytics, and user-centric training initiatives, Fortiphish stands as a stalwart guardian against the evolving landscape of cyber threats, ensuring the resilience and security of organizations worldwide.
Implementing Fortiphish: Expert Strategies and Integration Insights
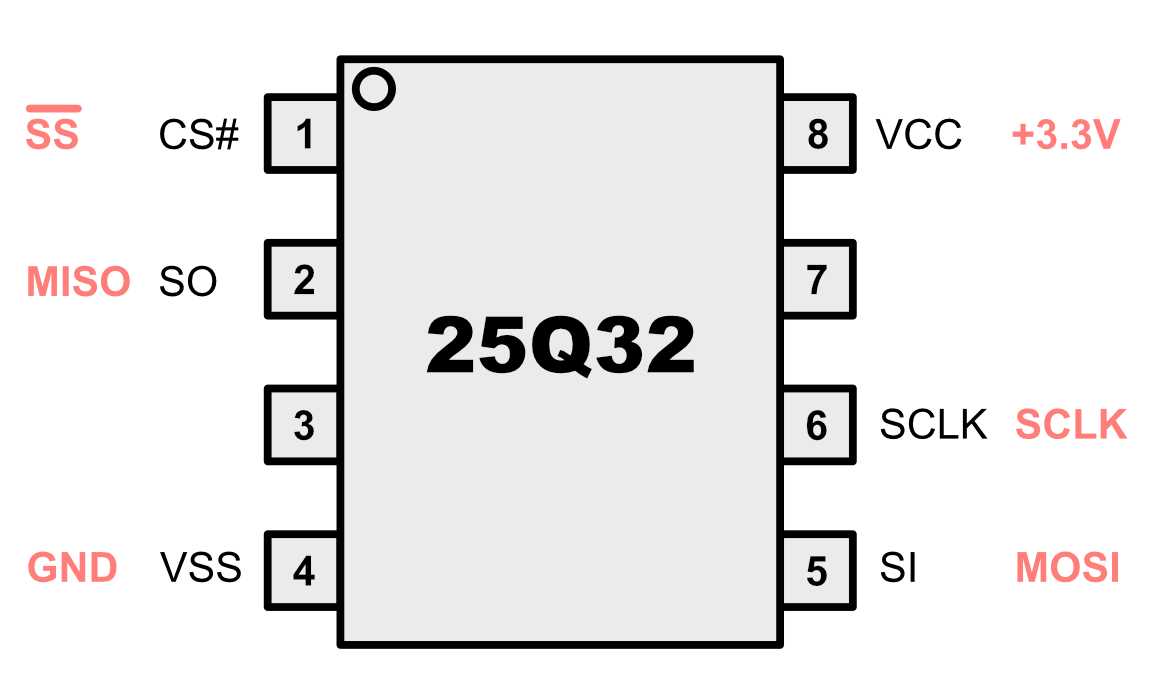
In this section, we delve into the intricacies of integrating a robust security solution into your infrastructure. Discover key strategies and expert insights to seamlessly incorporate the protective shield into your existing framework.
Understanding the Integration Landscape:
Before embarking on the integration journey, it’s imperative to grasp the nuances of your system’s architecture and identify potential integration points. By comprehensively mapping out your infrastructure, you can strategically place the safeguards without disrupting the flow of operations.
Optimizing Deployment:
Efficient deployment is the cornerstone of a successful integration. Explore techniques to streamline the deployment process, ensuring minimal downtime and maximal efficiency. From automated deployment scripts to staged rollout strategies, discover the best practices tailored to your organization’s needs.
Customization and Configuration:
One size rarely fits all in the realm of security solutions. Uncover the power of customization and configuration, allowing you to tailor the protective measures to align perfectly with your unique requirements. Learn how to fine-tune settings and parameters to strike the optimal balance between security and functionality.
Ensuring Seamless Interoperability:
Integration doesn’t exist in isolation. Explore methods to foster seamless interoperability between Fortiphish and your existing ecosystem of tools and applications. From API integrations to standardized protocols, discover how to establish smooth communication channels that enhance the overall security posture.
Continuous Monitoring and Optimization:
Security is an ongoing journey, not a destination. Dive into the realm of continuous monitoring and optimization, where proactive measures and vigilant oversight ensure that your defenses remain resilient in the face of evolving threats. Explore tools and techniques to monitor performance metrics, detect anomalies, and adapt swiftly to emerging challenges.
Conclusion:
In conclusion, implementing Fortiphish requires a strategic approach that encompasses understanding, optimization, customization, interoperability, and ongoing vigilance. By following these expert strategies and integration insights, you can fortify your defenses effectively and safeguard your digital assets against a myriad of threats.
Securing Your Data: Effective Strategies and Advantages
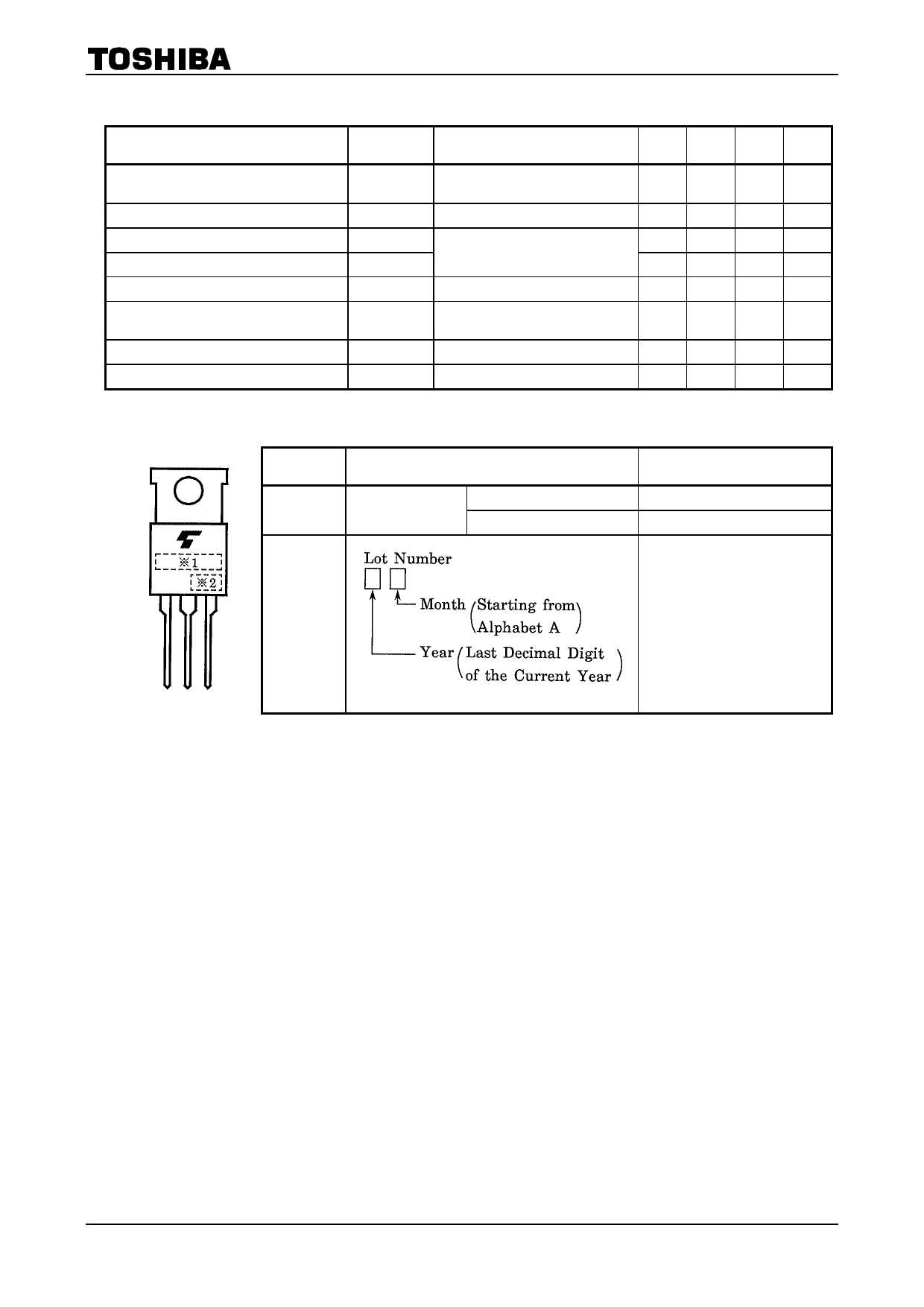
In today’s digital landscape, safeguarding your sensitive information is paramount. This section delves into powerful methodologies and the inherent benefits of employing cutting-edge data security solutions.
The Importance of Robust Data Protection
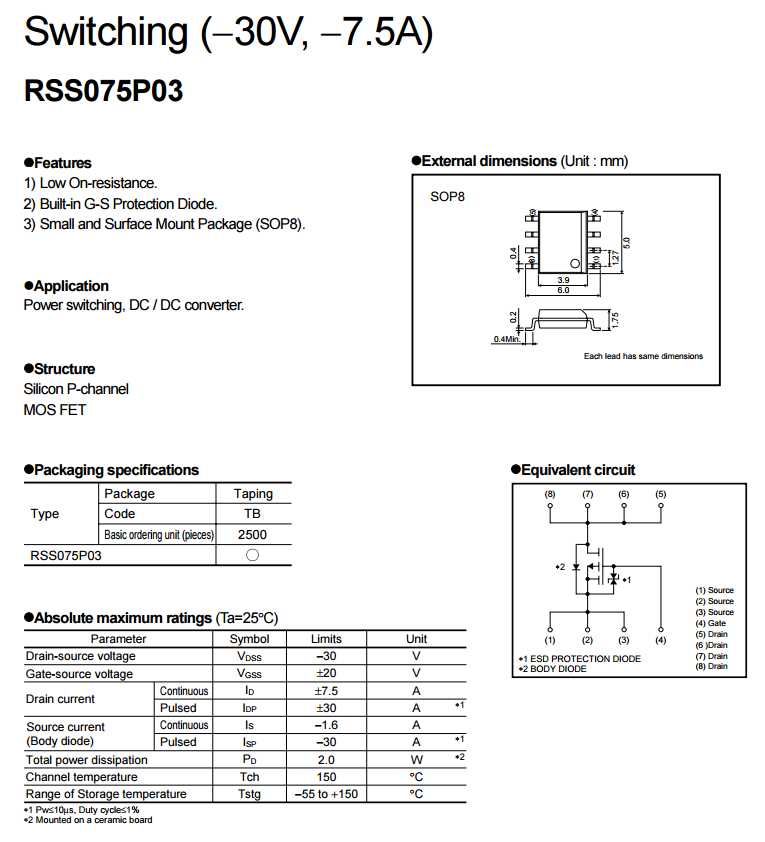
Ensuring the confidentiality, integrity, and availability of your data is crucial for maintaining trust with stakeholders and safeguarding against potential threats. Implementing comprehensive security measures mitigates risks associated with unauthorized access, data breaches, and malicious attacks.
Maximizing Security Solutions for Optimal Results
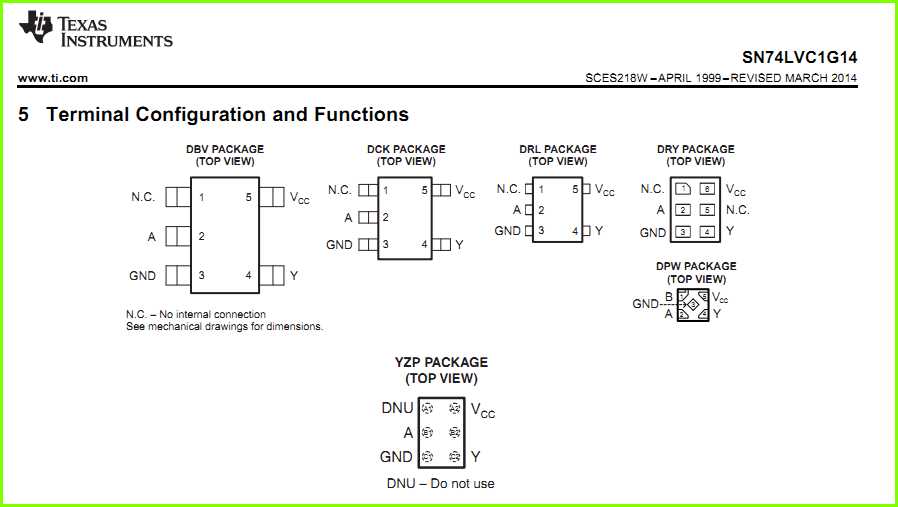
Embracing advanced technologies and proactive strategies fortifies your data infrastructure against evolving cyber threats. By leveraging robust encryption, multifactor authentication, and continuous monitoring, organizations can bolster their defense mechanisms and uphold regulatory compliance.
Key Advantages:
- Enhanced Protection: Shield your sensitive data from unauthorized access and potential breaches.
- Increased Resilience: Strengthen your resilience against emerging cyber threats and vulnerabilities.
- Regulatory Compliance: Ensure adherence to industry regulations and standards, fostering trust and credibility.
- Peace of Mind: Experience peace of mind knowing your data is safeguarded by state-of-the-art security solutions.