
Unlocking the potential of modern cybersecurity demands a paradigm shift in how organizations approach network access. In a digital landscape fraught with evolving threats and complex infrastructures, traditional methods fall short of delivering the robust protection required.
Embracing a dynamic strategy that prioritizes precision and flexibility is paramount. This entails transcending the confines of conventional approaches to access management, empowering enterprises to fortify their defenses without compromising agility.
Delve into this exploration to discover an innovative solution poised to redefine the realm of secure network access. Experience the fusion of cutting-edge technology and proactive defense mechanisms designed to propel organizations towards unparalleled resilience in an ever-evolving cybersecurity landscape.
Understanding Secure Network Access Beyond Traditional Boundaries
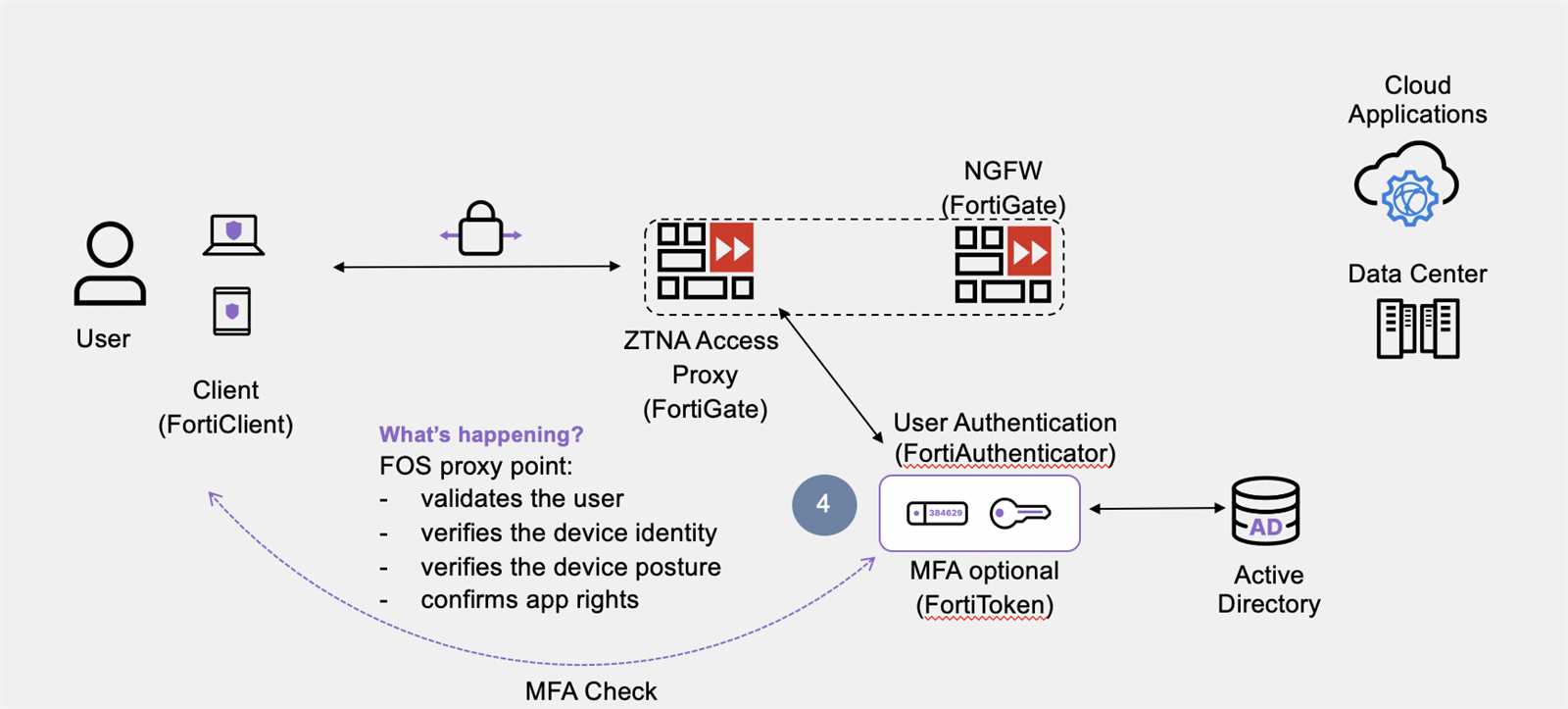
In the contemporary landscape of network security, the paradigm of secure access has evolved beyond conventional boundaries, necessitating a deeper comprehension of cutting-edge approaches. This segment delves into the intricacies of modern secure network access solutions, transcending traditional models to fortify organizational defenses against emerging threats.
Exploring the Key Features of Fortinet’s Zero Trust Network Access (ZTNA)
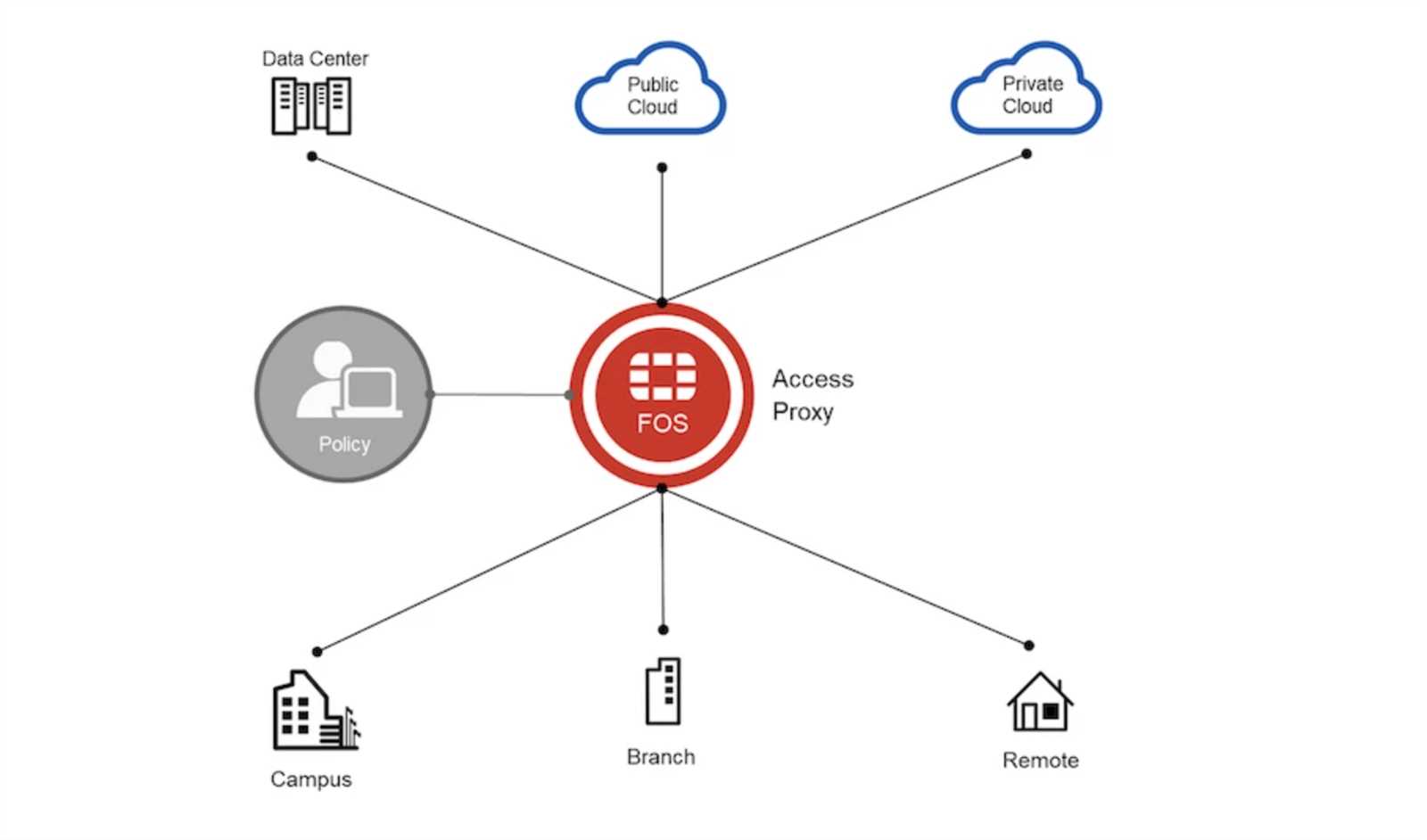
In this section, we delve into the essential components that define the innovative capabilities of Fortinet’s Zero Trust Network Access (ZTNA) solution. Discover the foundational elements and functionalities that empower organizations to establish robust security postures without relying solely on perimeter defenses.
- Dynamic Access Control: Instead of static, perimeter-based security measures, Fortinet ZTNA employs dynamic access controls, allowing granular permissions tailored to user identities and contextual factors.
- Identity-Centric Security: By prioritizing user identities, Fortinet ZTNA mitigates the risk of unauthorized access by implementing stringent authentication and authorization protocols.
- Micro-Segmentation: Through micro-segmentation, Fortinet ZTNA partitions network resources into isolated zones, limiting lateral movement and containing potential breaches.
- Application-Aware Policies: Fortinet ZTNA enables organizations to create policies based on specific applications, ensuring that access privileges are aligned with business needs and security requirements.
- Secure Remote Access: With robust encryption protocols and multi-factor authentication, Fortinet ZTNA facilitates secure remote access, enabling seamless connectivity for distributed teams without compromising security.
- Continuous Monitoring and Risk Assessment: Fortinet ZTNA incorporates continuous monitoring mechanisms to detect anomalies and assess risk levels in real-time, allowing proactive mitigation of potential threats.
By harnessing these cutting-edge features, organizations can establish a comprehensive Zero Trust framework that safeguards critical assets, adapts to evolving threats, and fosters a secure environment conducive to productivity and innovation.
Benefits of Embracing Cutting-edge ZTNA Solutions

In today’s dynamic digital landscape, organizations strive to fortify their security posture while ensuring seamless connectivity for their distributed workforce. Implementing advanced Zero Trust Network Access (ZTNA) solutions brings forth a multitude of advantages, revolutionizing the way businesses safeguard their assets and enable secure access.
Enhanced Security
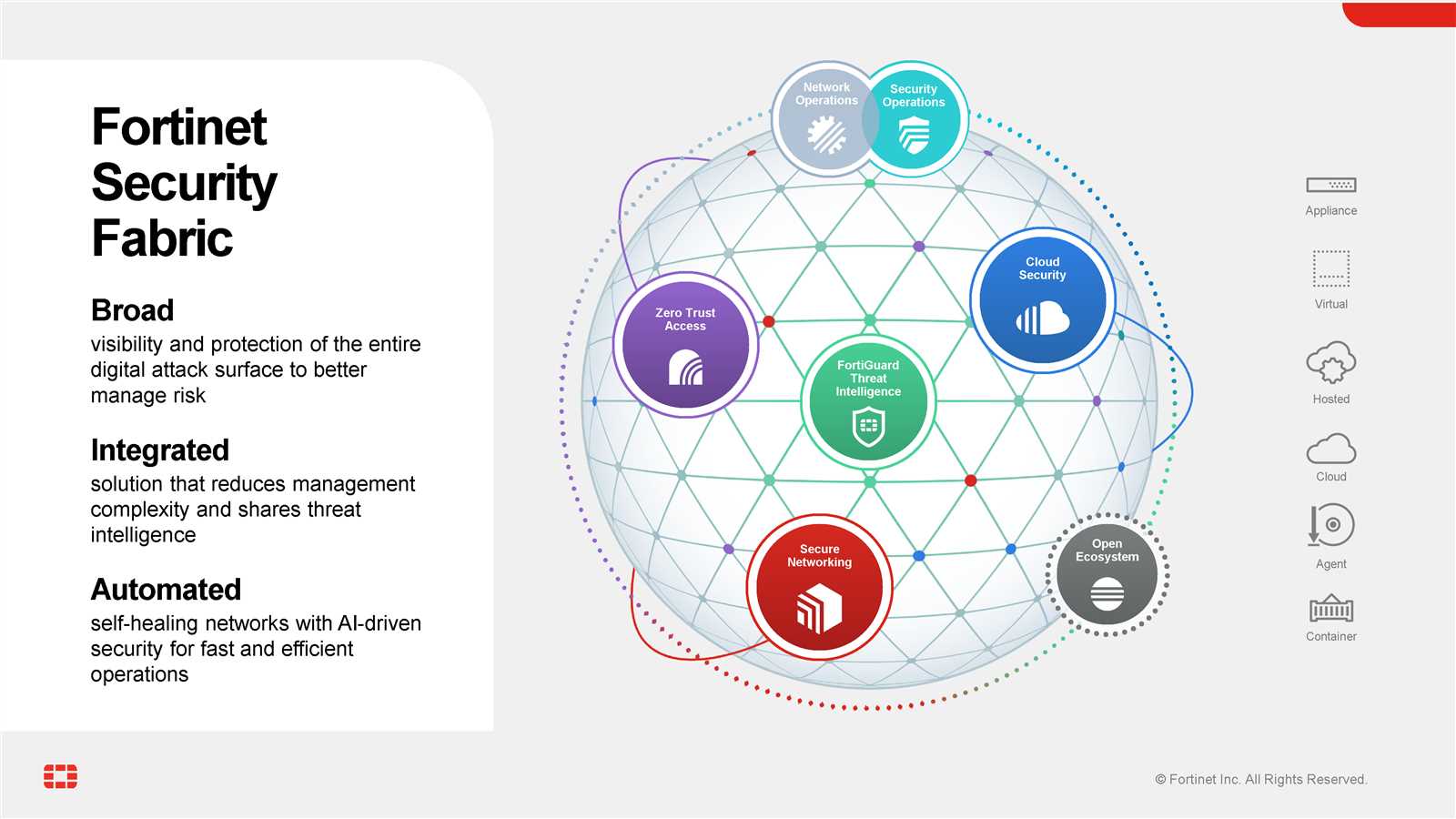
By adopting robust ZTNA frameworks, companies bolster their defense mechanisms against evolving cyber threats, safeguarding sensitive data and critical infrastructure. Through a meticulous authentication and authorization process, unauthorized access attempts are thwarted, mitigating the risk of breaches and data exfiltration.
Elevated User Experience

With ZTNA, users experience a seamless and frictionless access experience, irrespective of their location or device. By eliminating the need for traditional VPNs and adopting a user-centric approach, productivity soars as employees effortlessly access resources while adhering to stringent security protocols.
- Strengthened Security Posture
- Streamlined Access Management
- Seamless User Experience
- Reduced Operational Overhead
- Enhanced Compliance Adherence
Case Studies: Real-world Applications of Cutting-edge Zero Trust Network Access Technology
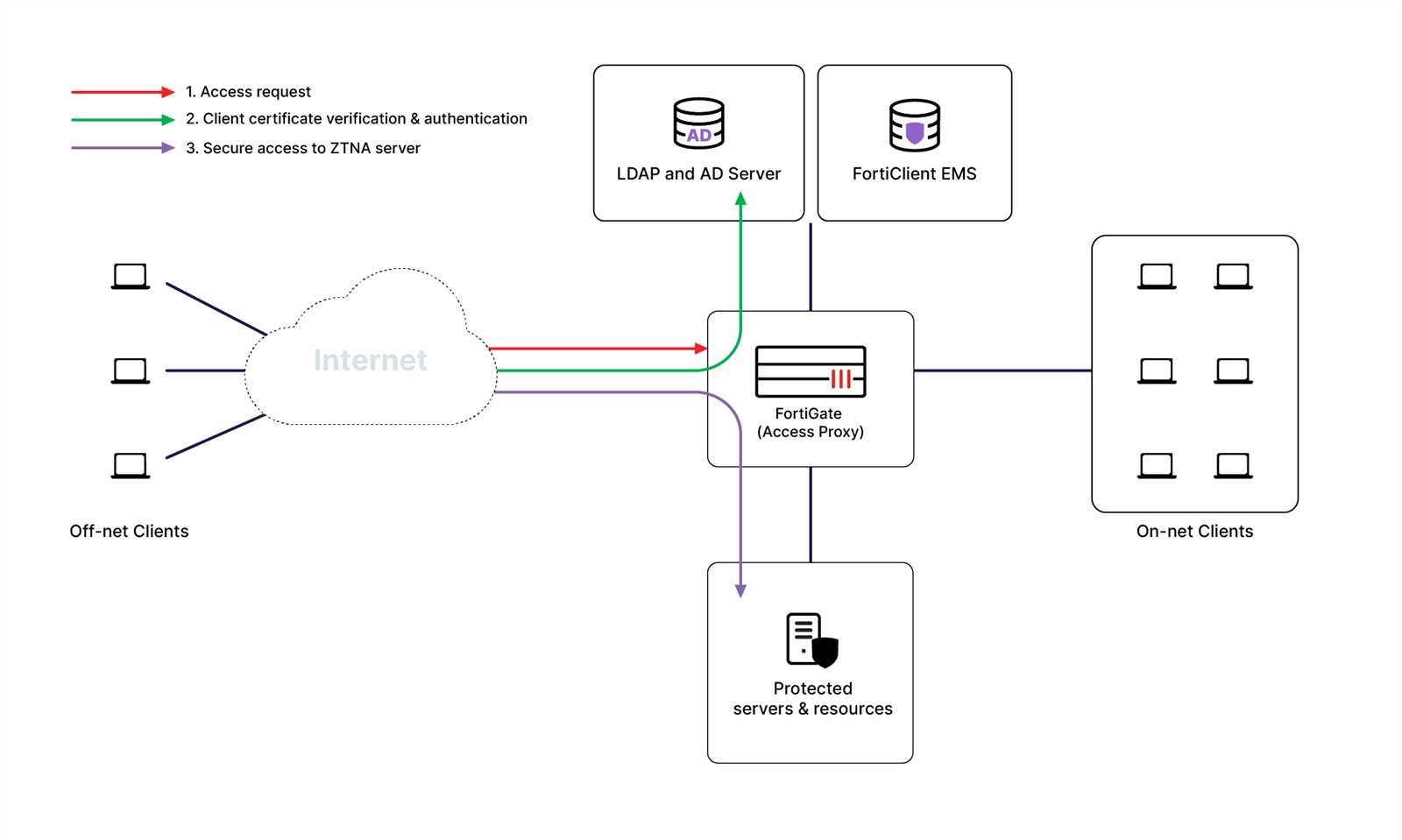
In this section, we delve into real-world scenarios where state-of-the-art Zero Trust Network Access (ZTNA) solutions have been pivotal. Through examining these cases, we aim to illuminate the practical applications and tangible benefits of advanced network security paradigms.
Enhanced Network Security for Global Enterprises: Explore how multinational corporations bolstered their cybersecurity posture by leveraging innovative ZTNA solutions. Witness firsthand how these organizations fortified their networks against evolving threats, safeguarding sensitive data and preserving operational continuity.
Streamlined Access Management in Healthcare: Discover how healthcare institutions optimized access control mechanisms, ensuring secure yet seamless access to critical patient information for authorized personnel. Witness the transformative impact of ZTNA in safeguarding patient privacy and upholding regulatory compliance.
Empowering Remote Workforces: Uncover the role of ZTNA in facilitating remote work environments, enabling organizations to embrace flexible work arrangements without compromising security. Delve into case studies showcasing how distributed teams accessed resources securely, irrespective of their location, fostering productivity and collaboration.
Securing Cloud Infrastructures: Witness how cloud-native businesses fortified their digital assets against sophisticated cyber threats through the adoption of ZTNA frameworks. Explore how dynamic access policies mitigated risks associated with cloud migration and empowered organizations to harness the scalability of cloud environments without compromising security.
Protecting Critical Infrastructure: Examine the intersection of ZTNA technology and safeguarding critical infrastructure, ranging from energy grids to transportation networks. Gain insights into how robust access controls shielded vital systems from cyber intrusions, ensuring the reliability and resilience of essential services.
Through these diverse case studies, it becomes evident that ZTNA transcends conventional security approaches, offering a paradigm shift towards proactive, granular access controls tailored to the modern threat landscape.