
Embark on a journey through the realm of advanced network fortification, where ingenuity meets security prowess in an unparalleled fusion. Delve into the intricacies of a technological marvel designed to safeguard digital landscapes against modern threats.
Discover the blueprint of a formidable guardian, meticulously crafted to navigate the complexities of cyberspace with precision and resilience. Unravel the architecture of a shield forged to withstand the relentless onslaught of cyber adversaries.
Unveil the unparalleled capabilities woven into the fabric of this sentinel, where innovation converges with efficiency to redefine the benchmarks of network protection. Step into the future of cybersecurity, where potential meets performance in a symphony of digital defense.
Understanding the Fortinet’s Premier Firewall Documentation

In delving into the intricacies of the premier firewall documentation provided by Fortinet for their flagship 6300f model, it becomes imperative to unravel the myriad layers of technical specifications, operational nuances, and strategic insights embedded within.
This section aims to dissect the essence of the comprehensive documentation, elucidating its significance in comprehending the functionalities, capabilities, and deployment scenarios of this cutting-edge security apparatus.
Key Features and Capabilities Unveiled

Revealing the essence
Unlocking the potential of cutting-edge technology, this comprehensive analysis sheds light on the intricate features and dynamic capabilities embedded within this robust solution.
Empowering Connectivity:
Forge seamless connections with enhanced networking prowess, ensuring fluid communication across diverse environments.
Security Reinforcement:
Fortify defenses with advanced threat detection mechanisms, bolstering digital fortresses against modern cyber threats.
Scalability and Flexibility:
Scale effortlessly to meet evolving demands, flexing adaptively to accommodate fluctuating workloads.
Performance Optimization:
Optimize efficiency with streamlined operations, delivering unparalleled performance for mission-critical tasks.
Insightful Analytics:
Illuminate insights with comprehensive analytics capabilities, providing invaluable intelligence for informed decision-making.
Enhanced Management:
Elevate control with intuitive management interfaces, streamlining administrative tasks for enhanced productivity.
Reliability and Resilience:
Champion reliability with resilient architecture, ensuring continuity even amidst challenging circumstances.
Performance Metrics: Speed, Throughput, and Scalability
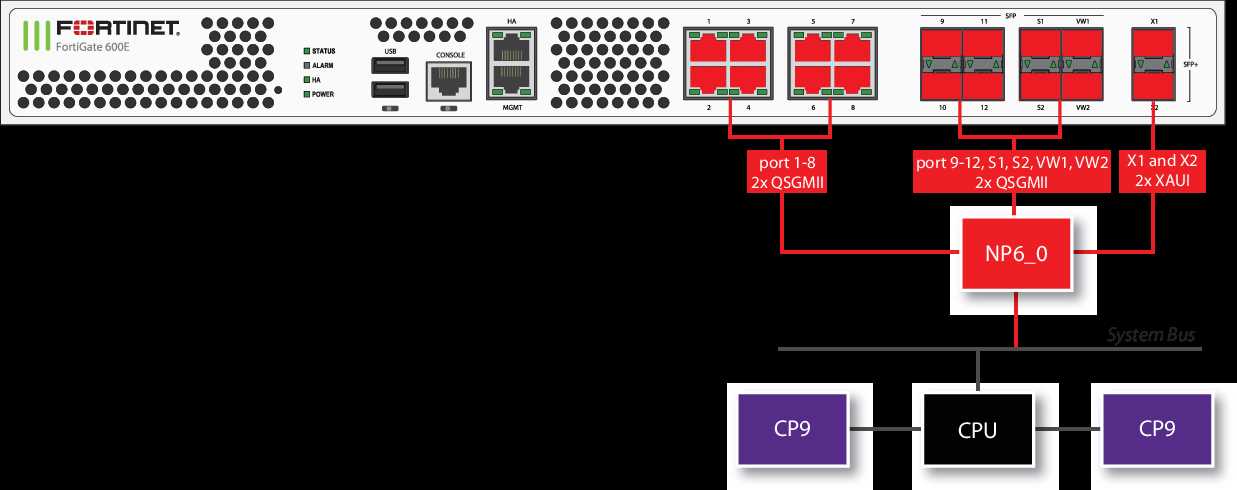
In this section, we delve into the fundamental aspects that define the operational prowess of the system under scrutiny. We explore the dynamic interplay between velocity, efficiency, and capacity without tethering ourselves to specific nomenclature. Our aim is to present a comprehensive overview of how this system navigates the intricate realm of data transmission and processing, showcasing its adeptness in facilitating swift data traversal, robust throughput, and seamless scalability.
Speed
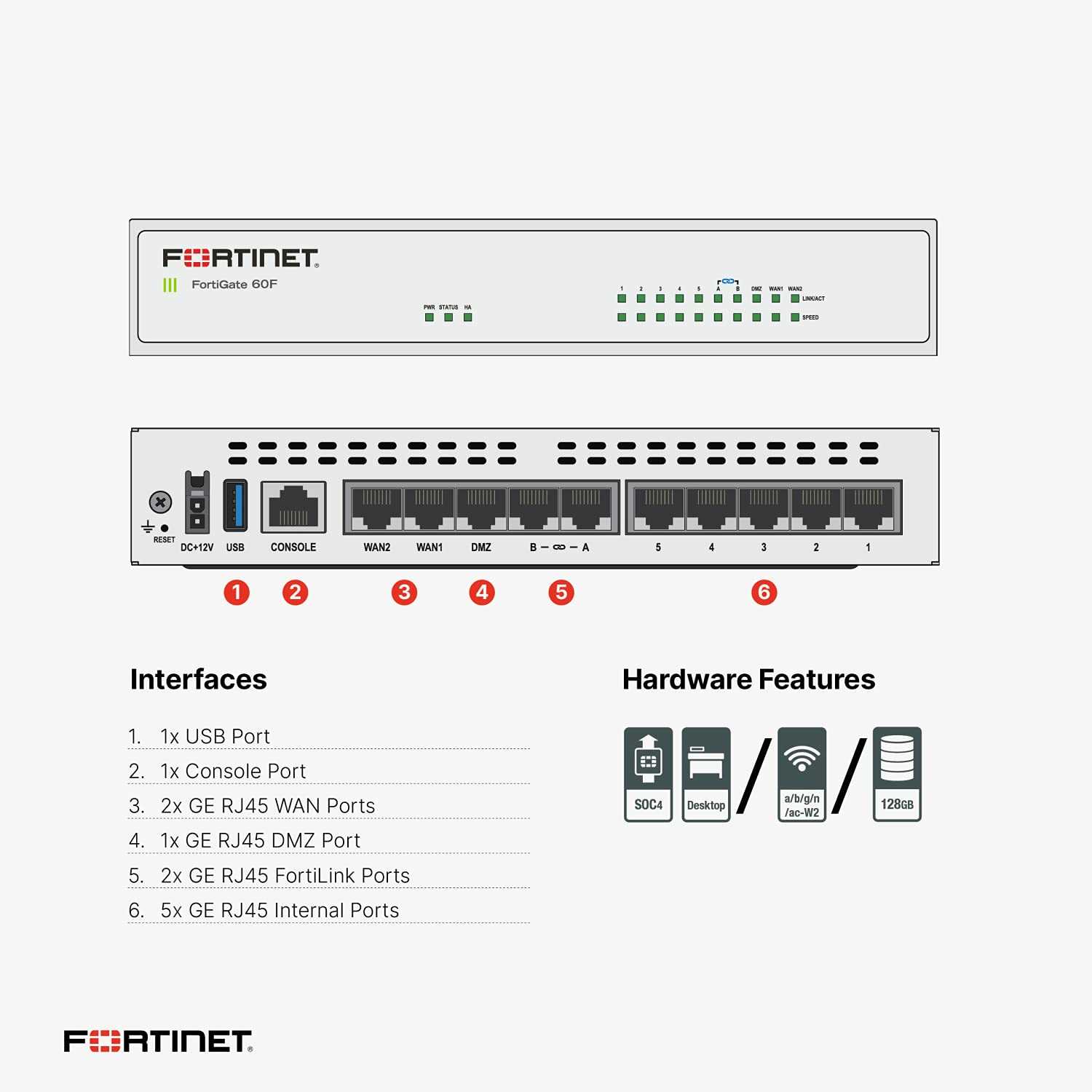
Speed encapsulates the rapidity with which data traverses through the system’s architecture, embodying the essence of instantaneous transmission. It is a testament to the system’s agility and responsiveness, reflecting its ability to swiftly execute commands, process requests, and relay information without undue latency.
Throughput

Throughput delineates the system’s capacity to handle and process a voluminous influx of data within a specified timeframe. It exemplifies the efficiency with which the system assimilates, analyzes, and disseminates information, ensuring uninterrupted data flow and seamless operation even under demanding circumstances.
| Aspect | Description |
|---|---|
| Vertical Scalability | Refers to the system’s ability to enhance performance by adding more resources within the existing framework, thereby accommodating increased workload without compromising efficiency. |
| Horizontal Scalability | Denotes the system’s capacity to expand horizontally by distributing workload across multiple nodes or instances, fostering seamless scalability and enhanced resilience against surges in demand. |
Security Protocols and Integration: Ensuring Network Resilience
In the realm of network fortification and robustness, the amalgamation of security protocols plays a pivotal role in bolstering network resilience. This section delves into the intricate interplay of various security measures and their integration strategies, aiming to fortify network infrastructure against potential threats and vulnerabilities.
At the core of network resilience lies a multifaceted approach to security, encompassing a spectrum of protocols and methodologies to mitigate risks and fortify defenses. Through seamless integration of diverse security measures, networks can attain a state of heightened resilience, capable of withstanding an array of adversarial maneuvers and emergent challenges.
One cornerstone of network resilience is the adoption of encryption protocols, which serve as an impregnable barrier against unauthorized access and data breaches. By harnessing the power of encryption, sensitive information traversing the network remains shielded from prying eyes, ensuring confidentiality and integrity in transit.
Furthermore, the integration of robust authentication mechanisms augments network resilience by fortifying access control and identity verification processes. Through the implementation of multifactor authentication and biometric recognition, networks can thwart unauthorized access attempts, bolstering overall security posture.
Moreover, the orchestration of dynamic security protocols, such as intrusion detection and prevention systems (IDPS), fortifies networks against evolving threats in real-time. By leveraging advanced anomaly detection algorithms and signature-based analysis, IDPS mechanisms proactively identify and neutralize malicious activities, safeguarding network integrity.
Additionally, the integration of security information and event management (SIEM) solutions serves as a linchpin in network resilience, facilitating comprehensive threat detection and incident response capabilities. Through centralized log management and correlation analysis, SIEM platforms empower organizations to swiftly identify and mitigate security breaches, minimizing potential impact.
In conclusion, the convergence of diverse security protocols and integration strategies is imperative in fortifying network resilience against an ever-evolving threat landscape. By adopting a proactive stance towards security orchestration and harmonizing disparate security measures, organizations can fortify their network infrastructure and uphold the integrity and confidentiality of critical assets.