
In the realm of advanced network security appliances lies a robust contender, offering a comprehensive array of features and capabilities. Delving into the intricate details of this technological marvel unveils a treasure trove of functionalities designed to fortify digital ecosystems and safeguard sensitive data.
Embark on a journey through the intricacies of a cutting-edge solution engineered to uphold the integrity of networks amidst evolving cyber threats. Unveil the arsenal of defenses meticulously crafted to repel intrusions and mitigate vulnerabilities, ensuring seamless operations in an ever-expanding digital landscape.
Discover a compendium of specifications, meticulously crafted and fine-tuned to deliver unparalleled performance and resilience. Navigate through the maze of technical intricacies, unraveling the essence of innovation embedded within each component and protocol.
Join the expedition into the realm of network security prowess, where every specification serves as a cornerstone in the fortress of digital defense, poised to confront the challenges of tomorrow’s cyber terrain.
Exploring the Specifications of the Advanced Fortinet 4201f Platform

In this section, we delve into the intricate details and comprehensive capabilities of the cutting-edge Fortinet 4201f solution. Unveiling its robust functionalities and innovative features, we navigate through its extensive array of specifications to provide a comprehensive understanding of its prowess in modern networking environments.
- Performance Metrics: Unveiling the operational efficiency and throughput capabilities of this formidable networking solution, we explore its performance metrics across various workloads and scenarios.
- Security Features: Delving into the security arsenal of this advanced platform, we analyze its diverse range of protective mechanisms, safeguarding networks against evolving cyber threats and vulnerabilities.
- Scalability and Flexibility: Investigating the scalability and adaptability of the Fortinet 4201f, we assess its capacity to seamlessly accommodate growing network demands and dynamic infrastructural requirements.
- Connectivity Options: Examining the connectivity options offered by this sophisticated device, we scrutinize its support for diverse network protocols and interfaces, facilitating seamless integration within complex networking environments.
- Management Capabilities: Unraveling the management capabilities inherent within the Fortinet 4201f platform, we explore its intuitive management interface and robust administrative features, empowering network administrators with streamlined control and oversight.
- Resilience and Reliability: Assessing the resilience and reliability of this formidable networking solution, we delve into its high availability features and failover mechanisms, ensuring uninterrupted network operation and continuity.
Through a meticulous exploration of these specifications, we illuminate the remarkable attributes of the Fortinet 4201f platform, underscoring its significance as a premier choice for modern networking infrastructures.
Key Features and Specifications
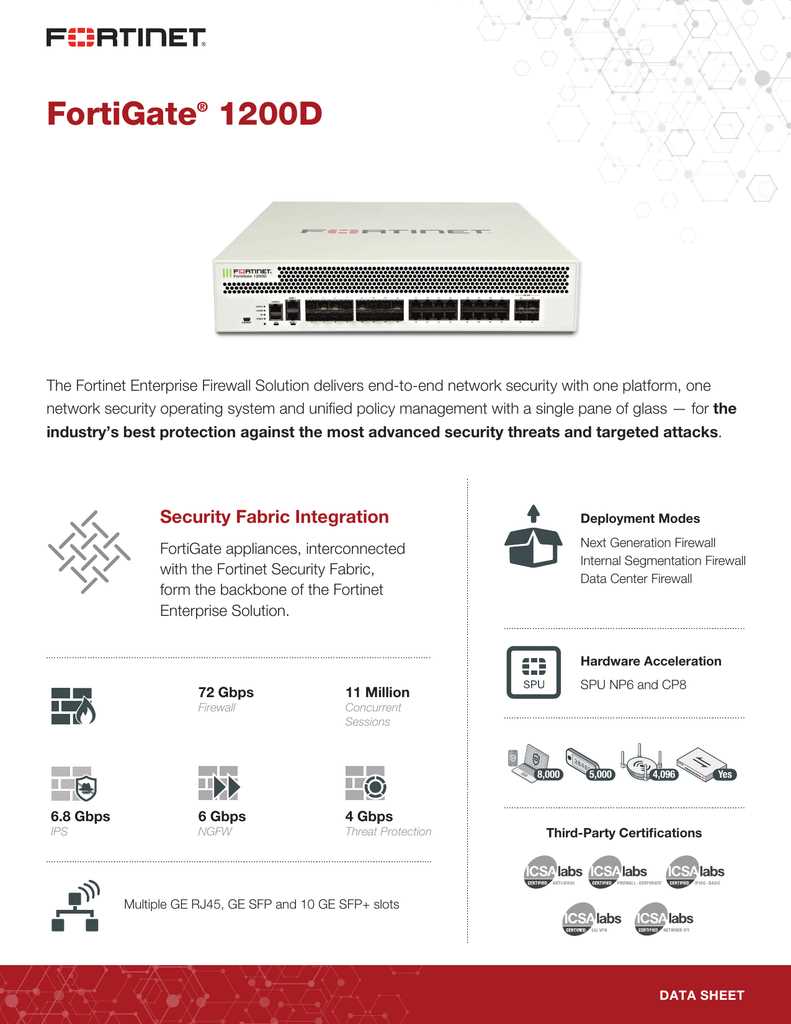
In this section, we delve into the distinctive attributes and technical specifications that characterize the cutting-edge solution under discussion. Highlighting its functionalities, performance benchmarks, and unique capabilities, this segment aims to provide a comprehensive overview of the product’s offerings.
Distinctive Attributes

- Innovative Functionality
- Advanced Performance Metrics
- Unique Capabilities
- Specialized Features
Technical Specifications
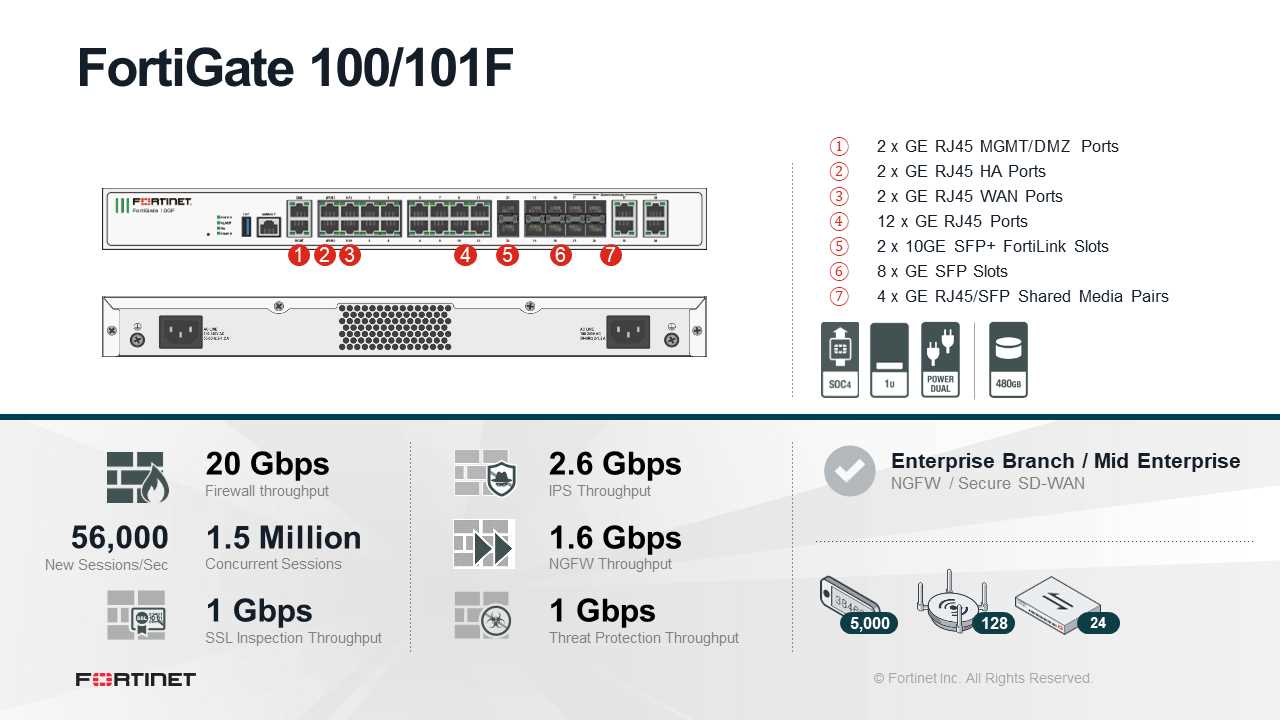
- Performance Metrics
- Hardware Specifications
- Network Connectivity Features
- Security Protocols Supported
Performance Metrics and Scalability

In this section, we delve into the intricate details of the operational capabilities and adaptability of the aforementioned security appliance. We explore the diverse array of measurements used to evaluate its efficiency and capacity to handle varying workloads, without directly referencing its model or specifications.
Efficiency Evaluation
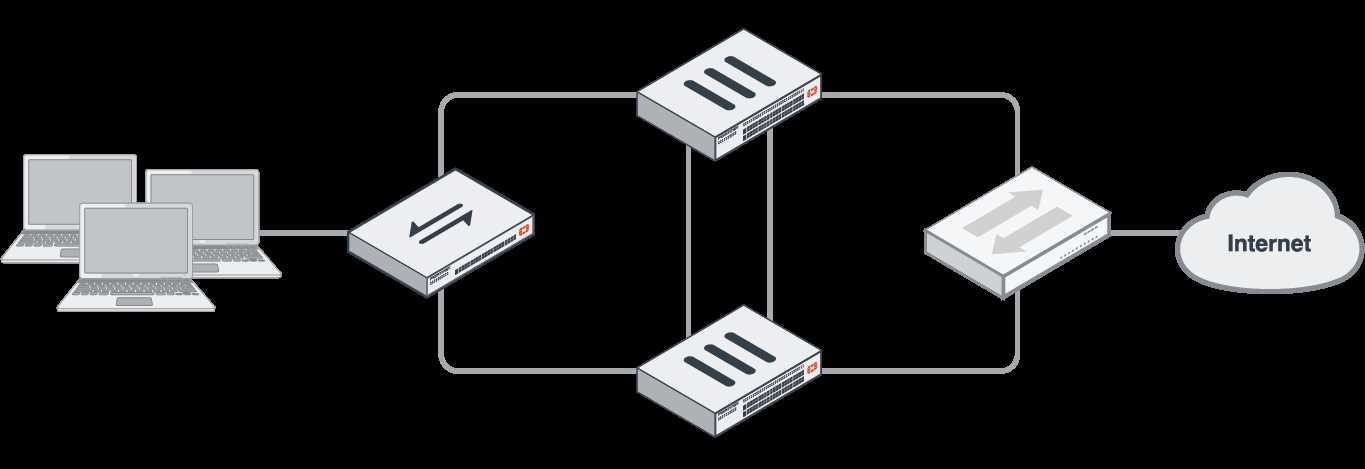
Throughout our analysis, we scrutinize the device’s ability to process data swiftly and effectively, emphasizing its performance under different loads and conditions. We investigate how it manages computational tasks, ensuring optimal utilization of resources and minimal latency.
Scalability Assessment

Further, we examine the appliance’s scalability, gauging its capacity to adapt and expand in tandem with evolving network demands. We explore its potential to accommodate increased traffic and workload without compromising operational integrity or introducing bottlenecks.
Deployment Options and Compatibility
In this section, we explore the various methods of deploying and integrating the product, ensuring seamless compatibility with diverse systems and configurations. Understanding the versatility of deployment options is crucial for optimizing performance and enhancing network security.
When considering deployment strategies, it’s essential to assess the scalability and flexibility offered by different approaches. Whether you’re implementing a standalone setup, integrating with existing infrastructure, or orchestrating a comprehensive network overhaul, compatibility plays a pivotal role.
- Standalone Deployment: This option involves deploying the product as an independent entity within your network architecture. It provides simplicity and autonomy, ideal for smaller-scale deployments or targeted security solutions.
- Integration with Existing Systems: Leveraging the product’s compatibility with a wide array of network devices and protocols, integration becomes seamless. This approach enables the consolidation of security measures within your existing framework, enhancing efficiency and reducing overhead.
- Virtualized Environments: With support for virtualization technologies, the product offers adaptability to modern IT infrastructures. Whether deploying on-premises or in cloud environments, virtualization ensures scalability and agility, catering to dynamic organizational needs.
- High-Availability Configurations: Ensuring continuous operation is paramount in mission-critical environments. Implementing high-availability configurations, including active-passive or active-active setups, enhances resilience and minimizes downtime.
Moreover, compatibility extends beyond hardware and software environments to encompass regulatory requirements and industry standards. By adhering to compliance mandates and best practices, you can ensure the seamless integration and operation of the product within your ecosystem.
By evaluating deployment options and ensuring compatibility at every stage, organizations can effectively harness the capabilities of the product to fortify their networks against evolving threats and challenges.