
Discovering the intricacies of state-of-the-art network security infrastructure involves delving into the detailed documentation that outlines its capabilities, performance metrics, and technical specifications. Within this realm of advanced cybersecurity hardware, there exists a formidable apparatus, renowned for its prowess in safeguarding digital networks against a myriad of threats.
Embarking on an exploration of this formidable entity’s technical dossier unveils a treasure trove of insights into its architecture, functionalities, and operational capacities. From its robust processing power to its sophisticated encryption protocols, every facet of this technological marvel is meticulously crafted to fortify digital environments against malicious intrusions.
As we delve deeper into the intricacies of this formidable guardian of cyberspace, we navigate through a labyrinth of specifications, each delineating the device’s ability to repel cyber threats with unparalleled efficiency. Through a lens of technical precision, we unravel the algorithmic intricacies and engineering marvels that underpin its formidable reputation in the realm of network security.
Exploring the Capabilities of the Fortigate 3000f

Embark on a journey through the myriad functionalities and capabilities of this cutting-edge network security solution. Delve into its extensive array of features designed to fortify your network infrastructure and safeguard your digital assets.
Discover the rich tapestry of security tools and protocols engineered to shield your network from a spectrum of cyber threats. Uncover innovative technologies that empower administrators with granular control over network traffic, ensuring optimal performance and protection.
Explore the versatile suite of security services seamlessly integrated into the Fortigate 3000f, bolstering defense mechanisms against malicious intrusions and ensuring compliance with industry standards. From advanced threat detection to robust encryption protocols, unlock the potential of your network with this comprehensive security platform.
Navigate through the intuitive user interface and ergonomic design crafted to streamline deployment and management processes. Gain insights into the scalability and flexibility inherent in the architecture of the Fortigate 3000f, tailored to adapt to the evolving demands of modern networks.
Experience firsthand the seamless integration capabilities of this versatile solution, facilitating interoperability with existing network infrastructure and third-party applications. Harness the power of automation and orchestration to optimize workflows and enhance operational efficiency.
Unveiling Performance Specifications
Delving into the intricacies of operational capabilities, this section unveils the core performance specifications of the device, offering a comprehensive overview of its capabilities and functionalities. Through meticulous examination and analysis, we uncover the dynamic range of operational parameters that define the prowess of this advanced solution.
- Throughput: Revealing the speed and efficiency at which data traverses through the system, indicating its ability to handle varying workloads seamlessly.
- Latency: Unveiling the responsiveness of the system, elucidating the delay experienced in data transmission and processing.
- Concurrent Connections: Shedding light on the device’s ability to manage multiple connections simultaneously, ensuring smooth and uninterrupted operation.
- Packet Processing: Uncovering the intricacies of packet handling, elucidating the device’s capability to inspect, filter, and forward data packets efficiently.
- Security Services: Disclosing the array of security features integrated into the system, safeguarding against diverse threats and vulnerabilities.
By unraveling these performance specifications, users gain a deeper understanding of the device’s operational capabilities, empowering them to make informed decisions regarding its deployment and utilization.
Security Capabilities and Threat Prevention
In this section, we delve into the robust array of security features and advanced threat mitigation techniques incorporated within the specified device. It encompasses a multifaceted defense strategy, meticulously crafted to safeguard against a spectrum of cyber threats, ranging from common malware to sophisticated attacks.
Comprehensive Threat Intelligence
Embedded within the framework of this system is a sophisticated threat intelligence mechanism, constantly gathering and analyzing data from diverse sources across the digital landscape. Through this amalgamation of global threat intelligence feeds and real-time updates, the system remains vigilant against emerging threats, ensuring proactive defense measures.
Dynamic Threat Prevention
Employing cutting-edge technologies, this platform implements dynamic threat prevention methodologies to intercept and neutralize malicious activities in real-time. By leveraging behavioral analysis, signature-based detection, and heuristic algorithms, it fortifies the digital perimeter against intrusions, exploits, and zero-day vulnerabilities, thereby mitigating potential risks before they escalate.
Scalability and Integration Options
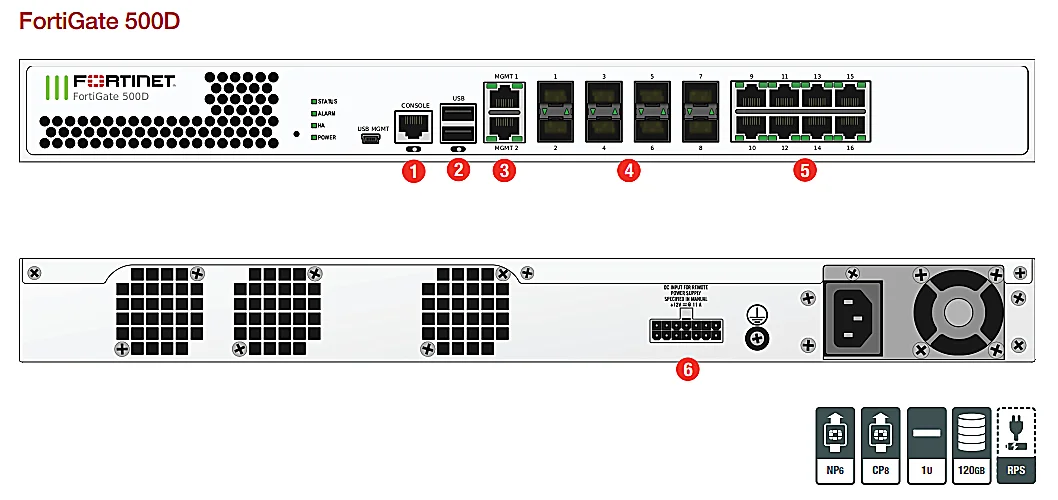
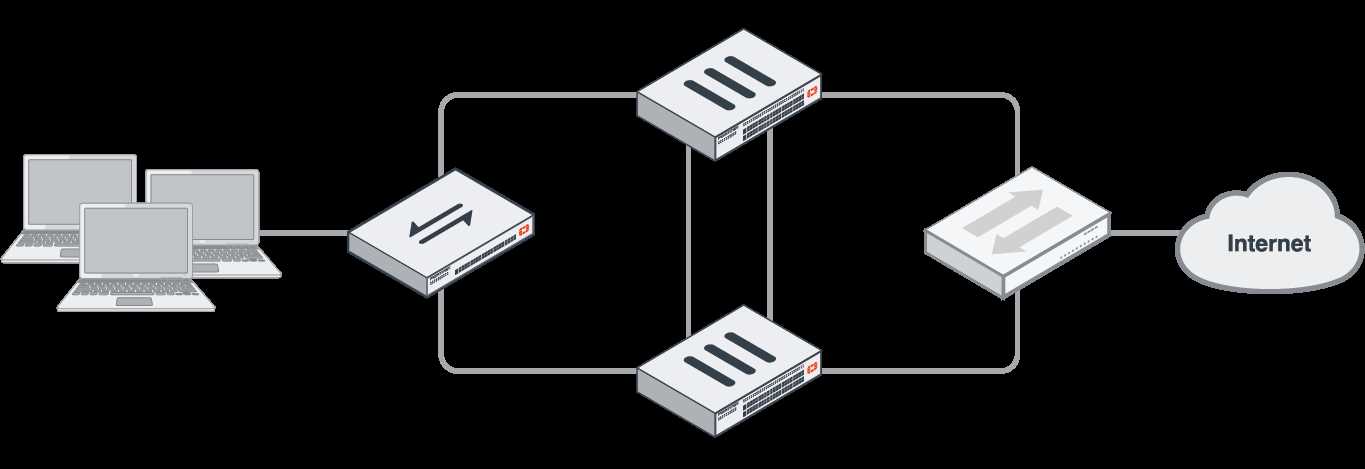
In the realm of network infrastructure, the ability to expand and adapt is paramount. This section delves into the diverse array of scalability and integration options available, allowing seamless growth and incorporation into existing systems.
1. Flexibility in Expansion

One of the key aspects highlighted here is the adaptability of the system to accommodate increased demands. Whether it’s through modular additions or dynamic allocation of resources, the solution offers avenues for organic growth without disruptions.
2. Interoperability with Existing Frameworks
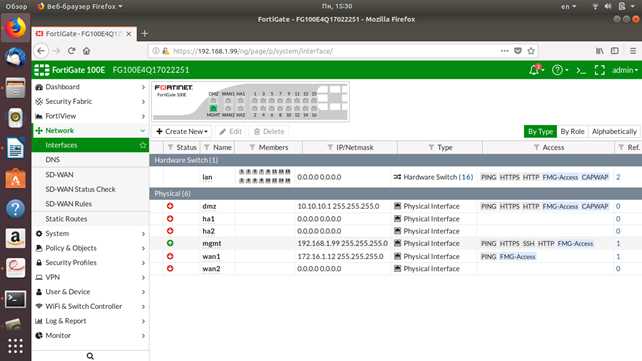
Integration plays a pivotal role in ensuring a cohesive network environment. By seamlessly meshing with established infrastructures and protocols, the system fosters interoperability, enabling smooth communication and data flow across diverse platforms.
- Compatibility with industry-standard protocols
- Support for third-party applications and tools
- Effortless integration into heterogeneous environments
These facets empower administrators to architect robust networks that can readily adapt to evolving requirements and incorporate emerging technologies.