
Discovering the myriad capabilities and functionalities of this robust security apparatus entails delving into its intricate specifications, meticulously engineered to fortify digital landscapes against myriad threats. Within these technical blueprints lie the blueprint for safeguarding networks, intricately woven with layers of protection, meticulously designed to ward off intrusions and fortify cyber perimeters.
Unveiling the nuances of its architecture reveals a tapestry of innovative solutions, each thread intricately spun to mitigate risks and bolster defense mechanisms. As we navigate through this landscape of digital security, we encounter a plethora of features, each indispensable in its contribution to the holistic safeguarding of sensitive data and critical infrastructure.
Embark on a journey through the landscape of resilience, where every specification serves as a cornerstone in the construction of impregnable cyber fortresses. Let us embark on an expedition through the realms of security, where each parameter, each attribute, paints a vivid picture of protection against the ever-evolving threatscape.
Understanding Fortigate 110c: An In-Depth Overview

In this section, we delve into the intricacies of one of the industry’s leading network security appliances, offering a comprehensive examination of its features, capabilities, and performance. Through meticulous analysis and insightful discussion, we aim to provide a nuanced understanding of this robust firewall device, shedding light on its role in safeguarding networks against a myriad of threats.
| Performance | Security Features | Connectivity Options |
| Delivering optimal throughput and responsiveness, this device ensures seamless operation even under high network loads. | Equipped with a suite of advanced security functionalities, it fortifies networks against intrusions, malware, and unauthorized access. | Offering diverse connectivity options, from traditional Ethernet ports to VPN support, it facilitates flexible network configurations tailored to specific requirements. |
Through a detailed examination of its performance metrics, security provisions, and connectivity options, readers will gain a holistic perspective on the capabilities of this versatile network security solution. By elucidating its strengths and capabilities, we empower stakeholders to make informed decisions regarding network defense strategies and infrastructure investments.
Key Features and Technical Specifications
In this section, we delve into the core aspects and technical intricacies that define the essence of the device under scrutiny. Unveiling the foundational pillars of its functionality and performance, we unravel a comprehensive array of characteristics and capabilities, elucidating its prowess in navigating the realms of network security and management.
Embarking on an exploration of its key features, we unearth a plethora of functionalities designed to fortify digital perimeters and fortify against cyber threats. From advanced intrusion detection mechanisms to robust encryption protocols, each facet contributes to a resilient defense architecture, safeguarding against malicious incursions and ensuring the integrity of data transmission.
Delving into the realm of technical specifications, we decipher the intricate details that underpin its operational prowess. From processing power to memory allocation, bandwidth management to interface configurations, each specification serves as a cornerstone in shaping its performance landscape, orchestrating seamless operations and facilitating efficient network management.
Moreover, we illuminate the dynamic ecosystem of connectivity options, delineating the diverse array of interfaces and protocols that enable seamless integration within existing infrastructures. Whether it be Ethernet ports for wired connectivity or support for emerging wireless standards, the device stands poised to adapt and evolve in tandem with evolving technological landscapes.
As we traverse through this compendium of features and specifications, a holistic understanding emerges, showcasing the device’s versatility and reliability in addressing the multifaceted challenges of modern network security. It stands not merely as a tool, but as a strategic asset in fortifying digital fortresses and safeguarding the integrity of digital assets.
Performance Metrics and Deployment Considerations
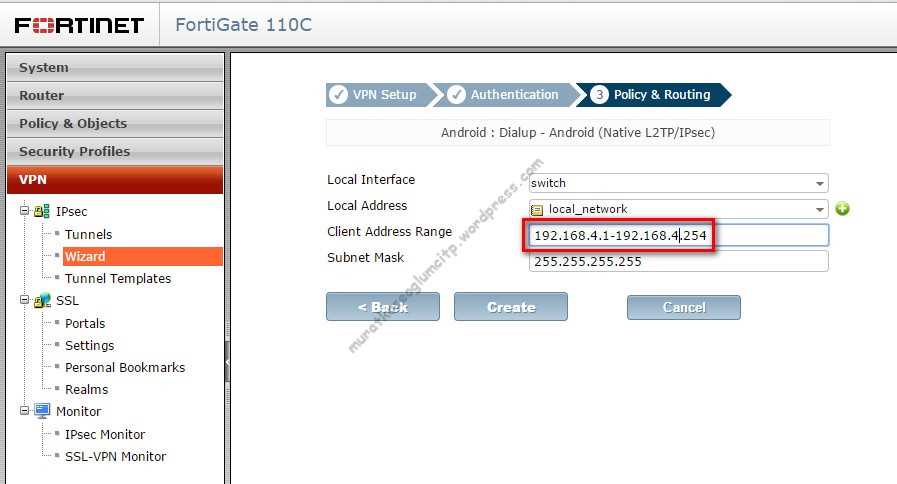
In this section, we delve into the various aspects governing the efficiency and efficacy of the device, along with strategic insights for its optimal integration into network infrastructures.
When evaluating the capabilities of this technology, it’s essential to delve beyond raw numbers and delve into the intricacies of its operational dynamics. Understanding the intricacies of throughput, latency, and scalability provides a holistic perspective, enabling informed decision-making regarding its deployment.
| Performance Metric | Description |
|---|---|
| Throughput | The rate at which data is processed, indicative of the device’s capacity to handle network traffic efficiently. |
| Latency | The delay incurred in data transmission, influencing the responsiveness of network applications and user experience. |
| Scalability | The ability of the system to accommodate increasing demands without compromising performance or stability. |
Deployment considerations play a pivotal role in harnessing the full potential of this technology. Factors such as network architecture, traffic patterns, and security requirements necessitate careful deliberation to ensure seamless integration and optimal functionality.
Moreover, strategic placement within the network topology and alignment with existing infrastructure are critical determinants of its effectiveness. Whether deployed as a perimeter defense mechanism or an internal security gateway, understanding the nuanced implications is imperative for achieving desired outcomes.
Security Capabilities and Network Protection Mechanisms
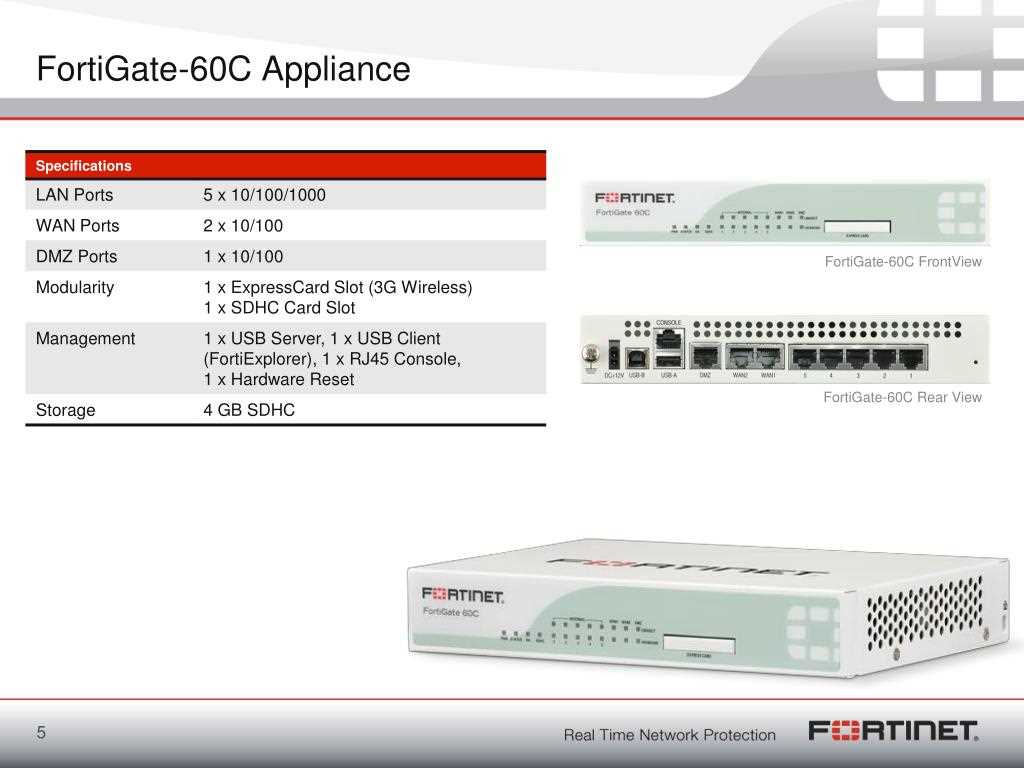
In the realm of network security, robust defense mechanisms are paramount to safeguarding sensitive data and ensuring uninterrupted operations. This section explores the arsenal of protective features and mechanisms designed to fortify networks against diverse threats and vulnerabilities.
Comprehensive Threat Detection

Within modern networks, a sophisticated array of threat detection mechanisms stands as the first line of defense. These systems employ advanced algorithms and heuristic analysis to identify and neutralize potential security breaches, ranging from malware and ransomware to intrusions and data exfiltration attempts.
Dynamic Firewalling and Access Control
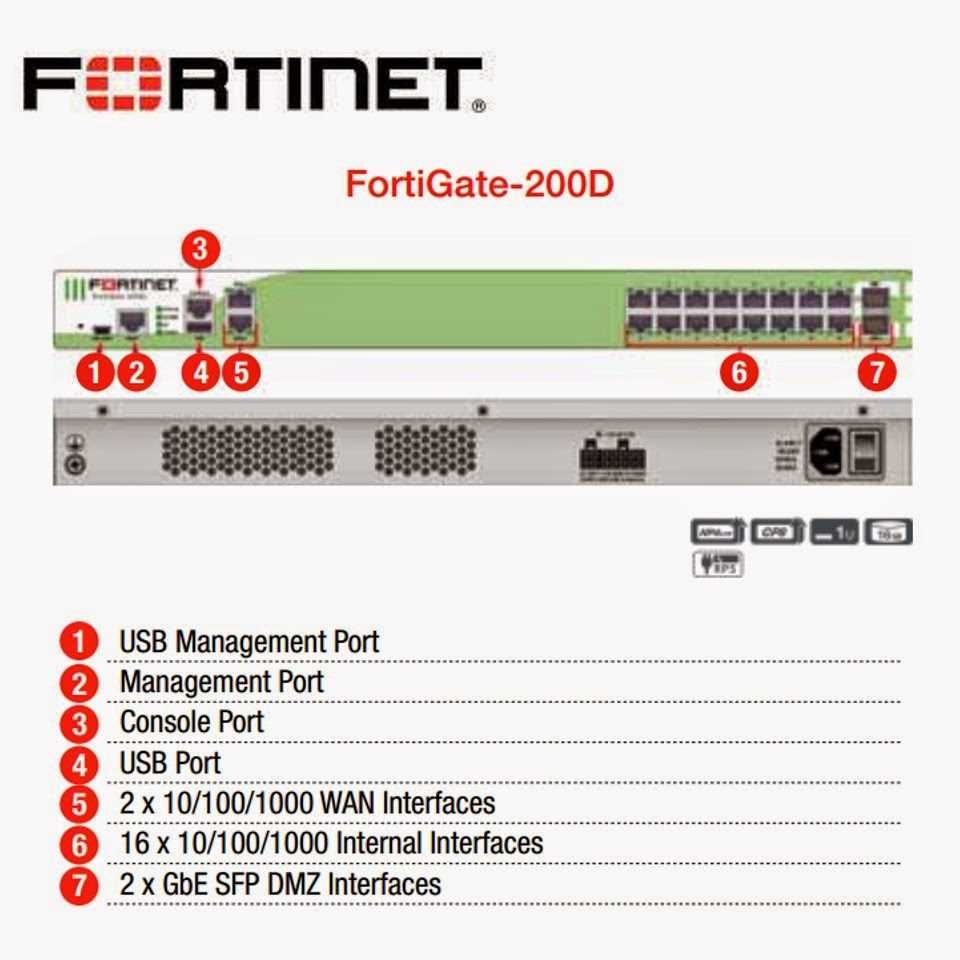
Effective network protection extends beyond mere threat detection, encompassing proactive measures such as dynamic firewalling and access control. By meticulously regulating traffic flow and enforcing granular policies, organizations can erect virtual barriers against unauthorized access, thereby mitigating the risk of unauthorized data exposure or system compromise.
- Intrusion Prevention Systems (IPS)
- Virtual Private Network (VPN) Integration
- Denial-of-Service (DoS) Mitigation
- Content Filtering and Application Control
These mechanisms collectively contribute to a multi-layered defense strategy, bolstering network resilience and fostering a secure operational environment.