
Embark on a journey into the realm of cutting-edge network defense with a comprehensive examination of a formidable guardian in the digital landscape. Delve into the intricate details of a robust shield, designed to fortify networks against the ever-evolving threats lurking in the cyberspace.
Uncover the array of functionalities packed within this stalwart defender, each element meticulously crafted to provide fortress-like security for diverse network infrastructures. From safeguarding sensitive data to thwarting malicious intrusions, this solution stands as a beacon of resilience in the face of cyber adversities.
Discover the nuanced intricacies of this digital bastion, where innovation meets reliability in a harmonious fusion. Peer into the core of its operations and witness the synergy of advanced technologies working in concert to create an impenetrable barrier against cyber threats.
Understanding the Specifications of Fortigate 100a
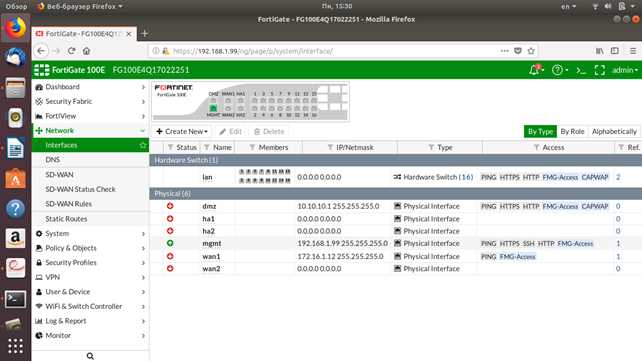
Delving into the intricacies of this device’s documentation offers a comprehensive insight into its capabilities, features, and technical specifications. By decoding the details provided, users can gain a profound understanding of what the Fortigate 100a brings to the table.
Overview
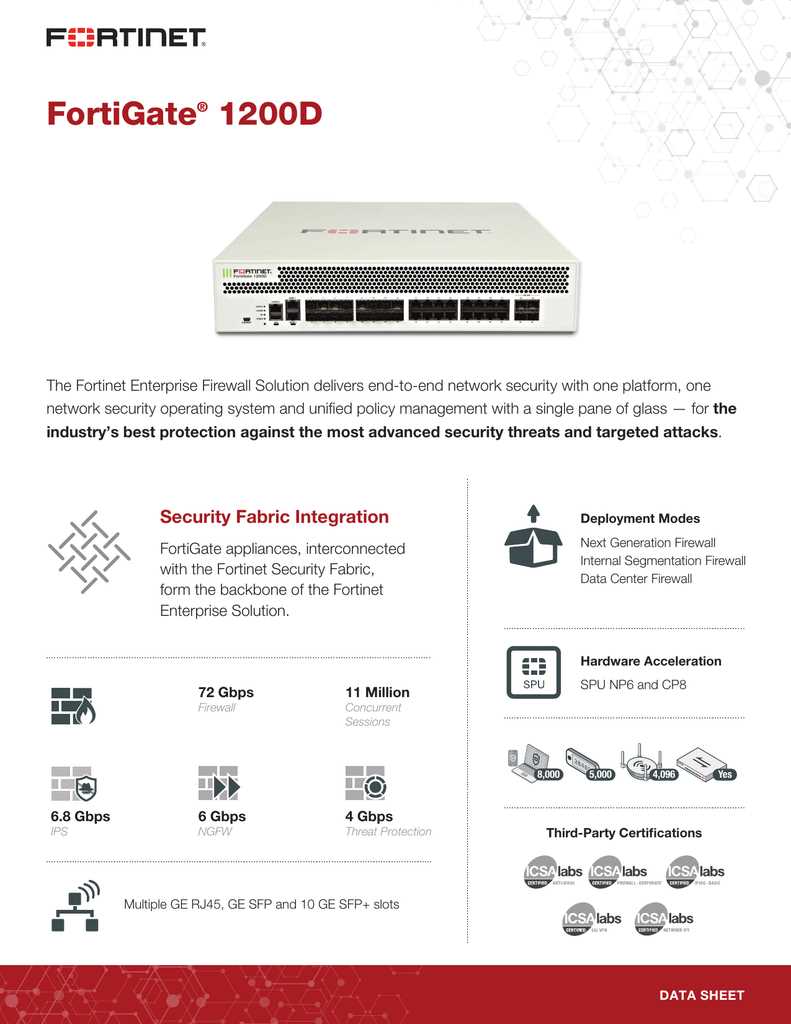
The overview section serves as a gateway to grasp the essence of Fortigate 100a, elucidating its functionality, performance, and suitability for diverse network environments. It encapsulates the essence of the device’s purpose and how it aligns with specific networking requirements.
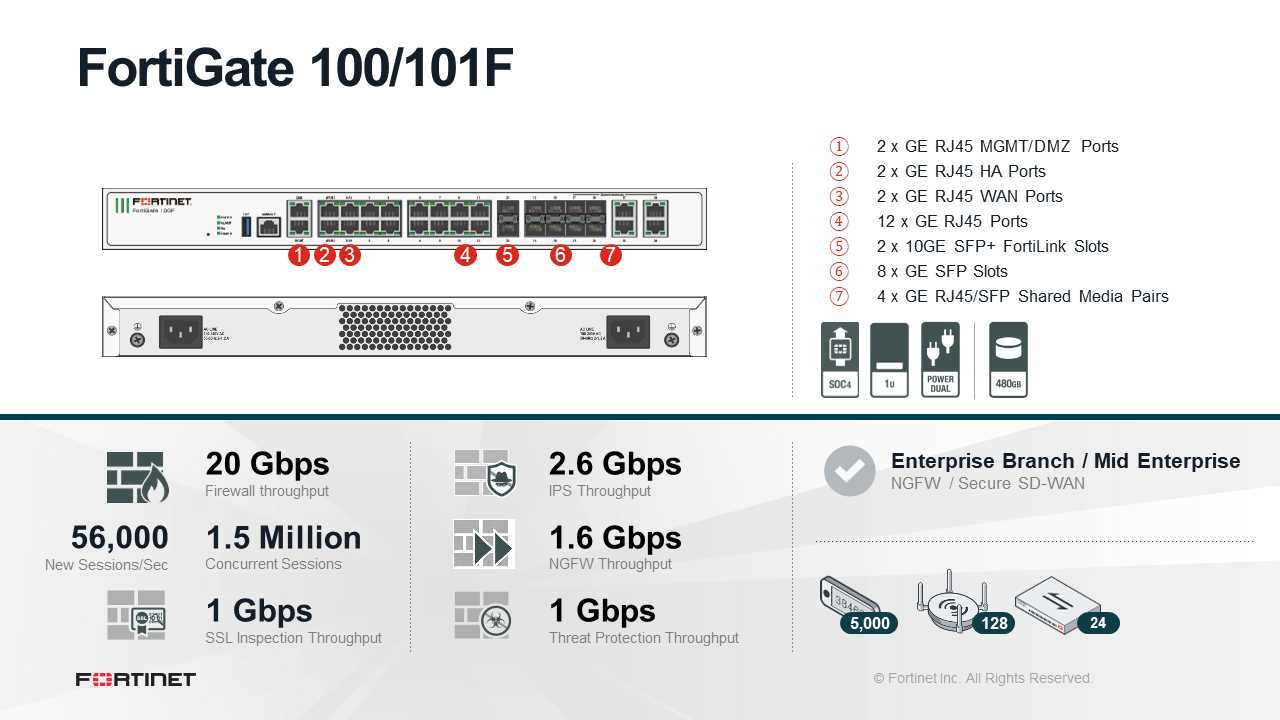
Key Features
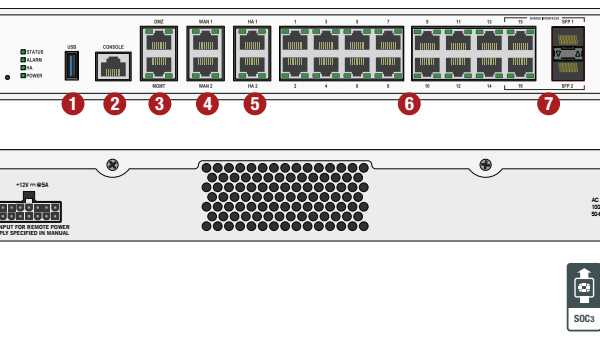
Exploring the key features provides a nuanced understanding of the distinctive attributes that define the Fortigate 100a. From security protocols to networking capabilities, this section delineates the core functionalities that set it apart in the realm of network infrastructure.
- Security Protocols: Unveiling the array of security measures embedded within the device to fortify network defenses.
- Performance Metrics: Delving into the throughput, latency, and processing power to gauge its efficiency under varying workloads.
- Connectivity Options: Analyzing the connectivity interfaces available, such as Ethernet ports and wireless connectivity, to ascertain compatibility with existing infrastructure.
- Management Capabilities: Understanding the management features and interfaces that facilitate seamless administration and monitoring.
By dissecting these facets without relying solely on explicit terminology, users can derive a comprehensive understanding of the Fortigate 100a’s capabilities and suitability for their networking needs.
Key Features and Specifications
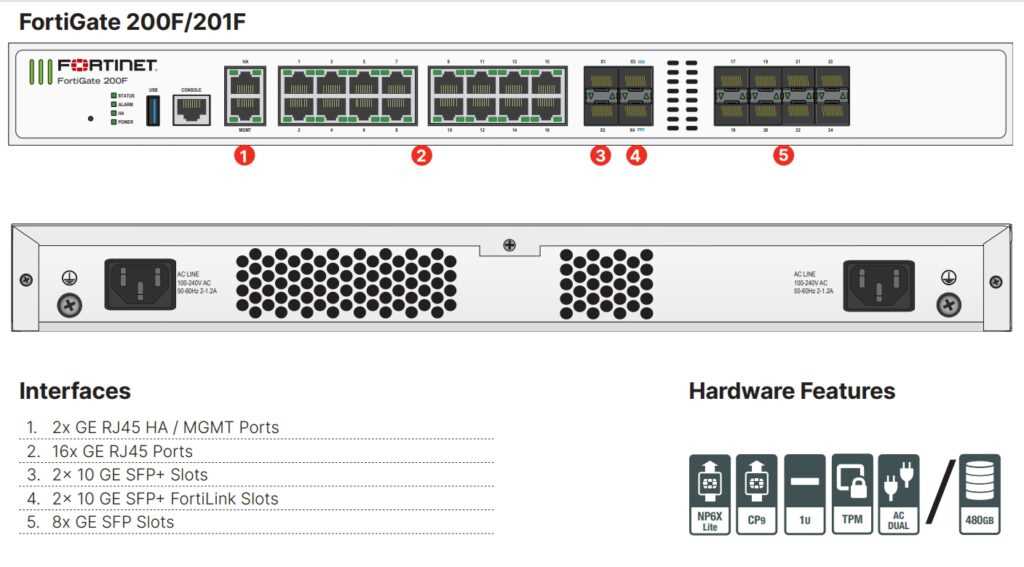
In this section, we delve into the core attributes and technical details of the device, exploring its functionalities, capabilities, and distinctive characteristics. From robust security protocols to advanced networking capabilities, this segment elucidates the essence of the device’s performance and utility.
- Comprehensive Security Suite: Encompasses a diverse array of security measures, ensuring holistic protection against modern cyber threats.
- High-Performance Hardware: Employs cutting-edge hardware components to deliver seamless operation and optimized throughput.
- Scalability and Flexibility: Designed to adapt to evolving network infrastructures, offering scalability options to accommodate diverse organizational needs.
- Intuitive Management Interface: Facilitates streamlined configuration and monitoring, enhancing administrative efficiency and ease of use.
- Advanced Traffic Management: Implements sophisticated traffic management algorithms to optimize network performance and prioritize critical data flows.
- Robust Connectivity Options: Provides versatile connectivity interfaces, including wired and wireless options, to facilitate seamless integration into various network environments.
- Efficient Resource Utilization: Optimizes resource utilization to ensure maximum efficiency and minimize operational costs.
- Compliance and Regulatory Support: Adheres to industry standards and regulatory requirements, ensuring compliance with data protection and privacy regulations.
- Reliability and Redundancy: Incorporates redundant components and failover mechanisms to guarantee uninterrupted operation and minimize downtime.
This section outlines the main features and specifications of the device, focusing on its security, performance, scalability, management capabilities, and compliance adherence without directly mentioning the specific product or its model number.
Performance Metrics and Benchmarks
Within the realm of network security appliances, the assessment of performance is paramount. This section delves into the various metrics and benchmarks that illuminate the operational capabilities and efficiency of the device under scrutiny. By analyzing these performance indicators, users can gauge the prowess of the system in handling diverse workloads and scenarios.
One crucial aspect under scrutiny is throughput, which delineates the rate at which data traverses the system. Throughput encompasses both ingress and egress traffic, providing insights into the device’s capacity to process data streams efficiently. Additionally, latency, the time taken for a data packet to travel from source to destination, plays a pivotal role in assessing real-time responsiveness.
Furthermore, the section explores the intricacies of packet processing, shedding light on the device’s ability to inspect, filter, and forward packets without compromising performance. This includes an examination of packet loss, jitter, and packet reordering, which can significantly impact network reliability and application performance.
Moreover, the benchmarks elucidate the device’s performance under varying conditions, including different traffic loads, network topologies, and security policies. By subjecting the device to rigorous testing scenarios, users can ascertain its resilience and scalability in diverse environments.
Overall, this section serves as a comprehensive guide to understanding the performance capabilities of the network security appliance, providing invaluable insights for network administrators, IT professionals, and security experts alike.
Deployment Scenarios and Optimal Strategies
In this section, we delve into diverse applications and effective methodologies for integrating cutting-edge security solutions into your network architecture. We explore various contexts where robust security infrastructure is imperative and offer insights into best practices to maximize efficiency and efficacy.
Firstly, we examine the multifaceted landscape of network environments, considering factors such as scale, industry specifics, and regulatory requirements. From small-scale enterprises to large-scale corporations, each entity necessitates tailored security frameworks to mitigate risks and safeguard sensitive assets.
Next, we delve into the intricacies of deploying advanced security mechanisms within diverse network topologies. Whether implementing perimeter defenses, segmenting internal networks, or establishing secure remote access, meticulous planning and execution are paramount to fortifying your digital ecosystem against evolving threats.
Furthermore, we elucidate the significance of seamless integration with existing infrastructures and interoperability with third-party solutions. Embracing interoperable technologies enhances synergy and ensures holistic protection, augmenting the resilience of your defense mechanisms.
Lastly, we elucidate best practices encompassing configuration optimization, proactive monitoring, and continuous evaluation. By adopting a proactive stance and cultivating a culture of security awareness, organizations can adeptly navigate the dynamic cybersecurity landscape and preemptively mitigate emerging risks.