
Delve into the realm of innovative network security technology with an in-depth exploration of a formidable device, boasting a plethora of functionalities to fortify your digital infrastructure.
Embark on a journey to uncover the capabilities of a powerful guardian, meticulously designed to safeguard your network from the ever-evolving landscape of cyber threats.
Discover a comprehensive array of specifications and performance metrics, providing insights into the robustness and reliability of this advanced solution.
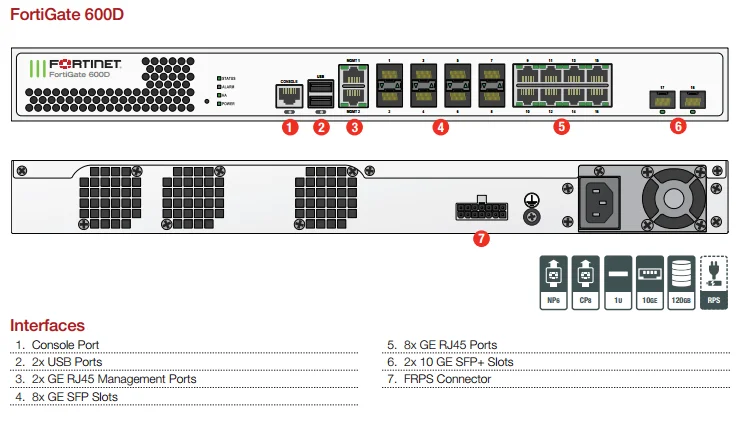
Exploring the Essential Specifications of the Fortigate 1001f

Delving into the intricacies of this high-performance network security appliance unveils a wealth of pivotal specifications that drive its robust functionality and reliability. Understanding these key metrics provides a comprehensive insight into the capabilities and potential of this advanced firewall solution.
Performance Metrics

Throughput: Unveiling the processing prowess, throughput metrics illustrate the volume of data the device can handle, ensuring seamless network operations even under heavy loads. This metric serves as a cornerstone for assessing the device’s efficiency and responsiveness.
Security Features: Beyond mere throughput, the depth and breadth of security features represent the fortitude of the appliance in safeguarding network integrity. From intrusion prevention to advanced threat protection, a nuanced understanding of these features elucidates the device’s capacity to thwart diverse cyber threats.
Scalability and Flexibility

Expandability: Embracing the evolving landscape of network demands, scalability metrics delineate the device’s potential to grow alongside organizational requirements. Whether it’s accommodating increasing bandwidth or integrating additional security services, scalability ensures future-proofing against emerging challenges.
Integration Capabilities: In the intricate ecosystem of modern networks, integration prowess emerges as a defining attribute. The device’s ability to seamlessly integrate with existing infrastructure and third-party applications not only enhances operational efficiency but also fosters interoperability across heterogeneous environments.
Unveiling the Performance Metrics

In this section, we delve into the intricate details of the operational capacities of the specified hardware, shedding light on its capabilities without resorting to specific nomenclature. Our exploration encompasses various facets of performance, offering insights into the device’s efficacy across a spectrum of functions and scenarios.
Throughput Analysis
Examining the throughput of the device, we dissect its ability to handle data transfer across diverse protocols and applications. By scrutinizing its efficiency in processing incoming and outgoing traffic, we unravel its proficiency in sustaining seamless connectivity and swift data transmission.
Resource Utilization Evaluation

Delving into resource utilization, we analyze the device’s adeptness in allocating and managing available resources to optimize performance. From CPU utilization to memory management, we decipher the efficiency of resource utilization strategies deployed within the system.
| Metric | Definition | Analysis |
|---|---|---|
| Throughput | The rate of data transfer | Assessing the device’s capacity to handle data transmission across various protocols |
| Resource Utilization | The efficient allocation and management of resources | Evaluating the device’s utilization of CPU, memory, and other resources to optimize performance |
Understanding Security Features and Capabilities

Exploring the Security Landscape: Delving into the realm of cybersecurity entails a comprehensive understanding of the myriad features and capabilities designed to safeguard digital assets. This section embarks on an insightful journey into the diverse facets of security, elucidating the multifaceted layers of protection.
Comprehensive Defensive Arsenal: Within the realm of digital security, a robust repertoire of defensive mechanisms stands as the cornerstone of safeguarding against diverse threats. From proactive preventive measures to responsive reactive strategies, this section delineates the comprehensive array of tools and techniques at hand.
Strategic Risk Mitigation: Navigating the intricate landscape of security necessitates a strategic approach towards risk mitigation. By identifying vulnerabilities, fortifying defenses, and implementing proactive measures, organizations can effectively mitigate risks and fortify their digital infrastructure against potential threats.
Dynamic Threat Detection: In an ever-evolving threat landscape, dynamic threat detection mechanisms play a pivotal role in identifying and thwarting emerging security risks. This section delves into the intricacies of threat detection methodologies, exploring the dynamic algorithms and heuristic analyses employed to detect and neutralize potential threats in real-time.
Proactive Incident Response: Beyond detection, proactive incident response mechanisms are instrumental in swiftly mitigating security breaches and minimizing potential damage. By establishing robust incident response protocols and leveraging automation technologies, organizations can expedite response times and mitigate the impact of security incidents.
Continuous Adaptation and Optimization: Sustaining effective security posture necessitates a commitment to continuous adaptation and optimization. This section explores the iterative process of security optimization, emphasizing the importance of ongoing evaluation, refinement, and adaptation to emerging threats and evolving security challenges.
Examining Scalability and Deployment Options
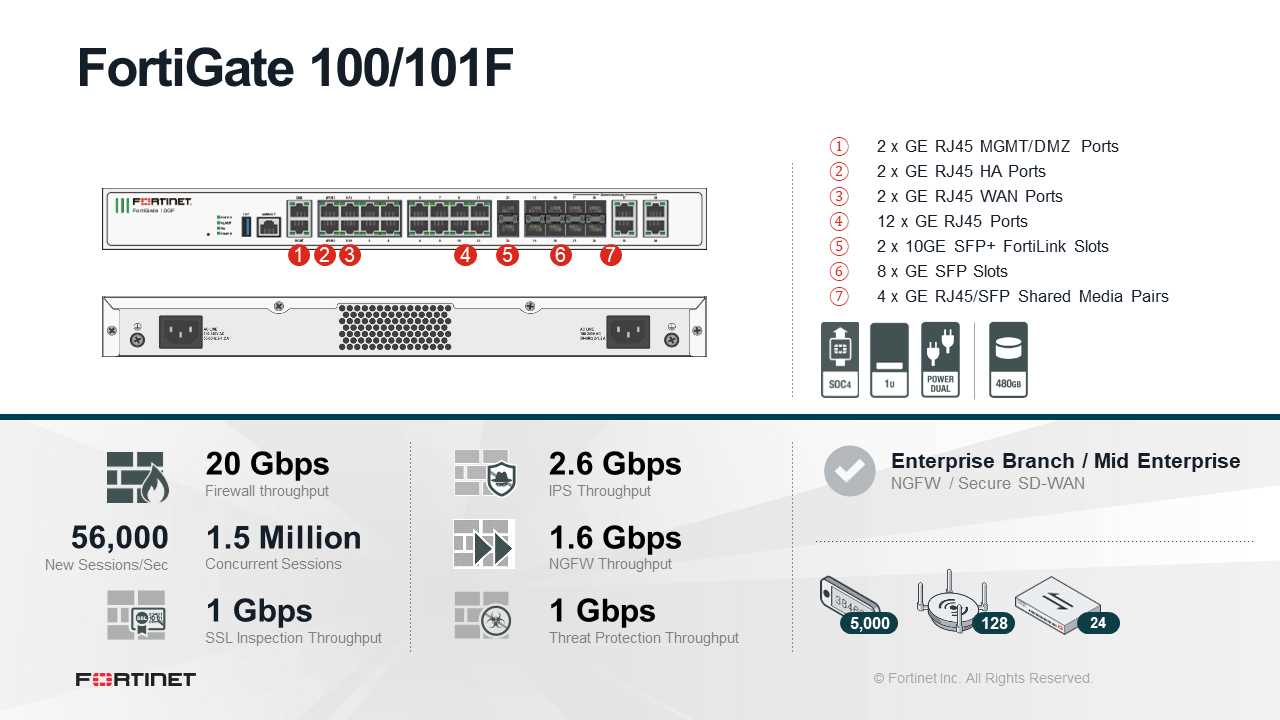
In this section, we delve into the various aspects of expanding capacity and implementing our solution across diverse environments. We explore the ability of our system to adapt to increasing demands, considering factors such as growth potential, flexibility in deployment, and adaptability to changing requirements.
Understanding Scalability: Scalability refers to the capability of a system to handle a growing amount of work, or its potential to be enlarged to accommodate that growth. We analyze how our solution can seamlessly grow alongside your organization, catering to evolving needs without compromising performance or reliability.
Exploring Deployment Flexibility: Deployment flexibility encompasses the versatility of our solution in terms of installation options, integration with existing infrastructure, and adaptability to diverse network architectures. We investigate the ease of deployment across different environments, including on-premises setups, cloud environments, and hybrid configurations.
Assessing Resource Allocation: Efficient resource allocation is crucial for optimizing performance and minimizing costs. We assess the resource management capabilities of our solution, examining its ability to allocate resources dynamically based on demand, ensuring optimal utilization without overprovisioning.
Examining High Availability: High availability is essential for ensuring uninterrupted operation and minimizing downtime. We evaluate the redundancy features and failover mechanisms integrated into our solution, guaranteeing continuous availability and reliability even in the face of hardware failures or network disruptions.
Evaluating Scalability in Practice: Finally, we provide real-world examples and case studies demonstrating how our solution has been successfully deployed in various scenarios, showcasing its scalability in action and illustrating the benefits it brings to organizations of different sizes and industries.