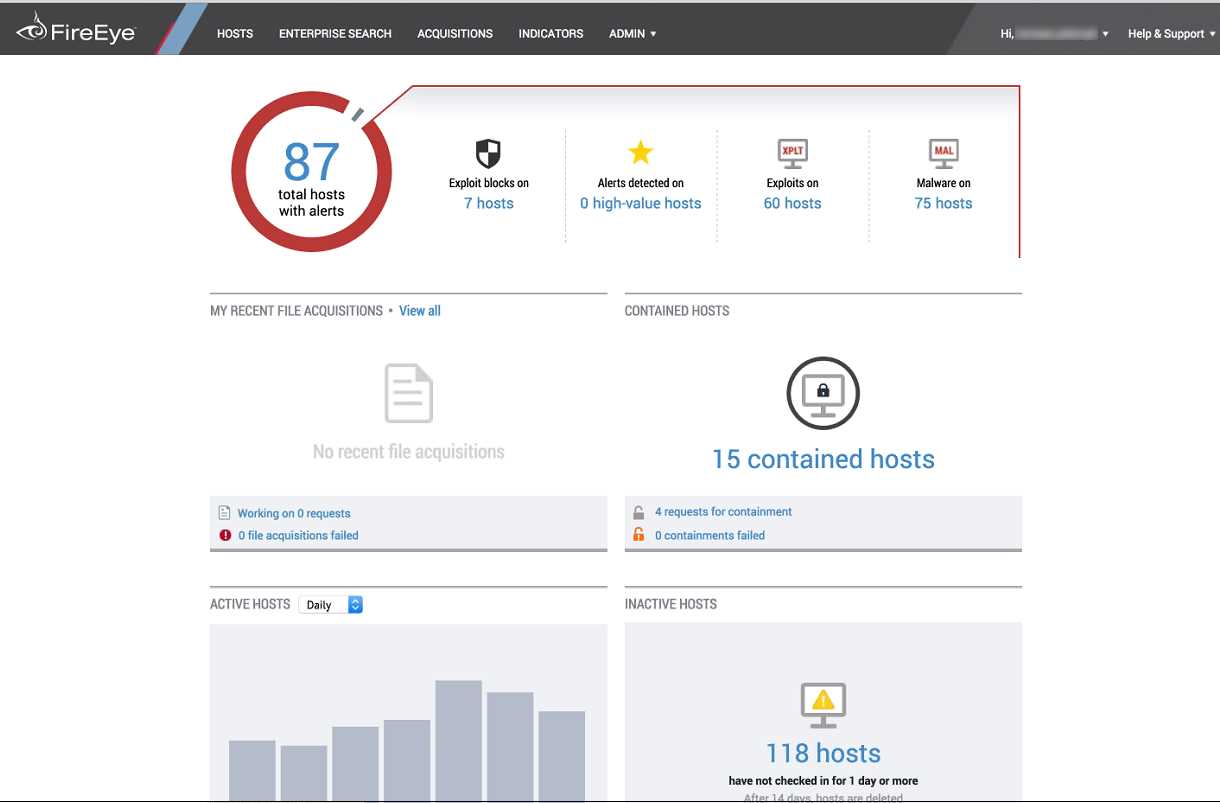
In today’s fast-paced digital landscape, businesses face an ever-increasing number of cyber threats. As technology evolves, so too do the tactics used by malicious actors seeking to breach the security of our valuable data. Protecting our endpoints has become more crucial than ever before.
Introducing a cutting-edge solution that will revolutionize your cybersecurity strategy – the game-changing FireShield Endpoint Armor. Developed by industry-leading experts, this formidable tool offers an unprecedented level of defense against cyber threats, ensuring the safety and integrity of your most sensitive information.
With FireShield Endpoint Armor, you can stay one step ahead of cybercriminals who employ an array of devious techniques to infiltrate your systems. This state-of-the-art software utilizes advanced algorithms that constantly analyze and identify potential vulnerabilities, enabling you to act swiftly and decisively in thwarting any malicious activity. Say goodbye to sleepless nights worrying about the safety of your data – FireShield Endpoint Armor has got you covered.
Imagine a world where your endpoints are not just protected, but also fortified against even the most sophisticated attacks. FireShield Endpoint Armor stands tall as a guardian, equipped with powerful features that bolster your cybersecurity defenses. From real-time threat detection to proactive incident response, its robust capabilities are tailored to address the unique challenges faced by businesses of all sizes, across various industries.
Fireeye Endpoint Security Datasheet: Key Features and Benefits
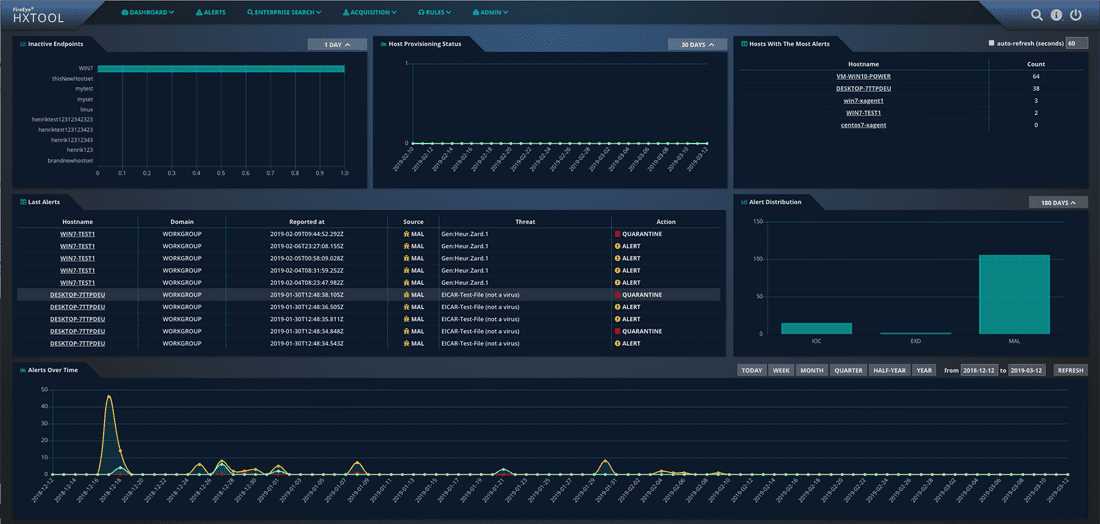
Ensuring the safety and integrity of your organization’s digital assets is of utmost importance in today’s evolving threat landscape. Fireeye’s cutting-edge endpoint security solution is designed to provide comprehensive protection and advanced detection capabilities, empowering businesses to proactively defend against sophisticated cyber threats.
Enhanced Threat Intelligence

- Gain access to a wide range of threat intelligence sources
- Stay ahead of emerging threats with real-time updates and actionable insights
- Leverage machine learning algorithms to analyze and detect anomalous behavior patterns
Advanced Malware Detection
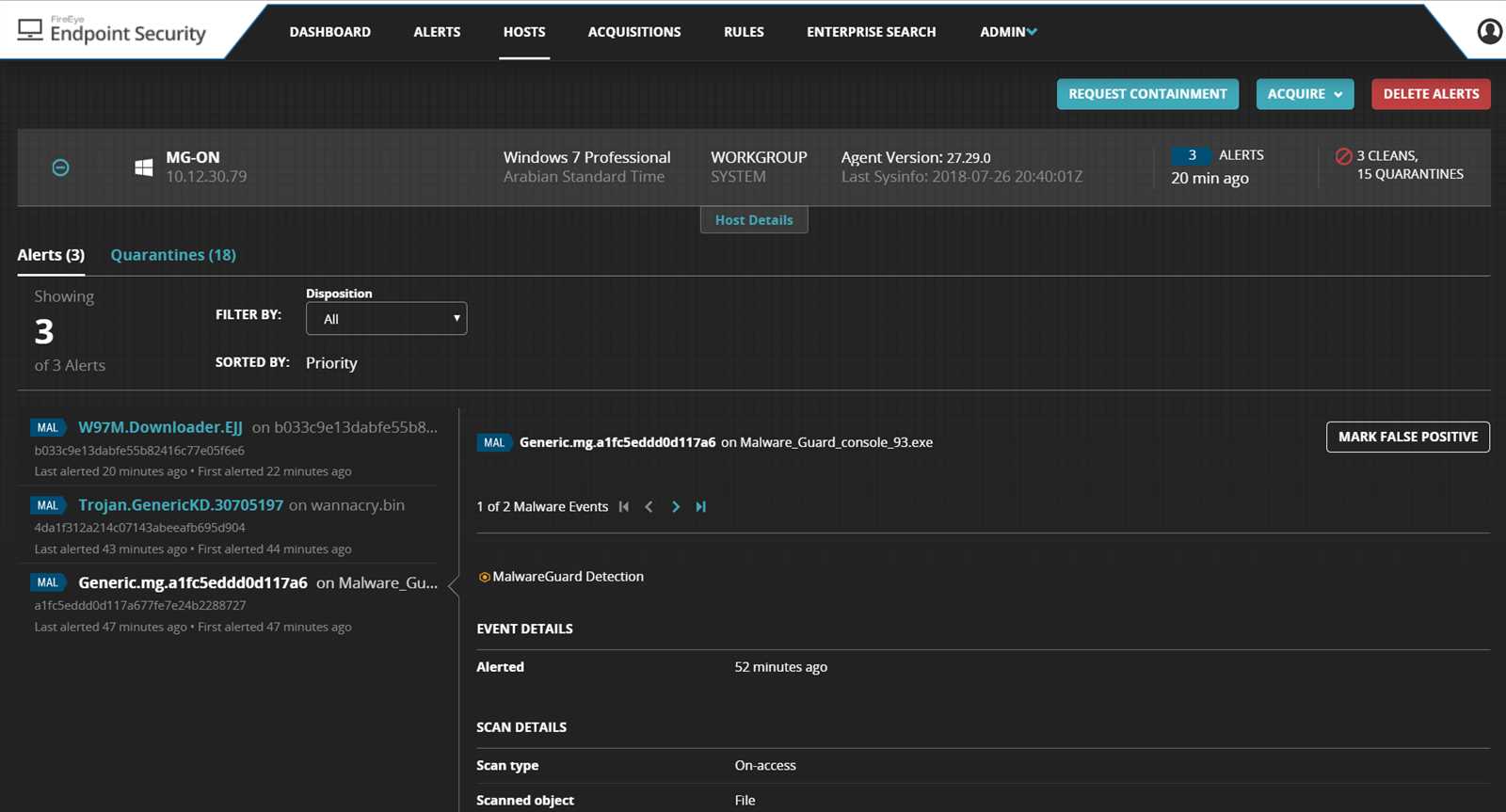
- Detect and block known malware signatures with industry-leading accuracy
- Utilize behavior-based analysis to identify and stop unknown malware
- Benefit from sandboxing technology for comprehensive analysis of suspicious files
Fireeye’s endpoint security solution goes beyond traditional antivirus methods, offering a range of key features and benefits that ensure maximum protection and rapid response to evolving threats. By combining enhanced threat intelligence and advanced malware detection capabilities, businesses can confidently secure their digital assets and minimize the risk of attacks.
Comprehensive Threat Protection for Endpoints
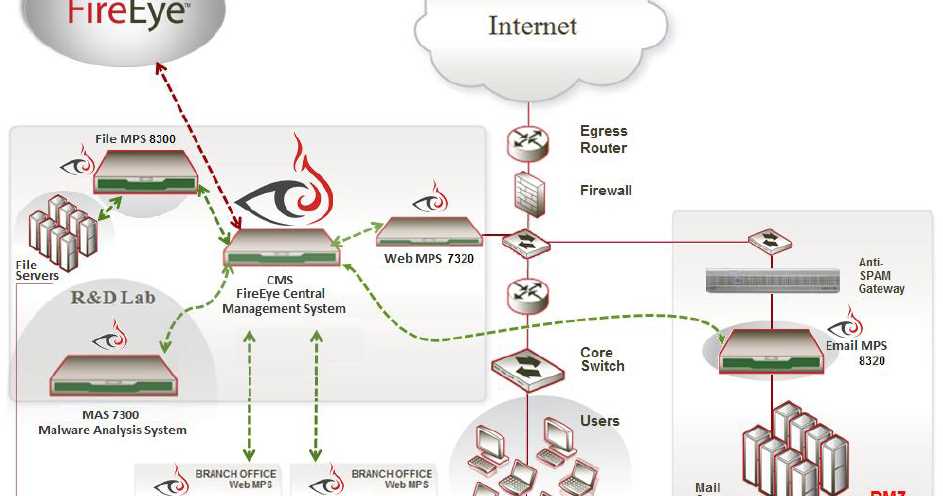
In today’s rapidly evolving digital landscape, protecting endpoints from a diverse range of threats has become a critical priority for organizations across industries. With the increasing sophistication of cyberattacks, it is essential for businesses to implement comprehensive threat protection measures to safeguard their valuable data and systems.
Enhanced Threat Detection
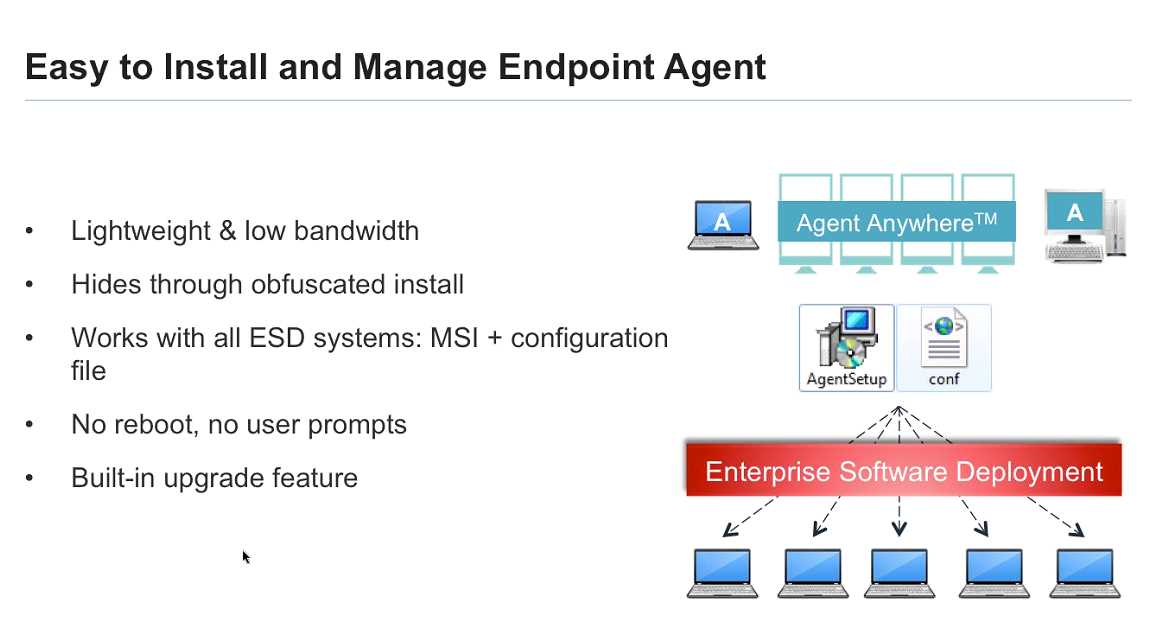
One of the key aspects of comprehensive threat protection for endpoints is the ability to detect and identify a wide range of threats. This includes not only traditional malware and viruses but also advanced persistent threats, zero-day exploits, and targeted attacks. By leveraging advanced algorithms and machine learning techniques, organizations can gain real-time insights into potential threats and take immediate action to mitigate risks.
Proactive Defense Mechanisms
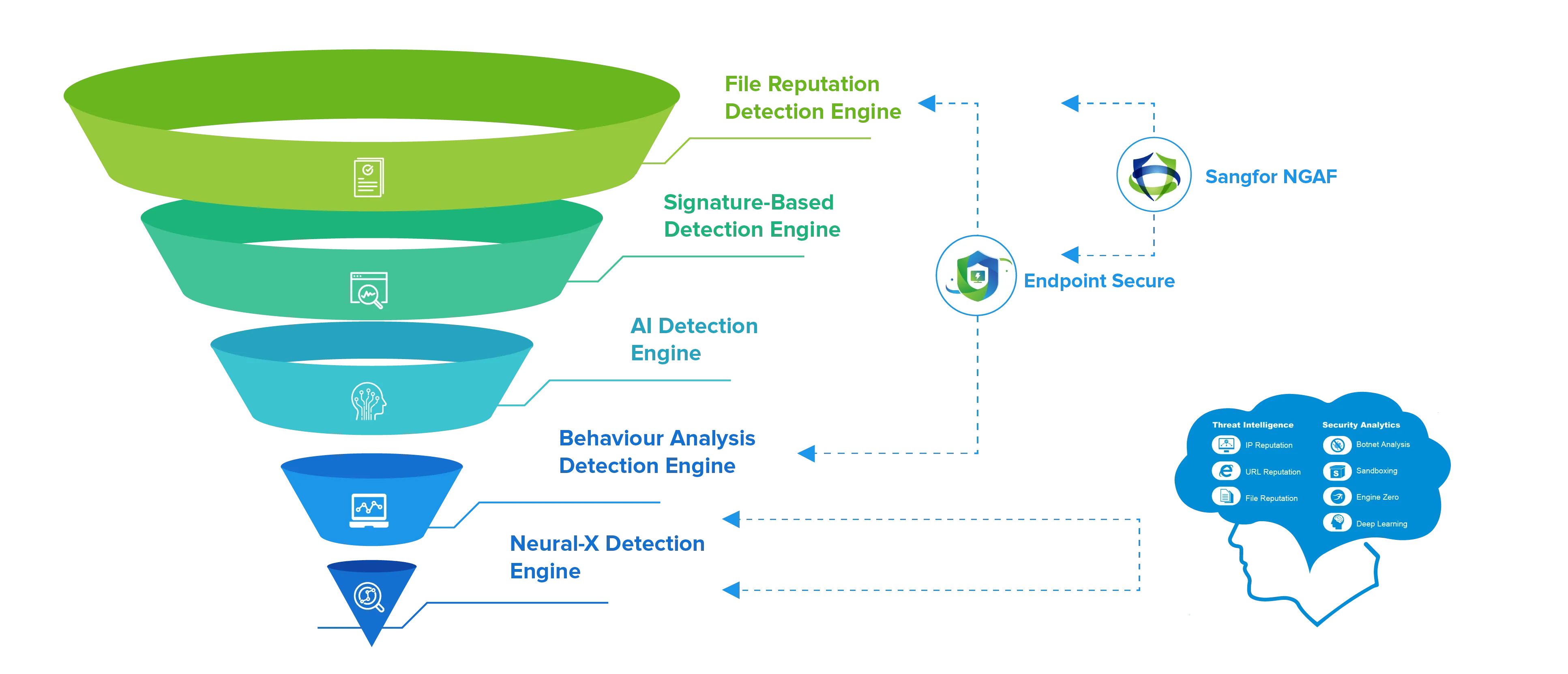
Comprehensive protection goes beyond detection and includes proactive defense mechanisms to prevent and disrupt attacks. These mechanisms may include behavioral analysis, sandboxing, and reputation-based filtering to identify suspicious activities and block potentially harmful content before it reaches the endpoint. By proactively monitoring and analyzing network traffic, organizations can prevent threats from ever reaching their endpoints, minimizing the risk of compromise.
- Behavioral analysis techniques can identify anomalies and deviations from normal user behavior, allowing for early detection of potential threats.
- Sandboxing provides a controlled virtual environment to analyze and execute suspicious files, allowing organizations to observe their behavior and determine if they pose a threat.
- Reputation-based filtering utilizes threat intelligence data to identify and block known malicious websites, IPs, and domains, preventing users from accessing potentially harmful content.
By combining these proactive defense mechanisms with robust threat detection capabilities, organizations can establish a strong security posture for their endpoints, minimizing the risk of successful attacks and protecting sensitive data from compromise. Comprehensive threat protection for endpoints is an essential part of any modern cybersecurity strategy to ensure the resilience and continuity of business operations.
Advanced Detection and Response Capabilities
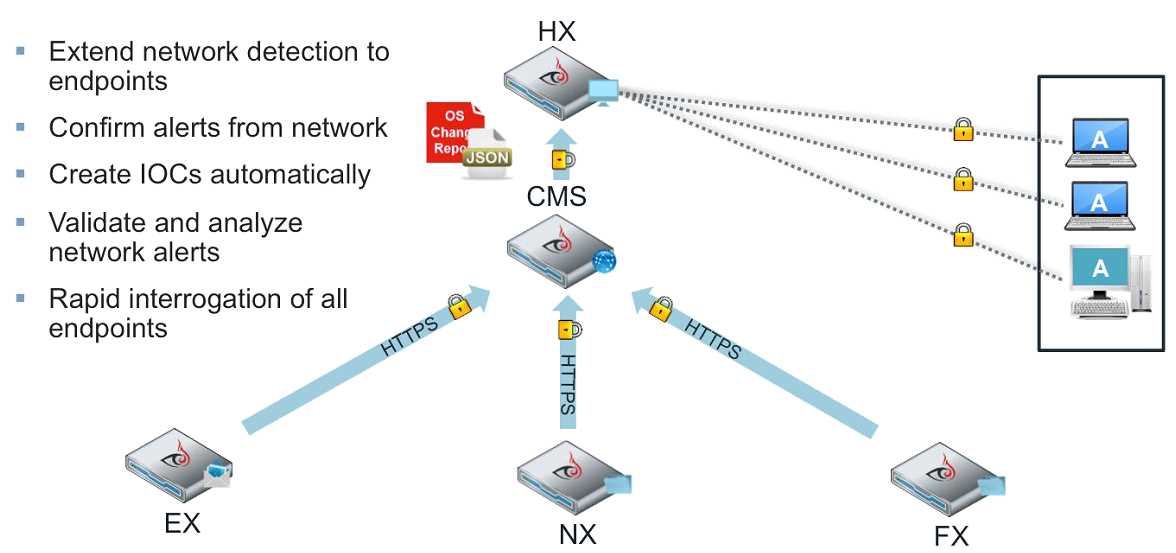
In this section, we will explore the advanced detection and response capabilities offered by the cutting-edge Fireeye endpoint security solution. By leveraging innovative technologies and a comprehensive approach, the solution provides unparalleled protection against emerging threats and enables proactive threat hunting.
Proactive Threat Hunting
- Employs sophisticated behavioral analysis to detect potential threats
- Uses machine learning algorithms to identify anomalous activities
- Leverages threat intelligence feeds for proactive threat hunting
Real-time Incident Response
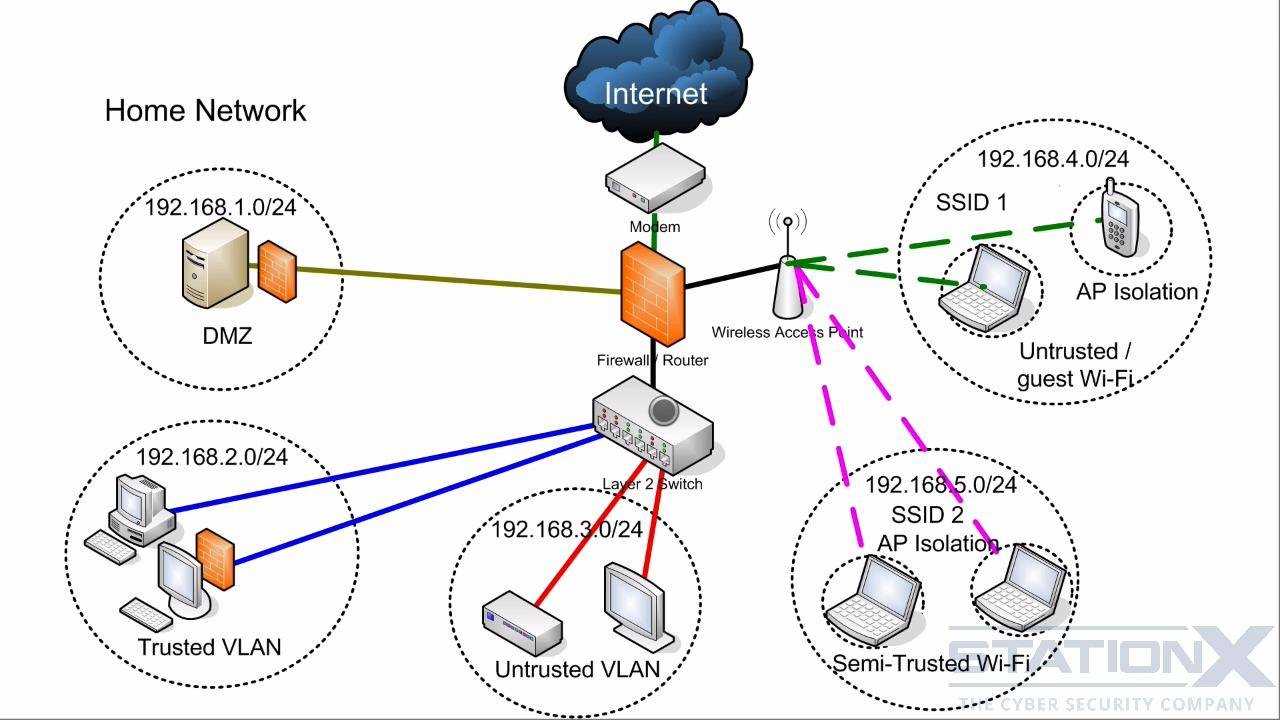
- Provides real-time visibility into endpoints and network events
- Offers automated incident response actions to mitigate risks
- Enables centralized incident management and collaboration
By combining these advanced detection and response capabilities, Fireeye endpoint security empowers organizations to stay one step ahead of sophisticated attacks. With its proactive threat hunting capabilities and real-time incident response, it ensures early detection, swift mitigation, and effective control over security incidents.
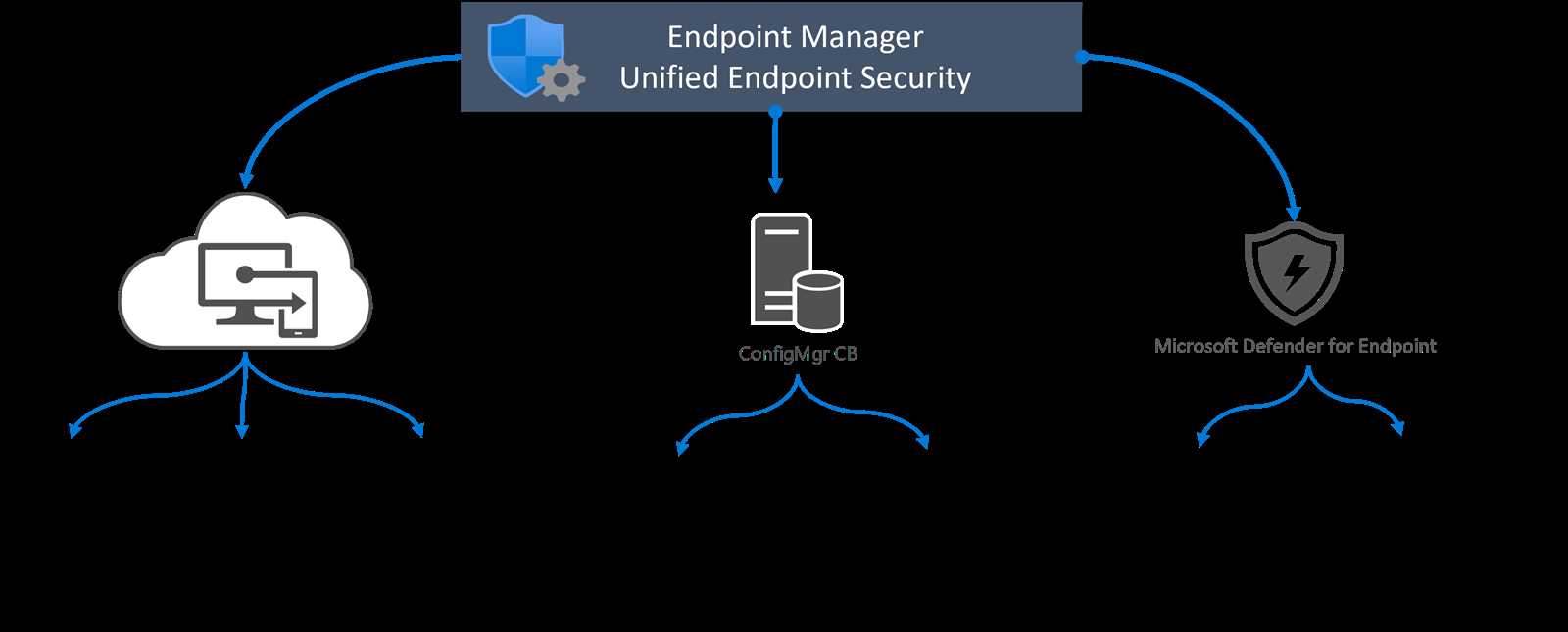
User-friendly Interface and Simplified Management
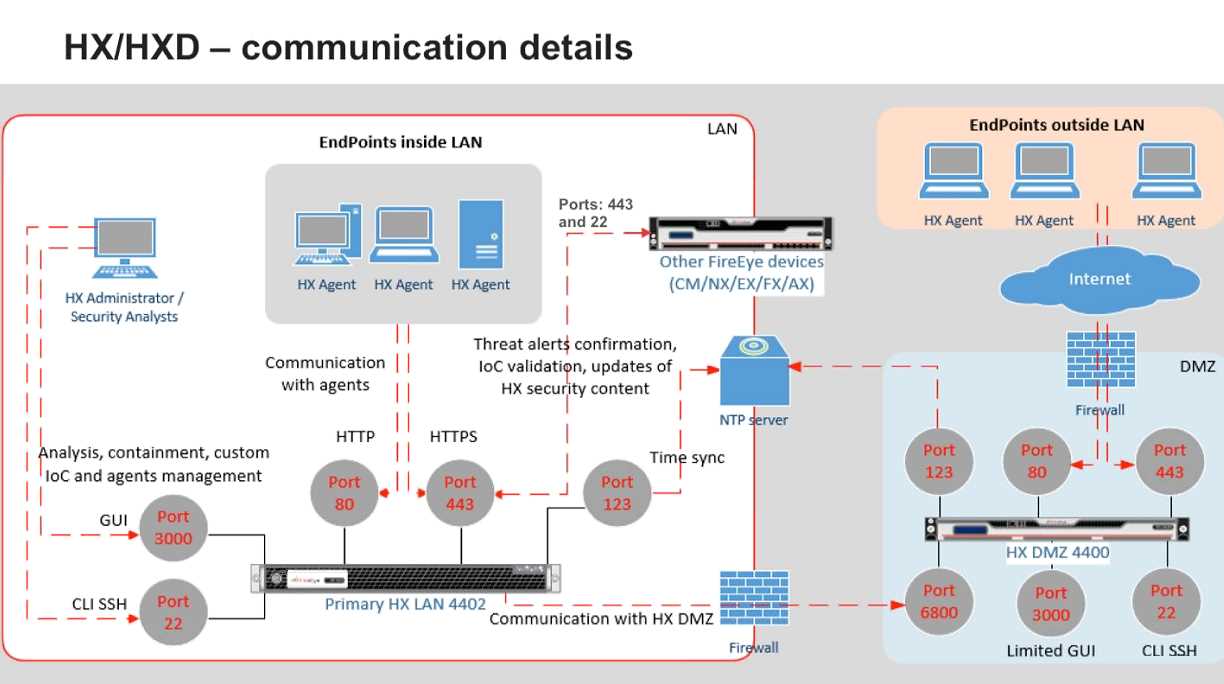
The User-friendly Interface and Simplified Management section of this article highlights the intuitive and efficient design of the Fireeye endpoint security software, allowing users to easily navigate and manage their security systems. The software’s interface is designed to provide a seamless and intuitive experience, ensuring that users can quickly access key features and settings without the need for extensive training or technical expertise. This streamlined and user-friendly approach simplifies the management process, enabling administrators to easily configure and monitor their security settings with ease.
In addition to its intuitive interface, the Fireeye endpoint security software offers a range of simplified management tools. These tools enable administrators to efficiently manage and customize their security settings, ensuring that their network is protected from potential threats. The software provides a centralized management console, allowing administrators to oversee all endpoints and make necessary adjustments from a single location. This centralized approach saves time and effort, as administrators can easily monitor and manage their security settings without having to navigate through multiple interfaces or systems.
| Key Features: |
| 1. Intuitive and user-friendly interface |
| 2. Simplified management tools |
| 3. Centralized management console |
| 4. Efficient configuration and monitoring |
The intuitive interface and simplified management tools of the Fireeye endpoint security software ensure that administrators can effectively protect their network without the need for extensive training or technical expertise. With its streamlined design and centralized management console, the software allows for efficient configuration and monitoring, enhancing overall security and reducing the risk of potential threats.