
In the realm of digital warfare, where the battleground is as intangible as the data flowing through networks, fortification is paramount. Enter F5, a stalwart guardian against the relentless onslaught of cyber threats. Within its arsenal lies a shield, a bulwark against the tumultuous tides of malicious intent.
Unveiling the Anatomy of Defense: Beneath the surface of F5’s armor lies a network of intricately woven algorithms and protocols, each thread contributing to the resilience of the whole. Through the symbiotic dance of hardware and software, F5 orchestrates a symphony of protection, safeguarding digital assets with unwavering dedication.
Empowering Defenders: Beyond the mere repulsion of adversaries, F5 bestows upon its guardians the tools to analyze, adapt, and overcome. It is not merely a shield but a wellspring of insight, offering clarity amidst the chaos and empowering defenders to anticipate and thwart the stratagems of their foes.
F5 DDoS Datasheet: Understanding Attack Vectors
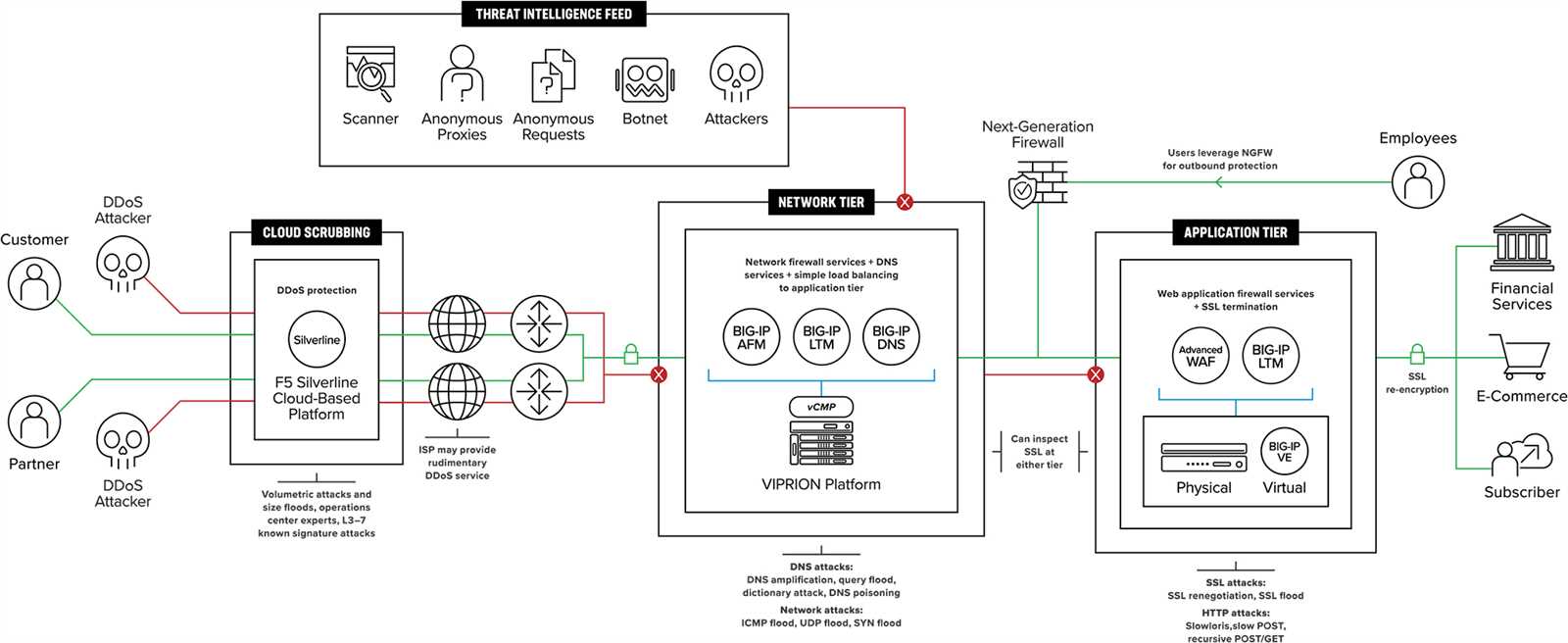
In the realm of cybersecurity, comprehending the diverse avenues through which malicious entities attempt to disrupt services and compromise systems is paramount. This section delves into the intricate landscape of attack vectors, exploring the myriad strategies employed by aggressors to undermine the integrity and availability of digital assets.
The Anatomy of Assault

Within the digital battlefield, adversaries employ a plethora of tactics to exploit vulnerabilities and launch assaults on networks and applications. Understanding the anatomy of such attacks entails discerning the multifaceted nature of infiltration attempts, ranging from volumetric onslaughts to sophisticated application-layer manipulations.
Exploring Ingress Points
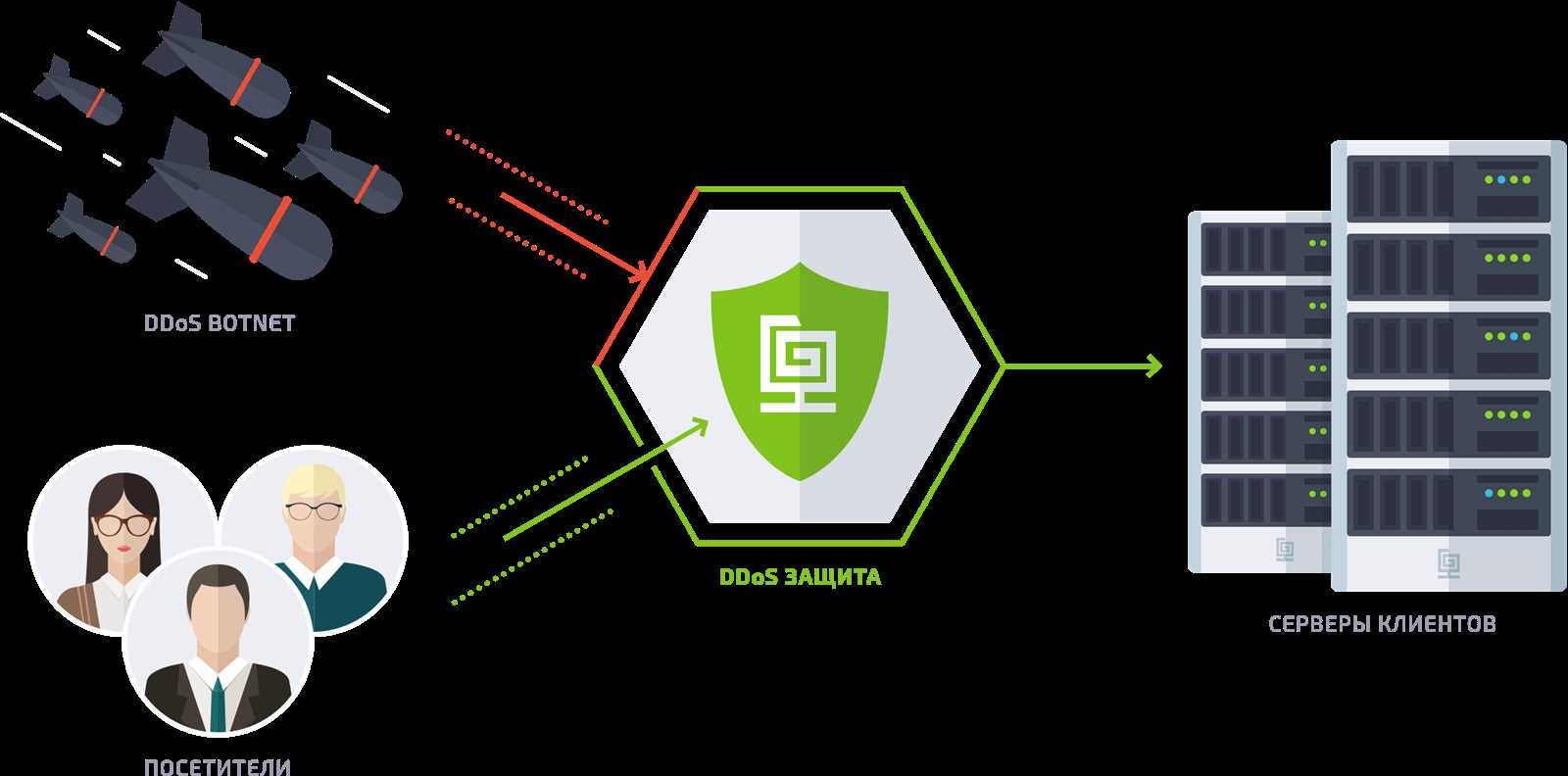
Examining the ingress points through which malevolent actors infiltrate systems illuminates the diverse avenues of exploitation. From leveraging protocol weaknesses to exploiting misconfigurations, each entry point represents a potential vulnerability ripe for exploitation. By dissecting these entryways, defenders can fortify their defenses and erect robust barriers against incursion.
- Protocol Vulnerabilities
- Misconfigurations
- Application Weaknesses
- Human Factor Exploitation
Explore the Various Denial-of-Service Techniques

Delve into the myriad strategies employed by malicious actors to disrupt, incapacitate, or render inaccessible online services and networks. This section sheds light on the diverse arsenal of methods utilized for such nefarious endeavors.
| Technique | Description |
|---|---|
| Flooding | Overwhelms target systems with an excessive volume of requests or traffic, effectively choking their bandwidth and resources. |
| Amplification | Exploits vulnerabilities in third-party systems to magnify the volume of attack traffic directed towards the target, maximizing its impact. |
| Spoofing | Falsifies the source addresses of packets to conceal the identity of the attacker and deceive the target into accepting malicious requests. |
| Application Layer Attacks | Targets vulnerabilities within specific applications or services, exploiting their weaknesses to disrupt or impair their functionality. |
| Botnets | Enlists a network of compromised devices or ‘bots’ to orchestrate coordinated attacks, amplifying their collective impact and resilience against mitigation efforts. |
Securing Your Network: F5 Cyber Onslaught Defense Solutions
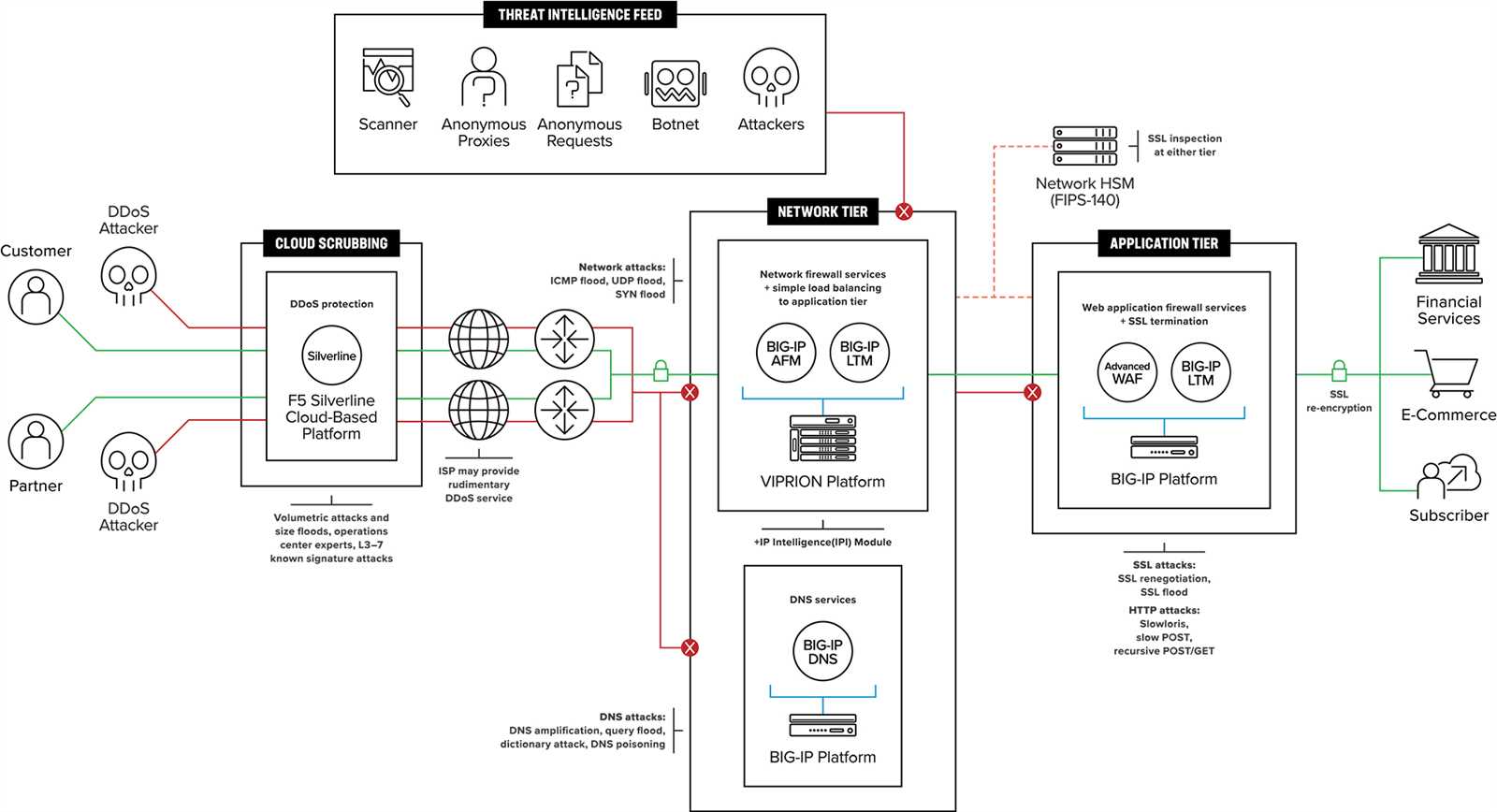
When safeguarding your network against the relentless barrage of cyber threats, it becomes imperative to fortify your defenses with robust solutions capable of thwarting malicious attacks. In this segment, we delve into the realm of safeguarding your network integrity through the formidable arsenal provided by F5’s Cyber Onslaught Defense Solutions.
Understanding the Threat Landscape
Before delving into the specifics of mitigation strategies, it’s crucial to comprehend the multifaceted nature of modern cyber threats. These nefarious entities come in various guises, ranging from volumetric assaults to sophisticated application-layer attacks, each posing a unique challenge to the stability and security of your network infrastructure.
Empowering Your Defenses
In the face of such diverse and evolving threats, F5 offers a suite of dynamic defense mechanisms designed to bolster your network’s resilience. Through a combination of proactive monitoring, adaptive traffic management, and intelligent threat detection, F5’s solutions stand as bastions against the tide of cyber incursions.
Fortifying Network Resilience
With F5’s Cyber Onslaught Defense Solutions, organizations can proactively fortify their networks against potential disruptions and data breaches. By seamlessly integrating robust security protocols with advanced traffic management capabilities, F5 empowers enterprises to maintain operational continuity even in the face of relentless cyber onslaughts.
Conclusion
In conclusion, safeguarding your network against the ever-looming specter of cyber threats necessitates a proactive and multifaceted approach. Through the deployment of F5’s Cyber Onslaught Defense Solutions, organizations can mitigate the risks posed by malicious actors, thereby safeguarding their digital assets and ensuring uninterrupted business operations.
Discover Effective Strategies for Safeguarding Against Cyber Attacks
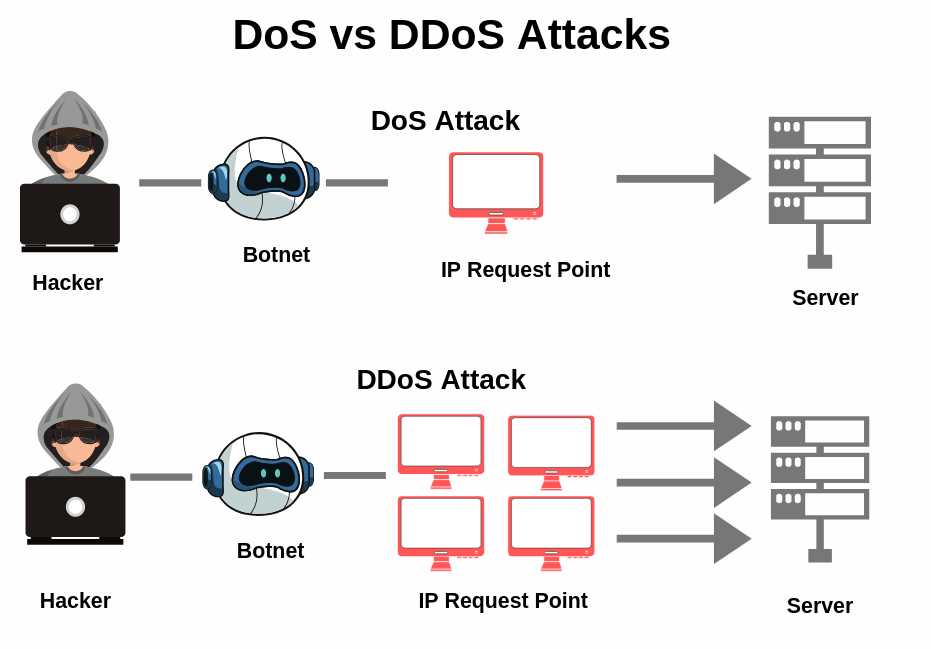
In today’s digital landscape, businesses face an ever-growing threat from malicious actors seeking to disrupt their online operations. Protecting your organization from such assaults requires a multifaceted approach that goes beyond mere reactionary measures. This section delves into proactive strategies aimed at fortifying your defenses against the myriad forms of cyber onslaughts.
| Strategy | Description |
|---|---|
| Network Segmentation | Divide your network into distinct segments to contain and mitigate the impact of potential intrusions. |
| Traffic Analysis | Employ sophisticated tools to scrutinize incoming and outgoing traffic patterns, enabling swift detection and response to anomalous behavior. |
| Redundancy | Establish redundant systems and failover mechanisms to ensure uninterrupted service availability in the face of disruptions. |
| Behavioral Analysis | Implement behavioral analysis techniques to discern normal user behavior from suspicious activities, thereby preempting potential threats. |
| Cloud-Based Protection | Utilize cloud-based security solutions to leverage vast computational resources and real-time threat intelligence for proactive defense. |
Enhancing F5 Performance and Scalability Against Cyber Attacks
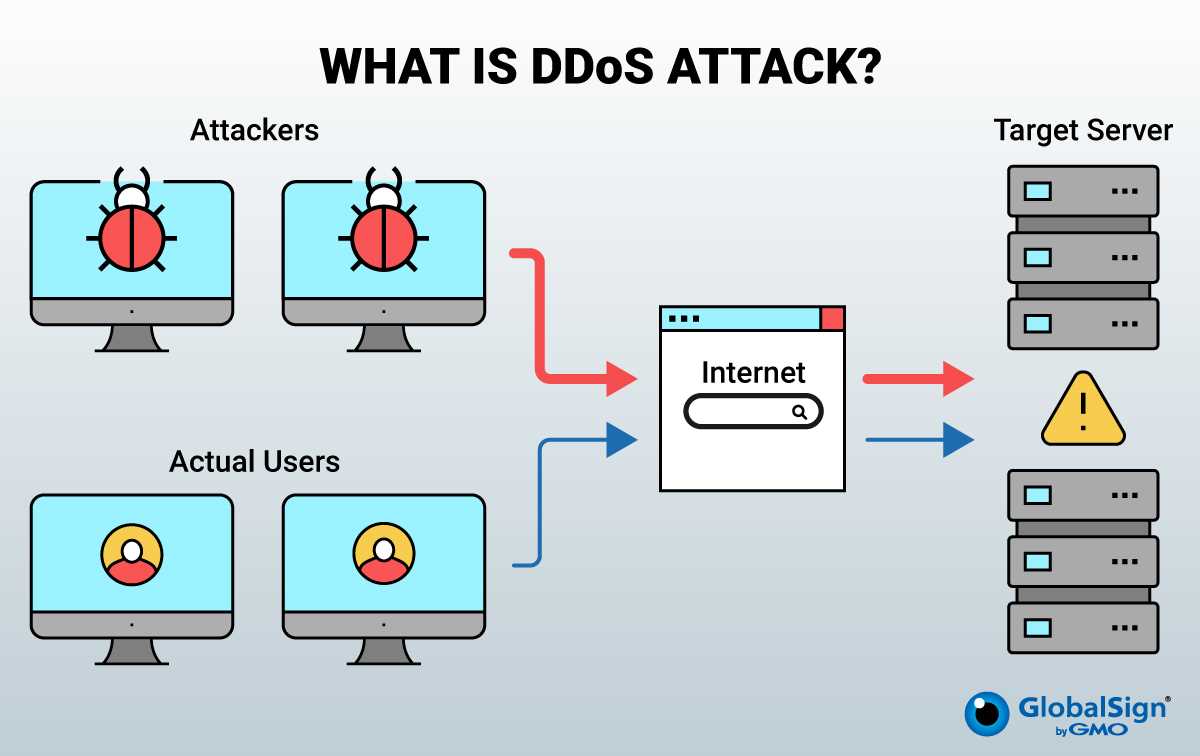
In this section, we delve into the robust capabilities of F5 technology in bolstering network resilience against malicious cyber assaults. By focusing on optimizing performance and scalability, F5 equips organizations with a formidable defense mechanism, ensuring seamless operation even under intense cyber threats.
Unrivaled Performance Optimization

One of the core strengths of F5 solutions lies in its ability to enhance network performance to unprecedented levels. Through meticulous optimization techniques and intelligent resource allocation, F5 empowers networks to operate efficiently, delivering superior throughput and minimizing latency. This optimization ensures smooth traffic flow, enabling organizations to maintain uninterrupted operations even amidst escalating cyber-attacks.
Scalability for Growing Demands
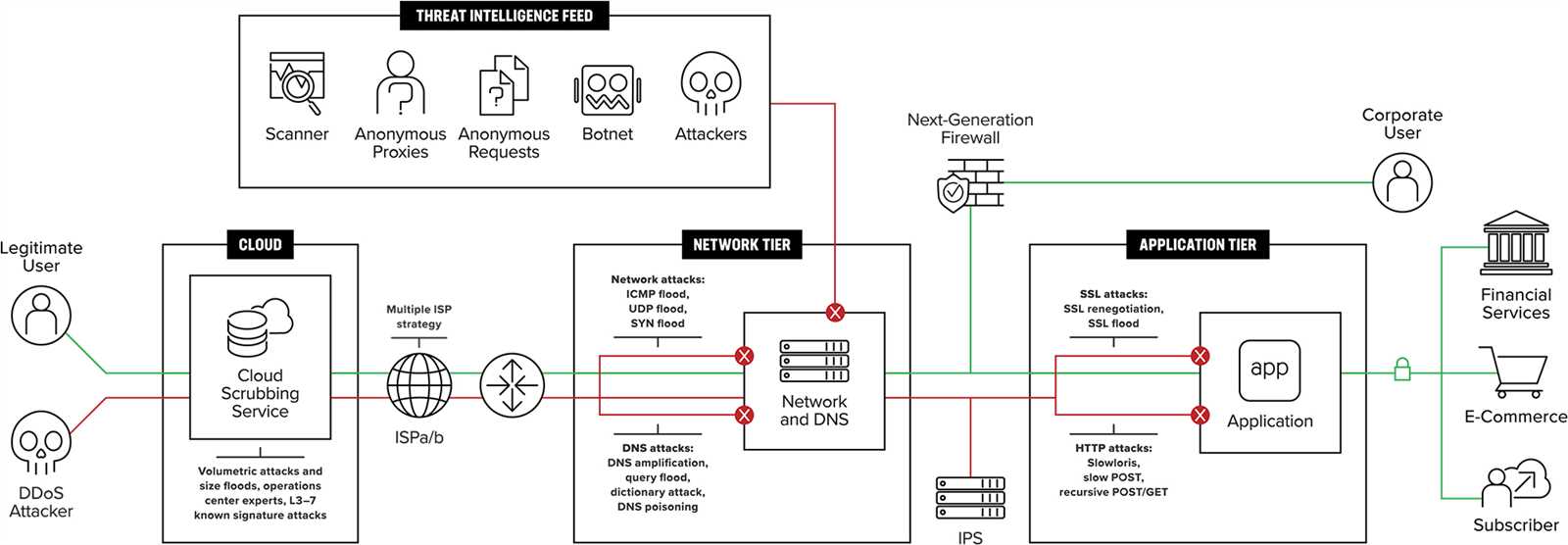
Scalability is paramount in the face of evolving cyber threats and expanding network requirements. F5’s scalable architecture allows seamless expansion to accommodate increasing traffic loads and growing infrastructure demands. With elastic scalability, organizations can adapt swiftly to fluctuating conditions, ensuring sustained performance and resilience against cyber adversaries.