
In the realm of wireless identification and tracking systems, there exists a ubiquitous protocol, quietly orchestrating seamless communication between tags and readers, shaping the landscape of access control, inventory management, and beyond. This protocol, a silent conductor in the symphony of connectivity, empowers myriad applications with its efficiency and reliability.
Unlocking Doors: Imagine a world where doors swing open at the mere approach of a card, granting access with a wave or a touch. This technology, concealed within unassuming plastic cards or key fobs, harnesses the power of radio waves to authenticate identities swiftly and securely. It’s a dance of signals, a choreography of encryption, ensuring that only those with the proper credentials can step through.
The Pulse of Inventory: Beyond entryways, this protocol pulses through the veins of warehouses and stockrooms, where inventory whispers its whereabouts without a single barcode scan. Each item, adorned with a tiny chip, speaks its identity in a language of radio frequencies, enabling swift inventory counts and real-time tracking with minimal human intervention.
Efficiency Redefined: In the ceaseless rhythm of modern commerce, efficiency reigns supreme. This protocol, with its elegant simplicity and universal compatibility, stands as a testament to progress, streamlining processes and enhancing security with every transmission. It’s not just a protocol; it’s the heartbeat of a connected world.
Understanding EM4100 Datasheet: Key Specifications and Features

In delving into the intricacies of the documentation pertaining to the EM4100 technology, we aim to decipher the fundamental elements encapsulated within its specifications and features. This exploration seeks to shed light on the core attributes that define the EM4100 system, elucidating its functionalities and capabilities for potential application in diverse contexts.
Core Specifications

At the heart of the EM4100 ecosystem lie pivotal specifications that govern its operation and performance. These foundational metrics delineate aspects such as communication protocols, frequency bands, and encoding mechanisms, forming the bedrock upon which the system functions.
Key Features

Beyond the realm of technical specifications, the EM4100 platform boasts an array of distinctive features that contribute to its versatility and efficacy. These encompass elements like robustness, compatibility with existing infrastructure, and adaptability to varying environmental conditions, rendering it a formidable solution across a spectrum of applications.
Exploring the Technical Specifications of RFID Tags

Delving into the intricacies of radio frequency identification (RFID) technology unveils a realm of fascinating technical specifications, elucidating the inner workings and capabilities of these ubiquitous tags. Within this exploration, we uncover the nuanced details governing the functionality and performance of RFID tags, shedding light on their operational principles and potential applications.
Operational Frequencies
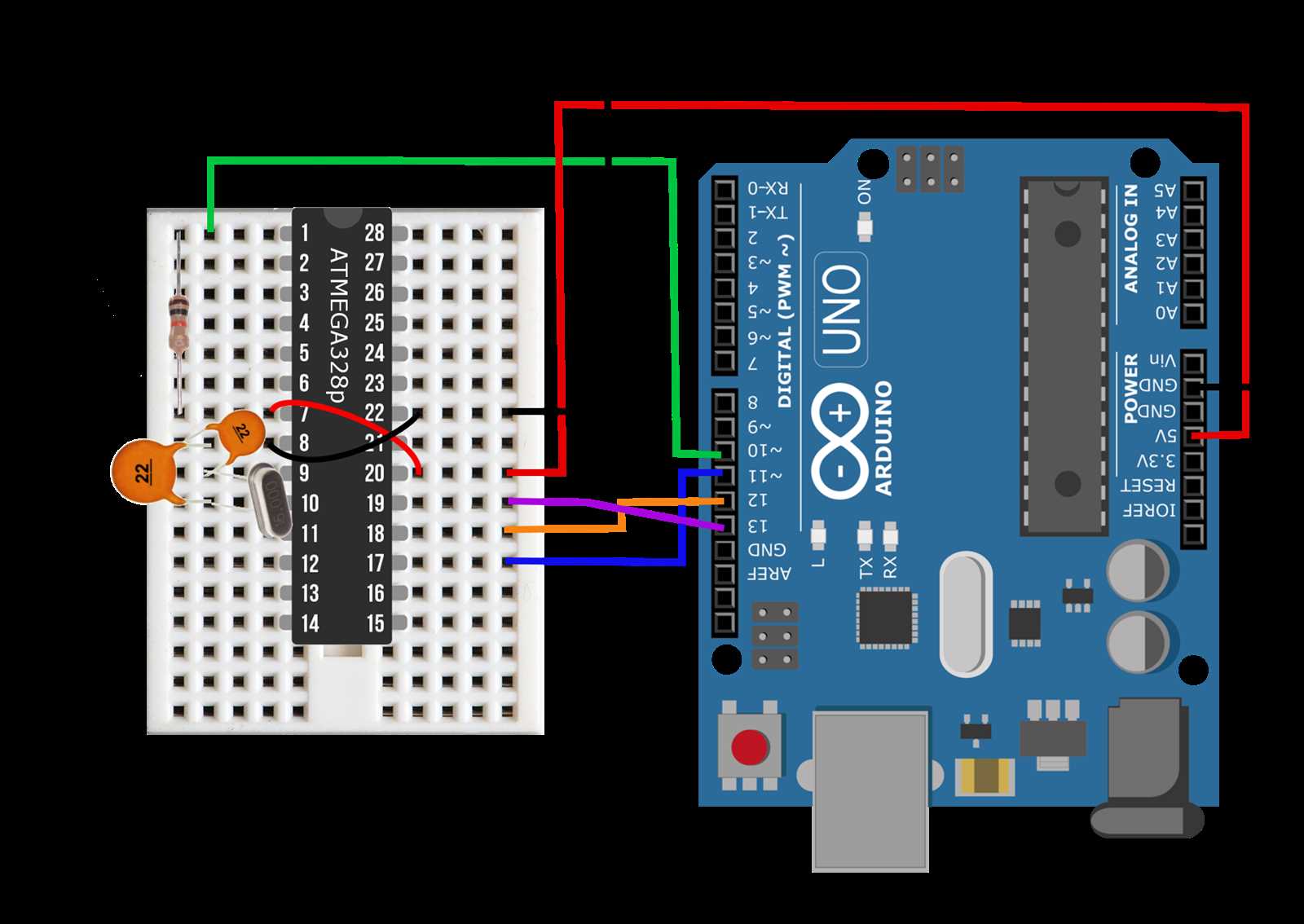
One of the fundamental aspects defining the functionality of RFID tags is their operational frequency range. These tags operate within specific frequency bands, facilitating communication with corresponding readers. Understanding the operational frequencies of RFID tags delineates their compatibility with diverse systems and environments, enabling seamless integration into various applications.
Data Encoding Schemes
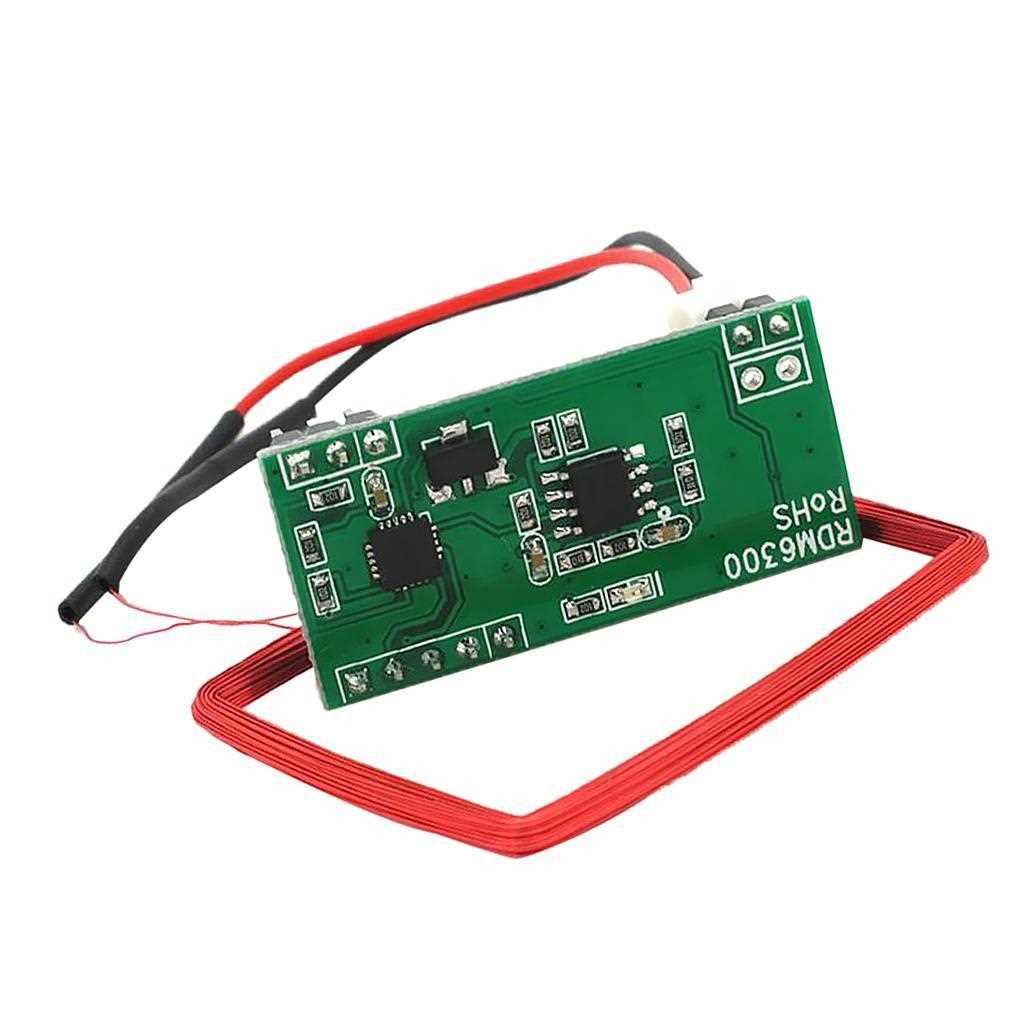
At the core of RFID technology lies the encoding of data onto the tags, encapsulating information essential for identification and tracking purposes. Different RFID systems employ distinct data encoding schemes, ranging from simple modulation techniques to sophisticated encryption algorithms. Examining these encoding schemes illuminates the methods by which data is transmitted, ensuring secure and reliable communication between tags and readers.
- Modulation Techniques
- Encryption Algorithms
- Data Integrity Protocols
Through a comprehensive analysis of these technical specifications, a deeper comprehension of RFID tags emerges, unveiling their diverse capabilities and potential applications across industries.
Unlocking the Potential: Applications of RFID Technology in Access Control Systems

In the realm of modern access control systems, leveraging advanced technology has become paramount. Exploring the capabilities of RFID (Radio-Frequency Identification) technology offers a myriad of solutions for enhancing security and streamlining access protocols. This section delves into the diverse applications of RFID technology, illuminating its transformative role in access control.
Enhanced Security Protocols
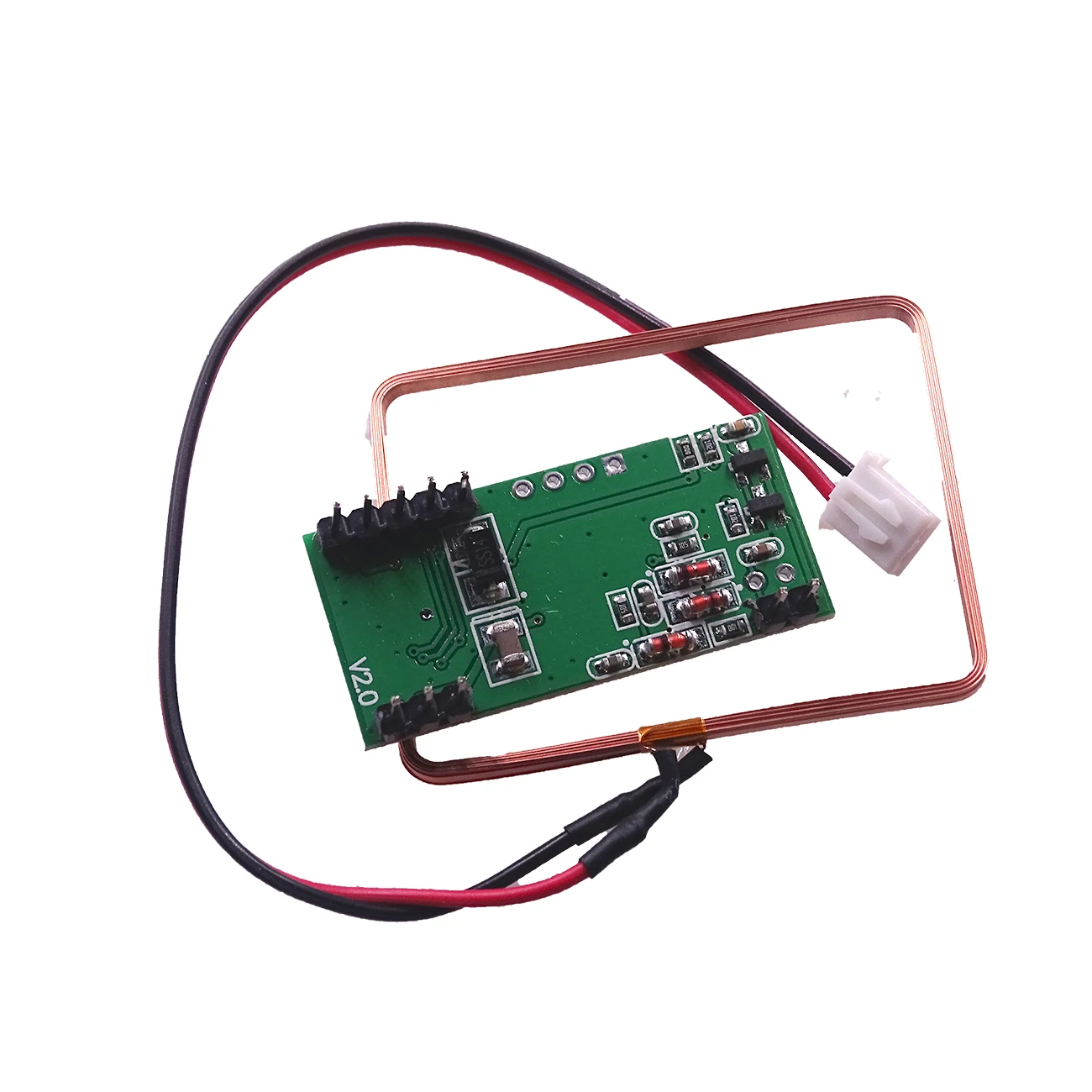
- Facilitating Secure Entry: RFID technology enables the implementation of secure access protocols, ensuring that only authorized individuals gain entry to restricted areas.
- Dynamic Authentication: With RFID-enabled access control systems, authentication processes can be dynamically adjusted, offering heightened security measures against unauthorized access attempts.
- Efficient Monitoring: The utilization of RFID tags allows for real-time monitoring of entry and exit points, enabling prompt response to any security breaches.
Streamlined Access Management

- Customized Access Levels: RFID technology empowers administrators to customize access levels based on individual roles and responsibilities, ensuring optimal operational efficiency.
- Seamless Integration: Integrating RFID technology into existing access control systems streamlines the management process, minimizing disruptions and enhancing overall system functionality.
- Scalable Solutions: The versatility of RFID technology facilitates scalable solutions, accommodating the evolving needs of access control systems in various environments.
Embracing the potential of RFID technology unlocks a new realm of possibilities in access control systems, offering enhanced security, streamlined management, and adaptability to meet the demands of modern environments.
Optimizing Performance: Strategies for Leveraging Technical Documentation in RFID Projects
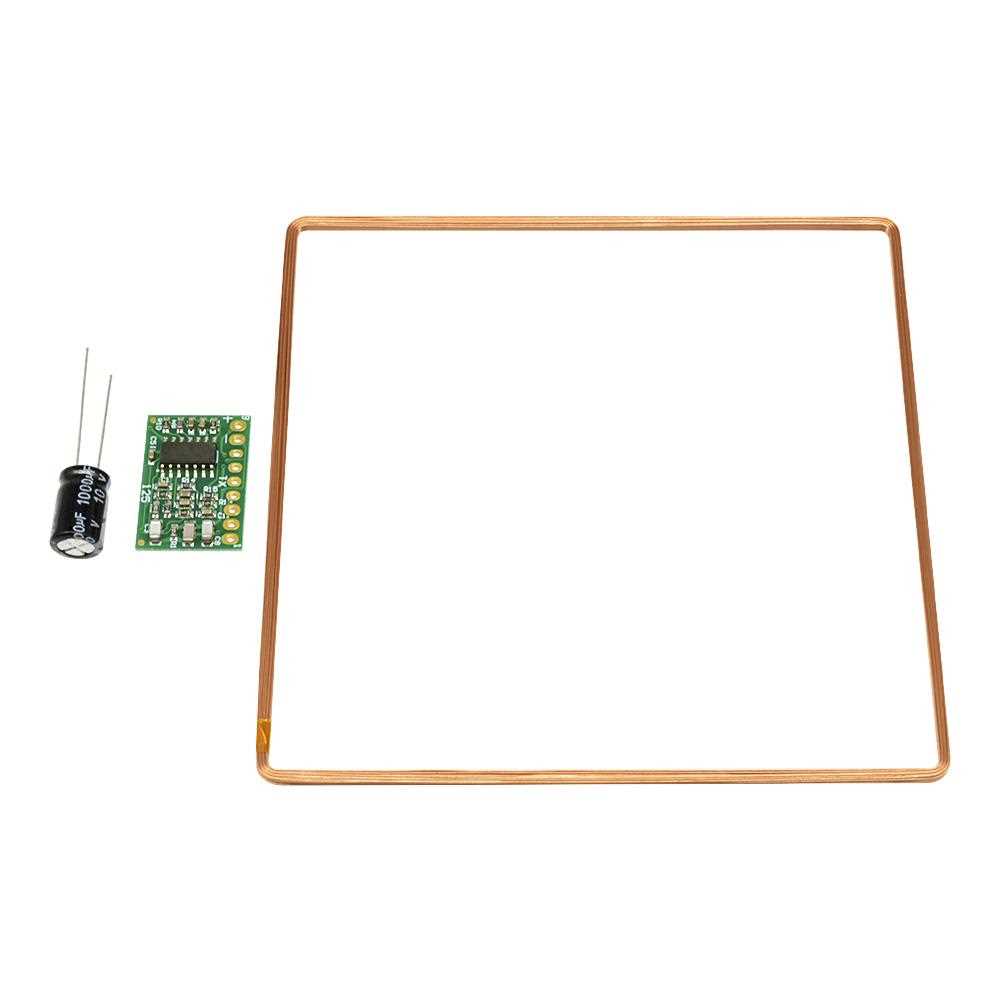
Unlocking the full potential of RFID technology requires a nuanced understanding of the technical specifications and guidelines provided in the documentation. By delving into the intricacies of RFID protocols and system requirements, project teams can enhance the efficiency and reliability of their implementations.
One key aspect to consider is the fine-tuning of parameters to align with specific project objectives. By scrutinizing the technical nuances outlined in the documentation, developers can tailor settings to optimize performance in diverse environments and applications.
Furthermore, leveraging the insights provided within the technical documentation enables practitioners to troubleshoot potential issues effectively. By interpreting the recommended practices and troubleshooting guidelines, project teams can preemptively address challenges and streamline deployment processes.
In addition to technical optimization, integrating innovative approaches based on the principles elucidated in the documentation can yield remarkable results. Embracing novel methodologies and adapting them to suit project requirements empowers teams to push the boundaries of RFID technology and unlock new possibilities.
Ultimately, the effective utilization of technical documentation serves as a cornerstone for success in RFID projects. By embracing a comprehensive understanding of the principles and guidelines outlined, project teams can elevate performance, enhance reliability, and unlock the full potential of RFID technology.