
Embark on a journey through the realm of digital data management, where the convergence of technology and innovation reshapes the landscape of information storage. Explore the essence of streamlined efficiency and heightened security in the realm of digital repositories.
Delve into the intricacies of contemporary data architecture, where every bit and byte finds its sanctuary amidst the dynamic currents of cyberspace. Discover the essence of resilience and scalability in the labyrinth of information infrastructure.
Engage with the avant-garde constructs of data sanctuaries, where the ethos of accessibility converges with the bastions of reliability. Unravel the tapestry of technological prowess woven within the fabric of digital fortresses.
The Benefits of Dell’s Data Management Solution
Within the realm of modern data management solutions, there exists a powerful tool that offers unparalleled advantages. This solution stands as a cornerstone of efficient data handling, providing a myriad of benefits to organizations across various sectors.
| Enhanced Efficiency | Streamlining processes and optimizing workflow |
| Cost-Effectiveness | Maximizing resource utilization while minimizing expenses |
| Scalability | Adapting seamlessly to evolving data demands |
| Reliability | Ensuring data integrity and consistency |
| Security | Implementing robust measures to safeguard sensitive information |
These advantages collectively contribute to a cohesive data management strategy, empowering businesses to thrive in an increasingly data-centric landscape.
Exploring the Efficiency and Performance

In this section, we delve into the efficacy and speed of operations when utilizing the specified technology. We investigate the system’s ability to optimize processes and its overall effectiveness in handling tasks efficiently. Furthermore, we assess its performance in terms of throughput and responsiveness, examining how swiftly it executes operations and responds to user inputs.
Efficacy Assessment
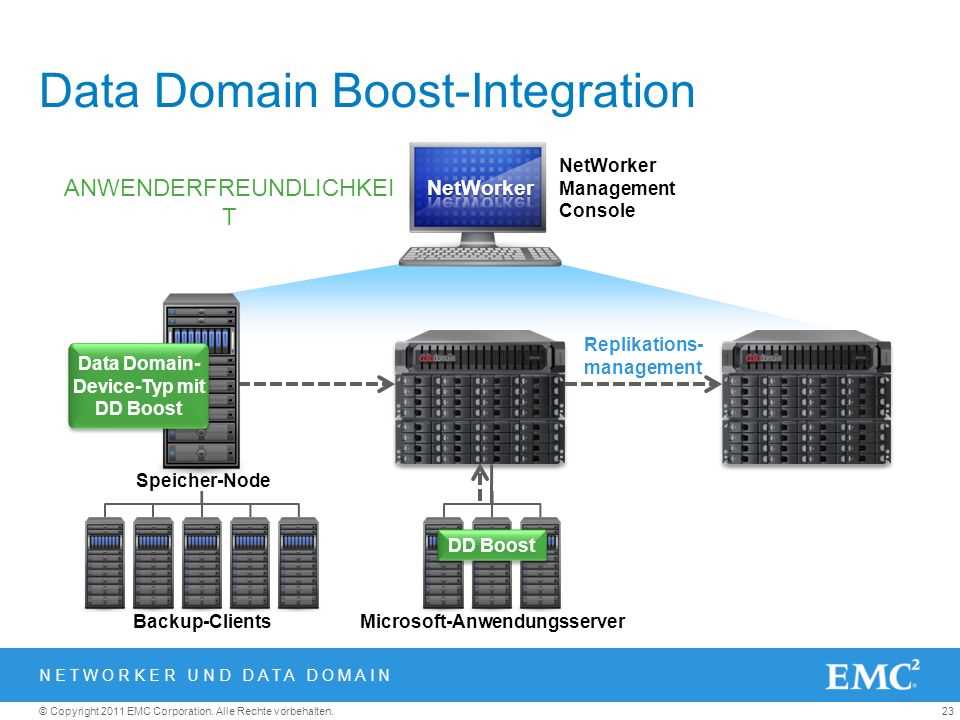
The efficacy evaluation focuses on the system’s capability to accomplish tasks effectively, ensuring seamless workflow and minimal resource wastage. We scrutinize its efficiency in resource utilization, assessing how adeptly it manages available resources to complete operations.
Performance Analysis

Performance analysis involves a comprehensive examination of the system’s speed and responsiveness under various workloads. We gauge its ability to handle concurrent processes without degradation in performance, evaluating its throughput and latency in processing tasks.
| Aspect | Criteria | Measurement |
|---|---|---|
| Efficiency | Resource Utilization | Percentage of resources effectively utilized |
| Workflow Optimization | Time taken to complete specified tasks | |
| Performance | Throughput | Number of operations completed per unit time |
| Responsiveness | Time taken to respond to user inputs |
Cost-effectiveness and Scalability
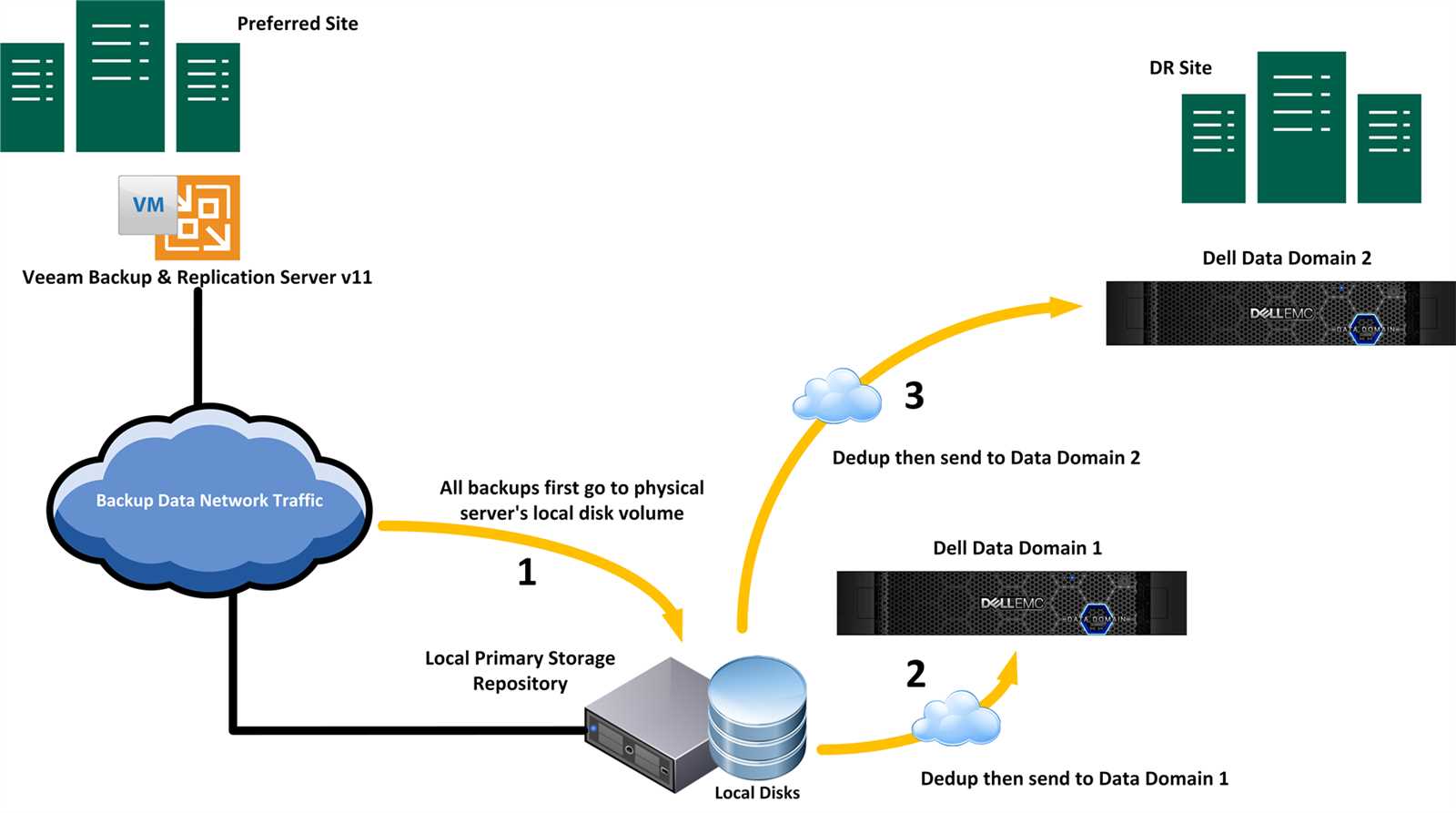
In the realm of financial prudence and expansive adaptability, the synergistic interplay between cost-effectiveness and scalability stands as a cornerstone. This section delves into the intricate dynamics of economic efficiency and the capacity for seamless expansion, essential components that underpin the robustness of the discussed solution.
Optimal Resource Allocation
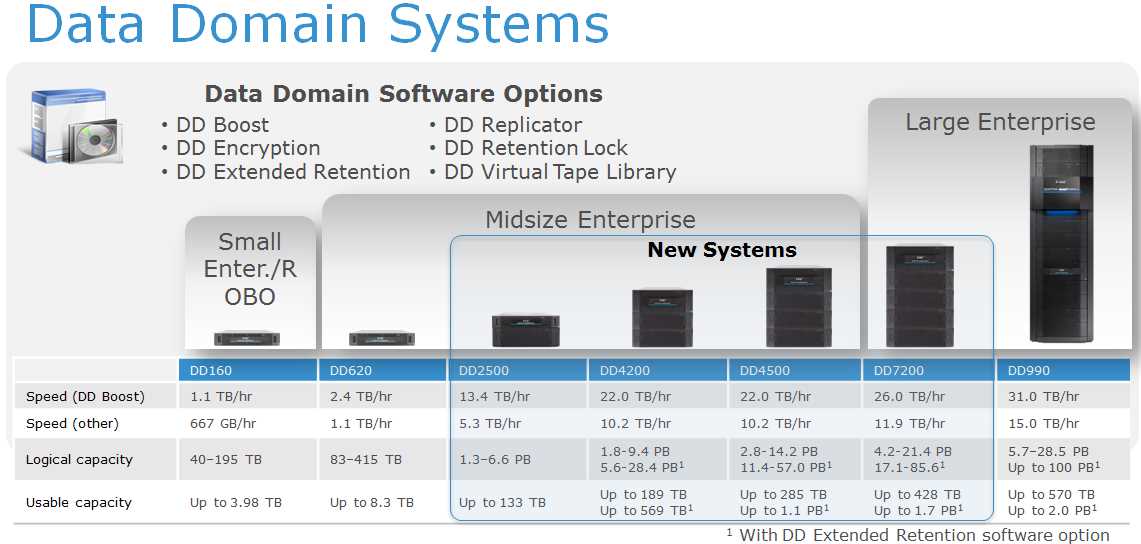
A critical facet of the solution’s economic viability resides in its adeptness at resource allocation. By optimizing resource utilization and minimizing unnecessary expenditures, the solution ensures a judicious distribution of funds, thereby maximizing cost-effectiveness.
Seamless Expansion Pathways

Scalability serves as the bedrock for future growth and development. The solution’s innate scalability facilitates a seamless transition towards accommodating evolving needs and burgeoning demands, without encountering impediments or disruptions.
| Aspect | Benefits |
|---|---|
| Cost-effectiveness | Optimized resource allocation Minimized expenditure |
| Scalability | Facilitates seamless expansion Accommodates evolving needs |
Security Features of Cutting-Edge Data Storage Solution
In today’s interconnected digital landscape, safeguarding sensitive information is paramount. This section explores the robust security measures embedded within this advanced data storage solution, ensuring the integrity and confidentiality of your valuable data.
Encryption Capabilities

- Advanced encryption protocols fortify data against unauthorized access, employing cutting-edge algorithms to secure information both at rest and in transit.
- Granular encryption options allow for tailored protection, ensuring that data remains shielded from compromise, even in diverse operational environments.
Access Control Mechanisms
- Role-based access control empowers administrators to define and enforce access privileges, limiting data exposure to authorized personnel only.
- Multi-factor authentication enhances security by requiring multiple forms of verification, mitigating the risk of unauthorized entry into critical systems.
- Immutable audit logs provide comprehensive visibility into access attempts, enabling proactive monitoring and swift response to potential security threats.
These security features collectively establish a robust defense posture, ensuring the confidentiality, integrity, and availability of your organization’s vital data assets.
Ensuring Data Integrity and Confidentiality

In the realm of information security, safeguarding the authenticity and secrecy of vital information stands paramount. This section delves into the mechanisms employed to uphold the trustworthiness and privacy of sensitive data, employing a fusion of robust protocols and cutting-edge encryption techniques.
Preserving Data Authenticity

Verifying the Integrity: Guaranteeing the accuracy and genuineness of data is fundamental in preserving its reliability. Through sophisticated algorithms and cryptographic hashes, the integrity of information is meticulously verified, ensuring that it remains unaltered throughout its lifecycle.
Securing Data Confidentiality

Implementing Encryption: To shield sensitive data from prying eyes and unauthorized access, advanced encryption methodologies are deployed. By transforming plaintext into indecipherable ciphertext, confidential information is shielded from interception, maintaining its secrecy even in the face of potential breaches.
Through a fusion of stringent integrity checks and robust encryption protocols, the sanctity and secrecy of critical data are upheld, fostering an environment of trust and confidentiality.