
In the realm of technological infrastructure, there exists a treasure trove of comprehensive documents that serve as blueprints for diverse networking solutions. These invaluable resources encapsulate the essence of connectivity, elucidating the functionalities, specifications, and configurations of various hardware offerings.
Delving into the intricacies of these documents unveils a world of innovation and efficiency, where each specification is a building block in the edifice of connectivity. Through meticulous detailing and structured organization, these documents become indispensable companions for network administrators, guiding them through the labyrinth of hardware choices and configurations.
Embarking on a journey through the specifications of network appliances, one uncovers the intricate dance of data transfer protocols, security features, and performance benchmarks. As the digital landscape evolves, so too do these documents, adapting to incorporate new technologies and address emerging challenges.
Exploring the RV345P Overview: Essential Features and Technical Specifications

In this segment, we delve into the fundamental aspects and intricate details encapsulated within the RV345P documentation. Unveiling the core functionalities and intricacies, we embark on a journey to comprehend the essence of this networking apparatus.
Key Features:
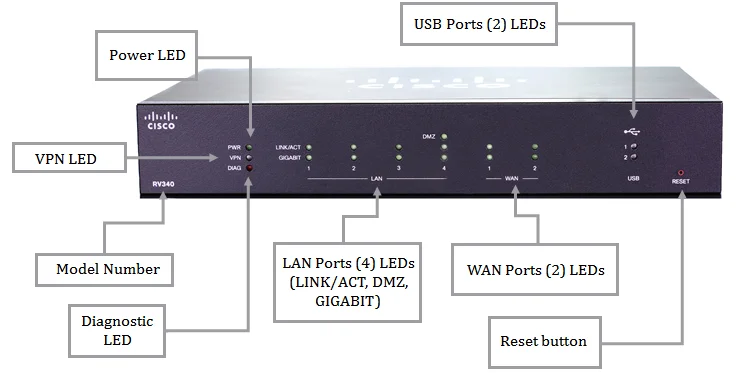
- Core Capabilities: Unveiling the backbone functionalities driving operational excellence.
- Enhanced Security Protocols: Fortifying networks with robust protective measures.
- Efficient Performance: Optimizing throughput and responsiveness for seamless operations.
- Scalability Options: Tailoring solutions to accommodate varying network demands.
Technical Specifications:

- Hardware Specifications: Delving into the hardware intricacies and capabilities.
- Connectivity Interfaces: Unveiling the diverse array of connectivity options available.
- Network Protocol Support: Exploring the supported protocols for seamless integration.
- Dimensions and Weight: Understanding the physical attributes for deployment considerations.
Exploring the Hardware and Connectivity Options

In this section, we delve into the intricate ecosystem of components and the network interconnections that form the backbone of the system. We embark on a journey to understand the physical elements and the diverse avenues for establishing and maintaining connectivity, facilitating seamless communication and data transmission.
Hardware Components

- System Infrastructure
- Peripheral Devices
- Processing Units
- Storage Solutions
Connectivity Options

- Wired Connections
- Wireless Networks
- Remote Access Protocols
- Internet Service Providers
Exploration of the hardware intricacies and connectivity avenues opens doors to comprehend the intricate web of technological possibilities and functionalities.
Unlocking Performance: Understanding RV345P Data Transfer Capabilities

In the realm of network infrastructure, the potential for optimizing data flow is paramount. This section delves into the intricacies of enhancing performance within the RV345P framework, exploring its capacity for efficient data transfer without compromise.
The Dynamics of Data Velocity

Efficiency in data transmission is the cornerstone of modern networking solutions. Unveiling the mechanisms behind data velocity within the RV345P ecosystem sheds light on its capability to seamlessly handle diverse data loads.
Streamlining Transfer Protocols

Optimization lies in the refinement of transfer protocols, ensuring a harmonious exchange of information across networks. By dissecting the protocols employed by the RV345P, we uncover avenues for enhancing transfer efficiency, bolstering overall performance.
Comparing Speed, Throughput, and VPN Performance

In this section, we delve into a comprehensive analysis of the velocity, data transfer capacity, and virtual private network (VPN) efficacy of the device under scrutiny. Understanding these pivotal aspects illuminates the device’s operational capabilities, facilitating informed decision-making for potential adopters.
Velocity Assessment

Velocity, a fundamental metric in networking, pertains to the rate at which data traverses the network infrastructure. It encapsulates the device’s ability to swiftly transmit and receive data packets, thereby influencing the overall efficiency of network operations. Our evaluation scrutinizes the velocity benchmarks of the examined hardware, shedding light on its real-world performance.
Throughput Analysis

Throughput, often misconstrued with velocity, delves deeper into the actual data handling capacity of the networking equipment. It encompasses factors such as bandwidth utilization, packet loss mitigation, and overall network congestion management. Our analysis dissects the throughput capabilities of the device, offering insights into its robustness in handling varying loads and network conditions.
- Bandwidth utilization assessment
- Packet loss mitigation strategies
- Network congestion management techniques
Together, these metrics furnish a comprehensive understanding of the device’s throughput prowess, guiding stakeholders in assessing its suitability for diverse networking scenarios.
Stay tuned as we delve further into the intricacies of speed, throughput, and VPN performance, unraveling the nuanced facets of network device evaluation.
Security Matters: Analyzing RV345P Firewall and Threat Protection

Ensuring the safety of your network infrastructure goes beyond mere hardware specifications. In this segment, we delve into the robust security features embedded within the RV345P, exploring its capabilities in thwarting various cyber threats and fortifying your digital assets against unauthorized access and malicious activities.
Firewall Integrity: Delving into the core of network security, we scrutinize the firewall mechanisms employed by the RV345P, dissecting its ability to regulate incoming and outgoing traffic, detect anomalies, and enforce access policies without compromising network performance.
Threat Detection: Amidst the ever-evolving landscape of cyber threats, the RV345P stands sentinel, equipped with advanced threat detection mechanisms. We uncover how this device identifies and mitigates potential risks, from malware infiltration to intrusion attempts, bolstering your network’s resilience against emerging threats.
Policy Enforcement: Upholding security protocols is paramount in safeguarding sensitive data and maintaining regulatory compliance. Here, we explore how the RV345P empowers administrators with granular control over access permissions and network policies, ensuring adherence to organizational security standards.
Encryption Protocols: Securing data in transit is imperative for preserving confidentiality and integrity. Within this segment, we analyze the encryption protocols supported by the RV345P, evaluating their efficacy in safeguarding data transmissions against eavesdropping and interception.
Continuous Monitoring: Vigilance is key to preempting potential security breaches. We examine the RV345P’s monitoring capabilities, assessing its capacity to provide real-time insights into network activities, detect anomalies, and prompt proactive responses to mitigate security risks.
In conclusion, our analysis underscores the pivotal role of the RV345P in fortifying your network infrastructure against evolving cyber threats. By harnessing its robust security features, organizations can instill confidence in their digital operations and safeguard their assets with unwavering vigilance.