Delving into the intricate framework of network management solutions, we venture into the realm of technological prowess, where innovation thrives and efficiency reigns supreme. In this exploration, we navigate through the blueprint of a remarkable toolset, uncovering its capabilities and unraveling its potential impact. As we embark on this journey, expect to encounter a treasure trove of functionalities designed to streamline operations, fortify security protocols, and empower organizations in their digital endeavors.
Prepare to be immersed in a narrative that transcends mere specifications, offering a glimpse into the transformative power of intelligent systems.
Cisco ISE 3515 Datasheet Overview

In this section, we delve into an insightful exploration of the intricate specifications and features encapsulated within the comprehensive documentation for the Cisco ISE 3515. By navigating through this detailed dossier, users can gain a profound understanding of the functionalities, capabilities, and technical attributes intrinsic to this innovative solution.
- An In-Depth Examination of Key Specifications
- Performance Metrics and Benchmarks
- Robust Security Protocols and Mechanisms
- Scalability and Integration Possibilities
- User-Friendly Interface and Accessibility Enhancements
- Deployment Flexibility and Configuration Options
- Advanced Analytics and Reporting Features
- Regulatory Compliance Standards and Certifications
Embark on a journey through the intricate tapestry of technical details and operational insights meticulously outlined within the Cisco ISE 3515 datasheet. From performance benchmarks to security protocols, this overview unveils the multifaceted capabilities of this cutting-edge solution, empowering users with the knowledge to make informed decisions and leverage its full potential in diverse operational scenarios.
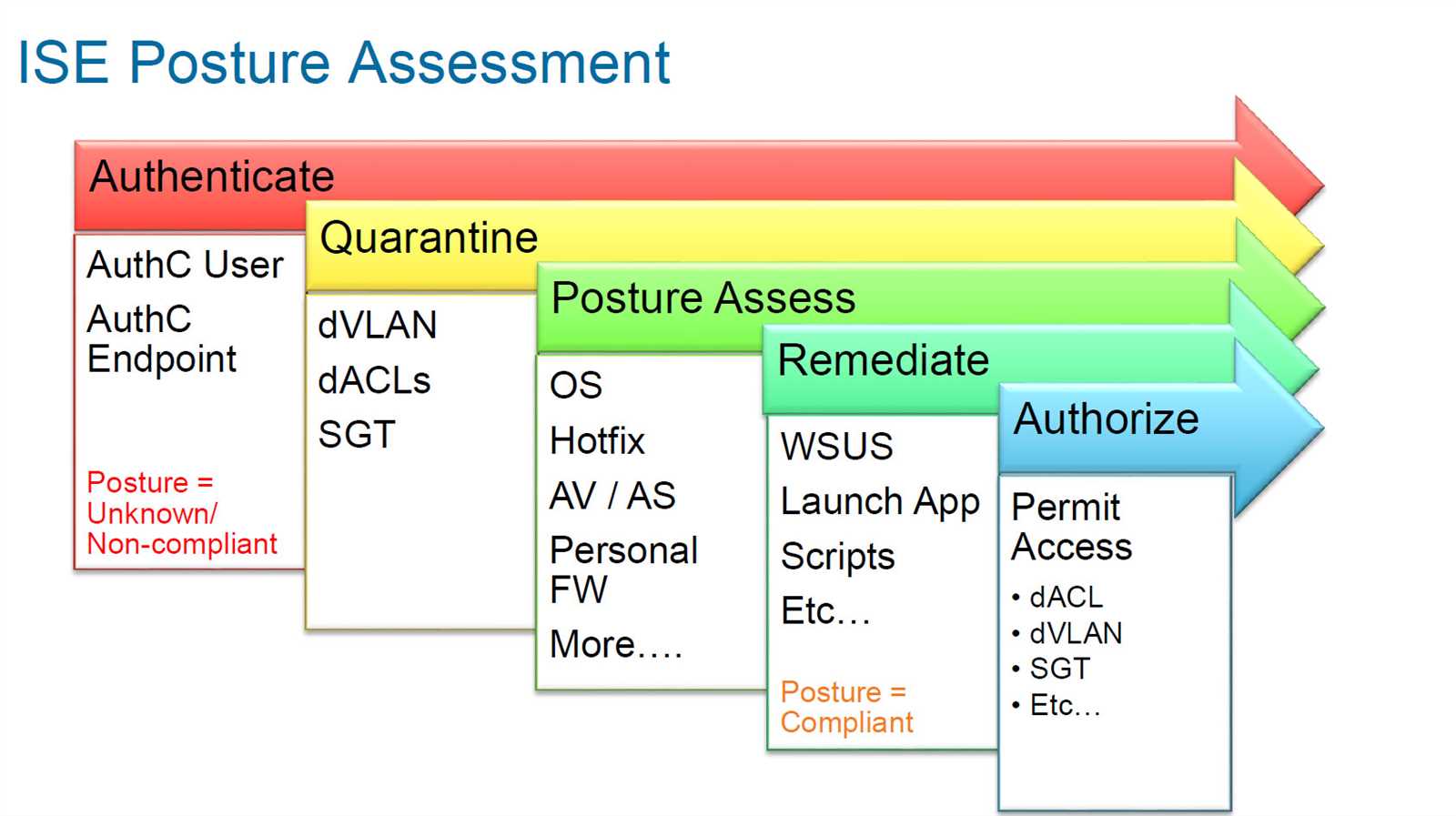
Exploring Key Features and Specifications

Delve into the intricate details and essential characteristics that define this cutting-edge technological solution. Uncover the core functionalities and distinctive attributes that set this system apart in the realm of network security and management.
Main Features
Discover the primary elements that form the backbone of this innovative platform, showcasing its prowess in facilitating seamless operations and robust security protocols. From fundamental functionalities to advanced capabilities, explore the diverse aspects that contribute to its efficiency and reliability.
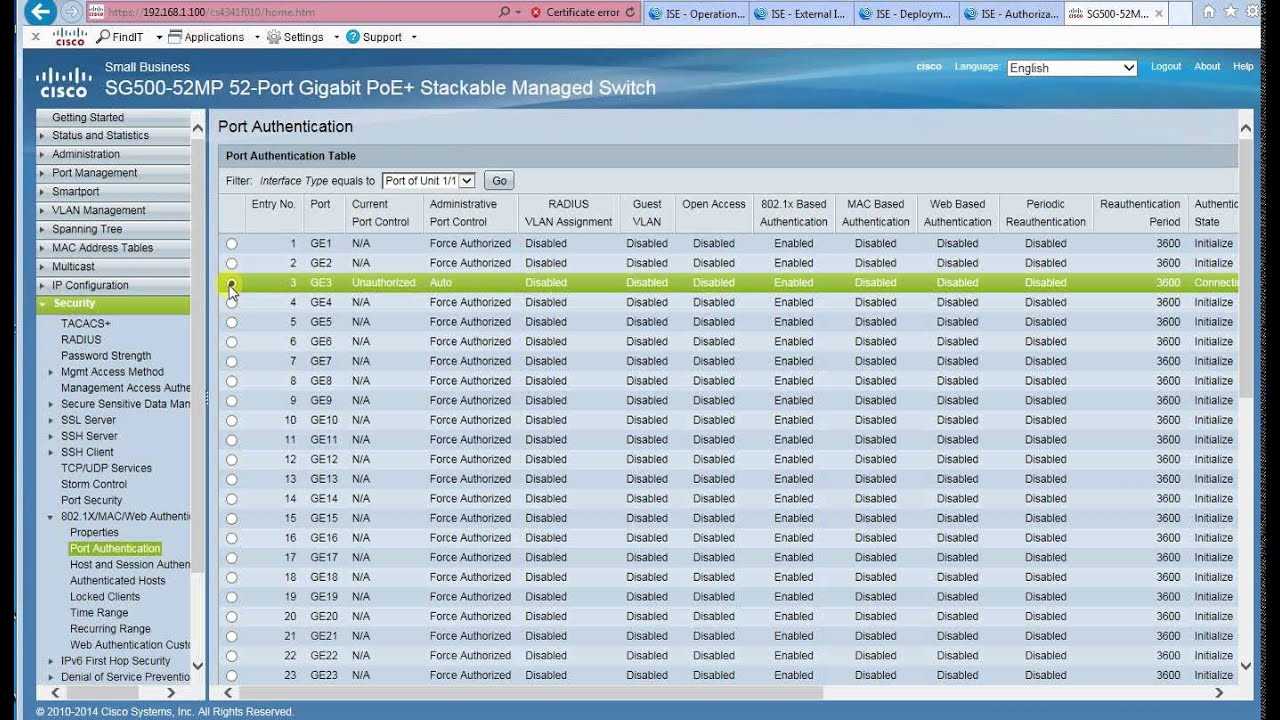
Technical Specifications
Explore the technical blueprint of this sophisticated system, encompassing a comprehensive overview of its hardware and software components. Dive into the intricacies of its architecture, performance metrics, and compatibility factors, unveiling the intricate framework that powers its exceptional functionality and performance.
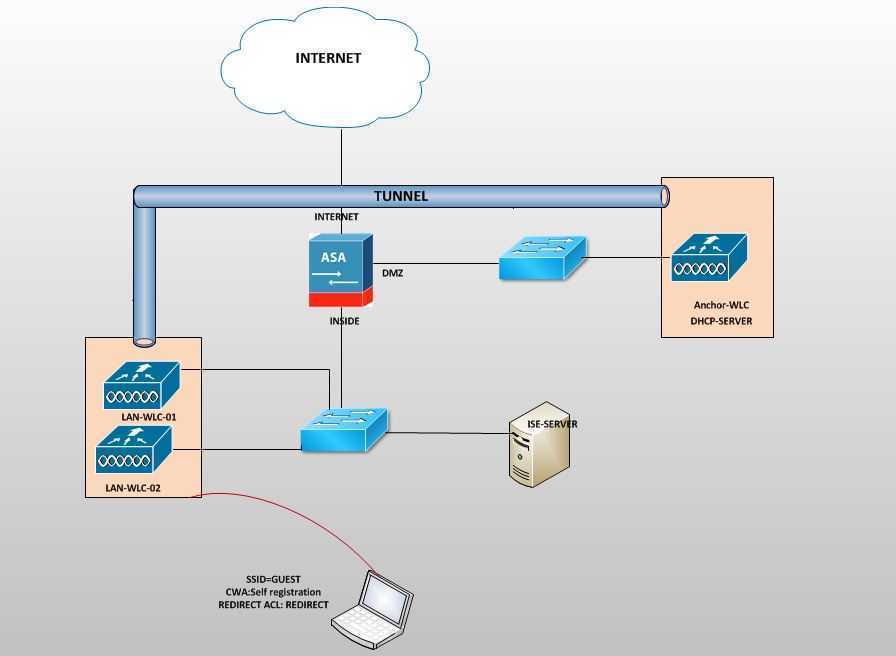
Understanding Cisco ISE 3515 Deployment
Embarking on the integration journey of the innovative network access control solution by the renowned technology leader, we delve into the intricacies of implementing the cutting-edge Cisco ISE 3515 system. This section elucidates the strategic maneuvers and pivotal considerations essential for the seamless deployment of this state-of-the-art network infrastructure solution.
- Essential Preparations: Before venturing into the deployment phase, meticulous groundwork is imperative. This entails comprehensive assessment and provisioning of requisite resources, including hardware, software, and personnel expertise.
- Architectural Framework: Crafting a robust architectural blueprint forms the cornerstone of a successful deployment strategy. This encompasses delineating network topologies, defining access policies, and orchestrating seamless integration with existing infrastructure.
- Deployment Strategies: An array of deployment options awaits, ranging from standalone installations to distributed deployments tailored to organizational exigencies. Each strategy necessitates astute planning and execution to ensure optimal functionality and scalability.
- Configuration Best Practices: Delving into the labyrinth of configuration intricacies demands adherence to best practices. From defining authentication protocols to configuring policy enforcement points, meticulous attention to detail is paramount to mitigate operational pitfalls.
- Operational Considerations: Post-deployment, the focus shifts to operational efficiency and efficacy. This entails establishing robust monitoring mechanisms, conducting periodic audits, and instituting proactive measures to preempt and mitigate potential security vulnerabilities.
Embarking on the deployment odyssey of Cisco ISE 3515 epitomizes a strategic endeavor, wherein meticulous planning, astute execution, and unwavering diligence converge to usher in a paradigm shift in network access control paradigms.
Best Strategies and Key Considerations
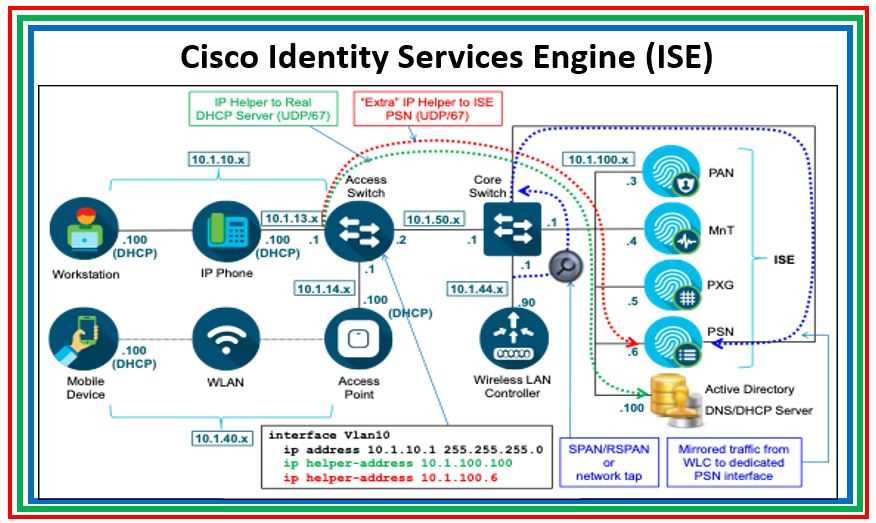
In this segment, we delve into optimal methods and critical factors to contemplate when engaging with the specifications and guidelines of the ISE 3515 platform. Our focus is on elucidating fundamental principles and strategic approaches rather than specific technical details. By adhering to these recommended practices and taking into account the following considerations, users can maximize the efficacy and efficiency of their utilization of this technology.
| Consideration | Key Points |
|---|---|
| Security Measures | Emphasize the importance of robust security protocols to safeguard sensitive data and networks. |
| Scalability | Discuss strategies for scalability to accommodate potential growth and evolving organizational needs. |
| Integration | Highlight the significance of seamless integration with existing systems and infrastructures. |
| Performance Optimization | Address techniques for optimizing performance to ensure smooth operation and minimal downtime. |
| Compliance | Outline the necessity of compliance with industry standards and regulatory requirements. |
By adhering to these overarching principles and being mindful of the specific nuances within your operational environment, you can effectively harness the capabilities of the technology encapsulated within the ISE 3515 framework.
Security Benefits of Cisco ISE 3515
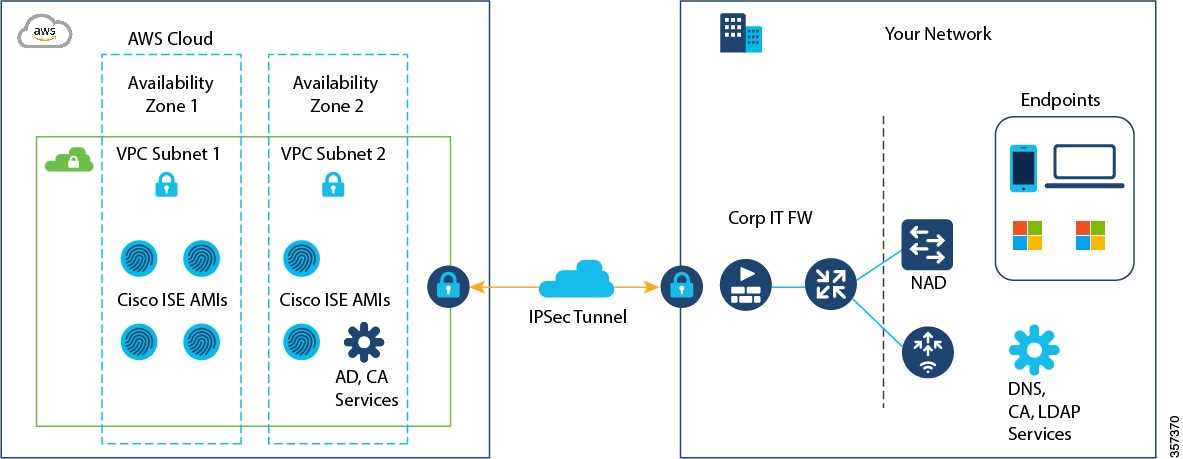
In the realm of digital security, the prowess of the innovative platform we’re examining extends far beyond mere protection. It serves as a stalwart guardian, fortifying your network with an array of sophisticated defenses, shielding against cyber threats and ensuring the sanctity of your data and operations.
- Enhanced Access Control: Grant or restrict access with granular precision, safeguarding sensitive resources from unauthorized entry.
- Streamlined Authentication: Seamlessly verify identities, thwarting potential breaches through robust authentication protocols.
- Dynamic Policy Enforcement: Enforce policies dynamically, adapting to evolving threats and operational requirements in real-time.
- Comprehensive Visibility: Gain unparalleled insights into network activities, empowering proactive threat mitigation and compliance enforcement.
- Integrated Threat Intelligence: Harness the power of integrated threat intelligence, bolstering your defenses with up-to-the-minute insights into emerging cyber threats.
By harnessing the multifaceted capabilities of this advanced solution, organizations can erect a formidable barrier against the myriad dangers lurking in the digital landscape, fostering resilience and peace of mind in an ever-evolving cyber ecosystem.