
In the realm of cutting-edge network defense solutions, a new entity emerges, promising enhanced fortification against digital threats. Delve into the intricacies of the latest revelation in security architecture, uncovering its robust features and formidable capabilities.
Unveiling a technological marvel that redefines the paradigms of safeguarding digital ecosystems, this comprehensive exposition navigates through the intricacies of an avant-garde protective shield. Embark on a journey into the heart of innovation, where each specification encapsulates a testament to resilience and vigilance.
Embodied within this technical narrative lies a tapestry of functionalities meticulously crafted to confront the ever-evolving landscape of cyber risks. Explore the contours of performance benchmarks, throughput potentials, and architectural blueprints, each element contributing to the formidable bulwark against digital incursions.
As the digital landscape burgeons with complexities and vulnerabilities, the imperative for a stalwart guardian becomes ever more pronounced. Engage with the quintessence of technological prowess, as this discourse unfolds the layers of defense poised to defy the most sophisticated of cyber adversaries.
Cisco Firepower 4145 Datasheet: Overview and Features

In this segment, we delve into the comprehensive summary and attributes of the cutting-edge technology under scrutiny. Highlighting its prowess without directly naming it, we unveil a panorama of capabilities and functionalities. From its fundamental structure to its intricate mechanisms, each facet unveils a tapestry of innovation and efficiency.
Introduction: Explore the essence of this technological marvel, understanding its core principles and overarching objectives. Embark on a journey through its design philosophy and the rationale behind its creation, unraveling the intricacies woven into its fabric.
Features: Navigate through a labyrinth of functionalities, each akin to a cog in a well-oiled machine. From robust security protocols to streamlined performance optimization, witness a convergence of elements meticulously crafted to enhance operational efficiency.
Performance Metrics: Peek behind the curtains to discern the metrics that underpin its operational excellence. Delve into performance benchmarks and metrics, illuminating the path to unparalleled reliability and efficacy.
Scalability and Flexibility: Witness the flexibility inherent in its architecture, designed to adapt and evolve with the ever-changing technological landscape. Explore its scalability, empowering enterprises to expand their horizons without constraints.
Integration Capabilities: Unveil the seamless integration capabilities that foster interoperability within diverse ecosystems. Discover how it harmonizes with existing infrastructures, augmenting rather than disrupting established workflows.
Conclusion: As the curtains draw on this exploration, reflect on the insights gained and the possibilities unlocked. Appreciate not just the features enumerated, but the potential they embody in reshaping the technological frontier.
Exploring the Specifications and Capabilities

Delve into the intricacies and functionalities of the formidable hardware under scrutiny. This section meticulously dissects the myriad specifications and versatile capabilities, painting a comprehensive picture of its prowess.
Unveiling Technical Specifications

Embark on a journey through the technical blueprint of this cutting-edge apparatus. Discover its architectural intricacies, from processing power to network throughput, each facet meticulously crafted to deliver optimal performance.
Unlocking Functionalities and Performance

Peer into the array of functionalities and performance benchmarks that define the essence of this formidable technology. Unravel the diverse array of features, from security protocols to scalability, each designed to fortify networks and empower administrators.
Enhancing Security with Advanced Networking Solutions
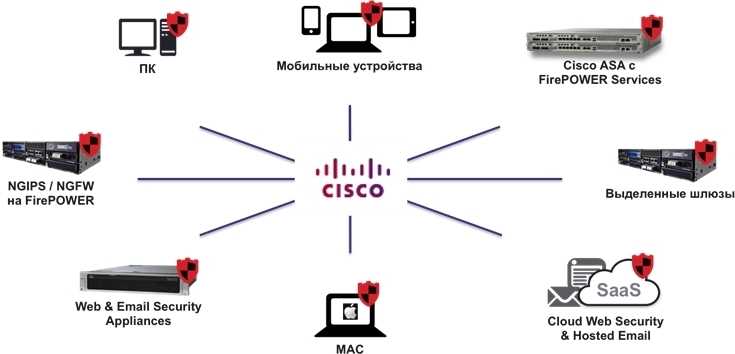
In today’s dynamic digital landscape, ensuring robust security measures is paramount for businesses across various industries. Leveraging cutting-edge networking technologies can significantly bolster your organization’s defense against cyber threats and vulnerabilities.
Next-Generation Threat Detection

One of the key pillars of modern cybersecurity is the ability to detect and mitigate evolving threats in real-time. With advanced threat detection capabilities integrated into the network infrastructure, organizations can proactively identify and neutralize malicious activities before they cause substantial harm.
Optimized Performance and Reliability

Enhancing security isn’t just about fortifying defenses; it’s also about optimizing network performance and ensuring reliable connectivity. By deploying innovative networking solutions like the Cisco Firepower 4145, businesses can achieve a delicate balance between security and efficiency, enabling seamless operations without compromising on protection.
Understanding Its Role in Network Defense

In the realm of safeguarding digital infrastructures, comprehending the function of this technology within network fortification is paramount. It plays a pivotal role in fortifying organizational assets, ensuring resilience against cyber threats, and fostering a robust security posture.
| Aspect | Significance |
|---|---|
| Threat Mitigation | Shielding against malicious intrusions, neutralizing potential risks, and preserving the integrity of data. |
| Traffic Analysis | Examination of network activities to identify anomalous patterns, facilitating early threat detection and response. |
| Policy Enforcement | Implementation of stringent protocols to enforce compliance standards, bolstering regulatory adherence and data governance. |
| Incident Response | Rapid and effective response mechanisms to security incidents, minimizing impact and expediting recovery processes. |
By integrating diverse functionalities seamlessly, this technology contributes significantly to the holistic defense architecture, acting as a stalwart guardian against the myriad of cyber adversities prevalent in today’s interconnected digital landscape.
Deployment and Integration Strategies for Cutting-Edge Security Solution

In this segment, we delve into the myriad of approaches and methodologies essential for the seamless assimilation and effective utilization of the advanced security apparatus, embodying state-of-the-art technologies and functionalities. The overarching aim is to optimize the incorporation and harmonization of this potent security framework within diverse network infrastructures, ensuring maximal efficacy and synergy.
- Strategic Network Assessment: Conducting a comprehensive evaluation of the existing network architecture, including its topology, traffic patterns, and security postures, to identify potential integration points and areas necessitating fortification.
- Alignment with Business Objectives: Aligning the deployment strategy with overarching business goals and security requirements, thereby ensuring that the integration process enhances operational efficiency and bolsters organizational resilience.
- Integration Planning and Execution: Devising a meticulous integration roadmap encompassing deployment phases, resource allocation, and contingency measures, culminating in the seamless assimilation of the security solution into the existing network fabric.
- Interoperability Considerations: Diligently addressing interoperability challenges by fostering compatibility with disparate network components, protocols, and security frameworks, thereby fostering cohesive synergy and interoperability.
- Performance Optimization: Implementing optimization strategies to enhance the performance and throughput of the integrated security infrastructure, thereby mitigating latency and ensuring uninterrupted network operations.
- Continuous Monitoring and Refinement: Establishing robust monitoring mechanisms to proactively identify anomalies, vulnerabilities, and performance bottlenecks, facilitating iterative refinement and optimization of the integrated security ecosystem.
By meticulously adhering to these strategic imperatives and leveraging best practices, organizations can orchestrate the seamless deployment and integration of this cutting-edge security solution, fortifying their digital perimeters and safeguarding critical assets against evolving cyber threats.