Embark on a journey through the realm of technological fortitude, where innovation intersects with security, and foresight becomes tangible. This enthralling exposition navigates the labyrinth of digital landscapes, unveiling a comprehensive narrative that transcends conventional boundaries. Prepare to delve into the intricacies of a pioneering compendium, meticulously crafted to illuminate the clandestine corridors of cyber guardianship.
Unlock the secrets veiled within the intricate tapestry of information, as this discourse unveils a panorama of strategic insights and tactical brilliance. Seamlessly woven into the fabric of this narrative are the threads of anticipation and preparedness, guiding the discerning reader through the variegated vistas of contemporary digital warfare.
Discover a trove of knowledge meticulously curated to redefine paradigms and fortify digital bastions against the relentless tide of cyber threats. Immerse yourself in a symphony of intellect and ingenuity, where each note resonates with the harmony of technological advancement and proactive resilience.
Cybersecurity Challenges in the Digital Era
In our contemporary landscape of interconnected systems and pervasive digitization, safeguarding sensitive information and digital assets presents a myriad of complex hurdles. The rapid evolution of technology has ushered in unparalleled convenience and efficiency, but concurrently, it has also engendered a host of cybersecurity dilemmas. These challenges stem from the intricate interplay between evolving threat vectors, the expanding attack surface, and the escalating sophistication of malicious actors.
One of the foremost challenges lies in the perpetual cat-and-mouse game between cyber defenders and adversaries. As organizations embrace digital transformation initiatives, they become increasingly reliant on interconnected networks, cloud services, and IoT devices, thereby amplifying their susceptibility to cyber threats. Furthermore, the proliferation of mobile computing and remote work arrangements has introduced new vulnerabilities, blurring the traditional boundaries of corporate perimeters.
Moreover, the exponential growth of data volume exacerbates the challenge of effectively identifying and mitigating potential security breaches. This deluge of data, coupled with the proliferation of sophisticated attack techniques such as social engineering and ransomware, inundates security teams, often leading to delayed detection and response times. Additionally, regulatory compliance requirements add another layer of complexity, necessitating robust cybersecurity frameworks to ensure adherence while navigating a constantly evolving threat landscape.
Addressing these challenges demands a multifaceted approach encompassing proactive threat intelligence, continuous monitoring, robust encryption mechanisms, and comprehensive employee training programs. Furthermore, fostering a culture of cybersecurity awareness across all organizational levels is imperative to cultivate a collective vigilance against emerging threats. By embracing a holistic cybersecurity strategy tailored to the nuances of the digital age, organizations can fortify their defenses and navigate the evolving cyber landscape with resilience and confidence.
The Evolution of Threats and Vulnerabilities
In the realm of digital security, the landscape is in constant flux, marked by the perpetual evolution of threats and vulnerabilities. Over time, the tactics employed by malicious actors have undergone a profound transformation, mirroring the advancements in technology and the changing paradigms of connectivity. This section delves into the dynamic interplay between emerging threats and the vulnerabilities they exploit, tracing the trajectory of this evolution and its implications for cybersecurity.
Rise of Sophisticated Malware

Initially, cyber threats were relatively simplistic, characterized by viruses and worms targeting individual systems with limited scope. However, as computing capabilities burgeoned, so did the sophistication of malware. The advent of trojans, rootkits, and ransomware ushered in an era of stealthy and multifaceted attacks, capable of infiltrating networks, encrypting data, and extorting individuals and organizations alike.
Exploitation of Emerging Technologies

With the proliferation of emerging technologies such as IoT (Internet of Things), AI (Artificial Intelligence), and cloud computing, new avenues for exploitation have emerged. Cybercriminals leverage vulnerabilities inherent in these innovations to orchestrate attacks on a vast scale, infiltrating interconnected ecosystems and compromising critical infrastructure. The interconnectedness of modern digital ecosystems amplifies the potential impact of such breaches, underscoring the pressing need for proactive security measures.
- The Shifting Paradigm of Cyber Warfare
- Human Factor: Social Engineering and Insider Threats
- Globalization and the Proliferation of Cybercrime
As the cyber threat landscape continues to evolve, it becomes imperative for organizations to adopt a holistic approach to cybersecurity, encompassing not only technological solutions but also robust policies, comprehensive training, and vigilant monitoring. By staying abreast of emerging threats and vulnerabilities, organizations can fortify their defenses and mitigate the risks posed by malicious actors in an ever-changing digital environment.
Empowering Network Security Solutions
Within the realm of safeguarding digital infrastructures, an amalgamation of robust measures is indispensable. In this narrative, we delve into the essence of fortifying network defenses through innovative technologies and strategic methodologies. Let’s explore how an integrated approach to security can mitigate risks, enhance resilience, and foster a proactive stance against emerging threats.
Enhancing Resilience through Integrated Solutions
Network security transcends mere fortification; it embodies a proactive paradigm, orchestrating a symphony of tools and strategies to thwart potential breaches. By amalgamating advanced threat detection mechanisms, behavioral analytics, and adaptive controls, organizations can erect formidable barriers against intrusions.
Fostering Proactive Security Posture
Empowering network security entails not only reactive measures but also a preemptive stance against evolving cyber perils. By cultivating a culture of vigilance, coupled with continuous monitoring and analysis, enterprises can anticipate and counteract potential threats before they materialize, thus fortifying their digital ramparts against adversarial incursions.
The Role of Comprehensive Information Overview
In the realm of technological solutions aimed at fortifying digital landscapes, a pivotal element emerges in the form of an intricate dossier encapsulating multifaceted insights. This section delves into the fundamental significance and functional essence of this comprehensive informational compendium.
At its core, this dossier serves as a beacon, illuminating the intricate contours of digital ecosystems, offering stakeholders a panoramic vista of operational nuances and potential vulnerabilities. It acts as a conduit, channeling intricate data streams into coherent narratives, empowering decision-makers with actionable intelligence.
- Providing a Holistic Insight Spectrum: By amalgamating disparate data points, this repository offers a holistic insight spectrum, transcending the confines of singular perspectives and fostering a nuanced understanding of operational landscapes.
- Empowering Informed Decision-Making: Armed with distilled insights, stakeholders navigate the digital terrain with precision, making informed decisions poised to mitigate risks, optimize efficiencies, and fortify resilience against emergent threats.
- Facilitating Proactive Risk Mitigation: Through predictive analytics and real-time monitoring capabilities, this dossier enables proactive risk mitigation, preempting potential disruptions and safeguarding the integrity of digital infrastructures.
- Fostering Collaborative Synergy: By fostering cross-functional collaboration and knowledge sharing, this repository catalyzes synergistic endeavors, uniting disparate entities in a concerted effort to fortify cyber defenses and uphold operational continuity.
In essence, this section underscores the pivotal role of an exhaustive informational reservoir in navigating the intricate labyrinth of digital ecosystems, heralding a paradigm shift in cyber resilience strategies.
Enhancing Visibility and Control
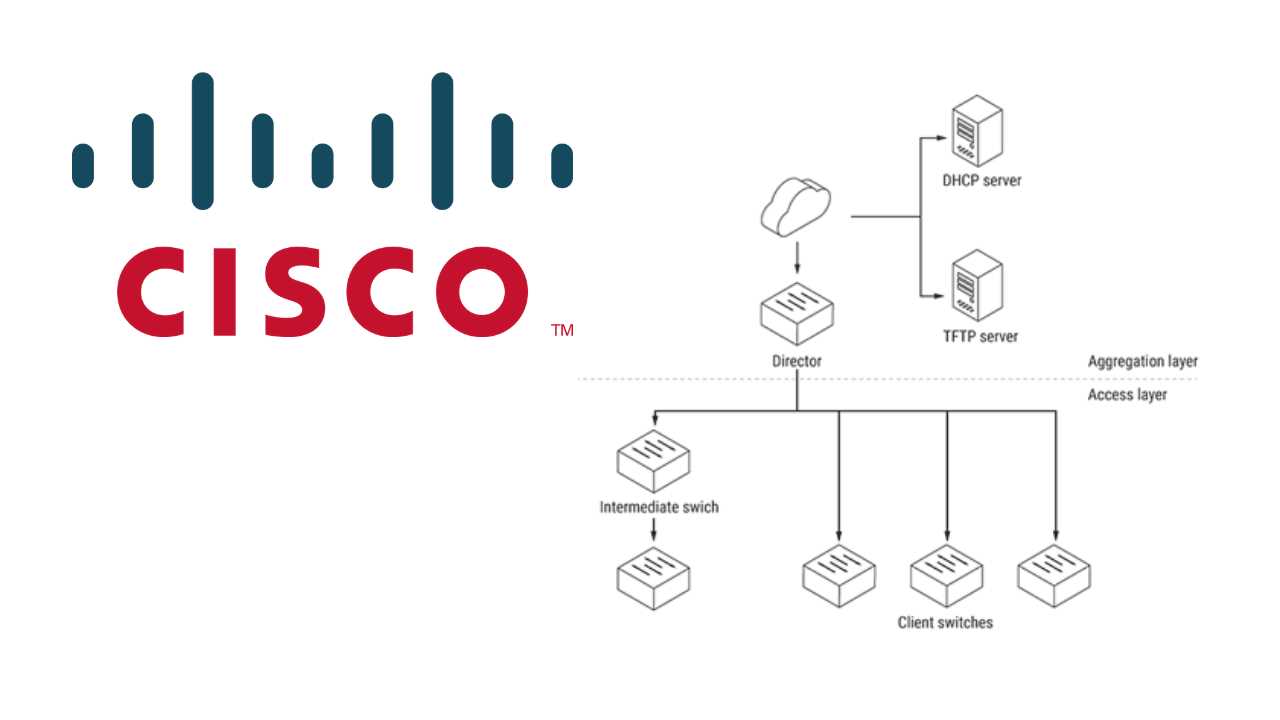
In the realm of digital security, bolstering the comprehension and management of network activity stands paramount. This segment delves into methods for augmenting the grasp and regulation of digital landscapes, empowering users with nuanced insights and refined governance.
Augmenting Insight
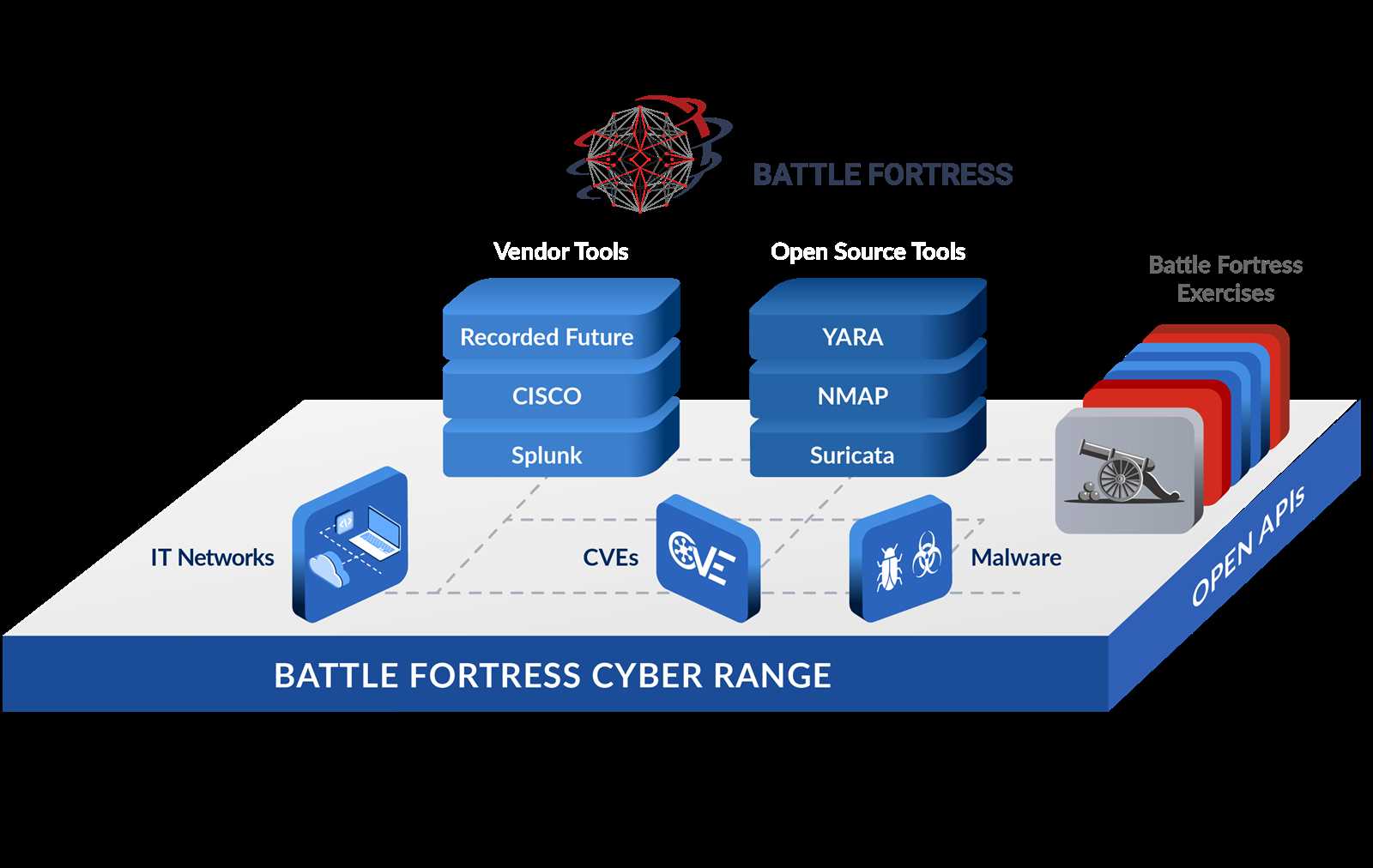
- Fostering a deeper understanding of network dynamics
- Empowering stakeholders with comprehensive data analytics
- Enhancing discernment through advanced monitoring mechanisms
Refining Oversight
- Implementing granular access controls
- Streamlining regulatory compliance processes
- Facilitating swift response mechanisms to emerging threats
Through these strategies, stakeholders can fortify their capacity to navigate the complexities of digital ecosystems, ensuring heightened vigilance and strategic governance.