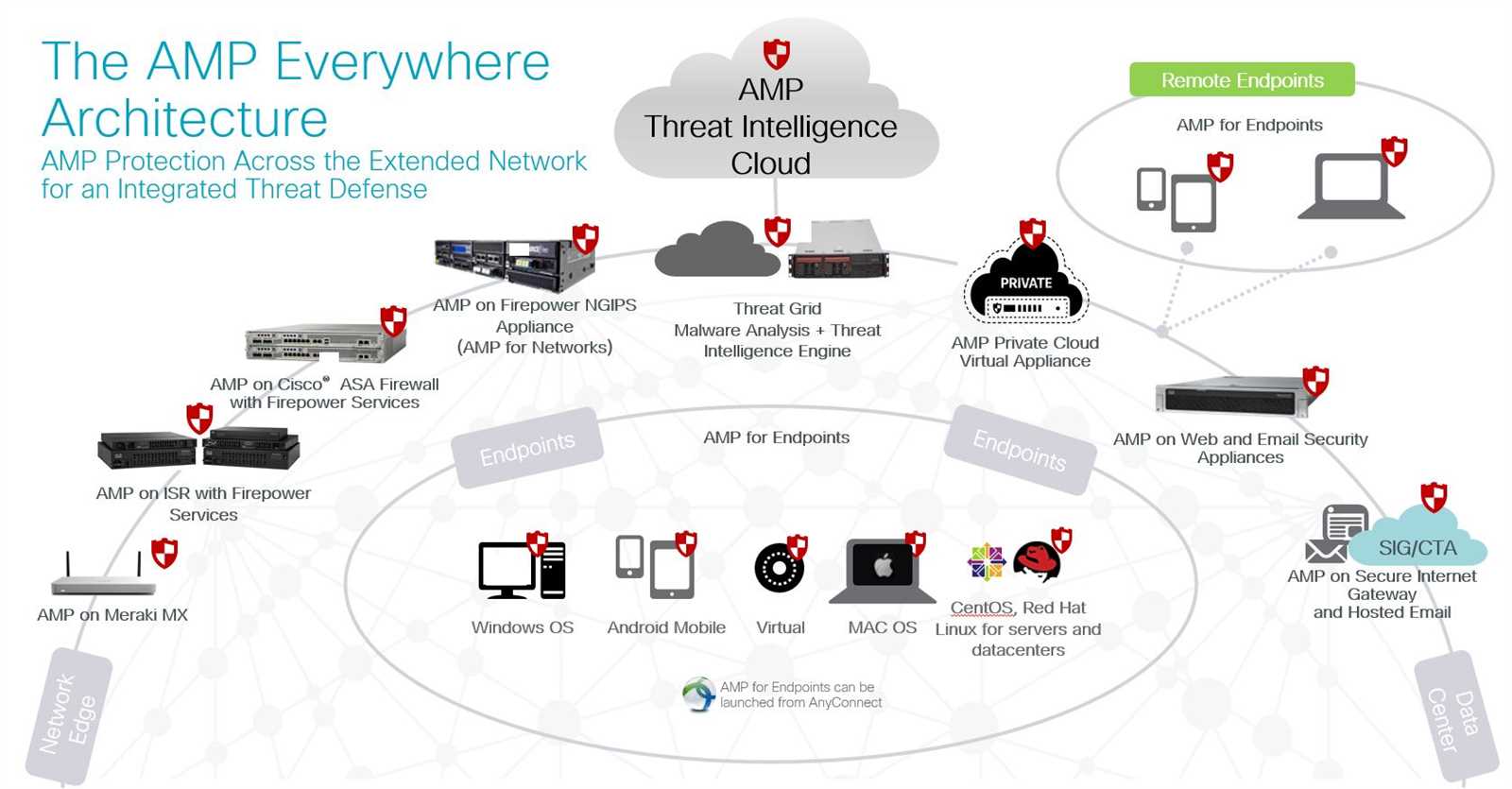
Exploring the realm of cutting-edge technological safeguards unveils a landscape where innovation intersects with security imperatives. Delving into the intricacies of advanced protective measures, this discourse navigates through the landscape of safeguarding assets against contemporary threats.
Embarking on a journey through the intricate web of protective mechanisms, one encounters a tapestry woven with precision and foresight. Within this intricate network lie solutions designed to fortify digital fortresses, ensuring resilience against the relentless tides of cyber adversaries.
Peering into the intricacies of these fortified bulwarks, one discovers a convergence of intelligence and resilience. Here, every line of code serves as a sentinel, standing guard against the encroachments of digital malfeasance.
As we traverse the digital landscape, armed with knowledge and innovation, we uncover the blueprint of defense mechanisms tailored to the exigencies of the modern age. Within this realm lies the promise of protection, where every layer of security is meticulously crafted to withstand the tests of time and adversity.
The Advantages of Cisco AMP for Endpoint

In the rapidly evolving landscape of cybersecurity threats, organizations are constantly seeking innovative solutions that can effectively detect and prevent advanced malware and attacks. Cisco AMP for Endpoint presents a comprehensive and advanced approach to protect endpoints from various threats, delivering a multitude of benefits that contribute to the overall security posture of the organization.
Enhanced Threat Detection and Response
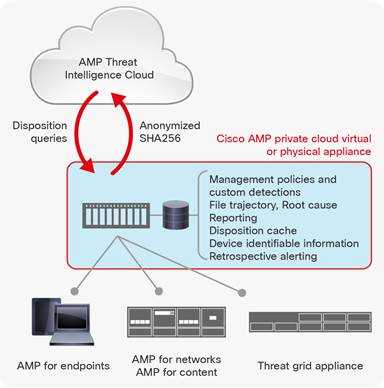
One of the key advantages of Cisco AMP for Endpoint is its ability to detect and respond to advanced threats with superior precision and speed. Leveraging advanced machine learning algorithms and behavioral analytics, it can identify and block sophisticated malware, zero-day attacks, and fileless threats that traditional security solutions may overlook.
Centralized Management and Visibility
Managing and monitoring endpoints can be a complex task, especially in large organizations with a distributed workforce. Cisco AMP for Endpoint offers centralized management and visibility, allowing security teams to have a unified view of the entire endpoint landscape. This enables quick identification of potential security vulnerabilities and faster response to incidents, reducing the overall risk exposure.
- Efficient Incident Response:
- Automated Threat Hunting:
- Real-time Forensics and Retrospective Analysis:
Integration with Security Ecosystem

Cisco AMP for Endpoint seamlessly integrates with the broader security ecosystem, enabling organizations to leverage existing investments in security infrastructure. By integrating with other Cisco security solutions, such as network and email security, it provides enhanced threat visibility and sharing of intelligence across different layers of defense, strengthening the overall security posture.
- Enhanced Threat Intelligence Sharing:
- Streamlined Incident Response:
- Consolidated Security Operations:
In conclusion, Cisco AMP for Endpoint offers numerous advantages that significantly enhance an organization’s ability to detect and respond to advanced threats. By combining advanced threat detection capabilities, centralized management, and integration with the security ecosystem, organizations can achieve a higher level of endpoint security and mitigate risks effectively.
Enhanced Threat Detection and Prevention

In today’s rapidly evolving digital landscape, the need for robust and intelligent threat detection and prevention mechanisms is paramount. Enterprises and organizations must stay one step ahead of cybercriminals, who are constantly devising new and sophisticated ways to exploit vulnerabilities and gain unauthorized access to sensitive information. The enhanced threat detection and prevention capabilities offered by Cisco amp empower organizations to defend against a wide range of threats, detect anomalous behavior, and effectively respond to security incidents.
Advanced Threat Intelligence
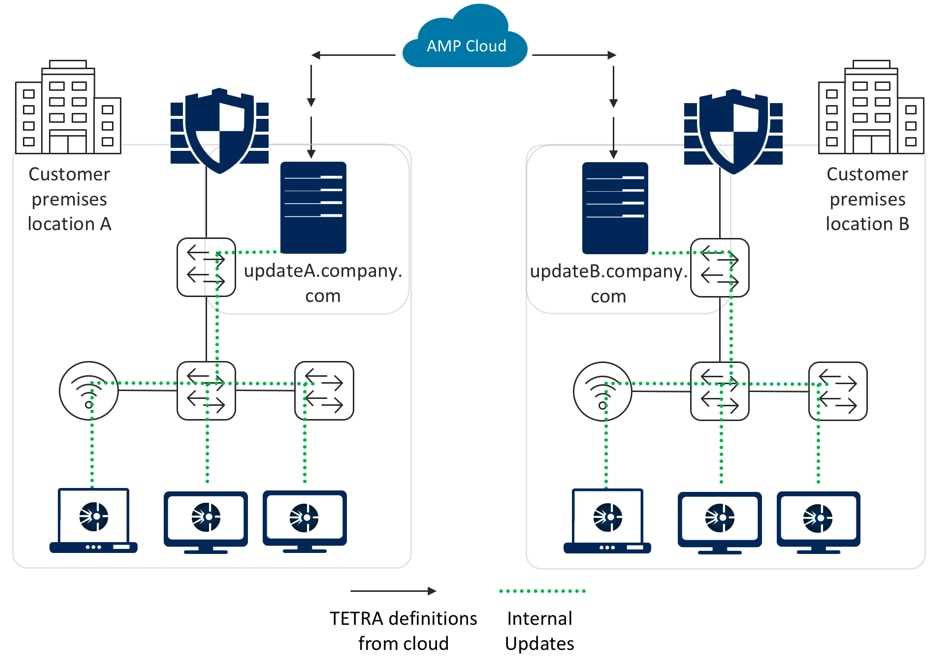
One of the key components of enhanced threat detection and prevention is the integration of advanced threat intelligence into the security infrastructure. By leveraging cutting-edge technologies and constantly updated threat intelligence feeds, organizations can proactively identify and mitigate potential risks before they cause significant harm. This allows security teams to stay informed about the latest threats, trends, and attack vectors, enabling them to make informed decisions and take prompt action to protect their digital assets.
Anomaly Detection and Behavioral Analytics
Traditional signature-based detection approaches are no longer sufficient to combat the ever-evolving threat landscape. Enhanced threat detection and prevention solutions utilize anomaly detection and behavioral analytics techniques to identify suspicious activities and deviations from normal patterns. By continuously monitoring network traffic, user behavior, and system interactions, these advanced systems can detect even the most subtle indicators of a potential threat. Real-time alerts and notifications can then be triggered, enabling security personnel to investigate and respond effectively.
Proactive Incident Response
In addition to detecting threats in real-time, enhanced threat detection and prevention solutions also facilitate proactive incident response. By automating incident response processes and providing centralized visibility into security events, organizations can accelerate incident resolution and minimize the impact of security incidents. Prompt action and efficient incident management can greatly reduce the potential damage caused by a successful cyber attack and ensure business continuity.
In conclusion, the enhanced threat detection and prevention capabilities offered by solutions such as Cisco amp provide organizations with a proactive approach to cybersecurity. By leveraging advanced threat intelligence, anomaly detection, and behavioral analytics, organizations can strengthen their security posture and effectively defend against evolving threats. With real-time alerts and automated incident response, organizations can stay agile and resilient in the face of constantly changing cyber threats.
Streamlined Incident Response and Remediation

In the fast-paced and ever-evolving world of cybersecurity, organizations face a constant battle against malicious threats and potential security breaches. To effectively protect their IT infrastructure, it is crucial for businesses to have a streamlined incident response and remediation process in place.
Streamlined incident response and remediation involves a proactive and efficient approach to identifying, containing, and resolving security incidents. It goes beyond just reacting to an incident; it aims to minimize the impact of a security breach and prevent it from escalating into a more significant issue.
A key aspect of streamlined incident response and remediation is the ability to quickly detect and analyze potential threats. By leveraging advanced security intelligence tools and techniques, organizations can identify suspicious activities or anomalies in real-time. This enables them to respond promptly and mitigate potential risks before they can cause significant damage.
Once an incident has been detected, the next step is to contain and isolate the affected systems or networks. This involves swiftly analyzing the scope and severity of the incident, determining the extent of the compromise, and segregating the impacted assets from the rest of the infrastructure. By containing the incident, organizations can prevent further spread of the threat and limit its impact on critical business operations.
After containment, the focus shifts to remediation and recovery. This involves not only removing the immediate threat but also investigating the root cause of the incident and implementing measures to prevent future vulnerabilities. Streamlined incident response and remediation involves thorough forensic analysis, proactive patching of vulnerabilities, and updating security policies and procedures to enhance overall resilience.
Furthermore, effective communication and collaboration play a crucial role in streamlined incident response and remediation. It is essential for organizations to have clear channels of communication among various teams, including IT, security, legal, and management. Timely and effective communication ensures that all stakeholders are aware of the incident, its impact, and the steps being taken to address it.
In conclusion, streamlined incident response and remediation is a fundamental component of a robust cybersecurity strategy. By embracing proactive measures, leveraging advanced security intelligence tools, and fostering effective communication, organizations can effectively mitigate risks and reduce the impact of security incidents. Through continuous improvement and adaptation, businesses can enhance their overall resilience and maintain a strong defense against evolving threats.
User-Friendly and Scalable Platform
In this section, we will explore the key features of a platform that is both user-friendly and scalable, enabling efficient and effective management of data and resources. This platform offers a streamlined user experience, ensuring that individuals of varying technical expertise can easily navigate and utilize its functionalities.
Intuitive Interface

The platform’s intuitive interface provides a visually appealing and straightforward design, allowing users to quickly access and understand the available features and tools. With its user-friendly layout, individuals can effortlessly navigate through different sections, apply filters, and perform searches to locate desired information or perform specific actions.
Flexible Customization
This platform offers extensive customization options, empowering users to tailor their experience according to their unique requirements. It allows them to configure various settings, personalize dashboard layouts, and select relevant data visualization formats. These customization capabilities enhance user productivity by ensuring that individuals can focus on the most critical information and workflows that align with their specific objectives.
- Personalized Dashboards: Users can create personalized dashboards by selecting and arranging widgets, charts, and graphs that provide real-time insights into key metrics and trends.
- Alerts and Notifications: The platform enables users to set up personalized alerts and notifications based on specific conditions or events, ensuring timely awareness of potential issues or opportunities.
- Report Generation: With the ability to generate custom reports, users can extract and present data in the desired format, facilitating decision-making and information sharing across teams and stakeholders.
Furthermore, this platform’s scalability ensures that it can adapt to changing organizational needs and growing data volumes without compromising performance. It is designed to handle large datasets and accommodate increasing user demands while maintaining optimal system responsiveness and resource allocation.
In conclusion, this user-friendly and scalable platform empowers individuals with diverse technical backgrounds to efficiently manage data and resources. Its intuitive interface and flexible customization options promote ease of use and personalized experiences. Additionally, its scalability ensures that it can accommodate organizational growth and evolving requirements. With this platform, users can effectively navigate complex data landscapes and make informed decisions to drive success.