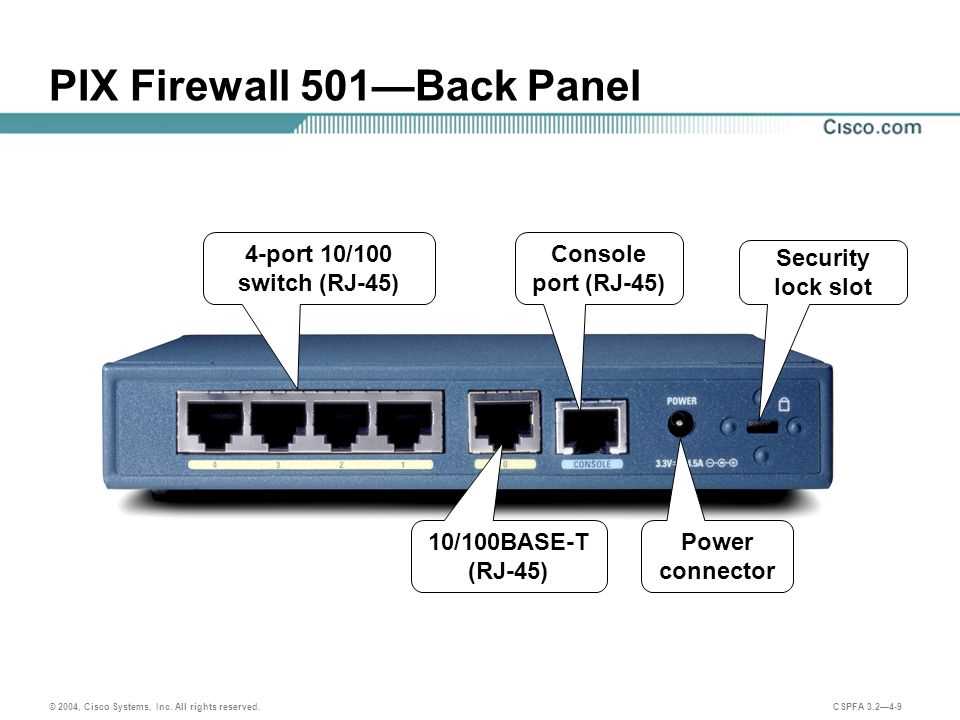
Empowering modern networks with robust protective measures
In the realm of network fortification, the quest for resilience and reliability stands as paramount. Within the dynamic landscape of digital defense, a formidable guardian emerges, embodying a fusion of sophistication and potency. This guardian, through its array of intricate mechanisms, serves as a bulwark against the relentless tide of cyber threats.
Embracing the ethos of fortified networks, this solution embodies a symphony of technological prowess and strategic foresight. Its design, a testament to meticulous engineering, heralds a new era in safeguarding digital domains against the myriad of adversarial incursions that loom ominously on the horizon.
As organizations navigate the turbulent waters of cyberspace, they seek not merely a shield, but a sentinel–a vigilant custodian that anticipates threats before they materialize, neutralizing them with efficiency and efficacy. This solution, imbued with intelligence and adaptability, stands ready to fulfill that role.
Cisco 2100 Firewall Datasheet: Key Features and Specifications
In this section, we delve into the fundamental attributes and technical details encapsulated within the comprehensive documentation of the innovative Cisco 2100 network security apparatus. Unveiling a plethora of functionalities and performance benchmarks, this segment aims to illuminate the essence of the device’s prowess in fortifying digital perimeters and safeguarding data integrity.
Core Functionalities
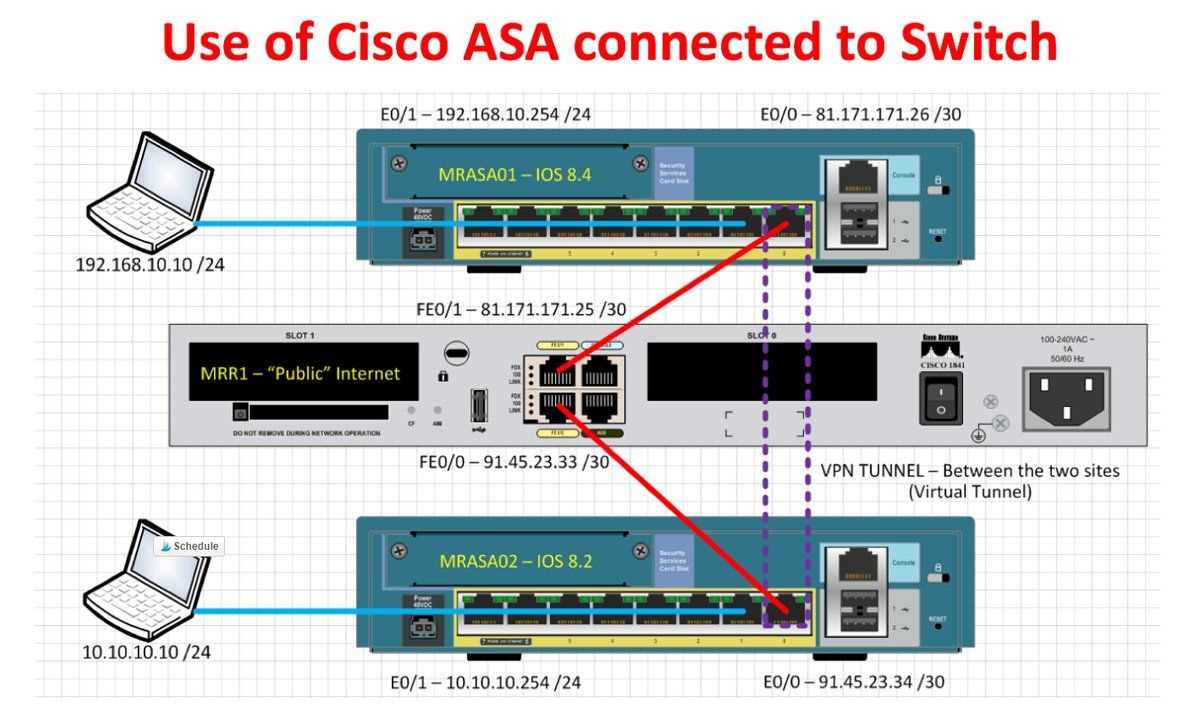
Embodied within the framework of this cutting-edge network safeguarding mechanism lie a myriad of indispensable features, each meticulously crafted to fortify cyber defense postures with unparalleled efficacy. From intricate threat detection algorithms to dynamic access control mechanisms, the device ensures robust resilience against a spectrum of digital adversaries.
Technical Specifications
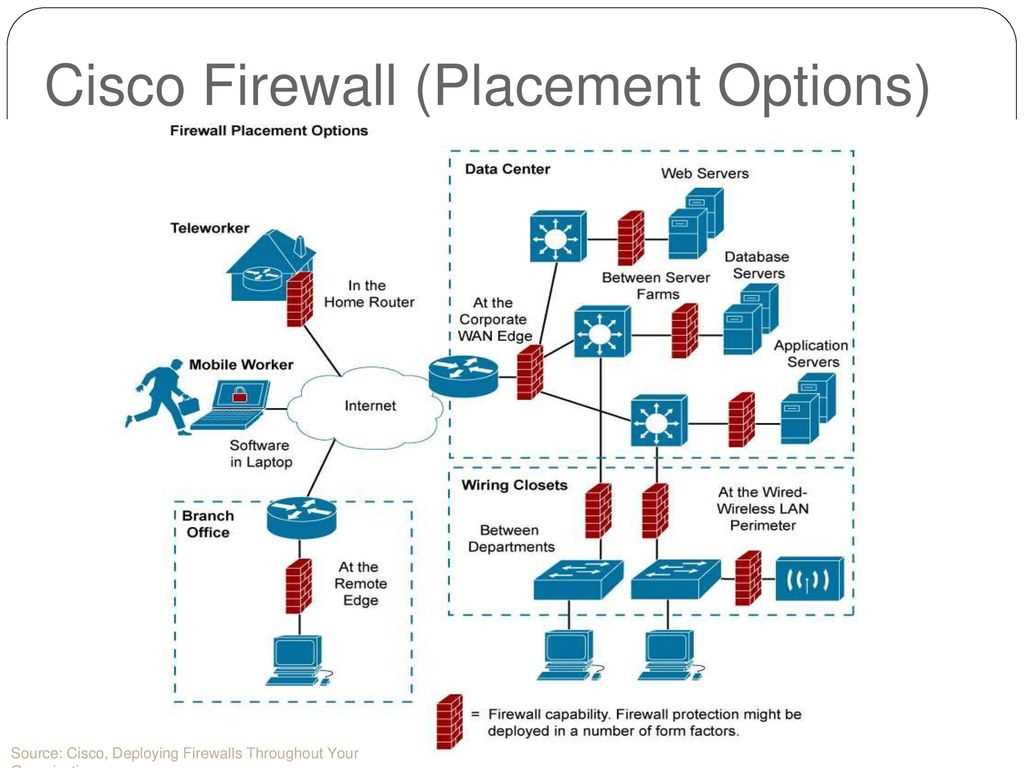
Diving into the technical minutiae, the Cisco 2100 Firewall manifests a symphony of hardware and software prowess harmonized to orchestrate seamless network protection. Boasting advanced processing capabilities and scalable memory configurations, it exemplifies a harmonious balance between performance and scalability, catering to the diverse needs of modern digital infrastructures.
Explore the Comprehensive Security Features

Delve into the expansive array of protective measures offered by this cutting-edge security solution. Uncover a spectrum of robust defenses meticulously engineered to safeguard against a myriad of digital threats. This section unveils a panorama of security protocols, mechanisms, and methodologies meticulously crafted to fortify your digital perimeter against intrusions and vulnerabilities.
Discover a suite of sophisticated tools designed to thwart malicious incursions and shield your network from unauthorized access. From advanced encryption protocols to dynamic threat intelligence mechanisms, this firewall solution employs a multifaceted approach to ensure the integrity and confidentiality of your digital assets.
Unravel the intricate layers of defense mechanisms meticulously woven into the fabric of this security architecture. Explore dynamic intrusion detection systems, proactive anomaly detection algorithms, and real-time threat mitigation strategies engineered to anticipate and neutralize emerging cyber threats before they can compromise your network’s integrity.
Embark on a journey through the nuanced landscape of access control mechanisms and privilege management protocols. From granular user authentication frameworks to role-based access control policies, this firewall solution empowers administrators with the tools needed to enforce stringent access restrictions and mitigate the risk of insider threats.
Step into the realm of comprehensive threat visibility and analytics, where advanced monitoring and logging capabilities provide real-time insights into network activity and security posture. Harness the power of actionable intelligence to proactively identify and respond to potential security incidents, ensuring uninterrupted operations and peace of mind.
Unlocking Performance: Understanding the Potential of the Cisco 2100 Security Gateway

Exploring the Core of Network Security: Delving into the intricate mechanisms of modern network defense systems unveils a realm where digital fortresses are erected to safeguard against the relentless onslaught of cyber threats. In this section, we embark on a journey to comprehend the underlying architecture and operational principles that empower the robust security paradigm of the cutting-edge Cisco 2100 Security Gateway.
Optimizing Throughput and Efficiency: Within the intricate tapestry of network security, the quest for optimal performance stands as a paramount objective. Unveiling the nuances of throughput enhancement and operational efficiency forms the cornerstone of our exploration. We delve into the strategies and technologies employed within the Cisco 2100 Security Gateway to amplify data processing capabilities and streamline network traffic management.
Harnessing Advanced Inspection Capabilities: In the ever-evolving landscape of cybersecurity, the ability to discern friend from foe lies at the heart of effective defense mechanisms. Our discourse ventures into the realm of advanced inspection methodologies, where deep packet inspection, anomaly detection, and behavioral analysis converge to fortify the digital bastions safeguarding organizational assets. Discover how the Cisco 2100 Security Gateway integrates these cutting-edge technologies to fortify its defensive arsenal.
Fostering Scalability and Adaptability: In the dynamic milieu of modern networking, the imperative for scalability and adaptability resonates profoundly. As organizations navigate the complexities of expanding infrastructures and burgeoning data volumes, the need for security solutions capable of seamless integration and flexible scalability becomes increasingly evident. Our examination extends to elucidating the scalability features and adaptive capabilities inherent within the architecture of the Cisco 2100 Security Gateway, empowering organizations to navigate the fluid contours of digital transformation with confidence.
Elevating Threat Intelligence Integration: Amidst the ceaseless flux of cyber threats, the fusion of threat intelligence with defensive strategies emerges as a linchpin of resilience. Our narrative ventures into the realm of threat intelligence integration, where real-time data feeds, threat feeds, and contextual analysis converge to fortify the proactive defense posture of the Cisco 2100 Security Gateway. Explore how the integration of threat intelligence elevates the efficacy of threat detection and response, safeguarding organizational assets against a myriad of adversarial incursions.
Navigating Compliance and Regulatory Landscapes: In the labyrinthine domain of regulatory compliance, adherence to established standards stands as a cornerstone of organizational governance. Our discourse extends to navigating the intricate tapestry of compliance frameworks and regulatory mandates, elucidating how the Cisco 2100 Security Gateway facilitates compliance adherence through robust auditing capabilities and comprehensive reporting functionalities. Uncover how the Cisco 2100 Security Gateway serves as a stalwart guardian, enabling organizations to navigate the regulatory landscape with poise and assurance.
Examining Throughput and Scalability

In this section, we delve into the performance capabilities and ability to accommodate growth of the firewall solution under scrutiny. We explore its capacity to handle increasing workloads and adapt to evolving demands, shedding light on its efficiency in processing data and facilitating seamless expansion.
Throughput Evaluation
Firstly, we assess the throughput prowess of the examined system, analyzing its capacity to swiftly and effectively process incoming and outgoing data packets. We delve into its ability to sustain high levels of data transmission without compromising on speed or reliability, gauging its performance under various loads and network conditions.
Scalability Assessment
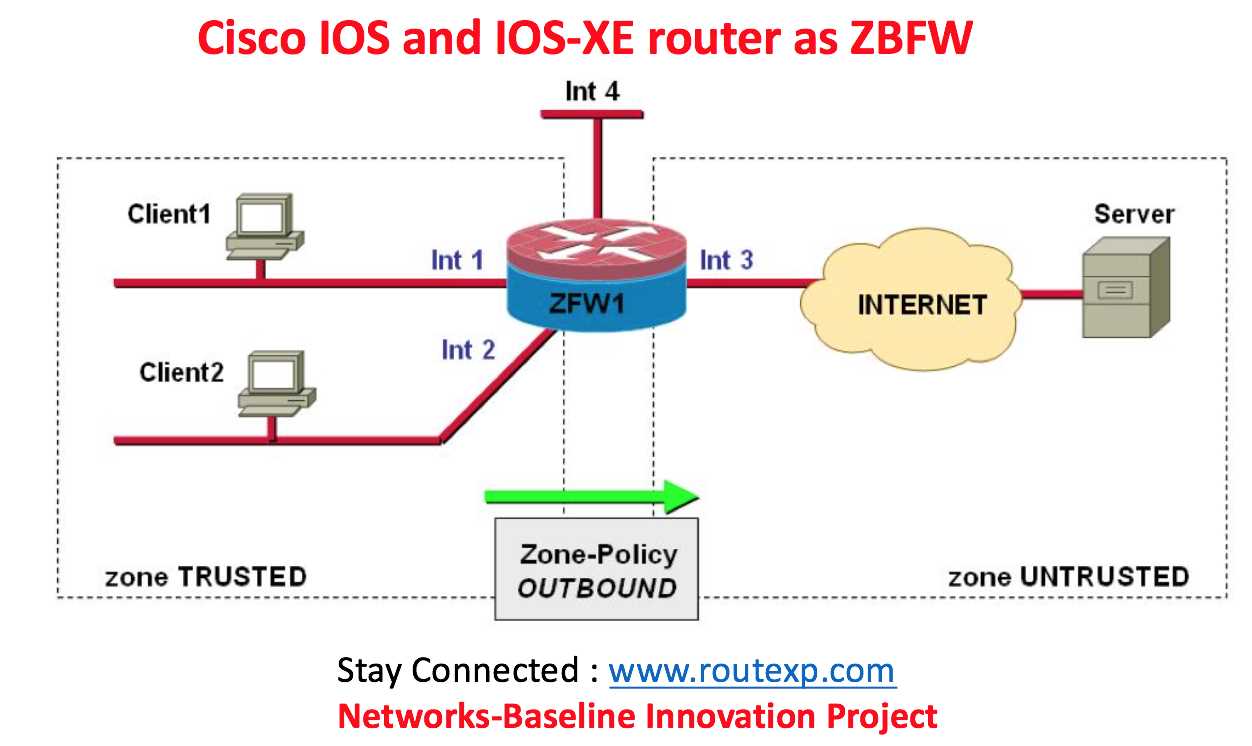
Furthermore, we delve into the scalability aspect, investigating the system’s capability to accommodate growing demands and expanding infrastructures. We scrutinize its flexibility in adapting to increasing user bases and burgeoning network complexities, examining its resilience in scaling both vertically and horizontally to meet evolving requirements.
Integration and Deployment: Enhancing Operational Efficiency with the Cisco 2100

In this segment, we delve into the seamless assimilation and strategic implementation of cutting-edge network fortification tools, harnessing the unparalleled capabilities of the innovative solution in question. Our focus extends beyond mere deployment; we explore the intricacies of integrating this advanced system into existing frameworks, optimizing functionality while minimizing disruptions.
Optimized Synergy: Maximizing the efficacy of your network infrastructure necessitates a harmonious fusion of diverse components. Here, we navigate the terrain of interoperability, ensuring that the incorporation of this sophisticated technology seamlessly aligns with your existing architecture. Through strategic planning and meticulous execution, we mitigate the risk of impedance, facilitating a smooth transition towards enhanced security paradigms.
Streamlined Deployment: Efficiency lies at the heart of successful deployment endeavors. Our approach emphasizes swift implementation without compromising precision. By capitalizing on intuitive deployment methodologies and leveraging automation where applicable, we expedite the integration process, empowering your organization to swiftly fortify its defenses against evolving threats.
Adaptive Frameworks: The dynamism inherent in modern cyber landscapes necessitates an adaptive approach to deployment. Here, we emphasize the flexibility of our strategies, accommodating the unique requirements of diverse environments. Whether your infrastructure embodies traditional architectures or embraces cloud-native paradigms, our deployment framework remains versatile, ensuring compatibility and resilience across the board.
Continuous Optimization: Integration is not an endpoint but rather a journey towards sustained excellence. Our commitment extends beyond initial deployment, encompassing ongoing optimization efforts. Through proactive monitoring, iterative refinement, and comprehensive performance analysis, we ensure that your investment yields enduring dividends, fortifying your network against emerging threats while optimizing operational efficiency.
In summary, the integration and deployment of advanced network security solutions represent a pivotal endeavor in safeguarding organizational assets and preserving operational continuity. By adopting a holistic approach that emphasizes synergy, efficiency, adaptability, and continuous improvement, organizations can maximize the value derived from innovative technologies such as the Cisco 2100, propelling them towards a more secure and resilient future.