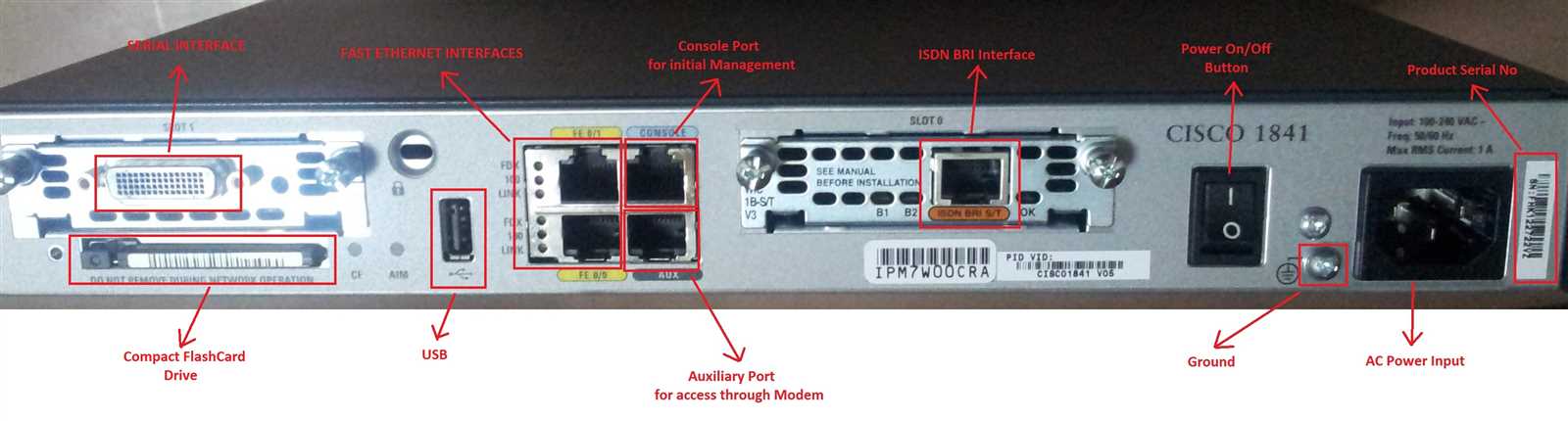
In the realm of technological advancement, there exists a compendium of unparalleled significance, encapsulating the quintessence of innovation and functionality. This document serves as a beacon, illuminating the path towards understanding and harnessing the prowess of contemporary networking solutions. Within its pages lies a tapestry woven with intricacies, where each thread represents a facet of connectivity and efficiency.
Exploring this comprehensive dossier unveils a panorama of possibilities, where intricate mechanisms converge to form a cohesive symphony of connectivity. Through its meticulous detailing, one embarks on a journey transcending mere comprehension, delving into the very fabric of network architecture.
This treasure trove of knowledge doesn’t merely enumerate features; rather, it unveils the intricacies of connectivity, delineating pathways to efficiency and reliability. Its pages resonate with the collective wisdom of technological prowess, offering insights that transcend the ordinary and embrace the extraordinary.
Cisco 1252 Datasheet Overview
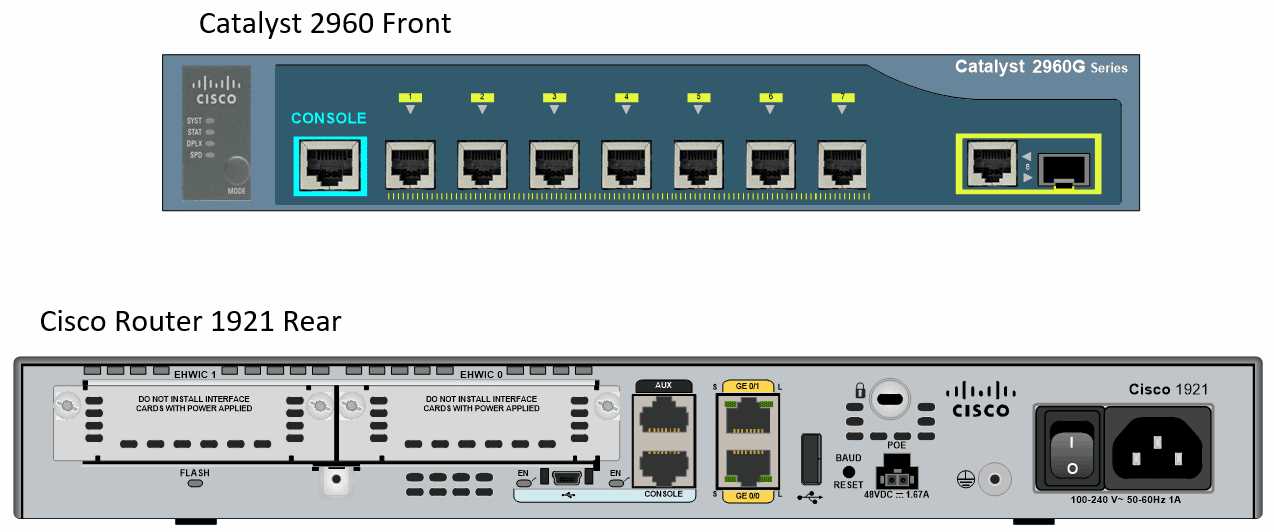
In this section, we delve into an insightful portrayal of the multifaceted attributes and functionalities encapsulated within the documentation of the esteemed networking entity, ushering an elucidating narrative that navigates through its intricacies and features.
Key Features
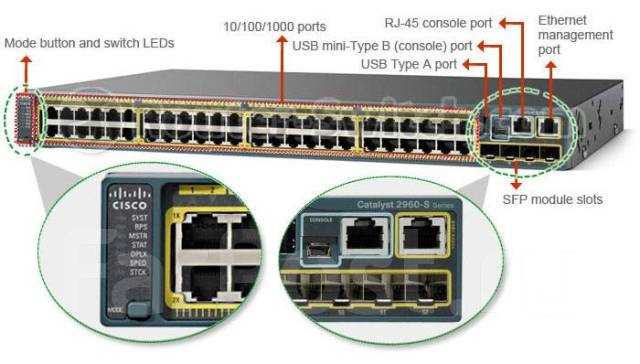
- Exploration of the pivotal functionalities
- An analysis of the noteworthy attributes
- Delving into the distinctive characteristics
Technical Specifications
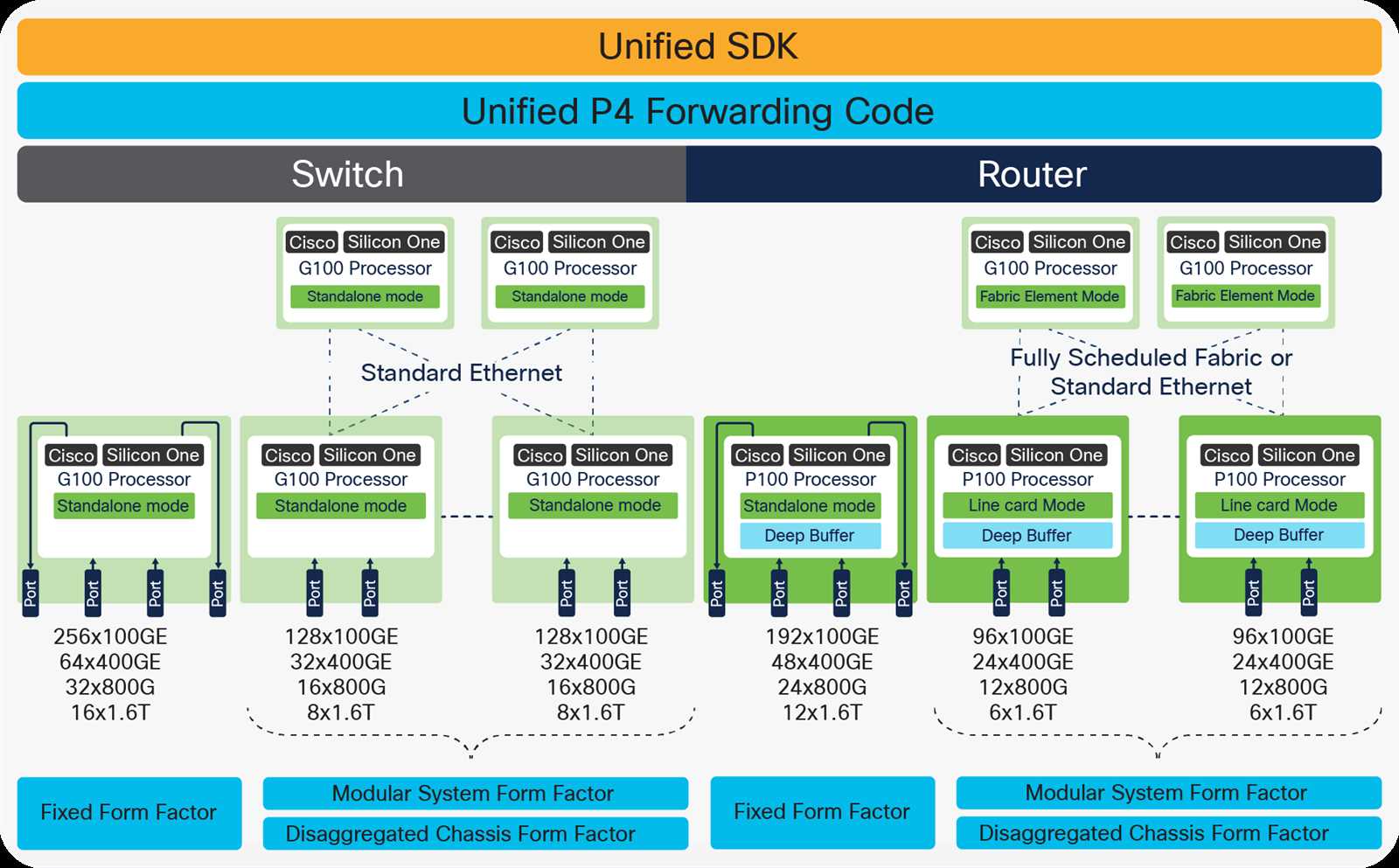
- Examination of the technical intricacies
- An overview of the performance metrics
- Scrutinizing the quantitative specifications
Understanding Key Features
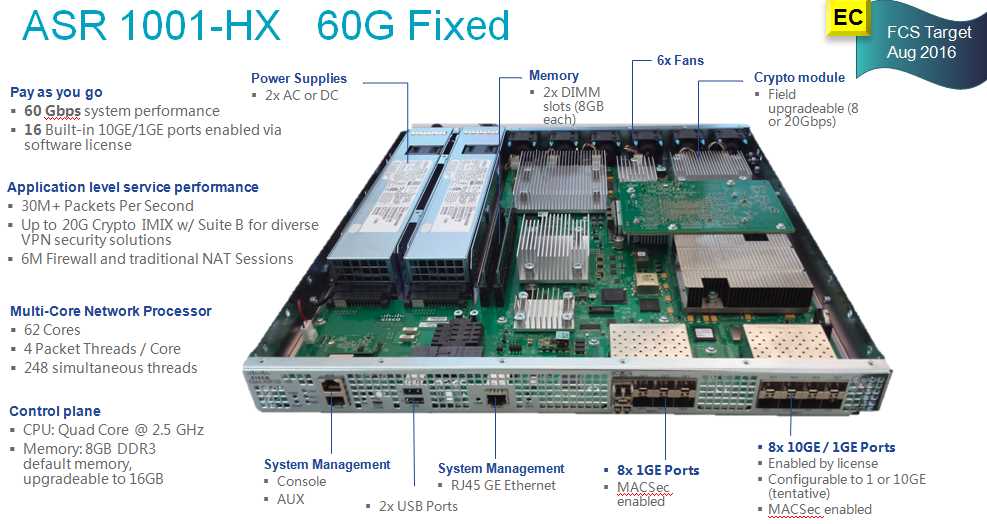
In this section, we delve into the essential characteristics and functionalities inherent to the technological specifications of the 1252 model. It elucidates the pivotal attributes integral to comprehending the operational prowess and distinguishing traits encapsulated within.
Enhanced Connectivity
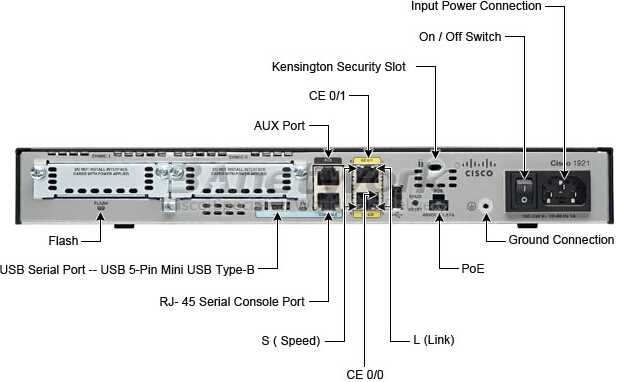
The device manifests augmented connectivity, facilitating seamless integration within diverse network infrastructures. Through its robust networking capabilities, it fosters fluid communication channels, bolstering interconnectivity across disparate nodes.
Advanced Security Protocols
Security protocols embedded within the system serve as stalwart guardians, fortifying data integrity and safeguarding against potential vulnerabilities. These protocols establish formidable barriers, ensuring stringent protection against unauthorized access and malicious intrusions.
| Feature | Description |
| High-Speed Data Transfer | Efficient transmission of data at accelerated rates, optimizing network performance. |
| Scalability | Adaptive scalability to accommodate evolving network demands, fostering expansion without compromise. |
| Reliability | Consistent and dependable operation, ensuring uninterrupted functionality even under demanding conditions. |
Technical Specifications Breakdown

In this section, we delve into the intricate details that constitute the technological framework of the device under scrutiny. We navigate through the labyrinth of specifications, dissecting each component to unveil its capabilities and functionalities.
Starting with the foundational elements, we explore the core features that lay the groundwork for the device’s performance. From there, we ascend to the higher tiers of specifications, scrutinizing the intricate nuances that define its operational prowess.
Throughout this breakdown, we decipher the technical language, unraveling the complexities to offer a comprehensive understanding of the device’s inner workings. From transmission speeds to encryption protocols, no detail is too minute to escape our examination.
By the conclusion of this exploration, readers will possess a nuanced comprehension of the technical fabric that underpins the device, empowering them to make informed decisions regarding its deployment and utilization.
Deployment Scenarios and Optimal Strategies
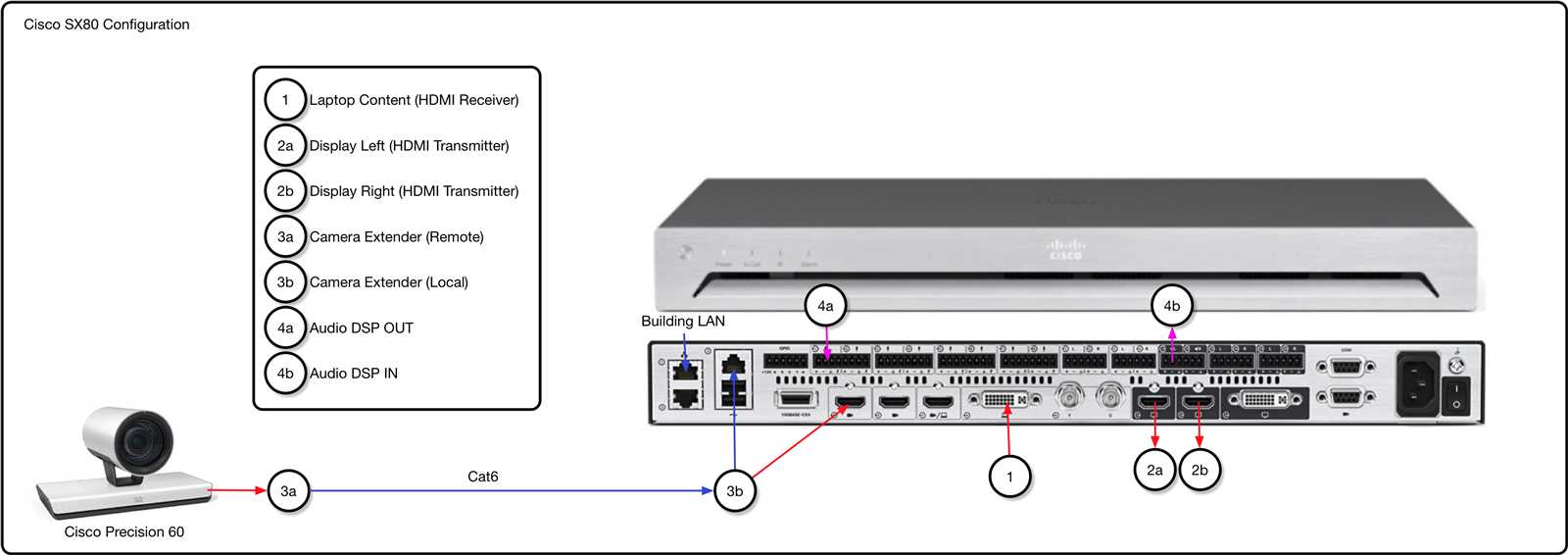
In this section, we explore various contexts and strategies for implementing the robust functionalities and leveraging the inherent capabilities of the aforementioned technology. We delve into the practical applications and recommended approaches for seamless integration within diverse environments.
Wireless Infrastructure Integration: One of the pivotal aspects revolves around integrating the technology seamlessly within existing wireless infrastructures. This encompasses a meticulous evaluation of network architectures, scalability considerations, and interoperability with prevalent networking protocols.
Vertical-Specific Implementations: Each industry sector presents unique challenges and requirements, necessitating tailored deployment strategies. Whether in educational institutions, corporate offices, or industrial settings, optimizing the technology to suit specific verticals enhances overall efficiency and performance.
Security and Compliance Considerations: Amidst escalating cyber threats, ensuring robust security measures is paramount. Delving into encryption protocols, access control mechanisms, and compliance standards forms the cornerstone of safeguarding sensitive data and mitigating potential vulnerabilities.
Optimization Techniques: Maximizing the efficacy of the technology entails employing optimization techniques tailored to the operational context. From fine-tuning signal propagation to mitigating interference, adopting best practices enhances network reliability and throughput.
Scalability and Future-Proofing: Anticipating future growth and technological advancements is essential for long-term viability. Deploying scalable architectures and future-proofing strategies empowers organizations to adapt seamlessly to evolving demands and emerging paradigms.
Performance Monitoring and Fine-Tuning: Continuous performance monitoring and fine-tuning are indispensable for maintaining peak operational efficiency. Leveraging diagnostic tools and analytics facilitates proactive identification and resolution of potential bottlenecks and performance constraints.
User Experience Enhancement: Ultimately, the overarching goal is to enhance user experience and productivity. Emphasizing user-centric design principles and optimizing network responsiveness fosters a seamless and gratifying user experience.
Conclusion: By elucidating diverse deployment scenarios and delineating optimal strategies, this section equips stakeholders with the insights and guidance necessary for leveraging the technology to its fullest potential.