
When it comes to modern cybersecurity, organizations are constantly seeking innovative and reliable solutions to protect their sensitive data and infrastructure from potential threats. In the ever-evolving landscape of digital security, one name consistently stands out: Checkpoint EDR.
Within the realm of endpoint detection and response, Checkpoint EDR sets the benchmark for comprehensive protection, leveraging cutting-edge technologies and intelligent algorithms to safeguard your network from even the most sophisticated cyberattacks. Operating silently in the background, this advanced security solution empowers organizations to proactively identify, analyze, and mitigate potential risks in real-time.
With a relentless focus on adaptability and agility, Checkpoint EDR diligently monitors and analyzes all activities happening across endpoints throughout your entire network. By employing state-of-the-art machine learning algorithms, it swiftly distinguishes normal behavior patterns from malicious activities, ensuring that potential threats don’t go unnoticed. The proactive nature of Checkpoint EDR allows businesses to stay one step ahead of cybercriminals, preventing potential security breaches and minimizing the impact of attacks.
Furthermore, Checkpoint EDR brings a multitude of intelligent features that facilitate effective incident response. Through constant monitoring and automated alerts, it provides security teams with valuable insights and actionable intelligence, enabling them to swiftly investigate suspicious activities, isolate affected devices, and eradicate threats before they can cause significant harm. The meticulous analysis of data and behavior patterns not only aids in deterring attacks but also assists in understanding potential vulnerabilities within your infrastructure, thereby enabling you to fortify your security measures.
With its robust and intuitive interface, Checkpoint EDR empowers security professionals with clear visibility and control over their network environment. Real-time dashboards, detailed reports, and customizable threat detection settings provide valuable information at a glance, enabling timely responses and proactive decision-making. Additionally, with its seamless integration capabilities, Checkpoint EDR seamlessly fits into existing security ecosystems, enhancing overall security posture and streamlining incident response workflows.
In conclusion, Checkpoint EDR, armed with its advanced technologies and intelligent features, offers unparalleled protection against evolving cyber threats. Trustworthy, efficient, and versatile, it ensures the safety of your organization’s critical assets, providing peace of mind for security teams and enabling businesses to focus on their core objectives without compromising on security.
CheckPoint EDR: Understanding the Basics
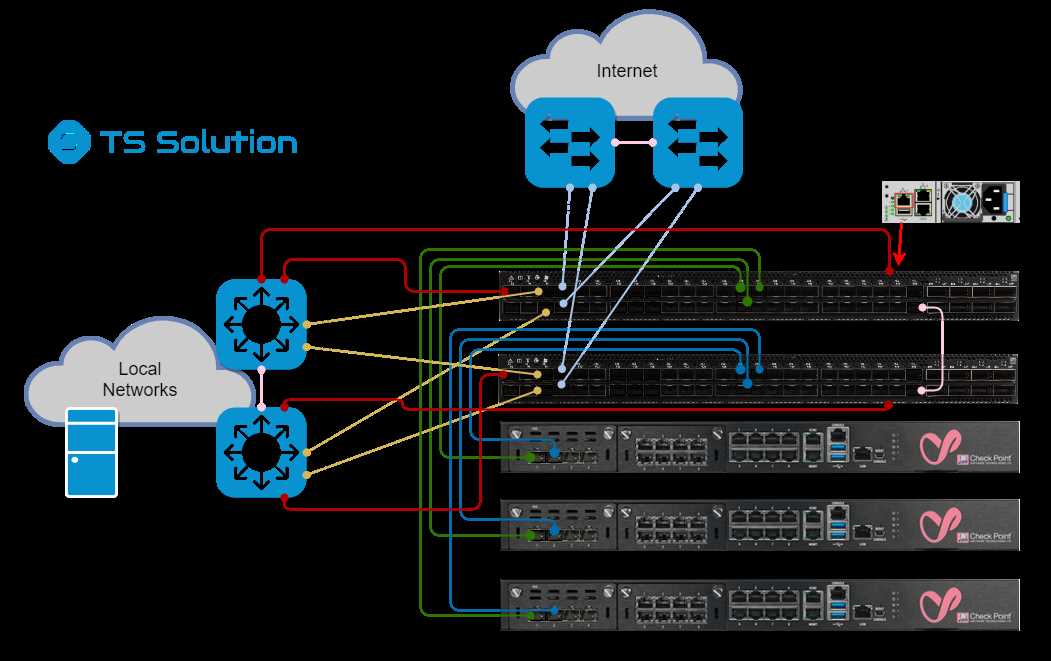
In this section, we will delve into the fundamental concepts of CheckPoint EDR, gaining a comprehensive understanding of its capabilities and functionalities.
1. Introduction to CheckPoint EDR
Firstly, we will introduce the concept of CheckPoint EDR, a cutting-edge technology designed to enhance endpoint security and threat management. We will explore its significance in safeguarding organizations against evolving cyber threats and the importance of deploying an effective EDR solution.
2. Key Features and Benefits

Next, we will examine the key features and benefits of CheckPoint EDR. We will highlight its advanced threat detection and response capabilities, proactive monitoring, and real-time alerting system. Moreover, we will explore how CheckPoint EDR empowers organizations with actionable insights and strengthens incident response capabilities.
3. EDR Workflow and Architecture
In this section, we will provide an overview of the EDR workflow and architecture. We will explain the data collection methods employed by CheckPoint EDR, including endpoint sensors and log analysis. Additionally, we will discuss the role of artificial intelligence and machine learning in facilitating timely threat detection and response.
4. Integration with Security Operations Center (SOC)
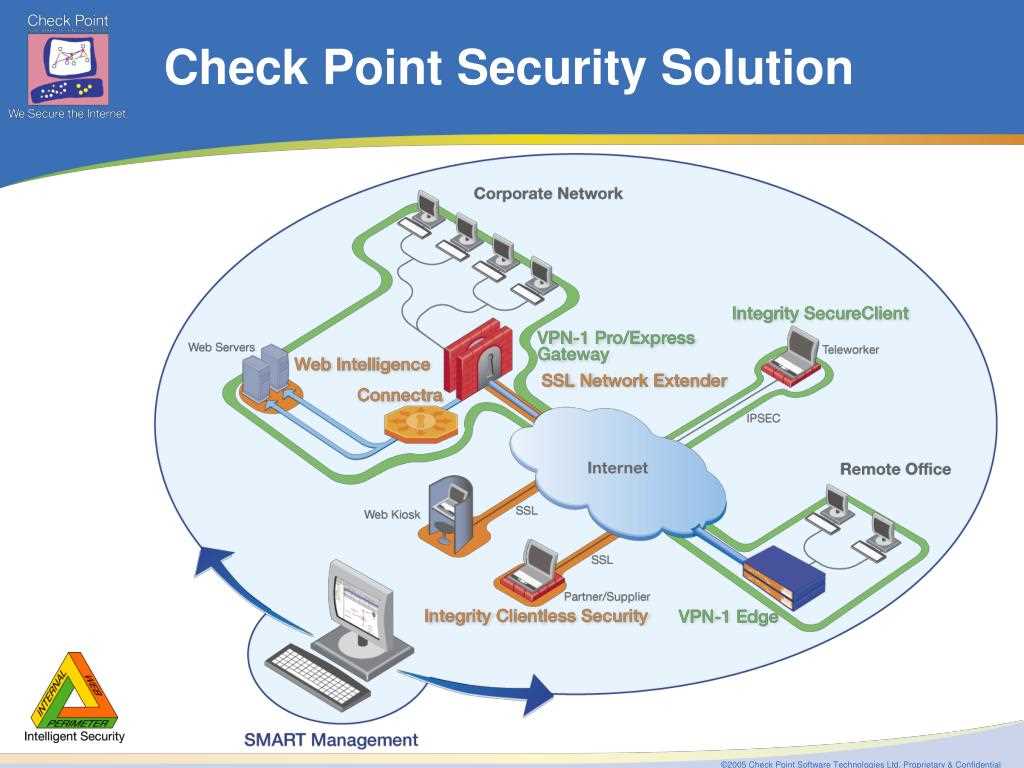
Furthermore, we will explore how CheckPoint EDR seamlessly integrates with Security Operations Centers (SOCs). We will outline the benefits of consolidating EDR data within a centralized SOC platform, facilitating streamlined analysis and collaboration among security teams. Moreover, we will discuss the importance of SOC integration in enhancing incident response and threat hunting capabilities.
5. Case Studies and Success Stories
Lastly, we will showcase real-world case studies and success stories that highlight the effectiveness of CheckPoint EDR in mitigating advanced threats and enabling swift incident resolution. We will examine specific scenarios where CheckPoint EDR played a pivotal role in preventing data breaches and minimizing the impact of cyber attacks.
By the end of this section, readers will have a solid grasp of CheckPoint EDR’s fundamental principles, its role in bolstering endpoint security, and its potential impact on mitigating sophisticated cyber threats.
Key Features and Capabilities
The following section outlines the essential features and capabilities of the Checkpoint EDR solution, providing an overview of its advanced functionalities without specifically mentioning the terms “Checkpoint,” “edr,” or “datasheet.”
Enhanced Threat Detection

- Advanced anomaly detection algorithms
- Real-time monitoring and analysis
- Behavior-based threat identification
- Machine learning-powered threat intelligence
Proactive Incident Response
- Automated incident notification and prioritization
- Real-time threat hunting and investigation
- Isolation and containment of affected endpoints
- Threat remediation and mitigation actions
Endpoint Visibility and Control
- Comprehensive endpoint asset inventory
- Continuous monitoring of device activity
- Application control and whitelisting
- Policy enforcement and compliance
Centralized Management and Reporting
- Single-pane-of-glass dashboard
- Customizable reporting and analytics
- Integration with existing security tools
- Automated software updates and patch management
With these key features and capabilities, the Checkpoint EDR solution provides unparalleled protection and visibility, empowering organizations to detect and respond to advanced threats effectively.
Benefits of Using CheckPoint EDR
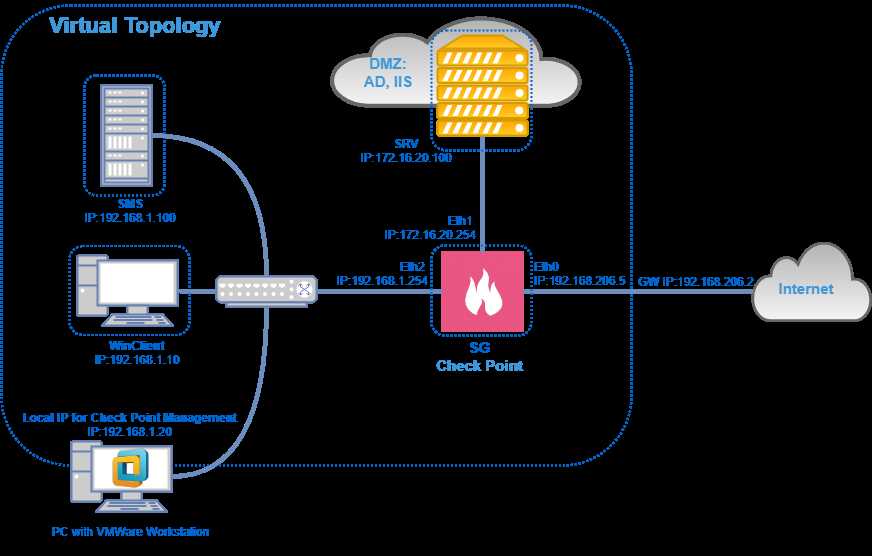
CheckPoint EDR provides numerous advantages and advantages for organizations seeking enhanced security and threat detection capabilities. This section explores the unique benefits that CheckPoint EDR offers, highlighting its value in safeguarding against advanced cyber threats and improving incident response.
Enhanced Threat Detection
CheckPoint EDR employs advanced detection techniques to identify and analyze potential threats, allowing organizations to proactively defend against various cyberattacks. By leveraging cutting-edge technologies, it offers real-time visibility into endpoint activities, detecting and mitigating threats before they can cause significant damage.
Improved Incident Response
With CheckPoint EDR, organizations can respond more effectively to security incidents. Its comprehensive incident response capabilities enable quick identification, containment, and remediation of threats. By minimizing the time between detection and response, it helps reduce the potential impact of cyber incidents and prevent their escalation.
| Benefit | Description |
|---|---|
| Enhanced Visibility | CheckPoint EDR provides deep visibility into endpoint activities, allowing organizations to gain insights into potential threats and vulnerabilities. |
| Advanced Analytics | By utilizing advanced analytics capabilities, CheckPoint EDR can detect and analyze sophisticated attack techniques that may evade traditional security measures. |
| Automated Response | CheckPoint EDR automates incident response actions, enabling quicker and more efficient reactions to security events, reducing manual effort and potential human errors. |
| Integration with Security Infrastructure | CheckPoint EDR seamlessly integrates with existing security infrastructure, allowing organizations to enhance their overall security posture without significant disruptions. |
Overall, the use of CheckPoint EDR empowers organizations to better protect their endpoints, detect emerging threats, and respond swiftly to security incidents. By leveraging its advanced capabilities and comprehensive features, organizations can establish a robust defense against modern cyber threats.
Enhanced Threat Detection and Response
In today’s rapidly evolving threat landscape, organizations are facing increasingly sophisticated and malicious cyber attacks. As a result, it has become crucial for businesses to enhance their threat detection and response capabilities to effectively safeguard their digital assets.
Comprehensive Threat Monitoring
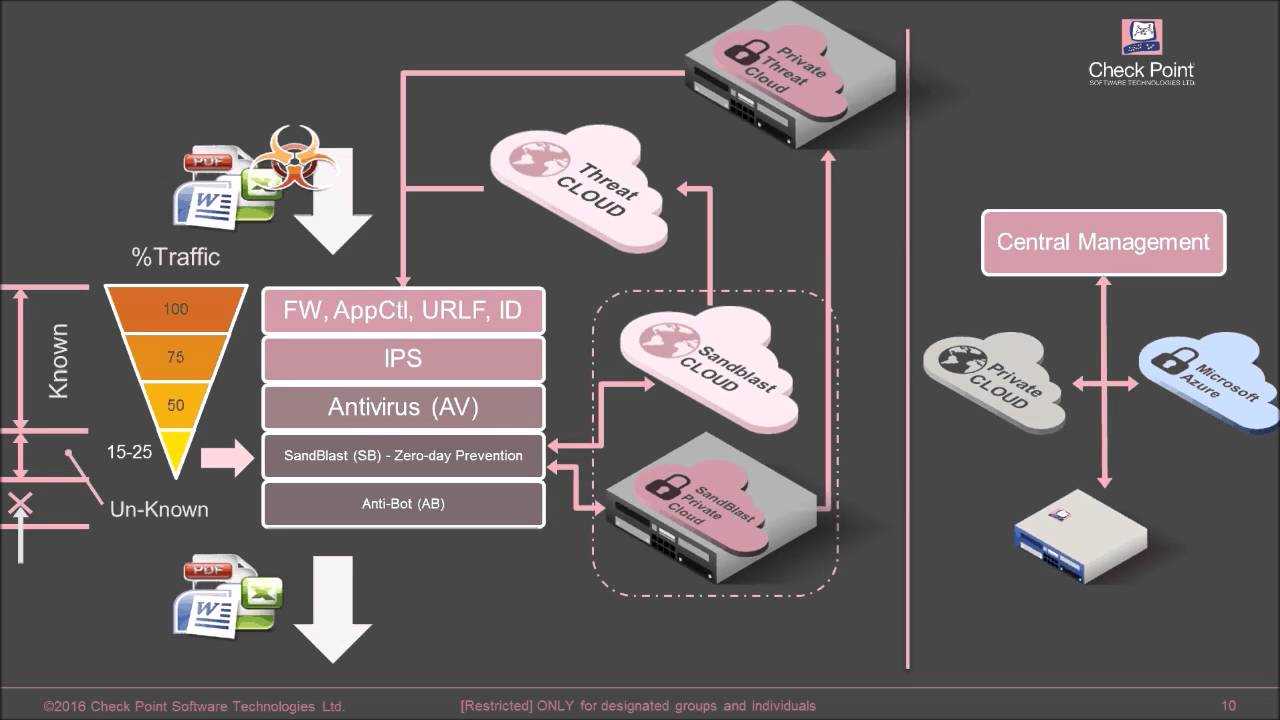
Enhanced Threat Detection and Response leverages advanced technologies and algorithms to provide organizations with comprehensive threat monitoring. This sophisticated solution constantly analyzes network traffic, user behavior, and system logs to identify any anomalies or suspicious activities that may indicate a potential security breach.
Through real-time monitoring and intelligent analysis, enhanced threat detection helps organizations stay one step ahead of cyber threats and proactively respond to any potential risks. By accurately detecting and promptly alerting security teams to potential threats, organizations can minimize the impact of cyber attacks and prevent them from spreading throughout their network.
Effective Incident Response
Enhanced Threat Detection and Response also offers powerful incident response capabilities. In the event of a security incident, this solution provides security teams with the necessary tools and insights to quickly identify the root cause, contain the incident, and mitigate any potential damage.
Organizations can create predefined response workflows, enabling them to automate certain actions and streamline the incident resolution process. This not only reduces response times but also ensures consistent and effective incident handling across the entire organization.
Moreover, enhanced threat detection and response solutions provide detailed reporting and analysis features, allowing organizations to gain valuable insights into their security posture. This information can be used to identify vulnerabilities, implement necessary security measures, and continuously improve the overall security posture of the organization.
- Real-time threat monitoring and analysis
- Proactive identification of potential security breaches
- Effective incident response and containment
- Automated response workflows for faster resolution
- Detailed reporting and analysis for continuous improvement
In conclusion, Enhanced Threat Detection and Response is a vital component of every organization’s cybersecurity strategy. By implementing this solution, businesses can bolster their defenses, detect threats more effectively, and mount a swift and efficient response to mitigate potential risks.
Improved Incident Response Management
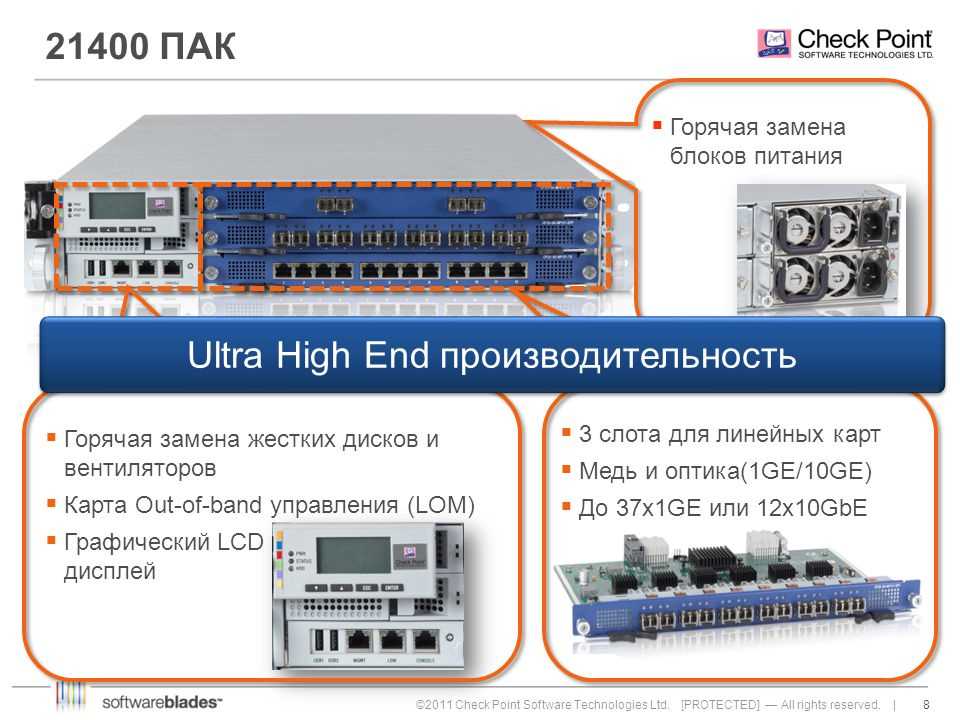
Enhancing the way organizations handle and mitigate security incidents is paramount in today’s rapidly evolving threat landscape. In this section, we explore the strategies and techniques that empower security teams to improve their incident response management capabilities and ensure a prompt and effective response to potential security breaches.
Streamlined Incident Detection
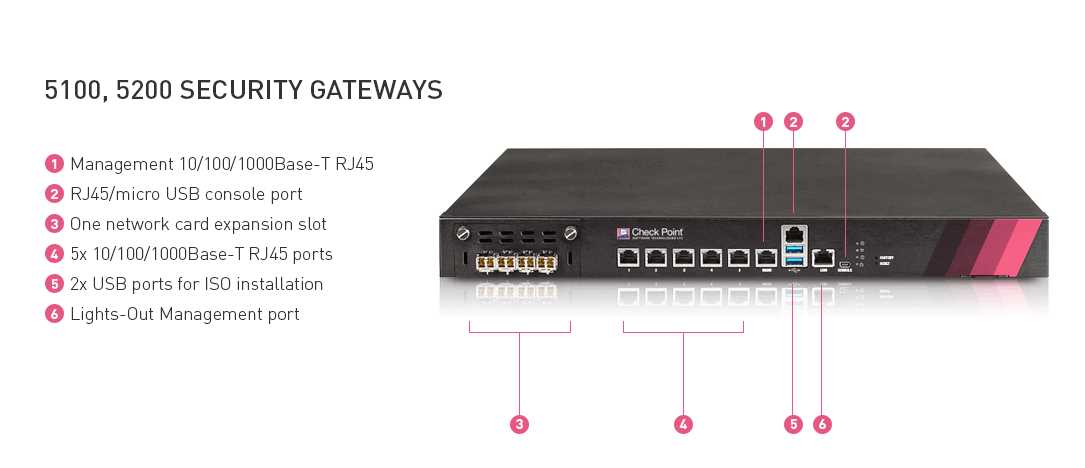
A key aspect of improved incident response management is the ability to swiftly detect and analyze security incidents. By implementing advanced monitoring and detection mechanisms, organizations can proactively identify potential threats, anomalous behavior patterns, and suspicious activities across their network infrastructure and endpoints. Through the use of cutting-edge technologies, such as artificial intelligence and machine learning algorithms, security teams can quickly and accurately identify potential security incidents, minimizing the time it takes to respond and mitigate the impact of a breach.
Effective Incident Response Coordination
Timely and coordinated response is essential when dealing with security incidents. By establishing clear escalation procedures, defining roles and responsibilities, and leveraging robust communication channels, organizations can optimize their incident response workflows. Proper incident response coordination enables security teams to align their efforts, collaborate seamlessly, and efficiently address the incident at hand. Moreover, the integration of incident response platforms and automation tools empowers organizations to streamline their response processes, ensuring consistent and efficient incident handling.
With an improved incident response management approach, organizations can better protect their sensitive data, safeguard their networks, and minimize the impact of security breaches. By leveraging advanced detection capabilities and fostering effective incident response coordination, security teams can enhance their ability to detect, analyze, and mitigate potential threats, providing a strong defense against ever-evolving cyber threats.