
Embark on a journey through the intricacies of modern digital fortifications. Within the realm of cybersecurity, there exists a realm of comprehensive documents, akin to navigational charts, elucidating the contours of protective measures and defensive strategies. These documents, akin to security blueprints, serve as a guidepost for safeguarding digital assets and preserving the integrity of virtual domains.
Delve into the heart of these informational compendiums, where the intricacies of network fortifications are unfurled in meticulous detail. These documents encapsulate the essence of cyber defense, outlining the methodologies, tools, and protocols essential for safeguarding against the myriad threats lurking in the digital ether.
Embark on a voyage through these cryptic manuscripts, where the secrets of cyber resilience await discovery. Unravel the enigma of security architecture and threat mitigation strategies, as these documents serve as beacons amidst the tempestuous seas of digital warfare.
Understanding Information Guides for Inspection Points
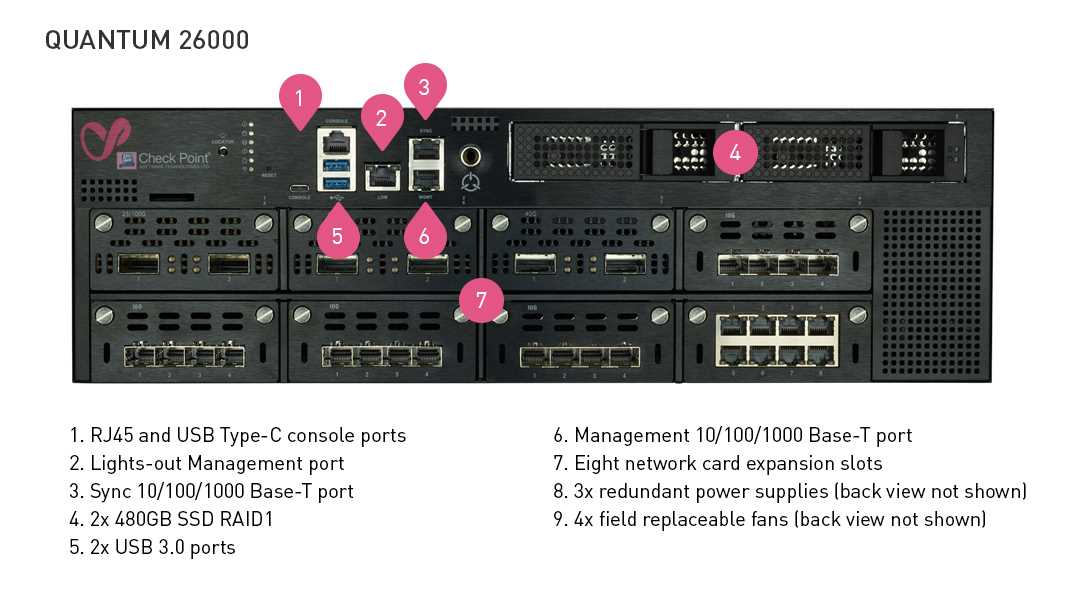
Delving into the comprehensive documentation designed to elucidate the intricacies of surveillance junctures offers a pivotal insight into network fortification. These informational compendiums serve as indispensable references, offering nuanced perspectives on the operational parameters and performance metrics intrinsic to security protocols.
Deciphering the Nitty-Gritties: Unraveling the dense fabric of technical specifications and procedural guidelines embedded within these guides furnishes a profound comprehension of the underlying mechanisms governing security checkpoints. By navigating through the labyrinth of terminologies and elucidating the contextual significance of each component, stakeholders can adeptly navigate the terrain of risk mitigation.
Peering into Operational Dynamics: Beyond a mere enumeration of features, these guides illuminate the dynamic interplay between hardware configurations and software functionalities. Through elucidating the symbiotic relationship between system architecture and operational exigencies, stakeholders gain a holistic understanding of the systemic resilience necessary for safeguarding digital assets.
Evaluating Performance Benchmarks: Rigorous assessment methodologies underpinning performance evaluations delineate the efficacy of defensive measures against emergent threats. By scrutinizing the empirical data encapsulated within these benchmarks, stakeholders ascertain the efficacy of security provisions and discern areas necessitating further fortification.
Envisioning Integration Strategies: The seamless integration of security frameworks within existing infrastructures necessitates a nuanced understanding of interoperability considerations. By delineating compatibility matrices and elucidating integration pathways, these guides facilitate the harmonious coalescence of disparate security solutions.
Anticipating Future Trends: A forward-looking perspective permeates these guides, offering prescient insights into evolving threat landscapes and anticipatory strategies. Through prognostic analysis and trend extrapolation, stakeholders are empowered to proactively adapt security paradigms to mitigate nascent risks.
Deciphering Technical Specifications

Understanding the intricacies of product documentation is paramount for informed decision-making. In this section, we delve into the nuances of deciphering technical specifications, shedding light on the essential elements that compose them.
Interpreting Key Metrics
Within technical literature, numerical data and performance metrics are often presented to encapsulate the capabilities of a product. These figures serve as benchmarks, guiding users in assessing the product’s suitability for their specific requirements.
Decoding Terminology
Technical specifications are laden with specialized terminology and jargon, which can be daunting for those unfamiliar with the domain. This subsection elucidates common terms and phrases encountered in technical documentation, facilitating comprehension and enabling users to navigate the datasheet effectively.
Analyzing Performance Characteristics
Each product specification carries a wealth of information regarding its performance under various conditions. From throughput rates to latency figures, this segment dissects the performance characteristics elucidated in the datasheet, providing insights into the product’s operational capabilities.
Understanding Environmental Considerations
Beyond raw performance metrics, technical specifications often outline environmental parameters within which the product operates optimally. This includes factors such as temperature ranges, humidity levels, and power requirements. Understanding these environmental constraints is imperative for deploying the product in diverse settings.
Assessing Compatibility and Integration
Compatibility with existing infrastructure and integration capabilities are pivotal aspects addressed in technical specifications. This portion examines compatibility matrices, interface protocols, and integration options, empowering users to seamlessly incorporate the product into their existing setup.
Evaluating Performance Metrics for Monitoring Points

When gauging the effectiveness of monitoring points, it’s imperative to delve into the intricacies of their performance metrics. By assessing these key indicators, one can gain valuable insights into the efficiency and reliability of the monitoring system. This section aims to dissect various performance metrics, shedding light on their significance in ensuring robust monitoring capabilities.
| Performance Metric | Description | Importance |
|---|---|---|
| Latency | The time it takes for data to traverse from its source to the monitoring point. | Crucial for real-time monitoring applications, where delays can compromise the effectiveness of the system. |
| Throughput | The rate at which data can be processed and analyzed by the monitoring point. | Essential for handling high volumes of data without experiencing bottlenecks or slowdowns. |
| Accuracy | The degree to which the monitoring point correctly identifies and interprets incoming data. | Integral for ensuring the reliability of monitoring insights and decision-making processes. |
| Scalability | The ability of the monitoring point to accommodate increasing data loads and expanding network infrastructure. | Crucial for future-proofing the monitoring system and adapting to evolving operational requirements. |
| Resource Utilization | The efficiency with which the monitoring point utilizes computational resources such as CPU and memory. | Important for optimizing resource allocation and maximizing the cost-effectiveness of the monitoring infrastructure. |
By carefully evaluating these performance metrics, organizations can make informed decisions regarding the selection and optimization of monitoring points. A thorough understanding of these factors empowers stakeholders to build resilient monitoring solutions capable of meeting the dynamic demands of modern networks.
Utilizing Information Sheets for Optimal Checkpoint Understanding
In the realm of navigating through pivotal junctures within systems and processes, a comprehensive grasp of crucial data repositories is indispensable. This segment elucidates effective strategies for leveraging informational documents to enhance comprehension and decision-making prowess in critical situations.
1. Strategic Digestion Techniques

Mastering the art of information absorption involves more than mere perusal; it necessitates a strategic approach. Prioritize identifying key insights and patterns embedded within the labyrinth of data. Employ techniques such as skimming, scanning, and in-depth analysis to extract pertinent details efficiently.
2. Contextual Synthesis Frameworks
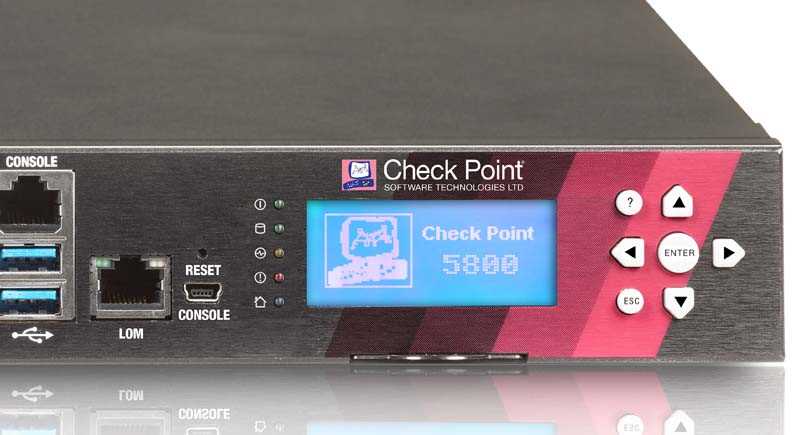
Understanding checkpoints extends beyond isolated data points; it demands contextual synthesis. Integrate diverse sources of information to construct a comprehensive narrative surrounding pivotal checkpoints. Utilize frameworks such as comparative analysis and historical context to imbue insights with depth and relevance.
- Deploy analytical tools to discern correlations and causal relationships.
- Embrace interdisciplinary perspectives to enrich understanding and foresight.
- Engage in collaborative discourse to foster diverse insights and perspectives.
By amalgamating strategic digestion techniques with contextual synthesis frameworks, individuals can unlock the full potential of informational documents, thereby enhancing their capacity to navigate and respond effectively to critical checkpoints.