
Welcome to an exploration of a remarkable breakthrough in the realm of cybersecurity. Brace yourself for an enthralling journey into the innovative dimensions unlocked by the remarkable 750 blueprint. This paradigm-shifting masterpiece has redefined the landscape of digital security, offering unparalleled protection against modern threats without compromising on performance or efficiency.
Immerse yourself in a realm where traditional barriers and limitations become a thing of the past. The 750 blueprint is a groundbreaking solution meticulously crafted to safeguard your digital infrastructure with unwavering precision and agility. Prepare to unravel a treasure trove of cutting-edge features and advanced technologies, all elegantly interwoven to create an impenetrable shield against the most sophisticated adversaries in cyberspace.
Embark on a voyage among the pioneers of security architecture and witness the birth of a game-changer. With the 750 blueprint, the boundaries of what was once deemed possible in safeguarding data and networks have been shattered. Through a fusion of uncompromising robustness and fluid intelligence, this revolutionary blueprint is poised to redefine the very notion of cybersecurity, enabling organizations to thrive in a fast-evolving digital landscape.
Overview and Key Features

In this section, we will provide an overview of the product and highlight its key features, without explicitly mentioning the specific product name or model number. We will present a brief introduction to the technology and its capabilities, showcasing its potential applications and advantages.
Advanced Security Solutions
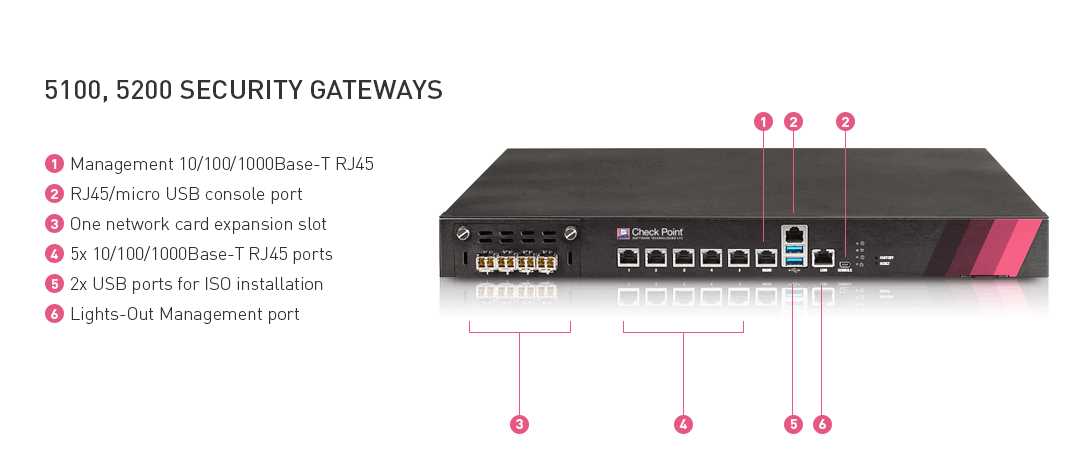
Discover a cutting-edge security solution that offers advanced protection for your network and data. This powerful technology is designed to safeguard your digital assets and confidential information from potential threats, ensuring the integrity and privacy of your network. With its robust security features, you can rest assured knowing that your network is secure from unauthorized access and potential breaches.
Efficiency and Performance

Experience enhanced performance and speed with this state-of-the-art technology. Engineered for optimal efficiency, it provides seamless and reliable connectivity, minimizing disruptions and maximizing productivity. Whether you are running critical business applications or simply browsing the internet, this technology delivers exceptional performance, allowing you to stay connected and productive with ease.
| Feature | Benefit |
|---|---|
| Advanced threat detection | Identify and neutralize potential threats before they can cause harm |
| Intuitive user interface | Streamlined management and configuration for effortless operation |
| Flexible connectivity options | Seamless integration with various network infrastructures |
| Robust performance | High-speed data processing for smooth and efficient operations |
| Scalability | Ability to expand and adapt to the changing needs of your network |
Technical Specifications and Performance

In this section, we will explore the technical specifications and performance of the device, providing you with a comprehensive understanding of its capabilities and functionalities. We will delve into various aspects such as processing power, network connectivity, and functional exceptionalities, offering you a rich and informative picture of the device’s performance.
Let’s start by looking at the processing power of the device. With a robust and efficient processor, the device ensures speedy and efficient operations. The powerful processor enables seamless multitasking and enables the device to handle complex tasks with ease. Additionally, the device boasts a high-performance engine that maximizes throughput and enhances overall productivity.
- Processing Power: The device is equipped with a high-speed processor that ensures fast and efficient operations.
- Network Connectivity: The device provides seamless network connectivity with its advanced networking capabilities, allowing for smooth and uninterrupted communication.
- Data Handling: With its exceptional data handling capabilities, the device efficiently manages and processes large volumes of data, facilitating effective decision-making and analysis.
- Security Features: The device incorporates cutting-edge security features, ensuring the safety and protection of your data from potential threats and unauthorized access.
In terms of performance, the device sets high standards, excelling in various key areas. Whether it be data processing speed, network reliability, or advanced security features, the device consistently delivers outstanding performance, meeting the demands of even the most challenging environments.
- Data Processing Speed: The device offers fast and efficient data processing, allowing for quick analysis and decision-making.
- Network Reliability: With its advanced network connectivity, the device ensures reliable and stable communication, minimizing downtime and maximizing productivity.
- Security Integrity: The device maintains the integrity of your data through its robust security features, safeguarding against any potential breaches or cyber threats.
- System Stability: The device guarantees stable and reliable performance, even under high workloads and demanding conditions.
Overall, the technical specifications and performance of this device demonstrate its capabilities in providing a high-performing and efficient solution. With its powerful processing capabilities, seamless network connectivity, and advanced security features, this device stands out as a reliable and secure choice for various applications.
Benefits and Applications
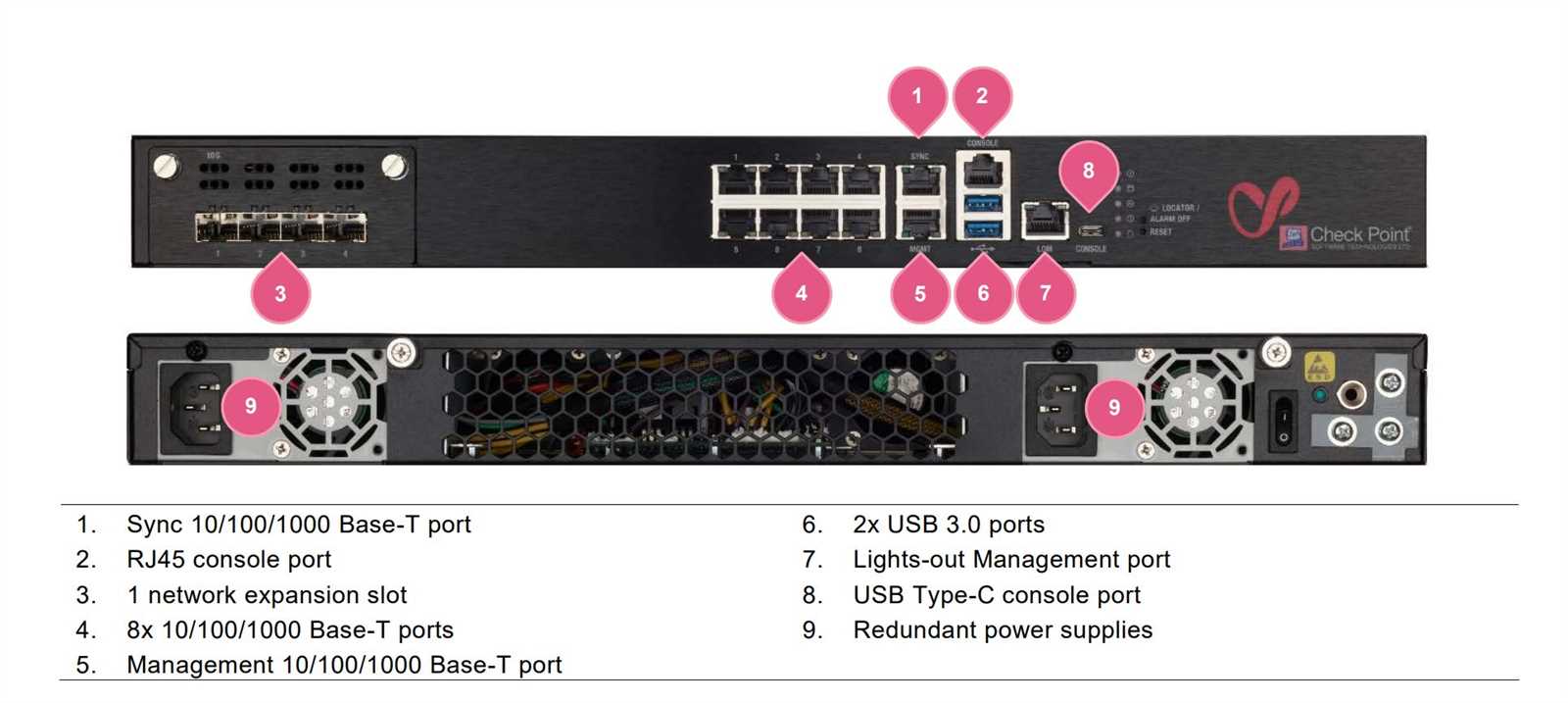
In this section, we will explore the various advantages and practical uses offered by the innovative features of the Checkpoint 750. By harnessing its cutting-edge technology, this solution optimizes security and simplifies network operations, providing a myriad of benefits for businesses across diverse industries.
Enhanced Security

One of the key advantages of the Checkpoint 750 is its ability to provide robust security measures for protecting critical assets. With advanced threat prevention capabilities and intelligent intrusion detection system, it safeguards networks from unauthorized access, malware, and other cyber threats. This ensures the integrity and confidentiality of sensitive business information, allowing companies to operate in a secure and protected environment.
Streamlined Network Management

By integrating powerful network management features, the Checkpoint 750 greatly simplifies the task of network administrators. Its intuitive and user-friendly interface allows for easy configuration, monitoring, and troubleshooting, reducing complexity and enhancing efficiency. With comprehensive visibility into network traffic and detailed reporting, businesses can quickly identify and address any issues, ensuring smooth operations and minimizing downtime.
| Applications | Description |
|---|---|
| Small and Medium Enterprises | The Checkpoint 750 offers an ideal security solution for small and medium-sized enterprises, providing cost-effective yet powerful protection against cyber threats. Its compact design and easy deployment make it a perfect fit for organizations with limited resources, enabling them to stay secure without compromising performance. |
| Remote Offices | For companies with remote offices or branch locations, the Checkpoint 750 offers a reliable and secure connection to the main network. Its VPN capabilities ensure encrypted and seamless communication, enabling remote workers to access critical resources and collaborate effectively, regardless of their physical location. |
| Retail Industry | The retail sector can benefit from the Checkpoint 750’s comprehensive security features to protect sensitive customer information, prevent data breaches, and ensure compliance with industry regulations. Its advanced firewall capabilities, combined with threat intelligence, provide a robust defense against cyber attacks, allowing retailers to focus on providing exceptional customer experiences. |
Overall, the Checkpoint 750 offers a wide range of benefits and applications, catering to the security and network management needs of businesses of all sizes and industries. With its advanced features and flexibility, it empowers organizations to stay resilient in the face of evolving cyber threats while maximizing operational efficiency.