
Unlocking the potential of cutting-edge technology, this exploration delves into the intricate details and pivotal features of a formidable device, revealing its prowess without explicitly naming it. Delve into the realms of innovation and performance as we dissect the essence of this technological marvel.
Embark on a journey of discovery, where each specification holds significance beyond its mere numerical value. Through meticulous examination and contextualization, we shed light on the essence of this formidable entity, unraveling its capabilities and strengths.
Peering beneath the surface, we navigate through a labyrinth of information to unveil the essence of this enigmatic apparatus. Prepare to be captivated by a narrative that transcends conventional boundaries, offering insights that transcend the ordinary.
Exploring the Comprehensive Specifications of the Big IP 3900 Document: Essential Details
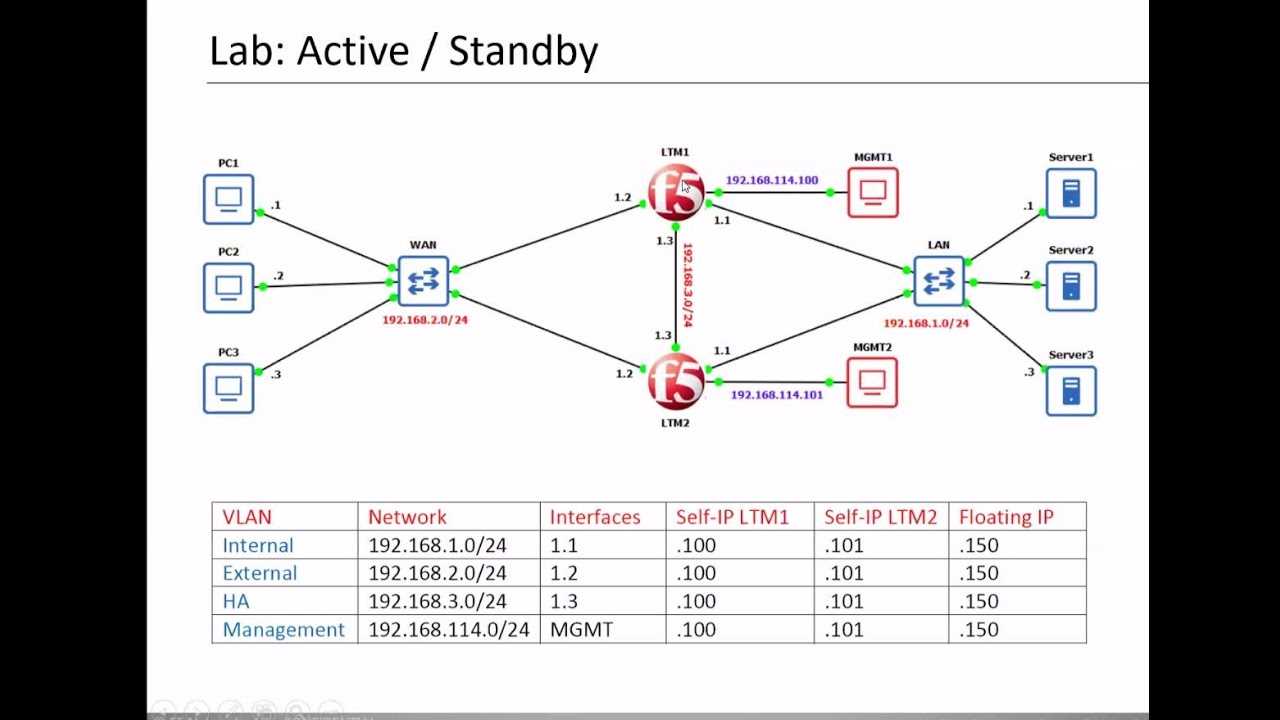
In this segment, we delve into the intricate particulars outlined in the comprehensive documentation of the formidable device, shedding light on its fundamental attributes and performance metrics. By navigating through the structured data provided, we aim to uncover the core functionalities and technical nuances encapsulated within.
| Feature Category | Key Aspects |
| Performance Metrics | Examining the device’s operational efficiency, throughput capacity, and response times. |
| Hardware Specifications | Analyzing the hardware components, including processors, memory, and network interfaces. |
| Software Capabilities | Assessing the software functionalities, such as supported protocols, security features, and management options. |
| Scalability | Evaluating the scalability potential in terms of concurrent connections, sessions, and SSL transactions. |
| Redundancy and High Availability | Exploring redundancy mechanisms, failover capabilities, and resilience to ensure uninterrupted operations. |
| Integration and Compatibility | Understanding integration possibilities with existing infrastructures and compatibility with diverse environments. |
Unlocking Performance Metrics

Exploring the intricacies of optimizing operational efficiency lies at the heart of understanding the performance metrics within the realm of advanced network infrastructure. This section delves into unraveling the key indicators that illuminate the efficacy and potency of network devices, fostering a comprehensive comprehension of their operational dynamics.
The Essence of Performance Metrics
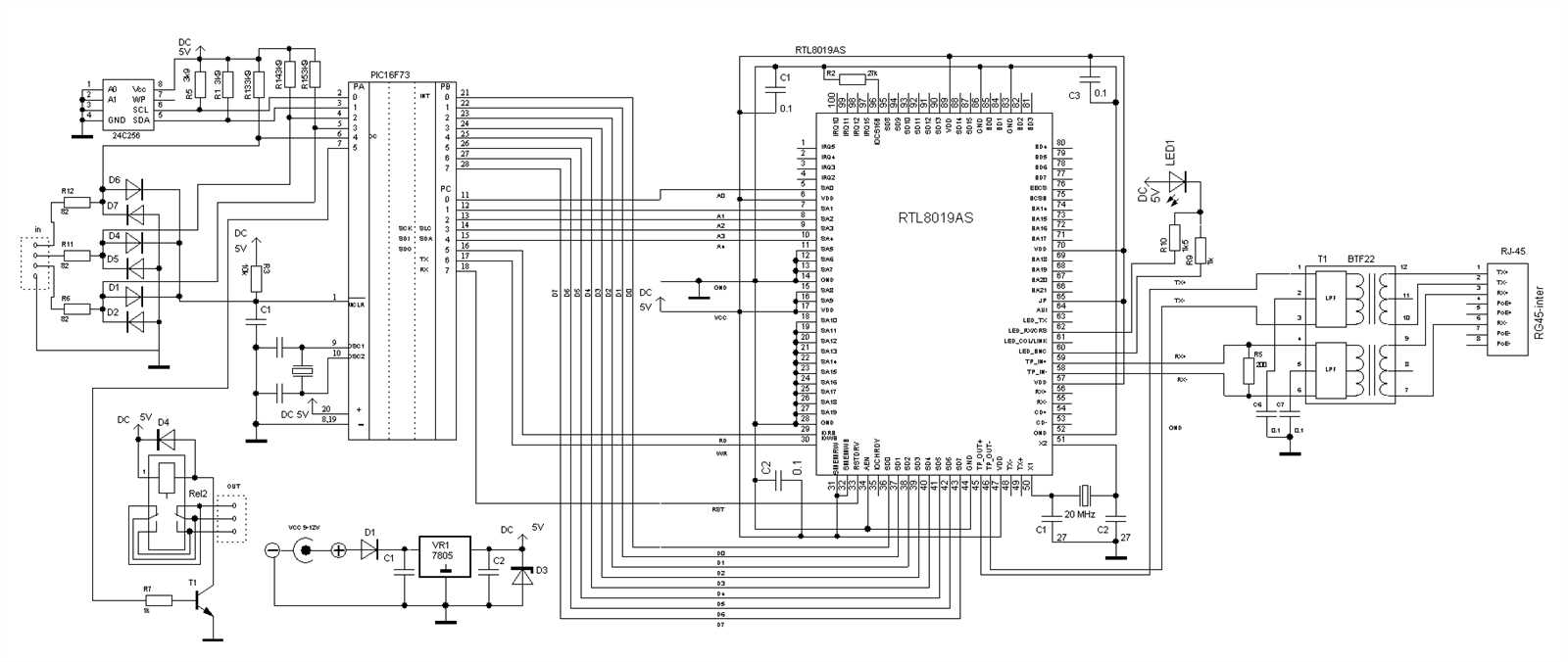
Performance metrics encapsulate the nuanced facets of operational efficacy, transcending mere numerical representations to unveil the underlying mechanisms steering network performance. By deciphering these metrics, one gains profound insights into the interplay of variables shaping the efficiency and resilience of network infrastructure.
- Unveiling the dynamics of throughput and bandwidth utilization.
- Deciphering latency and response times to gauge real-time responsiveness.
- Scrutinizing error rates and packet loss for seamless data transmission.
- Assessing CPU and memory utilization to optimize resource allocation.
Navigating Performance Optimization Strategies
Unlocking the full potential of network performance necessitates a strategic approach encompassing meticulous optimization techniques. By harnessing insights gleaned from performance metrics, administrators can orchestrate targeted interventions to enhance operational efficiency, fortify security postures, and streamline resource utilization.
- Implementing load balancing mechanisms to distribute traffic evenly.
- Deploying caching mechanisms to alleviate bandwidth constraints.
- Fine-tuning routing protocols to expedite data transmission.
- Integrating compression algorithms to mitigate latency.
Understanding Connectivity Options

Exploring the myriad of connection possibilities unveils a rich tapestry of pathways to link your system with external networks. Delving into these options opens the door to a world of communication avenues, each tailored to specific requirements and circumstances.
Wired Connections:
Embracing the stability and reliability of physical connections, wired options offer steadfast links through Ethernet ports and interfaces. These connections form the backbone of network infrastructures, ensuring consistent and secure data transfer.
Wireless Connectivity:
Embracing the flexibility of wireless technology, these options liberate devices from the constraints of cables, fostering mobility and agility. Wi-Fi and other wireless protocols provide seamless integration into networks, enabling connectivity in diverse environments.
Virtual Private Networks (VPNs):
Empowering secure communication over public networks, VPNs establish encrypted tunnels, safeguarding data as it traverses the internet. This clandestine connectivity ensures privacy and integrity, essential for transmitting sensitive information.
Cloud Integration:
Embracing the scalability and accessibility of cloud services, integration options facilitate seamless interaction between local systems and cloud-based resources. This synergy enables efficient utilization of distributed computing power and storage.
Redundancy Protocols:
Ensuring continuity and resilience, redundancy protocols offer failover mechanisms to mitigate disruptions in connectivity. Through redundant links and protocols like HSRP and VRRP, systems maintain uptime even in the face of network failures.
Network Security:
Guarding against threats and vulnerabilities, security measures fortify connectivity options, preserving the integrity and confidentiality of data. Firewalls, intrusion detection systems, and encryption techniques bolster defenses, ensuring robust network protection.
Interoperability:
Fostering seamless interaction between diverse systems and protocols, interoperability bridges gaps and facilitates collaboration. Standardized interfaces and protocols promote compatibility, enabling smooth communication across heterogeneous environments.
By comprehensively understanding the diverse connectivity options available, organizations can architect robust networks that meet the demands of modern digital ecosystems.
Examining Security Features and Capabilities
In this section, we delve into the robust array of protective measures and functionalities inherent within the specified device, aiming to provide a comprehensive understanding of its security provisions. Through meticulous scrutiny, we uncover the diverse arsenal of safeguards and capabilities engineered to fortify data integrity, thwart unauthorized access, and mitigate potential vulnerabilities.
Advanced Encryption

One pivotal aspect of the security architecture lies in its implementation of cutting-edge encryption techniques, ensuring that sensitive information remains shielded from prying eyes and malicious entities. By harnessing cryptographic protocols and algorithms, the system fortifies data confidentiality and integrity, fostering a secure environment for data transmission and storage.
Intrusion Detection and Prevention
Another integral facet of the security apparatus encompasses sophisticated intrusion detection and prevention mechanisms, which serve as vigilant guardians against illicit incursions into the system. Leveraging a combination of heuristic analysis, anomaly detection, and real-time monitoring, the device stands poised to identify and thwart suspicious activities, thereby fortifying the perimeter against potential breaches.
| Security Feature | Description |
|---|---|
| Firewall Protection | The device is equipped with a robust firewall solution, capable of filtering network traffic based on predetermined security rules, thereby erecting a formidable barrier against unauthorized access. |
| Role-based Access Control | Through the implementation of role-based access control mechanisms, the system administers granular permissions to users, ensuring that each individual is granted precisely the level of access necessary for their designated tasks. |
| Secure Remote Management | Facilitating secure remote management capabilities, the device enables administrators to oversee and configure system settings from remote locations, bolstering operational efficiency without compromising security. |