
Unlocking the potential of comprehensive information protection
Discover a revolutionary approach to safeguarding your critical data and ensuring its seamless accessibility. In an era where digital assets reign supreme, the need for robust security measures and efficient data management solutions has never been more pressing. This paradigm shift necessitates a comprehensive strategy that transcends conventional methods, embracing innovation and adaptability as cornerstones.
Explore the next evolution in data fortification, where resilience meets simplicity, and complexity yields to clarity. Delve into a realm where data integrity is not merely preserved but fortified against the ever-looming threats of corruption and loss. This paradigmatic shift in data protection heralds a new era of confidence, where businesses can thrive amidst uncertainty, knowing their information assets are shielded by an impenetrable fortress.
Enhanced Data Protection with Barracuda Backup Datasheet

In the realm of safeguarding critical information, ensuring the resilience of digital assets stands paramount. This section delves into the fortified fortifications provided by the data protection apparatus delineated in the Barracuda Backup Datasheet. Herein lies a narrative elucidating the augmentation of defensive mechanisms and the cultivation of impregnable bulwarks shielding against the pernicious onslaught of data vulnerabilities.
|
Robust Redundancy: Within the framework of data fortification, redundancy emerges as the cornerstone of resilience. The datasheet illuminates the deployment of redundant stratagems, fostering an ecosystem where data integrity thrives amidst the tumult of digital landscapes. |
|
Immutable Integrity: Integral to the discourse of data protection is the preservation of integrity in its purest form. Through meticulous methodologies outlined in the datasheet, integrity becomes an immutable facet, impervious to the erosive forces seeking to compromise its sanctity. |
|
Resilient Recovery: Amidst the labyrinth of potential disruptions, the datasheet advocates for a paradigm shift towards resilient recovery mechanisms. Armed with innovative methodologies, it endeavors to expedite the restoration process, ensuring minimal downtime and maximal continuity. |
As the digital terrain evolves and adversarial elements continue to proliferate, the Barracuda Backup Datasheet emerges not merely as a compendium of features but as a manifesto of fortitude. Through its synthesis of redundancy, integrity, and recovery, it stands as a sentinel guarding the sanctity of data in an era fraught with uncertainty.
Comprehensive Solutions Ensuring Business Resilience
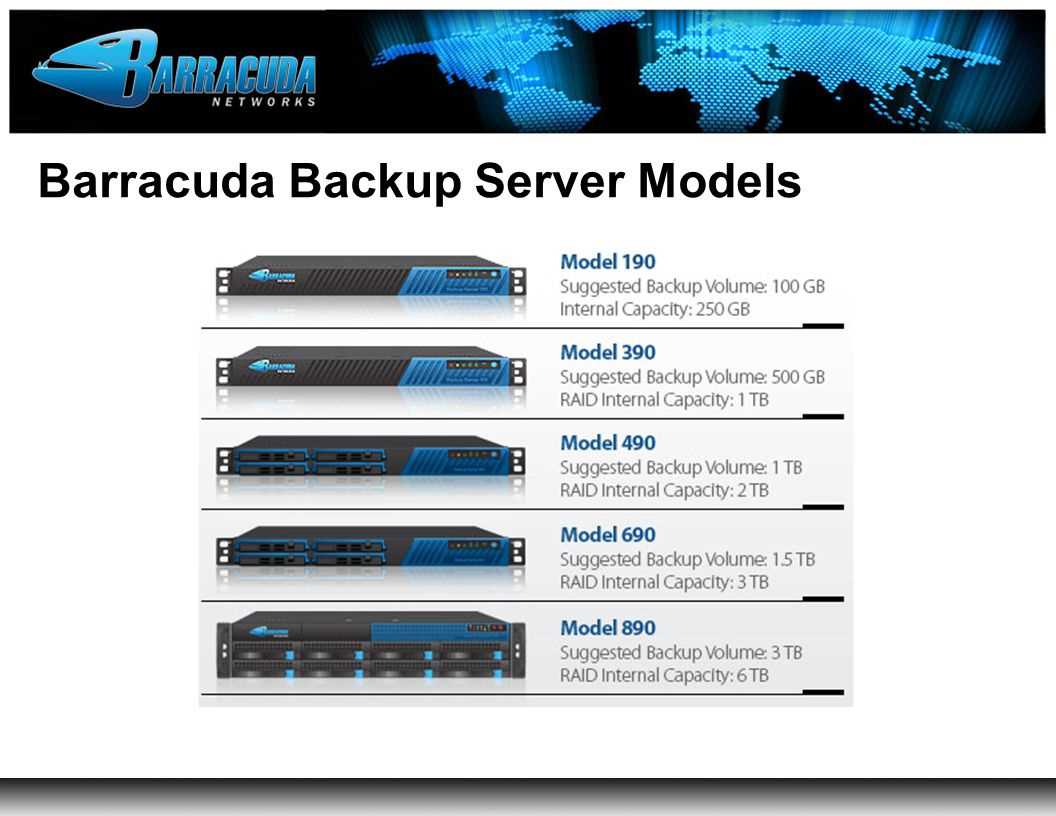
In today’s dynamic business landscape, maintaining uninterrupted operations is paramount for sustained success. A robust strategy for safeguarding critical data and ensuring seamless continuity is indispensable. This section elucidates a comprehensive suite of solutions designed to fortify businesses against disruptions, facilitating seamless operations even in the face of unforeseen challenges.
Holistic Data Protection Framework
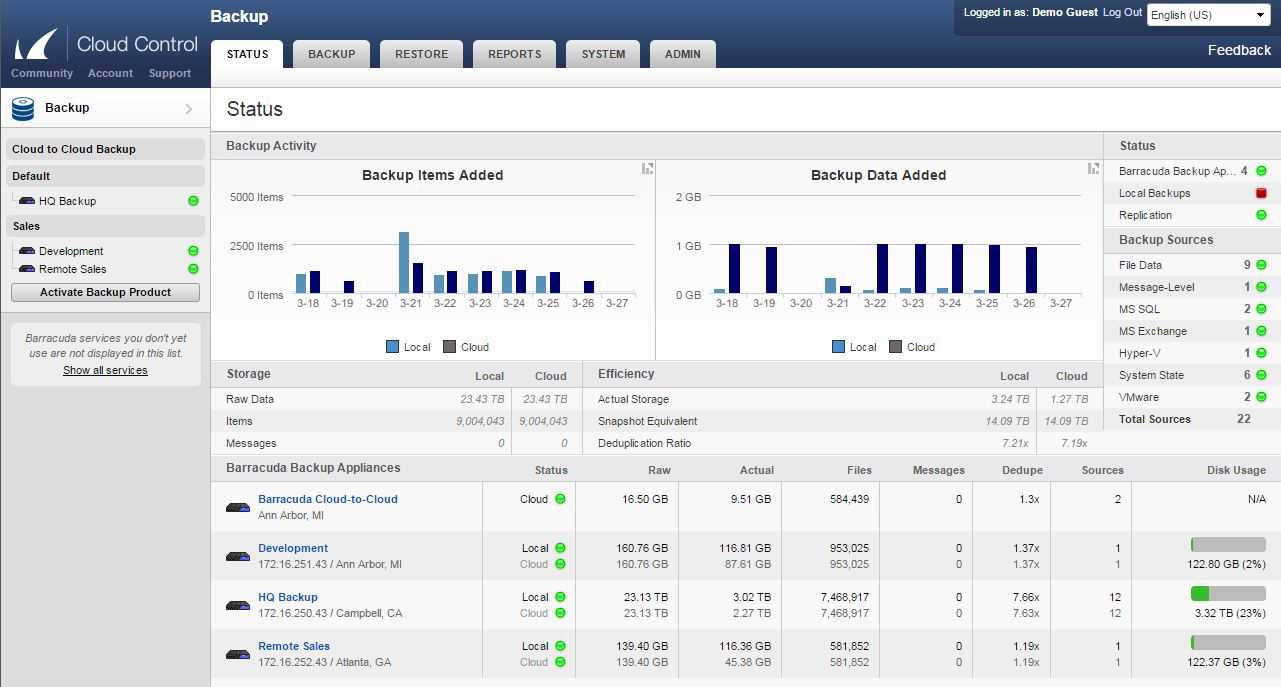
Central to business continuity is a holistic approach to data protection. This entails implementing a multifaceted framework encompassing redundancy, encryption, and rapid recovery mechanisms. By deploying a diversified arsenal of safeguards, enterprises can mitigate risks associated with data loss or corruption, thereby fortifying their resilience.
Scalable Infrastructure for Evolving Needs

Recognizing the evolving nature of business requirements, our solutions offer scalability to adapt to varying workloads and expanding datasets. Through scalable infrastructure, organizations can seamlessly accommodate growth without compromising efficiency or jeopardizing data integrity. This flexibility ensures that backup solutions remain agile, catering to the dynamic demands of modern enterprises.
| Feature | Description |
|---|---|
| Data Redundancy | Ensures redundancy across multiple storage nodes, safeguarding against single points of failure. |
| Encryption | Utilizes robust encryption algorithms to secure data at rest and in transit, bolstering confidentiality. |
| Rapid Recovery | Facilitates swift restoration of data in the event of disruptions, minimizing downtime and maximizing productivity. |
| Scalability | Offers flexible scalability to accommodate evolving business needs and expanding datasets. |
Simplified Management and Monitoring Features

In this segment, we delve into the streamlined methods and comprehensive oversight functionalities integrated within the system. These elements not only facilitate the administration process but also ensure meticulous surveillance of operations, ensuring seamless functionality.
Intuitive Interface
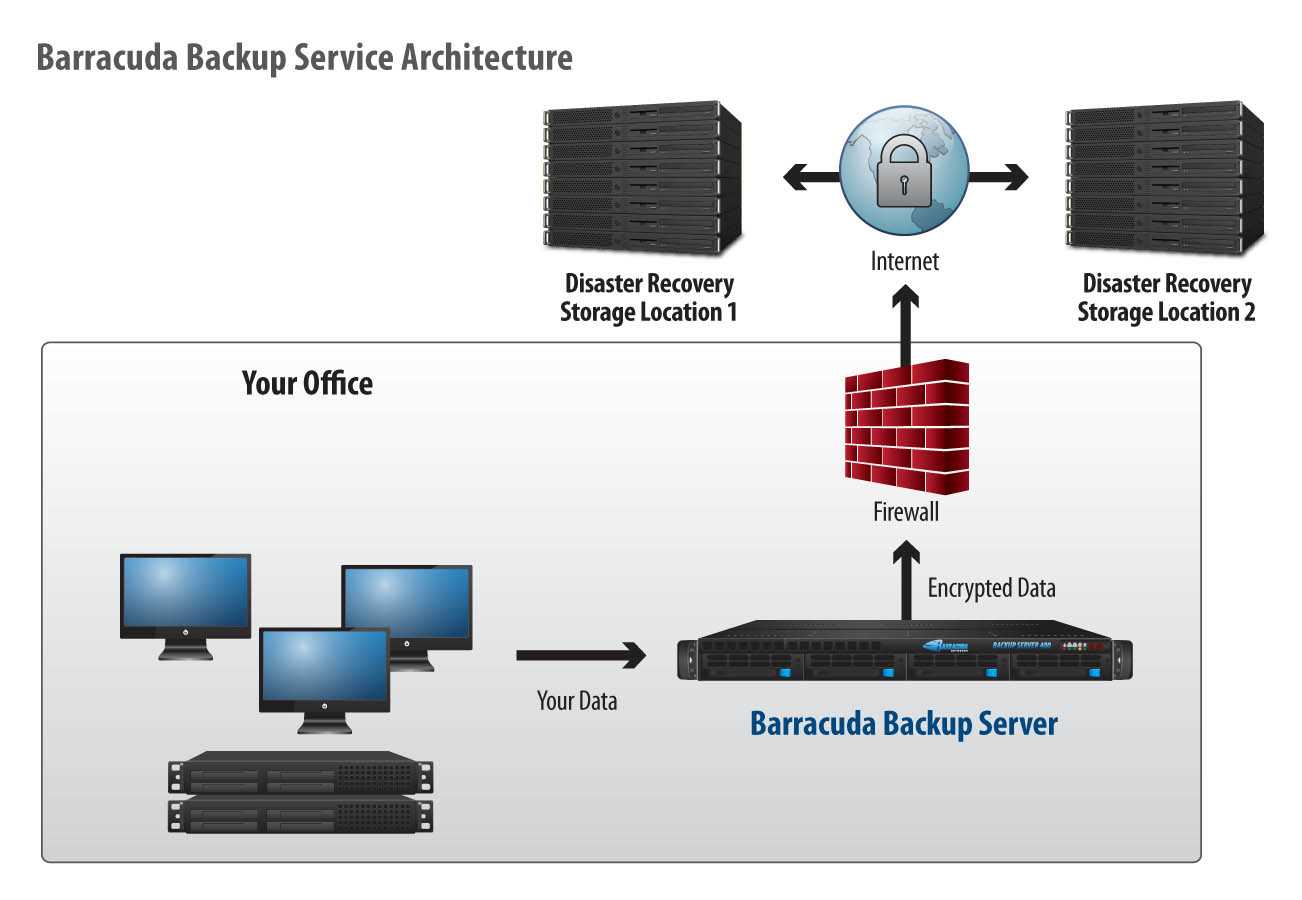
The platform boasts an intuitive interface, designed to simplify navigation and minimize the learning curve for users across proficiency levels. Through intuitive design elements and clear labeling, users can effortlessly traverse the system, accessing essential functionalities with ease.
Comprehensive Monitoring Capabilities
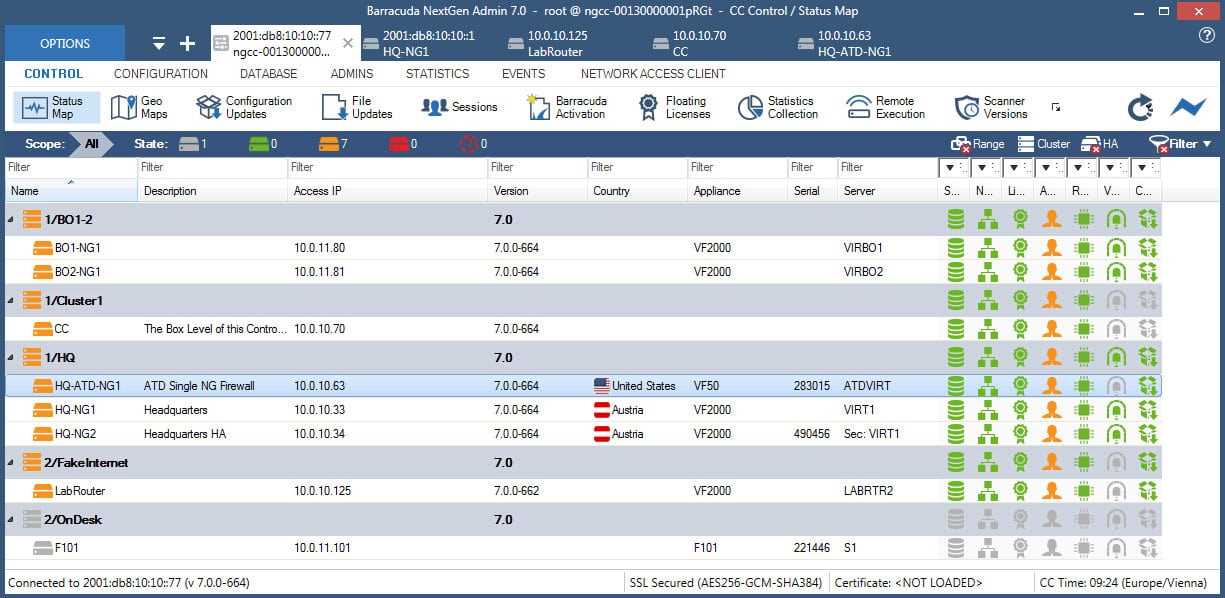
Bolstered by robust monitoring capabilities, the system provides comprehensive insights into performance metrics and operational statuses. Through real-time monitoring and detailed analytics, administrators gain invaluable visibility into system health, facilitating proactive maintenance and optimization efforts.
Robust Security Measures to Safeguard Your Data

In the ever-evolving landscape of digital threats, ensuring the security of your vital information is paramount. This section delves into the comprehensive security measures implemented to fortify your data against a myriad of potential risks. From encryption protocols to intrusion detection systems, every facet of safeguarding your valuable data is meticulously addressed.
Data Encryption Protocols

Utilizing cutting-edge encryption algorithms, your data is shielded from unauthorized access throughout its lifecycle. Strong encryption mechanisms scramble your information, rendering it unintelligible to any unauthorized entities attempting to intercept or tamper with it.
Intrusion Detection and Prevention Systems

Our robust intrusion detection and prevention systems stand vigilant, constantly monitoring for any suspicious activity or attempted breaches. With real-time alerts and proactive measures, potential threats are swiftly identified and neutralized before they can compromise the integrity of your data.
- Continuous Monitoring and Analysis
- Immediate Response to Suspicious Activity
- Dynamic Threat Intelligence Integration
By combining advanced encryption protocols with proactive intrusion detection measures, your data remains resilient against even the most sophisticated cyber threats, ensuring peace of mind and continuity of operations.