
Embark on a journey into the heart of modern networking infrastructure, where innovation and performance converge to redefine connectivity standards. Delve into the intricacies of next-generation hardware solutions that serve as the backbone of contemporary digital ecosystems. In this exploration, we navigate through the realms of advanced networking technologies, dissecting the capabilities and functionalities that propel data transmission to unparalleled heights.
Step into a realm where efficiency meets resilience, where every node and conduit orchestrates a symphony of seamless communication. Within these digital corridors lie the blueprints of progress, where components harmonize to uphold the integrity of information flow. Our focus transcends mere hardware; it encapsulates the essence of adaptability, the cornerstone of a dynamic network infrastructure tailored to meet the evolving demands of the digital landscape.
Unravel the tapestry of connectivity with a lens focused on the ASA5585 SSP 40. Here, we navigate through specifications and capabilities, deciphering the language of performance and reliability. This journey transcends the conventional notion of data sheets; it’s an odyssey through the realms of technological prowess and innovation.
Understanding the Key Features of ASA5585 SSP 40 Datasheet
In this section, we delve into the essential characteristics encapsulated within the ASA5585 SSP 40 datasheet, illuminating its core functionalities and pivotal attributes. Explore a comprehensive breakdown of its capabilities, delineating its performance metrics, security provisions, and operational intricacies.
Performance Metrics

Embark on an exploration of the performance metrics embedded within the ASA5585 SSP 40 datasheet, unveiling its prowess in handling data throughput, processing speeds, and resource utilization. Uncover the quantitative benchmarks that underscore its efficiency in managing network traffic and facilitating seamless operations.
Security Provisions
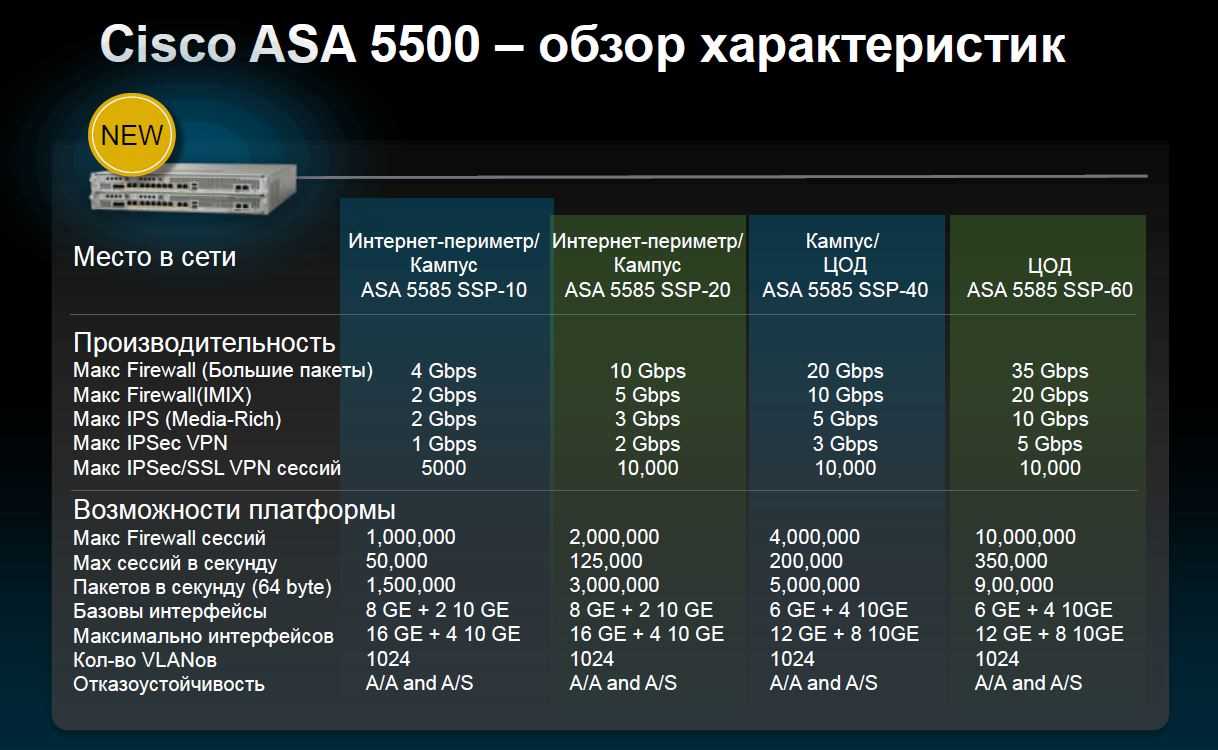
Delve into the realm of security provisions elucidated within the ASA5585 SSP 40 datasheet, elucidating its arsenal of defense mechanisms and threat mitigation strategies. Unravel the layers of protection crafted to safeguard against cyber threats, encompassing firewall capabilities, intrusion prevention systems, and encryption protocols.
| Key Features | Description |
|---|---|
| High Throughput | Efficiently processes large volumes of data without compromising performance. |
| Advanced Security | Utilizes sophisticated algorithms and protocols to fortify network defenses. |
| Scalability | Adaptable architecture capable of accommodating evolving network demands. |
| Reliability | Ensures consistent and uninterrupted service delivery under diverse conditions. |
Embark on a journey through the intricacies of the ASA5585 SSP 40 datasheet, gaining insight into its multifaceted functionalities and indispensable contributions to network infrastructure.
Exploring Performance Metrics and Specifications
In this section, we delve into the intricacies of evaluating the efficiency and capabilities of cutting-edge networking hardware. Understanding the performance metrics and specifications of advanced networking devices is paramount for informed decision-making and optimal network design.
Key Performance Metrics
When assessing the prowess of networking equipment, various key performance metrics come into play. These metrics encompass factors such as throughput, latency, scalability, and reliability. Through meticulous analysis of these metrics, network architects can gauge the device’s capacity to handle data traffic, response time under load, ability to accommodate growth, and overall stability.
Specifications Overview

Beyond performance metrics lie a plethora of specifications that delineate the capabilities and limitations of the hardware. These specifications include interface types, maximum connections, VPN throughput, firewall performance, and more. Each specification provides valuable insights into the device’s compatibility with specific network requirements and its suitability for diverse deployment scenarios.
- Interface Types: Enumerates the available interfaces for connectivity, such as Ethernet, Fiber, or SFP.
- Maximum Connections: Specifies the maximum number of concurrent connections the device can support.
- VPN Throughput: Indicates the rate at which encrypted data can be transmitted over the VPN.
- Firewall Performance: Measures the device’s capability to inspect and process incoming and outgoing traffic while enforcing security policies.
By comprehensively examining performance metrics and specifications, network administrators can make informed decisions when selecting and configuring networking hardware, ensuring optimal performance and reliability for their infrastructure.
Security Capabilities and Integration Options
In this section, we delve into the robust security features and seamless integration possibilities offered by the ASA5585 SSP 40. Explore a myriad of protective measures and the diverse array of ways in which this system seamlessly merges with existing infrastructures.
Enhanced Protection: Discover an assortment of cutting-edge security functionalities designed to fortify your network against emerging threats. From advanced intrusion detection to dynamic threat intelligence, the ASA5585 SSP 40 delivers unparalleled safeguarding capabilities.
Seamless Integration: Uncover the versatility of integration options available with the ASA5585 SSP 40. Whether you seek to unify with existing security protocols or implement new solutions, this system seamlessly adapts to your infrastructure, fostering synergy and efficiency.
Flexibility in Deployment: Explore the various deployment scenarios supported by the ASA5585 SSP 40, ensuring compatibility with diverse network architectures. From on-premises installations to cloud-based configurations, tailor the deployment to suit your specific requirements.
Interoperability: Experience the ease of integration with third-party applications and platforms, facilitating a cohesive security ecosystem. The ASA5585 SSP 40 harmoniously interacts with a multitude of tools and systems, fostering interoperability and enhancing overall efficacy.
Scalability: Witness the scalability of the ASA5585 SSP 40, allowing for seamless expansion as your network evolves. Whether accommodating growing demands or adapting to dynamic environments, this system ensures sustained performance and reliability.
Comparative Analysis with Similar Firewall Solutions
In this section, we delve into a comprehensive examination of firewall solutions akin to the subject matter, exploring their functionalities, performance metrics, and feature sets. Through this analysis, we aim to provide a nuanced understanding of how various firewall options compare and contrast with each other, offering insights into their strengths, weaknesses, and suitability for diverse network environments.
Functionalities: We scrutinize the array of features and capabilities offered by each firewall solution, examining their efficacy in threat detection, intrusion prevention, content filtering, and network security management. By dissecting the functional aspects, we gain clarity on the extent to which these solutions safeguard network integrity and mitigate potential cyber risks.
Performance Metrics: Evaluating the performance metrics encompasses an assessment of throughput, latency, connection capacity, and scalability. Through empirical data and benchmarking analyses, we discern the efficiency and reliability of each firewall solution in handling varying levels of network traffic and sustaining optimal performance under duress.
Feature Sets: Delving into the feature sets entails an exploration of advanced security functionalities, such as deep packet inspection, application-layer filtering, SSL decryption, and threat intelligence integration. By dissecting the feature repertoire, we elucidate the extent to which these solutions empower administrators to fortify network defenses and adapt to evolving cyber threats.
Usability and Management: Beyond technical specifications, we examine the usability and management aspects of each firewall solution, considering factors such as user interface intuitiveness, policy configuration flexibility, and centralized management capabilities. By assessing these facets, we ascertain the ease of deployment, administration, and maintenance associated with each solution.
Cost-Efficiency and Total Ownership: Lastly, we delve into the cost-effectiveness and total ownership implications of adopting each firewall solution, considering factors such as initial investment, licensing fees, subscription models, and long-term operational expenses. Through financial analysis and ROI assessments, we elucidate the economic viability and value proposition offered by each solution over the course of their lifecycle.