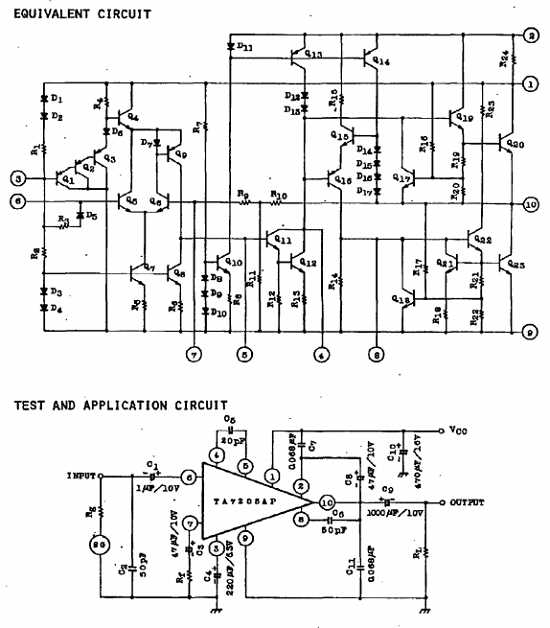
Embark on a journey of discovery as we delve into the intricate blueprint that encapsulates the essence of technological prowess.
Peer into the intricacies of innovation and explore the myriad functionalities that propel networks into the realm of efficiency and performance.
Unravel the layers of innovation as we navigate through the intricate pathways of connectivity and optimization.
Join us as we decipher the code to unparalleled network superiority, unveiling the secrets embedded within the fabric of advancement.
Understanding the Documentation of Aruba’s Network Device

In this section, we delve into comprehending the intricate blueprint of one of Aruba’s networking solutions. Unraveling the intricacies of this technical dossier unveils the core functionalities and specifications, providing a profound insight into its operational capabilities and performance metrics.
Exploring Technical Nuances: Navigate through the labyrinth of technical specifications and operational features encoded within the documentation. Delineate the functional intricacies that underpin the device’s operations, elucidating its architectural design and computational prowess.
Analyzing Performance Metrics: Scrutinize the empirical data delineated within the document, deciphering the performance benchmarks and efficiency metrics sans ambiguity. Uncover the empirical evidence that underscores the device’s reliability, scalability, and operational efficiency.
Deciphering Operational Capabilities: Unravel the narrative of operational capabilities encapsulated within the documentation, shedding light on its adaptive functionalities and operational versatility. Illuminate the operational scenarios wherein the device manifests its prowess, addressing diverse networking exigencies with finesse.
Interpreting Deployment Scenarios: Envision the myriad deployment scenarios elucidated within the documentation, discerning the tailored solutions catered to diverse networking environments. Explore the deployment flexibility and scalability options afforded by the device, accentuating its adaptability to varying infrastructural exigencies.
Unveiling Integration Possibilities: Embark on a journey through the documentation’s narrative, uncovering the integration possibilities and interoperability paradigms pertinent to the device. Navigate the realm of integration frameworks and compatibility matrices, elucidating the seamless assimilation of the device within heterogeneous networking ecosystems.
Key Features and Specifications
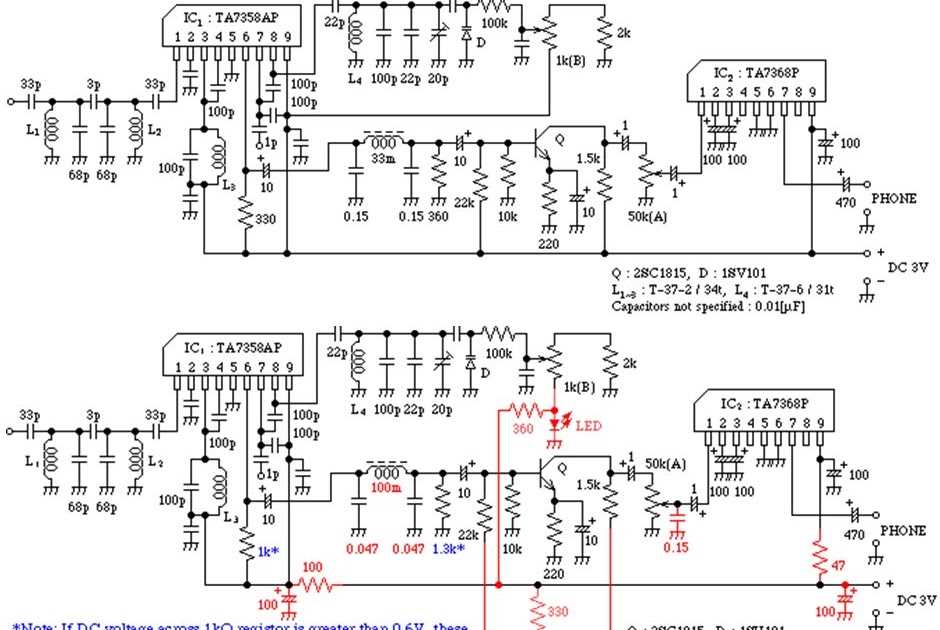
In this section, we delve into the distinctive attributes and technical details that characterize the essence of the device under scrutiny. From its foundational architecture to its performance benchmarks, this segment encapsulates a comprehensive overview of the product’s functionalities and parameters. Let’s explore the intricacies that distinguish this apparatus within its domain.
Performance Enhancements
- Advanced processing capabilities amplify operational efficiency.
- Optimized throughput ensures seamless data transmission.
- Elevated scalability empowers expansive network expansion.
Security Features

- Robust encryption protocols safeguard sensitive data.
- Intrusion detection mechanisms fortify network integrity.
- Granular access controls ensure authorized usage.
These are just a few highlights of the myriad features and specifications encapsulated within this remarkable device, setting it apart as a formidable contender in its realm of operation.
Deployment Scenarios and Application Scenarios

In this section, we explore various contexts and applications where the versatile capabilities of the product come into play. We delve into scenarios where this technology finds its niche, addressing diverse needs and challenges across different environments.
Enterprise Integration: One of the primary arenas where this solution shines is in seamlessly integrating diverse network infrastructures within enterprises. Whether it’s bridging legacy systems with modern architectures or harmonizing multi-site setups, the flexibility of this technology proves invaluable.
Edge Computing Environments: As computing continues its shift towards the edge, the importance of robust networking solutions becomes paramount. This product offers tailored solutions for edge deployments, ensuring low-latency connectivity and robust security in scenarios ranging from IoT networks to distributed computing environments.
Wireless Connectivity: With the proliferation of wireless devices in both consumer and enterprise settings, the demand for reliable and high-performance wireless networks has never been greater. This technology caters to various wireless deployment scenarios, from high-density environments like stadiums and campuses to outdoor setups requiring ruggedized solutions.
Cloud Integration: In an era dominated by cloud computing, the ability to seamlessly integrate on-premises networks with cloud services is crucial. This product provides seamless integration with leading cloud platforms, enabling hybrid cloud architectures and facilitating smooth migration strategies.
Security-Centric Deployments: Security is a top priority in today’s digital landscape, and this product offers robust solutions for security-centric deployments. From implementing advanced threat detection and prevention mechanisms to ensuring secure access control in BYOD environments, the versatility of this technology addresses a myriad of security challenges.
Vertical-specific Applications: Different industries have unique networking requirements, and this solution caters to a wide range of vertical-specific applications. Whether it’s optimizing network performance in healthcare environments, facilitating guest access in hospitality settings, or ensuring regulatory compliance in financial institutions, this technology adapts to the specific needs of diverse industries.
Explore the following sections to delve deeper into each deployment scenario, uncovering the tailored solutions and real-world use cases that demonstrate the versatility and effectiveness of this technology.
Performance and Efficiency Analysis

In this section, we delve into a comprehensive examination of the operational effectiveness and resource utilization of the specified hardware solution. The evaluation encompasses a meticulous scrutiny of its functionalities, responsiveness, and resource allocation strategies to ascertain its capability in meeting performance demands while ensuring optimal resource employment.
Functionality Evaluation

The first aspect under scrutiny pertains to the functionality assessment, wherein we explore the array of features and operations facilitated by the system. This evaluation encompasses an analysis of its diverse functionalities, including but not limited to, its handling of network traffic, management of connected devices, and execution of security protocols. Through this evaluation, we aim to discern the system’s versatility and its capacity to cater to a myriad of networking needs.
Resource Utilization Examination
Furthermore, our analysis extends to the examination of resource utilization efficiency. This involves a meticulous investigation into the allocation and utilization of computational resources such as processing power, memory, and bandwidth. By scrutinizing resource allocation strategies, we seek to gauge the system’s adeptness in optimizing resource employment to enhance operational efficiency while minimizing wastage.
| Performance Metrics | Evaluation Criteria |
|---|---|
| Throughput | Assessing the system’s data transfer rate under varying load conditions. |
| Latency | Evaluating the responsiveness of the system in processing and delivering network requests. |
| Resource Utilization | Analyzing the efficient usage of computational resources such as CPU, memory, and bandwidth. |
| Scalability | Assessing the system’s ability to accommodate increasing workloads and network expansion. |